An Introduction to Novell's Open Security Architecture
Articles and Tips: article
Senior Research Consultant
Novell Research
DR. ROGER R. SCHELL
Senior Development Manager
NetWare Products Engineering
CARL F. ALLEN
Manager, Security Components Business Team
NetWare Products Management
01 Aug 1994
Customers need security for microcomputer networks, and vendors want to supply it. Yet there is one basic problem facing both customers and vendors: how to evaluate system security. Customers need to know that security services are available, and have the assurance of protection for their data. Vendors need a constant measuring stick to compare their efforts against. This AppNote describes the direction Novell is taking in defining an Open Security Architecture that will provide the requisite security environment for networks. It also discusses the National Computer Security Center (NCSC) validation requirements and how the criteria outlined in the U.S. government's Trusted Network Interpretation (TNI) document are applied to NetWare.
- Introduction
- A Larger View of Network Security
- Key Services for Global NetWare Security
- NetWare 4 Class C2/E2 Evaluation
- Novell's Open Security Architecture
- Summary
Introduction
As networks proliferate, there is increased exposure of critical components and data to inadvertent modifications or deletions, unauthorized access, and outright attack. Novell recognizes the customer's need to protect vital data and has implemented many security features within the NetWare operating system. With the technological advances achieved in NetWare 4, these security features are being significantly enhanced to make it possible to build trusted computing systems. Yet the problem remains: how can the security of a network system be properly evaluated to ensure that it meets the customer's requirements?
This AppNote describes NetWare's security features -current and future- and introduces Novell's Open Security Architecture, which provides a model "Trusted NetWare" system for validation by U.S. and European agencies. The AppNote also explains some of the potential customer benefits of such an architecture.
This is the first in a series of security-related AppNotes that will augment the information contained in the Novell Cooperative Research Report entitled "Building and Auditing a Trusted Network Environment with NetWare 4" published in April 1994. Readers are referred to that report for more details on NetWare 4 security features, NetWare Directory Services (NDS) rights and attributes, security policies, and network auditing procedures.
A Larger View of Network Security
As a leading provider of specialized and general-purpose network operating systems and network application programming tools, Novell considers it critically important to include security features in its operating system products. In addition to high-performance file and print services, the NetWare operating system provides general services to support network process architectures such as client-server, peer-to-peer, cooperative processing, and distributed processing. It is essential that Novell provide security services from within NetWare to support these architectures.
As applications mature, developers rely more heavily on security features provided by the operating system. Without internal security services, developers would be faced with supplying their own security models or having to license compatible security technologies from other vendors. As developers well know, you cannot build rock-solid security on a foundation of sand. Services such as encryption and authentication must be available within the operating system.
Server security features alone may not be sufficient to protect vital data on a network. Given the numerous client operating systems (including the many variants of DOS, Windows, OS/2, Macintosh, and Unix) that are compatible with NetWare, it is becoming increasingly important to provide a complete security solution which includes the client platforms (see Figure 1).
Figure 1: Because of the numerous client operating systems NetWare supports, security must include client platforms.
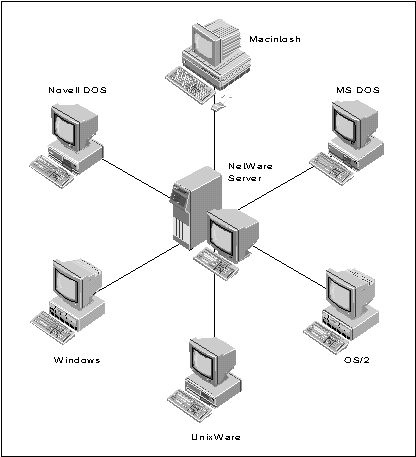
The remainder of this AppNote discusses the steps Novell is taking to provide a complete network security architecture that includes both servers and clients, will give developers the services they need to build secure applications, and will allow new hardware and software components to be added.
Key Services for Global NetWare Security
For years, NetWare has provided a number of services that form the foundation for network security. These include authorization and access control services for the login process and for the file system directories and files. In addition, Novell has provided administration utilities for managing and controlling security. With this security foundation in place, Novell customers have been able to erect barriers against intrusion into their information networks. These barriers help prevent unauthorized individuals from logging in to the network, accessing and modifying bindery information, and tampering with sensitive data contained in system directories and files.
In addition to providing security at various levels, NetWare has provided a high level of system reliability through numerous fault tolerant features. These include:
Read-after-write verification
Hot Fix
Disk mirroring and duplexing
UPS monitoring
Transaction Tracking System (TTS)
System Fault Tolerance (SFT)
Storage Management System (SMS) backup services
Today these services and features are an integral part of NetWare 4. The addition of NetWare Directory Services, Virtual Loadable Module (VLM) DOS Requester client software, and other security enhancements (authentication, auditing, and encryption) brings NetWare to a new level of data protection. The following sections briefly describe the key services for implementing NetWare security in a "global" network environment.
Administration
The security controls embedded into NetWare are administered with utilities designed to facilitate the setup of new users. With these tools, both users and accounts can be controlled based on the rights and relationships set up with the administration utilities. The setup can be based on sound organizational policies and procedures.
Figure 2 lists some of the administrative utilities available in NetWare 4 for managing users, servers, NDS, storage, printing, and backups.
Figure 2: Administrative utilities in NetWare 4.
|
Category
|
Utility
|
Description
|
|
General Administration |
NWAdminNETADMIN |
Allows the administrator to create NDS objects (users, groups, printers, and so on) and assign propertyvalues and rights. |
|
Server Management |
SERVMAN |
Lets the administrator change SET parameters in the server .NCF files, and view storage device,volume, and network information. |
|
MONITOR |
Providesserver status and resource utilization information. |
|
|
NDS Management |
DSREPAIR |
Repairsand corrects problems in the NDS database. |
|
DSMERGE |
Allowsthe administrator to merge the roots of twoseparate Directory trees. |
|
|
Storage Management |
SERVER |
Provides varied administrative functions-including commands to display disk device information,scan for disk hardware that has been addedsince the server was last booted, confirmwhether requests to insert and remove mediain the server have been satisfied, and displayall mirrored logical disk partitions andtheir status. |
|
VREPAIR |
Correctsvolume problems, such as corruption of theFile Allocation Tables or Directory EntryTables. |
|
|
CDROM |
Allowsthe server to use a CD-ROM disk as a read-onlyvolume. |
|
|
Printing |
NPRINTER |
Allowsany printer to be used as a network printer. |
|
Backup |
SBACKUP |
Completesthe backup and restore requests directedto it from the network. |
Access Control
Access control is an integral part of the NetWare file system structure and NDS. Access controls use authentication information -who the users are- to determine what functions users can perform. Administrators can thereby control users and groups needing access to resources, such as data and programs that reside in files and directories. They can also protect all the objects at the server level from unauthorized access.
Trustee rights can be assigned at the directory and file level for users and groups. These rights assignments, together with assigned attributes, can restrict a user's access to specific directories, files, print queues, and job queues. In many environments, this set of trustee rights and attribute assignments is called an Access Control List or ACL.
NetWare Directory Services
Along with basic NetWare security features, NetWare 4 includes NetWare Directory Services, a global, hierarchical database for naming and referencing entities on the network. As shown in Figure 3, the NDS schema defines the objects and attributes that can exist in the Directory Information Base (DIB).
NDS objects and their associated attributes are the focal point for security in NetWare 4. The security functionality for NDS objects and attributes is implemented using access control, inheritance, and security equivalences. Access control and inheritance are governed by the Access Control List (ACL) attribute. The ACL attribute specifies what objects have rights to access and modify an object and its associated attributes. The ACL attribute also governs the inheritance of rights to objects and their attributes. Security equivalences allow one object to receive the same rights as are explicitly assigned to another object.
Figure 3: The NDS schema defines the structure of the Directory Information Base (DIB).
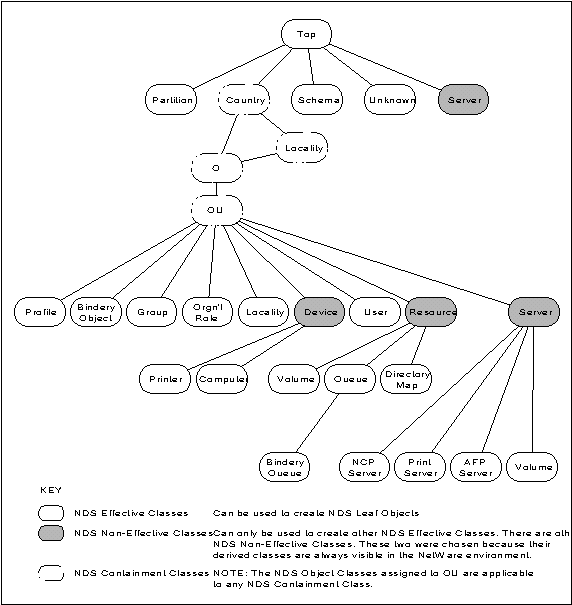
The NDS administrative tools and utilities facilitate the implementation and management of enterprise-wide security. These utilities provide administrators a simplified way to manage the security privileges of globally-defined network users.
Authentication Services
Authentication services verify the validity of a user for each login and for each attempted access to other network resources. NetWare 4's NDS authentication services use the RSA public key encryption technology. The authentication mechanism, which is a critical part of login security, uses the private key attribute to verify a user's identity. Ongoing (background) authentication is transparent to network users and takes place as required when users access other resources. Only during login (user ID and password exchange) is the user aware of authentication. The remainder of the session is authenticated as a network service.
Since authentication in NetWare 4 is session oriented, a client's signatureCthe basis of authenticationCis valid only for the duration of the current login session. The signature itself is never transmitted across the network. Thus authentication services between servers and clients can be mutual and ongoing. Both sides of a session can be required to authenticate themselves, and the authentication process can proceed throughout the session.
Other applications can use NetWare 4's authentication service infrastructure and APIs to set up authenticated sessions between their own services and clients.
The combination of NDS and authentication services provides the mechanism for a "single login" capability. This allows a user to log in to the network, rather than to individual servers. Figure 4 illustrates the sequence involved in establishing a connection between a client and a NetWare 4 server and authenticating that connection.
Figure 4: NetWare 4 authentication services come into play during the login process to establish the user's identity.
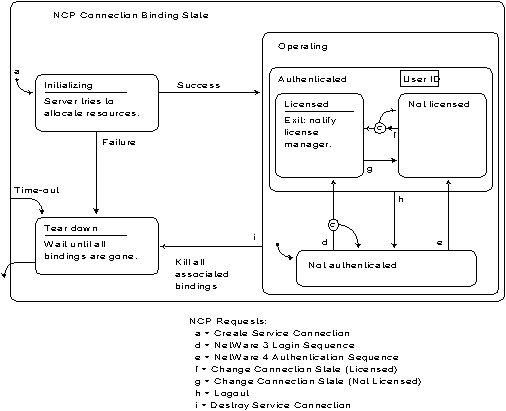
Audit Services
Auditing is the process of examining an organization's records to ensure that transactions are accurate and that confidential information is secure. System auditing refers to the recording and reporting of significant events which occur on a system. The collection of records is referred to as an "audit trail." NetWare 4's audit services allow individuals to act independently of network supervisors, administrators, or users in auditing both past and present transactions on the network.
Using the NetWare 4 audit facility, independent auditors can monitor Directory Services transactions related to security such as logins, logouts, creation of NDS objects, changes to NDS attributes, trustee modifications, and equivalence alterations. File system transactions (such as creations, deletions, modifications, reads, and writes) can also bemonitored.
Encryption Services
NCP packet signature is a security feature that protects servers and clients communicating via the NetWare Core Protocol (NCP). If NCP packet signature is not activated, a network client may be able to pose as a more privileged client and send a forged NCP request to a NetWare server. By forging the proper NCP request packet, an intruder could gain administrative rights and access to all network resources.
NCP packet signature counters packet forgery by requiring the server and the client to "sign" each NCP packet. The packet signature changes with every packet. If NCP packet signature is implemented correctly on the server and on all of its clients, it is extremely difficult to forge a valid NCP packet.
Future Directions
The current products are a significant step along Novell's path of expanding security services for existing networks, as well as for multi-level security for emerging computer technology environments. The evaluation and development initiatives identified above add to Novell's foundation for increasing security capabilities for the network computing industry. Novell will continue to build on this foundation to meet customer needs for more convenient and capable security services, such as single sign-on for users, AT&T NetWare Connect Services, certificate building, and privacy-based mail. Based on this foundation, additional steps will be implemented to provide multi-level security for the assurance that customers increasingly need for protection against deliberate or hostile attacks, and intentional or unauthorized modification or disclosure.
NetWare 4 Class C2/E2 Evaluation
Beyond supplying the key security services outlined above, Novell has pursued independent validation for a network security architecture under both U.S. and European criteria. Novell's proposal to the National Computer Security Center (NCSC) was accepted in September 1992, at which time work began on meeting the NCSC's rigid requirements for a "Trusted NetWare" product. Novell has selected NetWare 4 as the platform for this process.
Security Criteria Documents
The U.S. Department of Defense has published two main documents that contain their standard requirements and evaluation criteria for trusted computer and network systems:
Trusted Computer System Evaluation Criteria (TCSEC), commonly known as the "Orange Book"
Trusted Network Interpretation of the Trusted Computer System Evaluation Criteria (TNI: NCSC-TG-005), commonly known as the "Red Book"
These documents define seven progressively more restrictive classes of security:
|
Class
|
Description
|
|
D |
Minimalprotection (general access systems) |
|
C1C2 |
Moderatelysecure (majority of commercial systems) |
|
B1B2B3 |
Highlysecure (commercial systems with highly sensitive data) |
|
A1 |
Extremelysecure (government systems) |
The European ITSEC equivalent of Class C2 security is called "F-C2, E2" or just "E2" for short.
|
For more details about these classificationsand evaluation criteria, see Chapter 1 of "Building and Auditinga Trusted Network Environment with NetWare 4" in the April1994 issue of Novell Application Notes. |
The criteria set forth for evaluating a security model revolve around the following principles:
Identification and Authentication (I&A)
Discretionary Access Control (DAC)
Audit
Object Reuse
Assurance
The Orange Book was published in 1985 and deals with standalone systems. The Red Book, published in 1987, applies Orange Book standards to networks and defines optional features, including encryption. A substantial amount of Orange Book evaluation occurred before the Red Book was created. As a result, very few products have been evaluated using Trusted Network Interpretation (TNI) criteria.
Why Novell Chose the TNI
Novell has concluded that the Trusted Network Interpretation is the only network security evaluation document in place with a history of technical soundness and (in our judgement) commercial attractiveness. It poses a standard for evaluating networks-both commercial and public sector.
Since the NCSC created the TNI by interpreting the TCSEC standards for the network environment, the TNI's real power comes from using it as a security evaluation tool. For the commercial customer, the TNI provides an understandable discussion of security features in a complex implementation modelCa model based on the distributed network environment. Within this environment, the TNI answers questions on security. It explains where security is desirable, and upon what basis components should be evaluated.
Novell looks to the TNI for guidance in two major areas:
Conceptual modeling
Design and engineering documentation
For us, the TNI is both a basis for designing network security and a way of providing commercial users with understandable documentation. It allows us to handle the introduction of heterogeneous platforms - DOS, Windows, OS/2, Unix, and Macintosh - to the network, along with hardware and software provided by other vendors.
We have chosen the TNI as the logical starting point and accept the rationale underlying its creation. After carefully reviewing it, we recognize that the TNI is far more than a compilation of government-ese. It is a sound technical document. If it did not exist, we would have to accomplish the task of creating it. That would require us to reveal, examine, and provide rationale for an entire NetWare system - not just the relevant components.
While the TCSEC provides the criteria for evaluating a component or a whole system, the TNI allows us the advantage of evaluating confidently each of the security architecture interface points within a component or set of components belonging to the network environment.
There are sets of security properties for both protection and assurance. A customer's system can fail to provide the requisite security in two ways:
The set of criteria is adequate, but the product does not meet the criteria. (This is the type of evaluation the NCSC is doing today.)
The product accomplishes what you were trying to do, but the criteria are insufficient for evaluating that.
This second point underscores the importance of the TNI. When evaluation criteria are based on known security holes, new components may be introduced for which those holes don't apply. The TNI allows us to review new components, identify the interface points, and focus our evaluation on the strength of mechanism at each interface. This allows Novell to participate in an incremental evaluation.
Novell's approach to meeting the Class C2/E2 requirements is significantly different from other vendors' approaches. Novell recognizes that a trusted network can be built using trusted components, and that customers need the assurance of a trusted network - not just a trusted server. To responsibly address our customers' needs, Novell recognized we would have to do two things:
Provide security information and criteria for ourselves and for our customers.
Produce a product which offers features to meet those criteria.
Products currently under development are designed to enhance security with compliance to the TCSEC requirements at Class C2 for NetWare, and at Class B2 for UnixWare.
Novell's Open Security Architecture
Evaluation under the TNI calls for the Network Security Architecture to identify the security-relevant policies, objectives, and protocols. Additionally, the Network Security Design is called upon to specify the interfaces and services provided by the overall trusted network system. The Network Security Architecture and Design (NSAD) is a system-level design document whose content and format is specified in the TNI. For evaluated components, the NSAD has traditionally provided the description of a larger network system, depicting how the evaluated product fits into this targeted architecture. It describes how the full network system can be the set of security requirements at the targeted level of trust.
Using Novell's open network perspective, Trusted NetWare is a complete network system and not a component within a larger network. Trusted NetWare does not depend upon external components to satisfy TNI requirements.
This does not mean that Trusted NetWare will be the only component in the initial evaluated configuration. The open network architecture is intended to facilitate the development of components which fit within the Trusted NetWare framework. Novell sees the need to assist developers, integrators, and accreditors in producing new server and client products in the open architecture.
Figure 5: The Trusted NetWare Open Security Architecture provides a flexible model for a trusted network.
There are several ways to increase the population of developers and products in the open architecture. However, it is essential to keep in mind that Novell intends to add new versions of the evaluated products - both hardware and software -in a model that permits the easy re-evaluation of new components without requiring direct Novell assistance. This model will allow developers and integrators to develop candidate products for subsequent evaluation in accordance with the open architecture. Thus by using Novell's published interface specification and allowing an initially componentized facility at the workstation, products can be submitted for evaluation either by the integrator or by Novell. Finally, accreditors may use this open architecture as a road map for authorizing the use of unevaluated components in the NetWare environment. which produce new configurations.
Open Architecture Definition
The open architecture is based on the concept of a Network Trusted Computing Base (NTCB) that contains all hardware, firmware, and software responsible for enforcing the Trusted NetWare security policies. The TNI describes the decomposition of a trusted network into devices which perform specific functions within the overall network. Each of these components has an NTCB partition that contains the parts of the NTCB within the respective components.
Client-Server Model. The Trusted NetWare open security architecture is based on a simple client-server computing model. This model defines three types of network components: clients, servers, and the network medium that provides the communication between the client and the server (see Figure 6).
Figure 6: The open security architecture defines two main types of Trusted NetWare components: servers and clients.
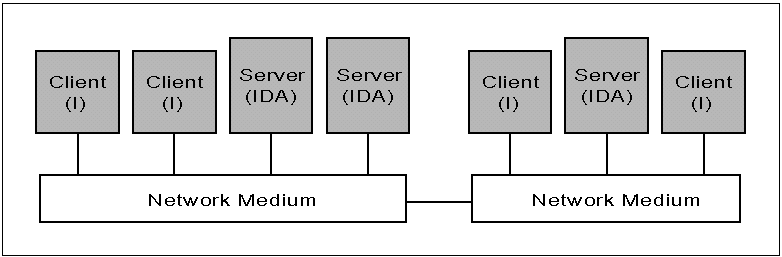
Note: In this figure, "I" stands for identification and authentication, "D" for discretionary access control, and "A" for audit.
Under this model, the server provides services - for example, file, storage, print, or communication services - which are invoked by a remote client using a common service protocol. Client operating systems or applications invoke services by making requests to the server and waiting for the server's response.
The open security architecture permits a wide variety of hardware and software platforms for Trusted NetWare severs and clients.
Network Architectures. The open security architecture is based on a NetWare 4 network model which supports both local (departmental) and wide area (enterprise-wide) networking. Enterprise networking allows a large, geographically distributed organization to tie together all the resources within its organization into a single internetwork.
Two key features of Trusted NetWare (TNW) are involved:
TNW servers (which contain an integral router)
A distributed management database
With an integral router, a server can route internetwork packets from one LAN segment to another LAN segment, or onto a long-haul circuit to another server. NetWare 4's Directory Services contains a distributed management database known as the Directory Information Base (DIB).
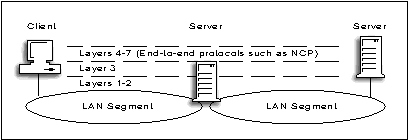
Although enterprise networkingis integral to the Trusted NetWare open architecture, the initial evaluated configuration is used to support an internetwork model of connected Ethernet LAN segments (see Figure 7).
Figure 7: The initial evaluated configuration involves a server's internal router connecting LAN segments.
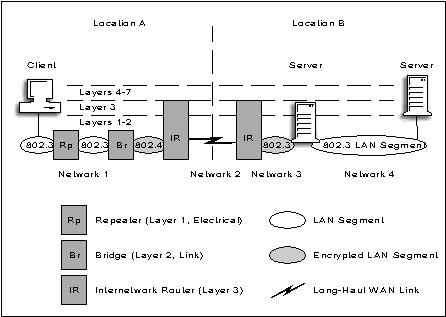
Even though the evaluated configuration does not contain capability for long-haul,wide-area networking, these can be added with externally evaluated components to complete a WAN (see Figure 8).
Figure 8: Network Security Architecture and Design (NSAD).
Trusted NetWare Server Architecture
The open architecture of the Trusted NetWare server is based on NetWare version 4 (NetWare 4). After completion of evaluation, an evaluated release of NetWare 4 will be available and maintained.
The open architecture permits the following changes in the server component:
New processors can be added to the server
New NetWare Loadable Module (NLM) software can be added
New peripherals can be added
These changes to the server architecture allow for an expanding software and hardware basis within Trusted NetWare.
Figure 9 lists possible hardware configurations that may be evaluated with the NetWare 4 operating system.
Figure 9: Several hardware platforms may possibly be evaluated with NetWare.
|
Platform Vendor
|
Processor
|
|
Compaq and others |
Intel Pentium |
|
Apple/IBM |
PowerPC |
|
DEC |
Alpha |
|
IBM |
RS/6000 |
The addition of new NLMs to the server will provide new functionalities - perhaps electronic mail or relational database functions. Of course, the open architecture requires that this new software be compatible with the security policies defined for the server.
The open architecture also permits the use of several physical network media, and an extensive collection of expansion boards and peripherals. For example, new storage devices, printers, and network interface cards can be added at the server. Addition of new peripherals will most likely be performed during updates to the evaluation. These updates will allow for the continued, incremental re-evaluation of the Trusted NetWare product.
Open Client Architecture
While the open architecture for the server is central to Novell's security plan, it is the open architecture of the client which is key to long-term success. Because Trusted Netware allows a broad range of client components, several vendor integrator possibilities are present. However, these will require specific client component provisions, including:
Self protecting and non-bypassable NTCB partition
Compatibility with the network protocols used by Trusted NetWare servers
Enforcement of the security policies allocated to a client
The Trusted NetWare client architecture permits the following types of changes to client components:
New processors can be added to the client
New peripherals can be added
Integrators may develop new client operating systems
Integrators may submit different client security software
While Novell initially is submitting one workstation using only one type of assurance (the Cordant ASSURE Card), many other possibilities are available for vendors and integrators.
Since we are using the TNI to evaluate the whole system, integration between the components can be evaluated. The TNI allows us to review the system components and discern what part (if any) of identification and authentication, audit, and discretionary access control they involve. Our evaluation can then focus on the strength of mechanism at the interface points.
Benefits of the Open Security Architecture
The Trusted NetWare open security architecture offers the following benefits to Novell customers:
It allows organizations to rightsize business-critical applications to the NetWare platform.
It offers mainframe-level security with the cost benefits of a network.
It creates administrative tools to maintain controlled access protection.
It meets corporate data security and audit requirements.
It provides directory, authentication, security, and audit APIs for developers.
It enables organizations to build trusted, reliable, auditable enterprise networks.
Summary
NetWare 4 is a product designed to meet the complete networking security needs of individuals, workgroups, and enterprises. To this end, Novell has strengthened the NetWare security foundation and added enhanced security and audit services. Particular to these security services are Directory Services, authentication, audit, and encryption services capabilities. NetWare will continue to be enhanced to keep pace with new technology and new security needs.
Novell selected the Class C2/E2 security baseline as both a government and commercial industry standard for "good, practical security" and applied these principles to the development of NetWare 4. The end result is a comprehensive set of security services, tools, and complementary third-party products that provides NetWare users and developers the ability to secure their networks with established and certified security standards.
Novell is working with customers, partners, and security experts worldwide to continually define and enhance the NetWare open security architecture model. Novell is committed to understanding changing customer and industry requirements to integrate the security of its operating system products to meet future demands.
* Originally published in Novell AppNotes
Disclaimer
The origin of this information may be internal or external to Novell. While Novell makes all reasonable efforts to verify this information, Novell does not make explicit or implied claims to its validity.