In Good Company
Articles and Tips: article
01 Mar 2005
Author's Note: Who cares enough about file systems to read about one? You should, assuming that you have an active interest in protecting what chief information officers (CIOs) apparently agree is a valuable corporate asset: data. (You can find support for this claim in "State of the CIO 2004," CIO Research Reports, September 30, 2004. Also check out "The Six Commandments of Ethical Data Management," CIO Magazine, July 1, 2002.) Much of the data on your network--perhaps customer information, proprietary secrets, payroll details--is critical to the smooth-sailing, if not success, of your enterprise. And what dictates the ease by which you manage that data, the speed by which you access it, and the degree (at least in part) to which you protect it? Your file system, of course. So read on.
In business, you can seldom predict what will happen one day to the next, but you can expect at least this much: the enterprise will change, and the network data that drives the enterprise will grow. Employees are promoted and transferred; departments splinter and fuse; companies merge. You can count on such change--just as you can count on the Information Age guarantee: your network will store more data next year than it did this year. (For an inkling of how much more, see Who Knew?)
For you, a network administrator, these two consistencies potentially mean trouble, particularly if your network juggles huge amounts of data. When you have multi-terabyte volumes holding subdirectories laden with 5,000 or more files, your file system might lose its punch. Under this load, a once snappy file system might sluggishly return files from weighty volumes that the system battles to mount. You can buy more servers, split volumes and beef up server memory, but doing so is an impractical approach to an ongoing problem. What you really need is a file system that returns files from the heftiest of data stores at the blink-of-an-eye speed users require.
Of course, while a file system that scales well solves many of the problems of data growth, such a system does not necessarily solve the problems associated with enterprise changes. Every time users' roles change (which, depending on the size of your organization, might be a weekly if not daily occurrence), you have to change users' rights to the shared file system. Depending on your file system, incessantly tweaking hundreds of users' file system rights consumes more time than you and co-workers have to spend.
In the quest for a file system that is both scalable and manageable, you have another factor to consider: management's lust for Linux. With a long-established reputation for being secure, reliable and fast-performing, Linux poses an attractive, open source alternative to other server operating systems. Among other benefits, installing lean Linux on inexpensive hardware promises to minimize costs. Now where can you find a sophisticated, scalable, easy-to-manage file system for Linux?
Novell now offers the logical answer: Novell Open Enterprise Server, which offers Novell Storage Services on both operating systems included in Open Enterprise Server--NetWare 6.5 and SUSE LINUX Enterprise Server 9.
Admittedly, Novell Storage Services on NetWare 6.5 is old news, but Novell Storage Services on SUSE LINUX Enterprise Server 9 is new indeed. With Novell Storage Services on SUSE LINUX Enterprise Server 9, Novell brings to Linux what Novell Product Manager Richard Jones refers to as "the Lexus of file systems." With Novell Storage Services, you gain a file system unlike any other that offers performance, scalability and ease of management as unfaltering as data growth and enterprise change.
Store More With Less
First introduced in 1998 with NetWare 5.0, Novell Storage Services offers baseline features--on Linux as on NetWare--that are quite cool. (For information on a couple of these cool features, see Overbook 'Em.)
The fundamental benefit of the 64-bit Novell Storage Services is that it enables you to amass and manage lots of data while still enjoying speedy response times. Novell Storage Services recognizes and stores files and volumes as large as 8 TB each and supports as many as 8 trillion files per server--1 million of which can be concurrently open. Regardless of the size of the file, directory or volume, Novell Storage Services promises users rapid access to data.
Novell Storage Services requires only 1 MB RAM on a server to mount a volume, independent of the number of files the volume holds. Furthermore, you can activate an unlimited number of Novell Storage Services volumes concurrently per server, up to the available server memory. In other words, if you have 512 MB RAM, you can activate 512 Novell Storage Services volumes. If each of these volumes stores the maximum 8 TB, then on this single server, you can store as much as 4 petabytes (PB) of data. (A petabyte is 1,000,000,000,000,000 bytes which equals 1,024 TB.)
The better news is that, after a clean dismount, Novell Storage Services takes only seconds to mount volumes of any size. The secret behind this mounting speed is the way Novell Storage Services uses the server's cache and the way Novell Storage Services organizes storage on the server's hard disk. To mount a volume, Novell Storage Services uses advanced caching algorithms to place in cache only a minimal amount of a volume's file and directory information. As users access the system, Novell Storage Services caches only the directory entries necessary to enable that access, rather than reading in all of a volume's directory entries.
After a not-so-clean dismount, mounting the volume requires only a few extra seconds, during which time Novell Storage Services accesses the journal that it maintains on the server's hard disk. As a journaling file system, Novell Storage Services associates every change to the file system with a transaction, which it records in its journal. (Hence, a journal is simply a list of transactions.) When a server goes down unexpectedly, Novell Storage Services needs only to replay the journal to restore the server's volumes to a consistent state.
Not Just another One
Of course, the fact that Novell Storage Services is a journaling file system and that it manages large amounts of data is not unique. As you may know, at least four popular journaling file systems already exist in the Linux world, namely Ext3, ReiserFS, XFS and Journaled File System (JFS). (For more information about these file systems, see http://olstrans.sourceforge.net, www.namesys.com, http://oss.sgi.com, http://oss.software.ibm.com, respectively.)
These systems are also adept at handling large--and, in some cases, larger--files and directories than Novell Storage Services. XFS, for example, supports files as large as 9,000 PB. Keep reading.
Before you start groaning aloud and saying, "Oh great! Just what we need--another file system for Linux!" let me get right to the point: make no mistake, Novell Storage Services is not just another Linux file system. In fact, as Jones is quick to point out, "nothing else like Novell Storage Services exists in the Linux space--period."
At the root of its distinctiveness lies the fact that Novell Storage Services offers many more features than are available in Linux file systems that comply with the Portal Operating System Interface (POSIX) standard. Based on the UNIX operating system and as its name suggests, POSIX is a set of standard operating system interfaces, including application program, shell, utility and thread management interfaces.
Novell Storage Services moves freely beyond some of this standard's inherent limitations, most notably in the area of access control. Novell Storage Services brings to Linux a richer set of capabilities than the POSIX standard supports. (For information about some of these capabilities, see Now for Something Completely Different.) In fact, Novell Storage Services includes several features that are unmatched by any other Linux file system, including--but not limited to--the following:
Back links in files and subdirectories to parent directories
A trustee model that ensures tight rein over who has access to what
An extensive list of file attributes that offers greater control over the treatment and purpose of each file
A Salvage feature that enables users to restore files that viruses or applications delete
When Children Know Their Parents
In all file systems, including Novell Storage Services, parent directories contain links to their children, that is, the files and subdirectories they hold. Novell Storage Services follows this rule and adds to it another neat--and unique--trick: in Novell Storage Services (as in the traditional Novell file system), file and subdirectory children contain links to their parent directories.
This is not true of any other file system. In Linux file systems, for example, the inode files for directories contain inode numbers for every file and subdirectory they hold. (These inode files are computer-stored files that contain information about a file. Each inode has a unique number.) The inode files for files and subdirectories, in contrast, do not include the inode numbers for the directories that hold them.
Because its file system children know their parents, Novell Storage Services offers unique features that simplify and, in most cases, accelerate the management of file system access rights.
For example, Novell Storage Services can assess users' rights from where you grant them (say, at the file level) back to the root of the file system directory tree. For example, look at Figure 1. To grant Joe rights to his Novell Storage Services directory, you start by making the Joe User object a trustee of the Joe directory. (Trustees can be any Novell eDirectory User, Group, Organizational Role or container object.)
Figure 1
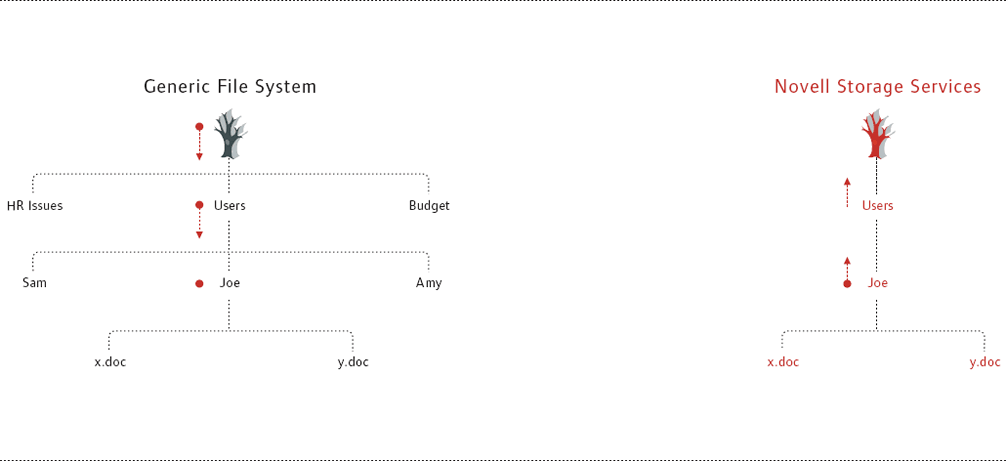
When you make Joe a trustee of the Joe directory, Novell Storage Services assigns the File Scan right by default. (See Figure 1.) By taking that one step, you enable Joe to see every subdirectory along the path from the Joe directory back to the volume's root directory. (For more information about File Scan and other rights, see A Range of Rights.)
To make this subdirectory path visible in other file systems, you have to stamp Joe's rights at every subdirectory along the way. (See Figure 1.) Granted, some file systems have tools that automate this task. While convenient, these tools pose the potential for problems of a different nature. For example, one Novell customer shared an incident in which two internal divisions merged. The users within these divisions needed access to each other's shared file servers (in this case, Windows 2000 servers). Administrators opted to automate the task, and when the action started, CPU utilization soared to 100 percent, leaving the server inaccessible for nearly 72 hours. And no wonder: the tool was stamping users' rights at every directory level in the multi-gigabyte-sized file systems.
"With Novell Storage Services," Jones points out, "this [process] would have taken a millisecond with no delays [in service]." (For more information about assigning rights in Novell Storage Services, see Go With the Flow.)
What They Can't See Won't Hurt You
Furthermore, in Novell Storage Services, users see only the subdirectories to which you have either granted explicit rights or to which they have inherited rights. (For more information about inherited rights, see Go With the Flow.)
For example, when you make Joe a trustee of the Joe directory, he can see the Joe directory, and the User directory, and every other directory along the path back to the root. However, just because he has rights to the Joe directory within the User directory does not mean that he can see the Sam and Amy directories also within the User directory. (See Figure 2.) In fact, unless you explicitly grant Joe rights to see these subdirectories or he has inherited rights to see them, Joe cannot see these subdirectories.
Figure 2
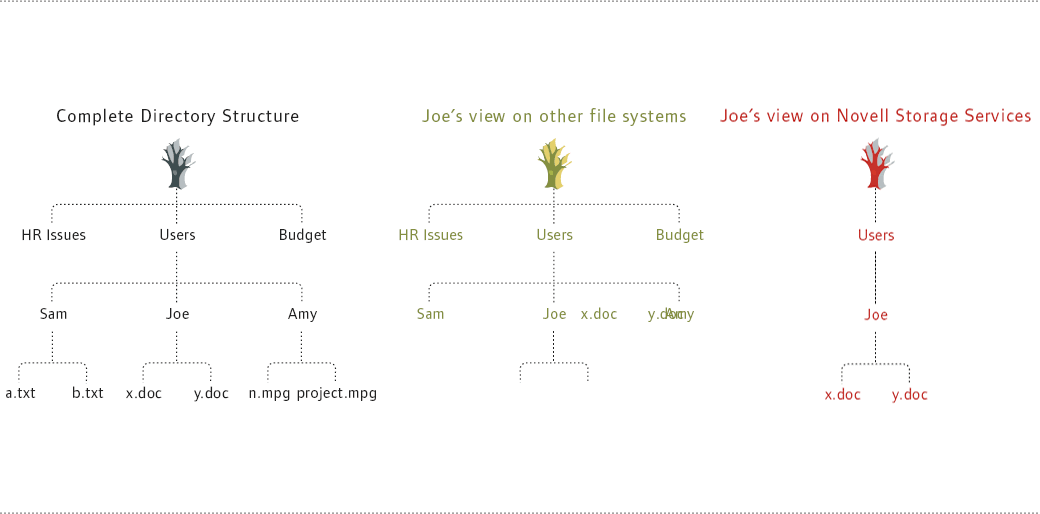
With Linux (and other) file systems, on the other hand, users see all of the subdirectories within a directory to which they have rights. (See Figure 2.) In these systems, you stamp rights for Joe at the User directory level to ensure that Joe has rights to the Joe directory and that he can see the directory path back to the root. When you do so, Joe also is able to see other directories within the User directory. Of course, Joe can only see these directories. He cannot open them, but allowing him to see directories he should not see is a bit like dangling the proverbial carrot.
Likewise, Novell Storage Services enables users to share files within a directory to which they have the appropriate rights without making visible all of the other files in this directory.
For example, suppose Amy wants Joe to see the project.mpg file in the Amy directory. (See Figure 3.) Assuming she has the Access Control right to the Amy directory, Amy can make Joe a trustee of the project.mpg file, after which Joe sees only project.mpg and none of the other files within the Amy directory. (The Access Control right enables Amy to add and remove trustees for the Amy directory and its files. For more information on Novell Storage Services trustee rights, see A Range of Rights below.)
Figure 3
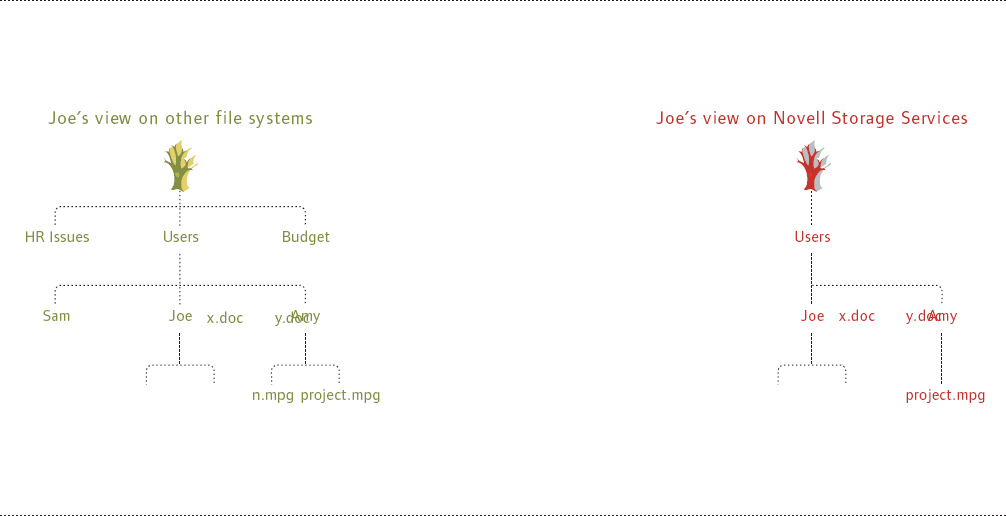
To accomplish the same task in other file systems, Amy would have to make Joe a trustee of the Amy directory to grant Joe rights to the project.mpg file, after which Joe can see all of the files in the Amy directory. (See Figure 3.)
Granted, Joe has rights only to see these files, so what, you may ask, is the harm? Exposing directories and files to users who should not see them is just an invitation for users to try to access them. One customer reported to Novell an incident that illustrates the potential impact of exposing tempting files. A directory named "HR Issues" had been hidden when the customer was using Novell's traditional file system on a NetWare server. However, after migrating to Windows, administrators unwittingly exposed the directory. After several failed attempts at opening the directory, one user eventually managed to do so.
A Range of Rights
In addition to the ability to limit the Novell Storage Services directories and files users can and cannot see, Novell Storage Services gives you a high degree of control over who has rights to what--and what those rights allow.
Novell Storage Services uses what Novell calls a Trustee model. In the Trustee model, you can assign as trustees of directories and files any Novell eDirectory object, most commonly, User, Group, Organizational Role or container objects (such as Organizational Unit and Organization objects). You can also make [Public] a trustee. Not an eDirectory object, [Public] represents any network user, logged in or not logged in. In Linux file systems, your options are considerably more limited. You can assign rights in Linux file systems only to users, groups or the world. (World is akin to [Public].)
For each Novell Storage Services trustee, you can grant one or more rights, which dictate access and usage restrictions for the directories and files to which trustees are assigned. Novell Storage Services offers a much richer set of rights than the POSIX-compliant Linux systems offer. Linux file systems offer only four rights: Set User ID (UID), Read, Write and Execute. "If you have only one application or one database accessing data in a file system," Jones concedes that this limited set of rights might meet your needs.
But if you are managing an environment where hundreds of users share millions of files on a large file system, a few extra rights for a little extra control might come in handy. Enter Novell Storage Services: Novell Storage Services doubles the number of rights available in Linux systems, offering eight access rights from which to choose. (For more information about these rights, view the Trustee Rights table.)
Specifically, in Novell Storage Services, you can assign trustees any of the following rights:
Supervisor
Create
Erase
File Scan
Modify
Read
Write
Access Control
As you may notice, Execute is not included in this list. In Novell Storage Services, Execute is a file attribute, not a right. (For more information on file attributes, see Attributes to Success.) With these eight different rights from which to choose (not to mention Execute as a file attribute), you have a high degree of control over the level of access trustees have to Novell Storage Services directories and files.
Go With the Flow
Remember that example of the customer who needed to grant two groups of users rights to each other's shared file system? What makes Jones so sure that the job would take considerably less time in Novell Storage Services? What makes him so sure is the concept of inherited trustee rights in Novell Storage Services, which makes managing access to the file system an efficient and simple process.
In Novell Storage Services, subdirectories and files can inherit rights from their parent directories. That is, when you grant a trustee rights, those rights (unless blocked) flow down the directory tree to subdirectories and files. Hence, to grant two groups of users rights to each other's file systems, you create two eDirectory Group objects: one each to represent the two user groups. Next, you make the Group objects trustees of the shared file systems' directories, and, by default, Novell Storage Services grants these trustees File Scan and Read rights. These rights flow down the tree, so with these two simple steps, your job is done.
As you may hope, you can easily block inherited rights by creating an inherited rights filter at any point in a directory path. Inherited rights filters stop rights from being inherited at and below the point along the directory path where you insert them. You may then assign trustees rights to specific files or directories at or below this point if these trustees' effective rights require broader or more restricted access than the filter allows.
For example, suppose the Communications group has Read rights to the Documentation directory. As a member of Communications, Linda has Read rights to the Documentation directory and inherits Read rights to any directory below this point. Further suppose that Linda is an explicit trustee of the Article subdirectory within the Documentation directory and has Write, Modify and Erase rights to this subdirectory. Other team members inherit Read rights to Linda's Article subdirectory.
Now suppose that Linda creates a Working subdirectory in the Article subdirectory, but she does not want other team members to see the Working subdirectory. To prevent other team members from being able to see the Working subdirectory, Linda simply creates an inherited rights filter to block the group members' inherited Read rights.
Inherited rights and inherited rights filters offer you a high degree of flexibility and simplify the process of controlling who has what rights to files and directories.
Attributes to Success
In addition to this high degree of control you gain with Novell Storage Services trustee rights and its Trustee model, Novell Storage Services on Linux makes available a list of 24 possible file and directory attributes. Of these, 17 attributes are available for external programs to use, including the following:
Do Not Compress
Delete Inhibit
Hidden
Immediate Compress
Purge
Rename Inhibit
Shareable
Execute
(For a list and descriptions of these attributes, see the File and Directory Attributes table.) Standard POSIX-compliant Linux file systems typically offer fewer than half this number of comparable file attributes, including the following:
st_atime (last access time)
st_mtime (last time modified)
st_ctime (last time attributes were changed)
st_size (byte size)
st_blocks (number of 512 byte blocks consumed by this file on disk)
Novell Storage Services directory and file attributes enable you to assign specific properties to individual directories or files. Many of these attributes increase either the efficiency or security of your system.
For example, the Archive Needed attribute, which Novell Storage Services sets automatically, identifies files that have been modified since the last backup. Backup utilities check this attribute to determine which files to back up. If the attribute shows that the file has been modified, then the utility backs up the file. If the attribute shows the file has not been modified, then the backup utility doesn't waste time. Hence, the Archive Needed attribute improves both the efficiency and accuracy of your backups.
No such attribute exists in POSIX-compliant systems. This means that rather than simply checking a single attribute, backup utilities first must search for the time that each file was last modified. Then, the backup utilities must compare each file's last-modified time with the last-modified timestamps stored in the utilities' database to determine which files need to be backed up. At best, this system is a bit sloppy, requiring the backup utility to do more work than it should have to do to accomplish incremental or differential backups.
Reappearing Files
You know what happens when you fail somehow to back up the latest version of an important file? A virus comes along and deletes it (as yet another reminder of Murphy's Law). Fortunately, Novell Storage Services enables you to set a volume attribute called Salvage, which solves the oddly frequent problem of disappearing files. With the exception of Novell's traditional file system, no other file system offers capabilities comparable to the Novell Storage Services volume Salvage attribute.
In most file systems, when a file is deleted, it is not immediately erased from the disk. Instead, the system unlinks the file's data block from the file table. The result is that the file system no longer knows where the file exists or that the file exists at all.
This can occur even in Windows. If you have ever used a Windows OS, you know that when you delete a file from within Windows Explorer or another Windows application, the Windows OS moves the file to a directory called the Recycle Bin. But if you delete a file from a non-Windows application or if a virus deletes the file, the location of the deleted file's data block is removed from the file entry table, as just described.
Tools, such as Norton Utilities, can help you recover these deleted files. If the file was recently deleted, chances are high that you will be able to recover the file data. On the other hand, if the file was deleted days ago, chances are high that you won't be able to recover the data. In this latter case, the system might have already written over the deleted file's data block because that space appears to the system to be available.
If you use Novell Storage Services, you won't need a separate file recovery utility. When users delete a file from a Novell Storage Services volume with the Salvage attribute set, Novell Storage Services enables you to easily recover the file. The better news is that you don't have to: with the appropriate rights, users can restore their own deleted files from any volume for which you have set the Salvage attribute. To do so, users use either the Novell client (available for Windows 95/98/NT/2000/XP) or the NetStorage interface.
You can retrieve files from the deleted.sav directory using the Novell NetStorage interface. The better news is that you don't have to: with the appropriate rights, users can restore their own deleted files from any volume for which you have set the Salvage attribute. To do so, users use either the Novell client (available for Windows 95/98/NT/2000/XP) or the NetStorage interface if they're running Linux.
Included in Novell Open Enterprise Server, NetStorage enables Internet-based access to users' iFolders as well as to network files stored on servers running Novell Open Enterprise Server or NetWare 5 and above. (For more information about the slick Novell iFolder solution which is included in Novell Open Enterprise Server, see Data Where You Want It, Just the Way You Need It.) To access these files, users need only an Internet connection and a standard Web browser (running on any platform). (Users also can access the NetStorage server using Microsoft Web Folders.) When users enter the NetStorage URL and log in, the server returns a list of the directories they are able to access remotely.
Because NetStorage includes a Salvage feature, users can restore deleted files whenever they feel like it, from wherever they are. To do so from within the NetStorage interface, users navigate to the directory from which the file was deleted and select Show Deleted Files from the View pull-down list. From the list of deleted files (indicated as such with strikethrough), users simply right-click the appropriate file and choose Undelete from the pop-up menu.
Of course, at some point, deleted files must be purged, and they are--according to your directions. You can set restrictions on the Salvage attribute to dictate at what point Novell Storage Services should free some of the space allocated to salvaging deleted files. For example, you can indicate that Novell Storage Services should purge deleted files when a volume reaches a certain capacity, say 80 percent. Alternately, you can indicate that Novell Storage Services should purge deleted files that are more than some number of days old, 60, for example. If you are familiar with the Salvage File feature from the traditional Novell file system, you will be glad to see that in Novell Storage Services, deleted files and subdirectories are maintained in the directory from which you deleted them. In contrast, the traditional file system moves deleted files and subdirectories from their original location to a deleted.sav subdirectory. To restore these deleted files, you have to remember the appropriate path. By leaving deleted files in their original directories, Novell Storage Services simplifies the restore process.
The Right Tool for the Job
You might assume that Novell is so enamored by its own file system that it will support Novell Storage Services alone. If that is what you are assuming, you are wrong. On the contrary, Novell supports a number of file systems on Linux. In fact, Novell even provides guidelines to help you select the system best suited for your needs. The bottom line is that Novell will support whatever file system you need.
Each environment has different requirements. For example, if you manage a file system that supports only an Oracle database or a Web application server, then you probably have little need for a file system with the sophisticated access controls that Novell Storage Services offers. After all, only one process (rather than multiple users) accesses the file system. In this case, you should use a file system specifically designed to allow high performance and scalable Oracle support.
Novell Storage Services is ideal for a decidedly different type of environment. With the degree of scalability, security and ease of management that it offers, Novell Storage Services is ideal for environments that share these characteristics: thousands of users share a file system built on volumes storing gigabytes to terabytes worth of data in thousands to millions of files; and the enterprise is in constant flux, as are users' rights to the file system. Novell Storage Services is specifically designed for these workgroup productivity environments, says Jones. As a result, managing such environments, Jones adds, "is an order of magnitude easier ... when you use the Novell Storage Services model rather than a standard POSIX model."
Novell's advice to you is simple: use the best file system for the job. Novell's claim about Novell Storage Services is equally simple: if your job is managing a shared file system in a large network supporting a typical enterprise (that constantly changes), Novell Storage Services is the best file system for the job.
Data Where You Want It, Just the Way You Need It
Whether or not you manage a large network that supports a typical enterprise, as a network administrator, you do manage network users. Because you manage users, you probably have witnessed the histrionics that ensure when a user's hard disk fails or the angst that follows when a needed file is on a user's laptop, nestled snuggly on her still-unmade bed. Through Novell iFolder, Novell helps you to help your users manage their personal files--as effortlessly as they might now mismanage them.
Last year, Novell Product Manager Trent Badger took a two-week trip across the United States that started in Florida on a sunny Sunday morning. Four days before his departure, Badger was not thinking about the adventures awaiting him on his cross-country journey. No, Badger was thinking about his data.
The Wednesday before his scheduled vacation, Badger's laptop hard disk--on which he had his entire data set--failed. Yes, failed. Badger was keenly aware of the months' worth of data that had been on that hard disk, data that included product prototypes that existed no where other than his personal directory. And yet, Badger remained relatively calm.
The secret to Badger's serenity in the face of these dire straights was Novell's slick, simple solution to the universal, pain-in-the-neck problems associated with managing personal data: Novell iFolder 2.1.5.
Included in Novell Open Enterprise Server for both NetWare 6.5 and SUSE LINUX Enterprise Server 9, Novell iFolder 2.1.5 (hereafter called iFolder) ensures that when your home desktop, laptop or work computer fails, you have nothing to fear. With iFolder, you can rest assured that the most recent versions of your data are where you need it, when you need it.
How it Works: Just the Gist
To enable yourself and other network users to take advantage of iFolder, begin by creating and enabling iFolder accounts on the server on which you installed Novell Open Enterprise Server. As you might hope, you don't have to manually create these accounts. At your prompting, Novell iFolder automatically creates accounts based on user accounts in your Novell eDirectory tree.
Once created and enabled on the server, your iFolder account is ready to be initialized. You initialize your account using the iFolder client, which you install on one or all of the computers you use. At the time this article was written, the iFolder client was available only for Microsoft Windows 98/XP/2000. However, an iFolder client for Linux was well on its way, with a scheduled release of first quarter 2005. Plans for a Macintosh iFolder client were also in the works.
Once initialized, your iFolder account is accessible from the iFolder client or from several Web-based interfaces, including the iFolder Web site, Novell NetStorage and Virtual Office.
Client Access
Working on your iFolder files from the iFolder client feels pretty much the same as working on any other file stored on your local hard disk. The difference is that while you work, the iFolder client logs and tracks the changes you make in a local iFolder directory. As long as you remain connected to your network (or the Internet) and the iFolder server, your iFolder data is synchronized with the data on the server at pre-specified intervals.
If you are working while disconnected from the network, then the next time you log in to the iFolder server via the Internet or your network, Novell iFolder synchronizes your data, typically transferring only the changed portions of files. The client checks each files' metadata to determine whether anything has changed since the last synchronization. It then uses the iFolder directory to reconcile changes to files on the client with those on the server, resolving any conflicts by checking time stamps.
Web Access
Of course, you don't always have access to an iFolder client when you get the urge to work on one of your files. No worries: you can access your iFolder account from anywhere you have access to an Internet connection and a standard Web browser.
From the browser, you enter the URL either for the iFolder, NetStorage or Virtual Office server. After you log in, you can view the directories and files in your iFolder account and download any of the files you want to work on. When you have finished with the files, you simply upload them and delete any traces of the files on whatever computer you are using.
So What?
Think for a moment about some of the benefits that Novell iFolder offers you and other end users:
It guards against data loss by automatically backing up local files to the iFolder server.
It enables anywhere, anytime access to the most recent versions of your files.
What about benefits to you and your co-workers in the IT department? Try these:
It helps safeguard users' data from hard drive crashes or other failures. Because in the event of hardware failure, users can download their data from the iFolder server where it has been replicated.
It helps safeguard users' data from server crashes. Because if the server crashes, users can upload their data from an iFolder client.
It simplifies the task of enabling remote access to the users' files.
It helps you help users stay productive.
It grows with your enterprise, enabling you to add as many iFolder servers as you need, each of which supports 2,000 to 4,000 user accounts, according to Novell recommendations.
Trustee Rights
|
Trustee Right
|
Description
|
|
Supervisor |
Grants trustee all rights to the directory or file and any subordinate items. This right cannot be filtered nor revoked. |
|
Create |
Grants trustee the ability to create directories and files and salvage deleted items. |
|
Erase |
Grants trustee the ability to delete directories and files. |
|
File Scan |
Grants trustee the ability to view the directory and file names in the file system structure, including the directory structure from the directory where this right is assigned back to the root. By default, this right is On. |
|
Modify |
Grants trustee the ability to rename directories and files, and change file attributes. Does not allow the user to modify the contents of the file. |
|
Read |
Grants trustee the ability to open and read files, and open, read and execute applications. By default, this right is On. |
|
Write |
Grants trustee the ability to open and modify (write to) an existing file. |
|
Access Control |
Grants trustee the ability to add and remove trustees for directories and files and to modify their trustee assignments and Inherited Rights Filters. |
Coming Soon
In a future release of Novell Open Enterprise Server, Novell plans to include a radical new version of Novell iFolder. At the time this article was written, Badger could provide few details about this upcoming version but did say that it will be a "complete re-architecture" of and share "no common code base" with Novell iFolder 2.1. Badger further noted that the new version "will include the collaborative capabilities that Novell customers are asking for," including, he added, the ability to share iFolders.
The future version of the iFolder client will enable you (and any end user) to convert one or more directories on your workstation to iFolders. After doing so, you can share these iFolders with as many users as you want and can control who among them can modify files within the shared folders. When you share an iFolder, your computer becomes the primary host for an iFolder workgroup. When members in this workgroup connect to your machine, iFolder files on your machine and theirs will be synchronized.
The big news is that this client will be open source software and, hence, available for anyone to use--not just corporate customers. Even home users will be able to download the free client from iFolder.com. The equally big news is that you will not need to set up or connect to an iFolder server to do any of this.
Of course, you will still have the option to add an iFolder server to the iFolder workgroup equation. With an iFolder server in the picture, you gain the convenience of being able to share your iFolders with any user in your corporate LDAP directory. You also gain the benefit of automated backups and the ability to fully restore your personal files.
If you have access to both the future workgroup version of the iFolder client and the traditional iFolder server, you gain more replication options. For example, in this case, you can opt to have one set of workgroup iFolders replicate across only the computers that you use. You can simultaneously replicate different iFolders on each of your computers to the iFolder server for backup purposes.
The Rest of the Hard Disk Story
Remember Badger's failed hard disk? As it turns out, Novell IT was able to get Badger a replacement hard disk drive by Friday morning--just in time for him to put things in order before his trek across the country.
After installing the operating system and applications he needed, Badger installed the iFolder client, connected to the network and watched for the next several minutes as his entire iFolder directory was replicated back to his new hard disk. "I cannot tell you how relieved I felt," says Badger. "I had no way of otherwise replicating months of work that would have been lost." iFolder in this instance saved the work, saved the day--and saved the trip.
File and Directory Attributes
|
Trustee Right
|
Description
|
Applies To
|
|
Archive Needed |
Identifies files that have been modified since the last backup. Assigned automatically. |
Files |
|
Copy Inhibit |
Prevents Macintosh users from copying a file. Overrides Read and File Scan trustee rights. |
Files |
|
Do Not Compress |
Keeps data from being compressed. Overrides settings for automatic compression of files not accessed within a specified number of days. |
Directories and files |
|
Delete Inhibit |
Prevents deletion of directory file. Overrides the Erase trustee right. |
Directories and files |
|
Do Not Migrate |
Prevents directories and files from being migrated from the server disk to another storage medium. |
Directories and files |
|
Do Not Suballocate |
Prevents data from being suballocated. |
Files |
|
Hidden |
Hides directories and files so they cannot be listed using the DIR command. |
Directories and files |
|
Index |
Allows large files to be accessed quickly by indexing files with more than 64 File Allocation Table (FAT) entries. Set automatically. |
Files |
|
Immediate CompressNormal |
Sets data to be compressed as soon as a file is closed. If applied to a directory, every file in the directory is compressed as each file is closed. |
Directories and files |
|
Normal |
Indicates the Read/Write attribute is assigned and the Shareable attribute is not. Default attribute assignment for all new files. |
Directories and files |
|
Purge |
Flags a directory or file to be erased from the system as soon as it is deleted. Purged directories and files cannot be recovered. |
Directories and files |
|
Rename Inhibit |
Prevents the directory or file name from being modified |
Directories and files |
|
Read Only |
Prevents file from being modified. Automatically sets Delete Inhibit and Rename Inhibit. |
Files |
|
Read/Write |
Allows you to write to a file. All files are created with this attribute. |
Files |
|
Shareable |
Allows more than one user to access the file at the same time. Usually used with Read Only. |
Files |
|
System |
Hides the directory or files so they cannot be seen by using the DIR command. System is normally used with OS files, such as DOS system files. |
Directories and files |
|
Execute |
Prevents the file from being copied, modified or backed up. It does allow renaming. The only way to remove this attribute is to delete the file. Used for program files such as .exe or .com. |
Files |
Who Knew?
Every couple of years, the School of Information Management and Systems at the University of California in Berkeley studies how much new information the world is storing on a variety of media.
According to the school's latest study, titled How Much Information 2003? the world stored as much as five exabytes of new information on magnetic storage media (primarily hard disks) in 2002.
Five exabytes, as you can guess, is a lot of information--equivalent, in fact, to 37,000 libraries with book collections as large as the Library of Congress collection. If the 17 million books in that collection were digitized with full formatting, the result would consume roughly 136 terabytes. To equal even one of those terabytes, you'd need 50,000 trees worth of printed pages--and you'd need 1,000,000 terabytes to equal only one exabyte.
Arguably more important in this context, the school's researchers also reveal in this study the growth rate of new information, which is surprisingly high. Between 1999 and 2003, the amount of new information the world stored grew about 30 percent each year. (For more information, see the study online.)
Assume for a moment that the rate of information growth on your network matches the world's rate. (This might be a stretch, but humor me.) In this case, if your network stored 10 terabytes of information last year, then within five years, your network's seams will be bursting with nearly 30 terabytes--that's three times the size of the U.S. Library of Congress print collection. (For more information, see Data Powers of Ten by Roy Williams of the California Institute of Technology.)
Now For Something Completely Different
Novell Storage Services brings to Linux a load of capabilities that other Linux file systems simply do not have--too many features to discuss adequately in this article. Here is a brief look at some of the other capabilities you will find only in Novell Storage Services:
Novell Storage Services efficiently manages files identified by many different namespaces Like the traditional Novell file system, Novell Storage Services offers native support for Unicode and supports multiple namespaces, namely UNIX (case sensitive), 8.3 DOS (case insensitive), Windows Long (case insensitive) and Macintosh (case insensitive) namespaces. The name-mangling algorithm that Novell Storage Services uses efficiently manages and uniquely identifies millions of files with similar long names in a directory. In contrast, Linux (and other) file systems begin to slow considerably when managing more than only 5,000 files in a subdirectory.
Novell Storage Services enables you to set space restrictions on directories Like Linux and other file systems, Novell Storage Services enables you to limit the amount of space that a single user can consume in a volume. Unlike other file systems, Novell Storage Services also enables you to limit the amount of data a directory or subdirectory can hold--regardless of who creates that data.
Novell Storage Services offers built-in data shredding capabilities Novell Storage Services enables you to set the Data Shredding attribute for Novell Storage Services volumes. When you do, you indicate that the system should apply data shredding to files deleted or purged from this volume. Data shredding hides deleted and purged files by overwriting them with random patterns of hexadecimal characters. Data shredding really erases deleted and purged files, making it impossible for unauthorized users to use a disk editor to access them. This data-shredding tool supports as many as seven data shred patterns over deleted data which meets U.S. government requirements. While other file systems offer add-on features to allow for data shredding, no other file system has this capability built in.
Novell Storage Services tracks and logs files and their metadata to the Event File List Using the Event File List, Novell Storage Services can report to information life-cycle applications about the usage of and changes in the file system under normal operations. The Event File List is the basis for Novell's File Archive and Versioning feature, currently available in Novell Open Enterprise Server for NetWare 6.5 and promised for a later version of Novell Open Enterprise Server for Linux. The File Archive and Versioning feature enables users to restore specific versions of closed or deleted files.
Overbook 'Em
Novell Storage Services enables you to create storage pools from free storage space available on different storage media, including hard disks and storage area networks (SANs). You can then create an unlimited number of logical volumes to share each storage pool.
For each of these volumes, you can set a hard-size limit--but you don't have to. Instead, you can allow the volume to grow dynamically to the pool's size. In any case, Novell Storage Services volumes consume only the amount of space they actually use, which means that you do not have to be clairvoyant to effectively allocate space.
Suppose, for example, that you need to create four volumes: A, B, C and D. These volumes will share a 250 GB pool. Rather than stewing about which volume is likely to require the most space, you can overbook the pool, setting each volume's quota at 100 GB. If Volume A quickly reaches 100 GB and appears to be growing strong while the other volumes are content with only 10 GB to 20 GB each, you can increase Volume A's quota and let it grow away.
Of course, you can probably imagine where overbooking might cause problems: if all four volumes eat up all the space available in the pool, users cannot create files in any volume. However, you can set new quotas for the volumes or expand your pool, if necessary--and have the time and tools to do so. The point is that Novell Storage Services allows for easy, flexible allocation of available storage space.
* Originally published in Novell Connection Magazine
Disclaimer
The origin of this information may be internal or external to Novell. While Novell makes all reasonable efforts to verify this information, Novell does not make explicit or implied claims to its validity.