Chapter One: Security Overview
Articles and Tips: article
01 Apr 1994
- Security Overview
- Major Audit and Security Concerns
- Network Technology Overview
- Trusted Computing and Networking Specifications
- NetWare 4 Security Models
- NetWare Security and Audit Highlights
Security Overview
Computer security has long been a concern for government and business. With the introduction of networks into the computer system security picture, the security issue is more important now than ever before. This chapter provides an overview of networks and network security and the various levels or classifications of security recognized by both government and business entities. It also introduces five security models that provide examples of progressive levels of protection.
Historical Perspective
Twenty-five years ago marked a change in mainframe operating systems. At that time, IBM, Digital Equipment Corporation, and others launched a major effort to implement active security within their operating systems. Representatives from government, the Department of Defense (DOD), and academia proposed features needed to build secure mainframe operating systems.
"In five years we will have secure operating systems..." were the words that echoed throughout the computing industry. Over the years, industry and government have spent billions of dollars trying to achieve the elusive condition of maintaining a controlled and secure place to process, exchange, and store information.
With the recent advent of rightsizing (characterized by some as "downsizing without capsizing"), and as businesses struggle to re-engineer their information systems through the use of client/server technologies, the same security problem has resurfaced. The question now echoing throughout the industry is, "Can network computing, with its mix of desktop operating systems, network operating systems, and multivendor environments, provide a secure environment with secure information?"
To compound the situation, government regulations, transborder data flow laws, security concerns, privacy requirements, and telecommunications deregulation all present numerous implementation, control, and management issues. Modern businesses simply cannot afford increased security and control risks that might disable their business functions.
Traditional mainframe data centers and operating systems provided fortress-like environments in which dumb terminals attached to secure hosts. The migration to distributed computing networks requires that client/server operating systems provide security capabilities equivalent to those provided by host systems. This level of security must become an integral part of network operating systems, so that a person will have to invoke access security and control before being allowed to use network resources. Confidentiality, integrity, and availability are the three major elements that must be properly migrated to and supported in networks.
Due to technological advances in the areas of network capacity, bandwidth, functionality, and so forth, network security can now be achieved. However, close integration between desktop and server operating systems is required in order to have a secure working environment.
The NetWare 4 operating system provides a sound basis for enterprise security with an X.500-like Directory Services component. This, along with extended file system security controls, raises network security to the level of most host implementations. NetWare 4 has been submitted to the National Computer Security Center (NCSC) for C2 evaluation, and to the European ITSEC for E2 certification.
In the future, a unification of Novell's desktop and network operating systems (Novell DOS, NetWare 3 and 4, and UnixWare) will provide a more cohesive operating base. However, this integration of operating systems will take time. Implementing security in a mixed environment today requires cooperative effort. By properly setting up and using NetWare 4, the following can be achieved:
Singular access control
Security standardization
Security interoperability
Security management (centralized and distributed)
Auditability (detective and real-time)
Once this is done, NetWare 4's security features can be more effectively implemented to reduce or eliminate risk and exposure.
The Importance of Network Security
Networks have become the "backbone" of many companies. Virtually all aspects of everyday work are dependent on communications whether it be voice, data, imaging, or any combination that exists now or in the future. This is true with the usage of networks to move and process information and to provide such services as multimedia, telephony, and applications development.
A review of the 1993 and 1994 budgets for various companies indicates the expansion of telecommunications (in particular networks) will be a prime source of budgetary expansion for information technology departments. The shift to the network computing enterprise model will require increased funding and major changes to the way data is handled. Thus, management, security, and auditing must form an integrated working partnership to provide the monitored control necessary for business systems.
In the case of major money center banking firms, it is estimated as much as 40% of the entire information technology budget will be allocated to telecommunications and network technologies. The aggregate sum of money being spent on voice, data, and specialized communications has presently grown about 200 to 300% from the typical average of 5% of the total operating budget in the early 1980's.
The expanded usage of enterprise and global networks with NetWare 4 has virtually eliminated the boundaries for information exchange. Combinations of NetWare 4 and NetWare 3.12 have given the industry the ability to downsize to new technologies offered by microcomputer-based hardware systems and to rightsize with the proper software base.
However, the migration to new operating systems is not without its potential concerns, such as control and security. With the advent of rightsizing, information storage has been concentrated at strategic locations and data processing has been distributed throughout the organizations. This has increased the reliance on data communications and moved the responsibility for the information to the desktop and to the individual user. This migration will have an even greater effect in the future with the coming ability to connect to everything from home or anywhere else via the information super highway.
The complexity of this paradigm is compounded by the fact that PC-based networks have grown up as "technology in a box" and wires in the wall, and have become the norm for the plug and play high tech business environments. As a result, the complexity of a company's telecommunications system, its asset value, and its importance in running mission critical business applications requires a new and unique audit approach and strategy. This strategy is examined and developed in the following sections.
Major Audit and Security Concerns
Telecommunications and network technology impacts a company in many different ways. In a large company, the operation and maintenance of these technologies can require enough resources to be considered a separate company. Having the proper resources for this operation and maintenance can be the difference between doing business successfully or going out of business. Not only does this impact the bottom line, it also controls both internal and external information flow.
Management and the Auditing department must realize that telecommunications growth has always been explosive in nature and that it affects all facets of a company and its clients. An overall strategy is needed to identify threats and risks, and to limit exposure to them. Poor planning prior to migrating to or building a NetWare 4 infrastructure can lead to unmanageable problems in the future. In order to minimize any threats or risks, consider the audit concerns in the following sections.
Strategic Planning
Enterprise network systems require careful planning. It is important to understand the organizational structure and data flow before formulating an implementation path for a Novell NetWare 4 network environment. Chapters 3 and 4 of this report address these concerns by providing a description of the NetWare Directory Service and file system structure features. These are important factors to consider when implementing security and auditing for an enterprise-wide network business solution architecture.
Networks can provide similar, if not better, solutions than are available on the current "fortress" systems. Reliability, performance, control, security, and user satisfaction can be evaluated and implemented at the necessary level of need for any company. Strategic planning is key to achieving this, and requires early involvement by both Auditing and Management.
Security
Security covers the five major areas listed below.
Understanding what protection is available
Identifying specific areas of possible attack
Identifying suitable countermeasures
Instituting (Deploying) countermeasures
Monitoring changes in the system and countermeasures
Computer system security can be divided into elements of integrity, confidentiality, and availability. These elements in turn can be combined to form a system that provides a trusted network operating system to the user. This provides the user with security equal to that provided by data processing and network control centers today.
In order to understand this arrangement, a road map should be generated for every review or audit which delineates the security requirements and provisions on client machines, servers, applications, users, and interfaces. One should clearly define the architecture for the systems development on a client/server based operating environment.
Encryption/Authentication. Using encryption/authentication technology, however advanced, as the sole source of your network security gives users a false sense of security. The use of encryption should be justified. The Audit group should help determine the need for encryption by analyzing risk and data value. NetWare 4 provides selective encryption in the areas of passwords, login procedures, and packet signature. These features are unique and address many issues being raised by concerned companies as they migrate to networks and need to retain a high level of confidentiality, integrity, and access control.
Auditing and Management. The classical concern of whether or not proper management controls are in place is paramount. By expanding telecommunications and operational needs, security and control needs can be overly taxed and create unauditable situations.
Auditor participation is crucial in early design and specification phases to ensure a proper mix of preventive, detective, and corrective management controls.
Distributed computing must be audited as both a business entity and a network system. A new network audit methodology, coupled with an improved automated tool set, is needed.
Security policies must define and examine all aspects of networking platforms. These include, but are not limited to, the following:
Client/server systems and applications
Domestic and international telecommunications facilities
Operations and maintenance procedures
Strategic planning at the component level (hardware, software, communications, and people)
Information services security personnel and auditors need to develop a cooperative, well-ordered approach to examining and analyzing enterprise network computing. This is accomplished by establishing common goals, complementary approaches to security deployment, and audit evaluation. These factors, coupled with product knowledge and good communication with security vendors, will facilitate effective security introduction, implementation, and maintenance.
Network Analysis. Auditors must determine if the business needs of internal users and clients are being satisfied. Implementation and use of new technologies to help in the audit process must be stressed. Cost recovery, inventory control, and network re-engineering provide a foundation for Audit scrutiny.
Additional concerns and specific methods to deal with them are presented in Chapter 4 of this report.
Network Technology Overview
Networks were originally designed and engineered to provide an open path of communication between devices, as suggested by the following definition.
Network: A data communications system that allows a number of independent devices to communicate directly with each other over a physical communications channel for the transfer or exchange of communications, commands, and data.
Figure 1: A typical network is defined as a collection of devices that can communicate with each other.
Networks were originally set up to provide services at the department level of a company. This was achieved through the use of such departmental operating systems as NetWare 2 and NetWare 3. Later, wide area connectivity allowed networks to connect and communicate with the same functionality as mainframes and data centers around the world.
Network Computing
Network computing allows users working on different personal computers, microcomputers, or workstations to communicate with each other via the network. Users can share network resources - such as server hard disks, data, applications, and printers - and use any services provided by the network. These services include such things as large database storage and processing, external communications, specialized image processing, and so on. Beyond that, networks have interconnected desktop computing with powerful host environments.
Enterprise Computing
The next step in the evolution of network computing was the advent of global Directory Services. Users wanted to log on once and obtain access to computing and communications resources no matter where they were. NetWare 4 was developed to meet these needs and to address the security and control threats and exposures that accompany such an operating system. NetWare 4 allows users to login once to the network (rather than individual servers) and to use network resources no matter where they are located on the network. (See Appendix A for a comparison of NetWare 3.12 and NetWare 4.)
Rightsizing
Rightsizing to the NetWare and UnixWare platforms requires dealing with many security and control concerns. Thus, to achieve confidentiality, integrity, and availability goals, consider the following points:
In the next five years, as users are given powerful network computing operating systems supported by more powerful hardware and storage at the desktop, they may have to manage their own security. Will the users be ready? Will they have the right tools to effectively manage their own security? Can this security be monitored and managed remotely?
As the use of NetWare 4 networks increases, will the proper tools be provided to maintain control, availability, integrity, and confidentiality?
NetWare 4 provides NetWare Directory Services technology to the enterprise in addition to the classic file system services provided in NetWare 2, 3, and 4. Many companies systems will support mixed environments of NetWare versions 2, 3, and 4 for the foreseeable future. Work is being done to resolve any incompatibility problems that might arise.
Operating systems can no longer be installed without security. Interconnectivity mandates security as a standard. Security features must be easily understood, implemented, and tested in a NetWare 4 environment.
As more and more people are connected to the network, it is important that network security and auditability become standard. Standards must be consistent across various implementations, and control and security provisions must be in place during current or future migrations from main frame to client/server environments.
Because of constantly changing business environment and security needs, the Network operating system's security features must be compatible with other systems you might use during your transition period. Ensure that network security meets both current and future requirements and standards efforts.
Resource sharing and utilization can be a real challenge in any kind of computing environment. How are resources and services effectively mapped to users? The network operating system must provide interoperability and integration with X.400 and X.500 solutions critical to your business functions.
The current trend to "right sizing" requires an integrated security model. It is important to understand what is provided by Novell and what the software and hardware industry can ultimately provide as add-ons to enhance the network operating system's security and auditability.
Many businesses find themselves in the position of trying to "rightsize" in a world full of experimentation. This may include the early adoption of technologies that provide only part of the answers. Thus, non-fortress operating environments can place a tremendous burden on security and auditing departments, as they are faced with the task of reviewing a dynamic set of facilities and services which are in constant flux.
Network Components
This complex mixture of hardware, software, and communications can be very confusing, with a large number of relatively small components located over a large geographical area. To provide a better understanding of these components, the following sections describe their purpose and uses. This explanation is intended to familiarize the reader with the major components in a NetWare network.
The Network Server and NetWare. The network server is a microcomputer that runs an operating system (such as NetWare) to control its network resources. The server is usually a microcomputer of the Intel x86 variety or RISC chip design, or a specialized "super server" such as a Tricord or NetFrame, with custom high capacity internal bus structures and large-capacity disks. The network operating system coordinates network activities, regulating who can access which files, make changes to data, and use the network resources.
Instead of being stored on diskettes or hard disks in individual PCs, all network files are stored on hard disk drives located on the server(s). The storage capacity of these network disks is typically measured in hundreds of megabytes or even gigabytes. This capacity now approaches that of the central data centers that industry has come to depend on for its existence.
Network Workstations. Workstations are the personal computers on which network users do their work. Workstations are used much like non-networked personal computers - each processes its own files and runs its own operating system (such as DOS, UNIX, or OS/2). The main difference is that network workstations can access files from more than just local drives.
NetWare workstations can be diskless or disk-oriented microcomputers. They use two pieces of software to communicate with the file server: the shell, and a protocol. The shell redirects workstation requests across the network when necessary. The protocol provides a common communication mechanism between the workstation and the network server.
Transmission Media. The transmission media used to connect network stations can take on many different forms, including:
Copper wire (twisted pair and coaxial)
Fiber optic or fiber plastic
Wireless (laser beam, infrared light, microwave, and recently a resurgence of radio wave facilities by such companies as Motorola,Xircom, and NCR)
These types of media differ in their characteristics, advantages, disadvantages, and costs.
With these basic components, information flows between the workstations and the servers. On the local or departmental level, the server is the "host" computer with which the remainder of the network entities interact. The NetWare operating system provides the glue that cements the hardware and software components into a functioning whole. NetWare 4 expands on this level of connectivity to include global access and resource independence. NetWare 4 allows users and their workstations to be connected to the network comprised of different types of servers - file, print, database, application, communications, and so on. NetWare 4 also allows interconnection among any number of networks, thus forming an internetwork. The operating system itself can function as a connecting point in the internetwork through its routing capabilities.
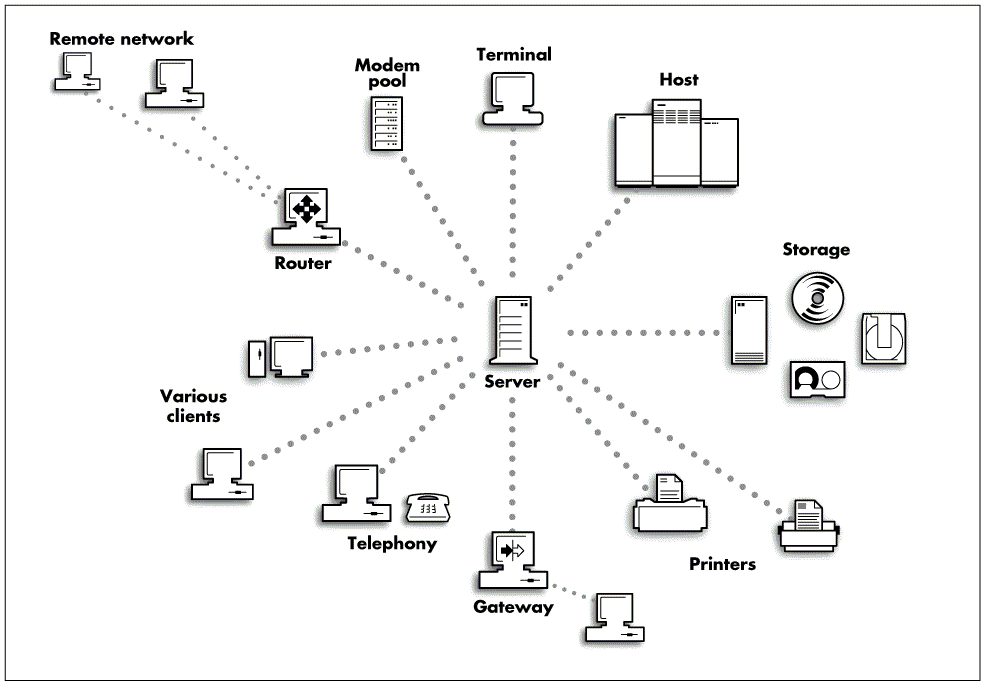
Add-on services can also provide the facilities to run backup devices, external communications via modem pooling, coordinate the functions of different types of servers (such as print or database servers), and communicate directly with mainframe computers. Figure 2 shows what enterprise-wide networking can provide and achieve today.
Figure 2: An enterprise-wide network opens up the network to numerous other services.
Thus, the concept of the local PC network performing a local set of functions for its members has been extended to include the high-volume processing functions of the mainframe and wide area connectivity. Distributed or decentralized computing facilities can now be set up in areas that were once strictly the domain of mainframe and minicomputers.
Geographically localized mass storage, applications, communications, and printing capabilities parallel those available from the centralized data center. As more organizations find increased computing power per dollar as a result of decentralizing, rightsizing is becoming not only a possibility, but often a necessity.
In a distributed environment, data is exposed to numerous threats. The risks must be minimized by building a "trusted" network computing framework. This framework consists of meeting the requirements of trusted computer networks and systems.
Trusted Computing and Networking Specifications
To help you understand how a trusted network environment can be implemented, the following sections summarize the "Trusted Computing and Network" specifications formalized by the U.S. Department of Defense. This is followed by a section on more widely-applicable, commercial view of trusted computing.
Government/Military Classifications
In October 1967, the U.S. government assembled a Defense Science Board task force to address computer security safeguards to protect classified information in remote-access, resource-sharing computer systems. Their Security Controls for Computer Systems report, published in February 1970, formulated policy and technical recommendations for reducing the threat to classified information processed on remote-access computer systems.
This set the groundwork for defining a trusted computer base (TCB) and evaluation criteria that could be applied to commercially available electronic data processing (EDP) systems. The criteria applied not only to the acquisition of EDP systems (and subsequently networks), but to their day-to-day operation.
The classification of EDP and network systems was formulated into two distinct sets of requirements: specific security feature requirements, and assurance requirements. These requirements were codified into a set of standards entitled Trusted Computer System Evaluation Criteria, dated December 1985 (referred to as DOD85 or the Orange Book). These standards were applied to networks in a later document published July 31, 1987, entitled Trusted Network Interpretation of the Trusted Computer System Evaluation Criteria (known as the Red Book) and its companion document, Trusted Networks Interpretation Environments Guideline, published August 1, 1990.
While the government's intention was to provide security for both government and industry, the process became extremely complex. It has had success with few implementations, but those successes came about over an extended period of time. From these proceedings have emerged some highly-developed criteria for building trusted security systems. However, even these are quite complex, and are not readily understood.
Classes of Protection. These documents describe seven progressively more restrictive classes:
|
D |
Minimal Protection |
|
C1 |
Discretionary Security Protection |
|
C2 |
Controlled Access Protection |
|
B1 |
Labeled Security Protection |
|
B2 |
Structured Protection |
|
B3 |
Security Domains |
|
A1 |
Verified Design |
In turn, these classes identify various measures to fit the following six requirements:
|
Security Policy |
An explicit and well-defined security policy must be enforced by the system. |
|
Identification |
Every subject must be uniquely and convincingly defined.Access requests must be checked. |
|
Marking |
Every object must be associated with a"label" that indicatesthe security level of the object. |
|
Accountability |
The system must maintain complete, secure records ofactions that affect security. Such actionsincludeuser setup, assignment, or changeof security level (privilegegroup), and deniedaccess attempts. |
|
Assurance |
The system must contain mechanisms that enforce security,and it must be possible to measure the effectiveness of these mechanisms. |
|
Continuous Protection |
The hardware and software mechanisms that implement securitymust be protected against unauthorized change. |
These requirements are further broken down into specific elements which, as mentioned before, are incorporated in various ways into the D, C, B, and A ratings. This breakdown is depicted in the table in Figure 3 (adapted from the Appendix in DOD85).
Figure 3: Table of requirements for DOD security ratings.
CRITERIA CLASSES Security Policy: D C1 C2 B1 B2 B3 A1 Discretionary Access Control x R R - - R - Object Reuse x x R - - - - Labels x x x R R - - Label Integrity x x x R - - - Exportation of Labeled Information x x x R - - - Labeling Human-Readable Output x x x R - - - Mandatory Access Control x x x R R - - Subject Sensitivity Labels x x x x R - - Device Labels x x x x R - - Accountability: Identification and Authentication x R R R - - - Audit x x R R R R - Trusted Path x x x x R R - Assurance: System Architecture x R R R R R - System Integrity x R - - - - - Security Testing x R R R R R R Design Specification/Verification x x x R R R R Covert Channel Analysis x x x x R R R Trust Facility Management x x x x R R - Trust Recovery x x x x x R - Trusted Distribution x x x x x x R Documentation: Security Features User's Guide x R - - - - - Trusted Facility Manual x R R R R R - Test Documentation x R - - R - R Design Documentation x R - R R R R An "x" means no requirement. A "-" means this class has the same requirements as the next lower class. An "R" means this class has additional requirements over the lower classes.
Currently, Class A exists in several environments, mostly oriented toward DOD-type funded projects which require ultimate security. This level of security is recommended only in the most extreme cases.
Access Control. The Discretionary Access Control (DAC) and Mandatory Access Control (MAC) criteria are important security policy concepts.
DAC allows the owner of a file to set the security parameters for the file. In a UNIX system, for example, a file owner can set the permission bits in the file's Access Control List.
MAC means that the system automatically controls the security parameters of a file through control parameters set by the security officer-the owner of the file cannot change them. However, not all UNIX systems support MAC.
Strength of Mechanism. The "Evaluation Structure for Network Security Services" added the concept of a "minimum strength of mechanism assurance" requirement. The criteria for this requirement are listed in the following table:
|
RiskIndex
|
Strengthof Mechanism Assurance
|
MinimumEvaluation
|
|
0 |
None |
D |
|
1 |
Minimum |
C1 |
|
2 |
Fair |
C2 |
|
> 2 |
Good |
B2 |
Once these requirements were established, manufacturers were encouraged (or mandated by incorporation of these specifications into Requests for Proposal) to produce systems which fit the various categories.
Evaluation. The requirements listed in Figure 3 above are very general. Many systems claim to cover various levels of these requirements. To have any real meaning, a system must be certified for a particular level. In other words, the system must be examined in great detail by a U.S. government agency and certified to operate at a certain security level.
This evaluation process is a long one and it can be expensive for the system developer. The specific tests and criteria are designed for national security installations and may not be completely appropriate for commercial users. As of this writing, NetWare 4 is undergoing the C2 evaluation process at the National Computer Security Center (NCSC), and for an E2 security rating in Europe from the ITSEC.
Evaluation does not guarantee that the security system is perfect. It merely indicates that the security system satisfied the agency performing the evaluation.
Commercial Classifications
The above classifications can be grouped into a finite, functionally-oriented commercial set. Based on the government specifications, industry can select its requirements from the four levels illustrated in Figure 4 below. This is a simpler, more homogeneous approach to trusted systems than the military's hierarchial structure.
Figure 4: A commercial interpretation of security classifications.
CRITERIA CLASSES
D C B A
Security:
Discretionary Access Control x R R -
Object Reuse x R - -
Labels x x R -
Label Integrity x x R -
Exportation of Labeled Information x x R -
Labeling Human-Readable Output x x R -
Mandatory Access Control x x R -
Subject Sensitivity Labels x x R -
Device Labels x x R -
Accountability:
Identification and Authentication x R R -
Audit x R R -
Trusted Path x x R -
Assurance:
System Architecture x R R -
System Integrity x R - -
Security Testing x R R R
Design Specification/Verification x x R R
Covert Channel Analysis x x R R
Trust Facility Management x x R -
Trust Recovery x x R -
Trusted Distribution x x x R
Documentation:
Security Features User's Guide x R - -
Trusted Facility Manual x R R -
Test Documentation x R R R
Design Documentation x R R R
An "x" means no requirement. A "-" means this class has the same requirements
as the next lower class. An "R" means this class has additional requirements
over the lower classes.
The classes can be defined as follows:
|
Class D |
Though currently availableoperating systems have numerous integrated security features, they are usually not enabled or "turned on" during the installation. Becauseof the low level of security provided by this class, we recommend this class of system be avoided. |
|
Class C |
This is the minimum recommended set of security features that should be examined and implemented. This level constitutes a security baselinewith which you can build a trusted systemfoundation. |
|
Class B |
Many corporations have dedicated and non-dedicated systems thatmanipulate and transfer sensitive data. Thisdata, classified as financial, private, or proprietary,is a valued asset. As such, the data shouldbe protected at a level above the normal baselinesecurity level. A compressed Class B generalizationprovides features that offer a better choiceof security and control considerations forthese important cases. This grouping is byno means mandatory or all-inclusive; it simplyoffers recommended practicesfor handlingsensitive data. These recommendations mustbe judiciously applied as best fits each particularcase. |
|
Class A |
This is generally nota commercially viable solution. Its restrictivenature is cost-prohibitive to implement, andthe required overheadmay seriously limitthe processing and communications capabilities ofthe applications systems implemented on thistype of platform. |
Novell recognizes this simplified commercial interpretation. Out of the box NetWare systems fall into Class D, because the security features are not automatically activated during installation. This means that if you install NetWare without activating any of its security features, you have a class D system. It is important to take the time to enable and take advantage of NetWare's strong security features.
Later in this report, we detail the security features available with NetWare 4, and discuss how they might be structured to achieve a trusted network computing environment that can be audited to satisfy the standard Class C and several B security requirements.
NetWare 4 Security Models
Several levels of security can be obtained using NetWare 4. These security models are presented to provide you with examples of the functionality and service provided by each level. The models are progressive in nature, with each focusing on a greater level of protection. These are presented as a skeleton upon which to build your own security implementation. Additionally, you can view each of these models as a stopping point, depending upon the amount of risk you are willing to assume for your own system.
Any attempt at presenting a complete security model presents several difficulties. If your requirements are different than the model, then the level of trust you put into your security may be disproportionate to the actual benefit you expect. This is a difficulty in working with generalized models. However, these models can be used to provide a reference point for your own security model.
The five security models discussed here are:
Simple
Basic
Protected
Audited
Secured
As mentioned earlier, each model builds upon the one proceeding it and covers the following points in succession:
Instituting physical security
Passive warning signs
Passive security measures - includes physical isolation of computer components, and using backup software and off-site storage of data
Changing default NetWare 4
Active use of passwords and intruder detection in NetWare
Active use of Virus detection software
Education of end-users to security concerns
File system file and directory protection
Simple Model
The simple security model is based on not knowing much about security. It can be implemented, if necessary, by an end-user, and can be started anytime. It provides a minimal layer of security. It also provides those direct actions which prevent inadvertent damage to NetWare 4 or to the server and equipment. The simple security model provides a level of security equivalent to a mid-level D commercial security classification.
The simple security model is based upon having adequate backup and archival copies of application software.
One of the simplest security methods is posting a sign stating, "HANDS OFF." Unfortunately, in some environments, a warning sign is not enough to prevent loss or damage. In these environments even the simple physical security provided by locking up servers and essential equipment - in places where they cannot be physically accessed - can be advantageous.
The reasons for implementing physical security are relatively straightforward. You have an investment - in hardware as well as software - and you wish to have uninterrupted use of your investment. Backup software supplies some of this need. Properly using backup software in coordination with offsite storage of backup copies provides some assurance of continued usability in the event of loss. This allows you to recover data files in the event of an unexpected disaster or accident.
End-users are responsible for more recorded hardware and software catastrophes than criminals or disgruntled employees. Of greater importance, end-users usually have guaranteed access to the network server via their local workstation - especially in environments where they do not have to use passwords to gain access to computer resources. Passwords only ensure that your users have access - they do nothing to prevent inadvertent access (file deletions), or subverted access in the form of computer viruses on contaminated disks. Backups are essential.
Even with active methods - physical security (locked containment rooms), passwords, virus scanning - there is no substitute for education. One of the most important security measures is proper education.
Basic Model
The basic security model expands on the simple security model for local area networks, and shows an increased emphasis on user restrictions for file system and Directory Services. It segregates application and data files, seeks to reduce the risk of inadvertent or subverted access, and directs the network administrator to develop a security policy. The basic security model provides a level of security equivalent to a high class D level of commercial security.
In addition to the simple security model presented above, the basic security model seeks to ensure a proper administration function - an administered network with security functions enabled, and someone to review what is actually going on.
The goal of the basic security model is to enable NetWare Directory Services for both system and end-user administration. It proposes file system management for file access, and presents workstation file integrity issues as a realistic objective.
In the basic security model, some attention is given to the workstation components (such as keyboards and floppy drives). The workstation is looked at to see if unauthorized users can accomplish access, and what might be done to prevent this.
One suggestion for prevention of unauthorized access is the writing and implementation of a security policy. In basic security, you should be writing down ideas, and qualifying which are real threats.
Protected Model
The protected security model is actually an audited model without the professional auditors required in the audited model. Protected security turns on the NetWare 4 audit functions and begins gathering information about the system. The audit parts of this report will help you with that. The professional auditors who put together the auditing sections provide a wealth of information which will simplify many arduous tasks. The protected security model provides security equivalent to a low class C level of commercial security.
The protected model relies on education. This education must be more than cursory - it requires actual "hands on" training for password protection, anti-virus procedures, and the organization's personal computer security policy.
An organization's security policy becomes an important part of the network operation, and should be referenced and updated often. In the protected model, details concerning what a loss consists of should be clearly delineated in the security policy.
Education extends beyond the security policy to the operating systems of both the workstation and NetWare 4 where administrators need to understand both NDS and file system administration.
Floppy drives become increasingly important at the workstation level of security. In the protected model, access to workstation floppy drives can be monitored, locked with an access control device, or physically removed. Additionally, the workstation itself can be secured in a locked room when not being used. Workstations then become accessible only by trusted users.
Audited Model
The audited security model is audited by professional auditors. Network activities, installations, and premises are evaluated regularly by professional network auditors. The audited model also mandates the use of security administrators. This model also requires constant interaction between the security administrators and the end-users, as well as between the departments and the auditors. Professional auditing (outside of security), becomes the feedback loop for trusting the computer network. The audited model provides the security equivalent to medium-level class C commercial security.
The major difference between the audited and protected security models is how security policy is affected by the feedback of audits. Individual administrators are responsible for implementing security policy, and the activity surrounding the network is reviewed and monitored.
A workstation monitoring program is necessary with audited security. This program should include labeling and monitoring workstation cabinets and network connections. Keyboards and floppy drives are disabled (or removed and then locked in a drawer or cabinet) when they are not being used.
Security policy exists as a formal document in the audited model. It should have a table of contents, numbered pages, and be under constant review to ensure all pages and updates are present. Auditors may inspect the security policy, the departmental copies, and the signature logs for those responsible for knowing and implementing security standards within the organization. Auditors should also make suggestions for new or updated inclusions within security policy.
Security policy implementation can be expensive and require additional personnel, and can be awkward for department managers and end-users alike. However, if a security policy is ineffective or not implemented, there is the possibility that the electronic data components of your business will be adversely affected resulting in financial loss.
Secured Model
The secured model is different than the previous models. It is based on the premise that someone is actively trying to penetrate the network. The implementation is very different, both in hardware and in personnel as it cannot be implemented by an individual, but requires a professional administrator with security evaluation experience. While this model is not the complete solution for security, it requires network monitoring and evaluation to provide information security and network protection. The secured model provides security equivalent to high-level class C commercial security.
The secure model is based upon a strict adherence to a precisely defined and implemented security policy. It is required that a complete security policy exists and has been distributed within the company. It is also essential that everyone understands their part in the security procedures.
In a secured environment, there is ongoing maintenance and evaluation of deployed countermeasures. Countermeasures are based upon implementing all previous components in lower models, and upon ongoing research to determine if new security threats have achieved a status of credibility. It is also based on the continued intrusive testing of workstations, communications, network servers, and the isolation of trusted users from untrusted components in the network.
The secure model can have any number of users, but is constrained by workgroup isolation, and restraints on external communication through bridges and routers. Access to the physical components of the network is hidden, indecipherably marked, and maintained in a translucent cloak of secrecy. All repairs are done with a security evaluator present.
The secured model is achieved through a combination of NetWare 4's protective features and protective measures which are enabled end-to-end to continue the integrity of the network, and make it infinitely harder to attack.
In the secured model, workstation monitoring is only one component of the security policy. Both workstations and servers are operated with as much security hardware and software as available. Secured routers, bridges, and telecommunications equipment is the norm, not the exception. Monitoring and administration are ongoing.
NetWare Security and Audit Highlights
In bringing the NetWare 4 operating system to market, Novell recognized that customers wanted systems that were easy to implement, provided enterprise networking and excellent performance, and offered "fortress" computing control features in a distributed network computing environment.
Novell now offers extensive security and audit features in NetWare 4 which provide a strong line of defense against threats that arise from common daily errors and focused malicious attacks and network intrusions.
Novell has made major strides in helping network and security administrators, auditors, and users in their quest for a secure system. Security controls are embedded into Novell's departmental network operating system - NetWare 3.12. With the advent of NetWare 4, Novell made a concentrated effort to produce a network operating system that provides a well-balanced and expandable base for enterprise-wide secure business solutions.
In NetWare 4, Novell provides a secure and auditable system that can be managed on an enterprise-wide basis. However, network designers, administrators, and users must activate and use these functions to build a trusted network computing environment at both the local and global level.
NetWare 4 offers flexible, multilevel security that controls access to the network and its resources. These features, which meet several requirements of the D, C, and B classes described above, can be categorized into Directory Service and file system resource management which controls security for:
Network
Access
Login
Rights
Attribute
File Server
Information
These features allow the system administrator to control network security which can be implemented at the Directory Services, network, server, and file system levels to determine:
Who can access the network
What resources (such as file system directories and files) users can access
How users can utilize the resources
Who can perform tasks at the server console
To accomplish this, NetWare 4 provides such security features as:
User identification at the individual, group, and management levels
User authentication (service request-oriented)
Password management, including password encryption
Network resource access control through assigned rights and attributes
Console security to ensure only those with the proper security equivalences have access to the server console
Formal evaluation generally depends upon a combination of hardware and software. Since Novell chose the path of hardware independence, Novell has partnered with several third-party vendors to form strategic alliances that will provide additional security, control, and auditability.
NetWare's security and control features provide the basis for building a trusted network computing system. The utilities and tools available for establishing and monitoring security are described in this report. A baseline equivalent for Level C-type security is recommended as the minimum acceptable setup for a NetWare 4 network. This is based on Generally Accepted Security Practices, the Standards for the Professional Practice of Internal Auditing, and the Systems Auditability and Control (SAC) Report.
* Originally published in Novell AppNotes
Disclaimer
The origin of this information may be internal or external to Novell. While Novell makes all reasonable efforts to verify this information, Novell does not make explicit or implied claims to its validity.