Novell's Approach To Red Book Evaluation
Articles and Tips: tip
Senior Research Engineer
Novell, Inc.
01 Jul 1996
Battling bastions -- Novell and Microsoft, each one fighting for market share. Novell is marketing their Green River operating system as Class C2 compliant, and "Red Book" or Trusted Network Interpretation (TNI). Microsoft went for "Orange Book" Trusted Computer Security Evaluation Criteria (TCSEC) compliancy with a standalone Windows NT Server and NT Client. However, Microsoft's C2 evaluated operating systems are not networkable -- not if it is to still be trusted as having Orange Book security compliancy. Microsoft is saying Novell is not "Orange Book" compliant, and so the marketing wars go on.
While market share and marketing have a lot to do with your perception of security and change what you will or will not buy, there are more important elements to examine and to consider which you as the security buyer must make without being influenced by marketing and marketeers. And independent evaluation (such as the National Computer Security Center) is a good factor to help curtail or diminish marketing hype.
The bottom-line: Security is either in the operating system or it is not. Buyers, sellers, and users need the assurance that the security mechanisms do in fact offer some level of protection, with assured protection at the operating system level. There is no other place in the network to place security services and features other than the operating system if you want any real security.
Let me add that there is more to security than obtaining evaluated assurances. Specifically, there are three areas: Environment, Risk, and Assurance. While this article does not go into detailed examination of Environment or Risk, you can be sure that the potentials for security breach exposed though your computer operating environment (Environment) and the importance of the information that you are concerned about (Risk) are very important factors in choosing the correct operating system software.
The Difference Between Novell's Evaluation for Class C2 and Microsoft's
There is a fundamental difference between Novell's offering to the National Computer Security Center (the NCSC) and Microsoft's. Novell offered an entire network as the evaluation platform, which includes servers, workstations, NICs, and the wire (see Figure 1). Microsoft brought their NT client and NT server -- without NICs, software drivers, or connectivity media -- as two unconnected, unrelated, and separately evaluated units.
Figure 1: Novell has submitted an entire networkservers, workstations, network adapters, and the wire for C2 evaluation. wire for C2 evaluation."
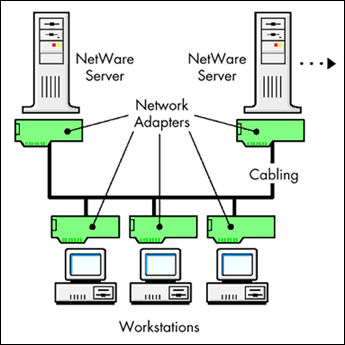
Moreover, Novell has submitted the interaction of the various components which make up the network as the evaluation platform. (Microsoft has only offered the standalone component without the interaction with other network components.) This is extremely important for Novell developers, partners, and other networking manufacturers, since it means Novell's offering is modular, and is built from (not just on) the strength of each component evaluated, guaranteeing the now probable substitution of components. This is partly the intent of "Red Book" evaluation -- to create complete security in each module for that module's intended purpose.
Orange Book defines what security services must exist for any component to be trusted. The Orange Book point of view is as if the component itself were the whole of the evaluation. For example, one could "Orange Book" a single workstation standing by itself like Microsoft did and obtain a Class C2 evaluated rating for a standalone workstation or server. Alternatively, one could submit a configured network with NICs and drivers, and a specified number of workstations and servers. This is the "Orange Book" approach that Novell and Cordant, Inc. have done to provide a network solution to a specific situation, and therefore Novell has used the "Red Book" Trusted Network Interpretation (TNI). However, Orange Book does not apply to a general purpose network. Ordinarily it does not apply to a Commercial-Off-The-Shelf (COTS) solution.
"Orange Book" delineates the level of assurance which can be derived from the evaluated configuration. In Microsoft's case, these were a standalone workstation (not connected to anything) and a standalone server not connected to anything. The point is that Microsoft has a configuration which is Class C2, it is just not evaluated to be networked. This is a very important differentiation, it means you cannot hook up an NT box to anything and still have a Class C2 evaluated configuration.
Red Book Compliance
If Microsoft had done a "Red book" evaluation, they would have had to connect their NTAS server and prove the strength of security mechanisms while operating in a networked environment. Red Book also defines with Orange Book precision how the components should interact in a distributed networking environment in order to maintain "Orange Book" definitions. There are several differentiating aspects to Novell's Red-Orange evaluation. These include:
Comprehensivity
Modularity
Extensibility
COTS
As evaluations go, Novell's Class C2 evaluation is both broad and detailed. It is the first Commercial-off-the-shelf network operating system to apply to the NCSC for TNI evaluation. The design of the network security architecture presented for C2 evaluation was presided over by Dr. Roger Schell, previously Deputy Director of the NCSC and now leader of Novell's Network Security Team, with assistance from and in cooperation with Novell's Class C2 contractor, Cordant. Considering the credentials as well as past proven capabilities of the Cordant team, the team from the NCSC, and Dr. Schell's team, you know how important it is for the world's largest supplier of commercial network operating systems to implement real security services at the operating system level.
Novell's evaluation takes into consideration the entire network, which includes operating system of the client workstations as well as servers, network drivers and protocols. The entire network was documented and these documents, along with the complete test procedure for each security relevant interface, assure that the components work exactly as claimed when evaluated by the independent evaluators of the NCSC.
The Novell approach offers some extremely important features, advantages, and benefits to network operating system buyers. The first consideration is the assurance from Novell company executives that there will be on-going version support for security, for no one wants to buy a "one-rev" solution. Secondly, buyers, developers, and partners all want assurance that Novell will keep its on-going commitment to a completely evaluated security services architecture incorporated in all future releases of Novell NetWare products.
Beyond the longevity of the NetWare Class C2 product release, you must also consider the flexibility and extensibility of the security services at the operating system level as needed by your company. Since you cannot build security services into application software, at least not services which are "secure" without a secure (and underlying) operating system, you must derive security features for client and server from extensible secure operating system -- the client and server as macro modules in security. NetWare documentation for the Green River Release of Trusted NetWare includes over 27 individual documents that describe the individual components of the NetWare security offering.
Modularity and Extensibility
Modular and extensible components are important for a Red Book evaluation by the NCSC. The modular documentation approach of Novell's evaluation also allows a vendor to include their network component, such as a new workstation operating system, in a new evaluation as a Trusted component of NetWare. Novell's security architecture allows the vendor to submit their component along with Novell's other documents without having to do an entire network evaluation, and without Novell having to do the evaluation with them.
With the Green River release, security vendors who would like to place an evaluated component "in-line" with the NetWare solution can insert their new evaluated product into the existing architecture. Modular evaluation components are a great benefit to partners, manufactures and users as they allow new components to be introduced into the NetWare architecture without having to re-evaluate the entire architecture.
This special feature of the NetWare Class C2 evaluation is an important aspect intrinsic to Red Book evaluation. It is an important aspect which Microsoft over looked in its pursuit of getting to the market first instead of offering "real" network security. Microsoft does not have the modularity, extensibility, or COTS in their Class C2 offering.
Weight Factors
The factors described above should weigh heavily in the minds of buyers, sponsors and users of security products. While marketing is a key component to a successful sales strategy, independent evaluation and a networkable trusted technology solution that can be readily installed are more important, not to mention ease of use and installation.
NetWare is commercial-off-the-shelf software today. When you upgrade to Green River, or purchase the Green River release, the security is built-in and operating system defaults will load with a single NetWare Loadable Module (NLM) -- the SECURE.NLM. This version of NetWare is designed to meet all criteria for networked Class C2 requirements.
* Originally published in Novell AppNotes
Disclaimer
The origin of this information may be internal or external to Novell. While Novell makes all reasonable efforts to verify this information, Novell does not make explicit or implied claims to its validity.