Plugging Security Holes
Articles and Tips: qna
01 Feb 2005
No matter how much security hardware and software or how many policies you have in place, you'll probably always have holes. Most often, these security breaches are caused by common end user mistakes and oversights. The following are five common areas that introduce security holes and tips for how a combination of Novell solutions and educated users can plug these holes for good.
Keeping Passwords Safe
Q.
Passwords are a major security issue in my organization. What can be done to make them more secure?
A.
Passwords are the keys that unlock electronic information. But just as traditional locks can be picked, passwords can also be cracked. Although most IT professionals know how to create strong passwords and keep them safe, many users compromise security by choosing weak passwords, writing passwords down, posting passwords on their workstations, using the same password for multiple applications, or telling passwords to co-workers or other unauthorized personnel. In the defense of users, many companies require them to remember several passwords, sometimes one for each application they are authorized to use. If users forget one of these passwords, they waste their time and help desk time to reset the password. Therefore, many users feel it is a necessity to write down passwords or choose easy-toremember words and don't realize that they are compromising company security.
Even Novell solutions can't help plug the holes if users don't follow a few tips on keeping their passwords safe:
Never tell your passwords to anyone. This is always the safest policy to follow. Although there may be exceptions in certain companies, having a policy of never divulging passwords can help protect users from "phishing" and social engineering schemes aimed at gaining access to identity information.
Don't write down passwords. Even if you think your sticky note is well hidden in a drawer or under the keyboard, the fact that it is written down means it can be compromised.
Create a strong password. Strong passwords are at least nine characters long, cannot be found in the dictionary, do not use any numbers or words that may be significant to the user (names, birthdays), and use a combination of upper and lowercase letters, numbers and symbols. Just as there are tools to pick locks, there are software tools to crack passwords. These programs use a combination of actions including trying every word in the dictionary, every combination of numbers, and every combination of numbers and letters. Although password cracking programs may be able to crack even strong passwords, a password with more characters that can't be found in a dictionary and that includes a combination of numbers and letters may take years for one of these programs to crack. Because of the strange combination of characters, many people think strong passwords may be difficult to remember, but strong passwords are easily created by including symbols with the first letters of a familiar phrase or song title, (for example, "Jack and Jill went up the hill" could be "JaJ$Wuth1",) or by changing a few characters in a familiar word (security=53cVr1+y). The key is to choose something you can remember and then convert it into a strong password by substituting other characters.
Change your password often, at least every 30 days. (See Figure 1.) If it can take weeks or years to crack a strong password, a strong password that changes every 30 days should be impossible to crack. When changing a password, users should remember not to use any kind of variation of the previous password (such as VN!+y4A11 to VN!+y4A12) and to create another strong password using the guidelines above.
Figure 1
Do not use the same password for several applications. Although the Novell Nsure solution solves part of this, you should still warn your users not to use a work password for their home computer or vice versa.
Hide or cover the computer monitor and keyboard as well as possible when typing in a password. Others may be watching your monitor or keyboard while you enter a password to count the number of characters and some of the keys you press.
If you suspect your password has been compromised, change it immediately and report the incident.
The Novell Solution
Novell SecureLogin, Novell eDirectory and Novell Nsure Identity Manager work together in the Novell Nsure solution to solve many of these problems. With SecureLogin, users only need one password to log in to all company applications. With only one password to remember, users are less likely to write it down and more likely to create a strong password. A Novell solution also reduces the time necessary to reset a password if a user suspects it has been compromised. Instead of calling the help desk, users can securely reset their own passwords.
Safe Internet Use
Q.
Everyone in our company uses the Internet to do their jobs. What can I do to make sure open access to the Web doesn't breach the security of our systems?
A.
The Internet is a powerful research and contact tool, but access can also create security hazards. Without knowing it, users can download malware, or destructive software, that may spread to the company network. Although most of this malware, such as adware, is more annoying than harmful, inadvertently downloading it still creates security holes. Have your users practice safe Internet usage.
The resources of the Internet seem endless, but many of these same resources cannot be trusted. Because of the lack of Internet regulation on the, some downloads that may seem to solve one problem actually may cause others. To protect your computer from possible Internet bugs, follow these tips:
Follow your company's guidelines about downloading programs from the Internet. Many companies prohibit downloading software, games or even screensavers or toolbars for the simple reason that these programs have the ability to add dangerous add-ins, such as malware, to your computer. If your company does not have these kinds of guidelines, use caution in what you download from the Internet. The simple rule is: when in doubt, don't download. (See Figure 2.)
Figure 2

Carefully read the EULA (End User License Agreement) for each type of software you download. Make sure the agreement does not say the company will share your information with others or add a kind of spyware to let them know about your computing activities. These kinds of agreements open the door for adware and spyware to be placed on your computer potentially exposing personal and company information, even on your network.
Do not use your work Internet connection for personal use. If you need to use the Internet at work, chances are it will be for some type of research. Do not give into the temptation to browse your favorite shopping or entertainment sites at work. Just visiting these kinds of sites can often add identifying information on your computer further jeopardizing information and even your job security.
If you find yourself inadvertently at a restricted site or if a link redirects you to something inappropriate, immediately shut down your computer, unplug the network connection and call the help desk. This action will not only protect your computer, but will help explain any seemingly inappropriate actions that may jeopardize your job.
The Novell Solution
Novell BorderManager helps protect your users and network from inappropriate Internet access. For most companies, shutting off Internet access to your end users, isn't an option. Using the Novell solution, along with educating users about potential Internet problems, can help plug some Internet security holes. As part of the Novell Nsure solution, BorderManager allows administrators to track company Internet use and block unwanted content from ever reaching end users' desktops. Although BorderManager is a powerful content management tool, it does not stop all potential security threats. To further strengthen security, users should follow the previously listed guidelines when using the Internet.
E-mail Precautions
Q.
Most users in our company live in e-mail as their main application. How can I help them not to jeopardize the security of the system?
A.
Like the Internet, e-mail at work has become indispensable. It is the main way co-workers communicate with each other and often with clients and customers. Because e-mail travels in and out of the company network, it can introduce security holes. Although most e-mails are not a threat, the way users view and interact with e-mail messages can lead to virus infections that may harm the company network. Using a Novell messaging solution, as well as following a few simple precautions, can help plug the holes which e-mail may introduce to your company's network.
Have your users follow some simple rules to help plug e-mail security holes:
Never open e-mails or attachments from unknown sources. Although most users know and follow this precaution, they may not realize that just by previewing an email from an unknown source they can potentially download a virus or hoax. To be on the safe side, users should disable any previewing panes and immediately delete e-mails from someone they don't know.
Don't pass along suspicious or even joke email. In company settings, it is often tempting to pass along the latest Internet joke or hoax to a co-worker. Because these jokes are often the method used to transfer viruses, it is best to delete the jokes and use e-mail only for work-related purposes.
If you inadvertently open an e-mail you think may contain a virus, immediately shut off your computer and unplug the network connection. This will reduce the chance of spreading the virus to co-workers.
Because some viruses spread using your address book, be leery of any e-mails you aren't expecting from co-workers that have a suspicious subject. If you aren't expecting a message or attachment, call the person to confirm it's legitimate before opening.
To reduce the amount of spam and junk mail you receive in your work account, set up a separate account for shopping and entertainment purposes. Use your work e-mail account only forwork-related communication.
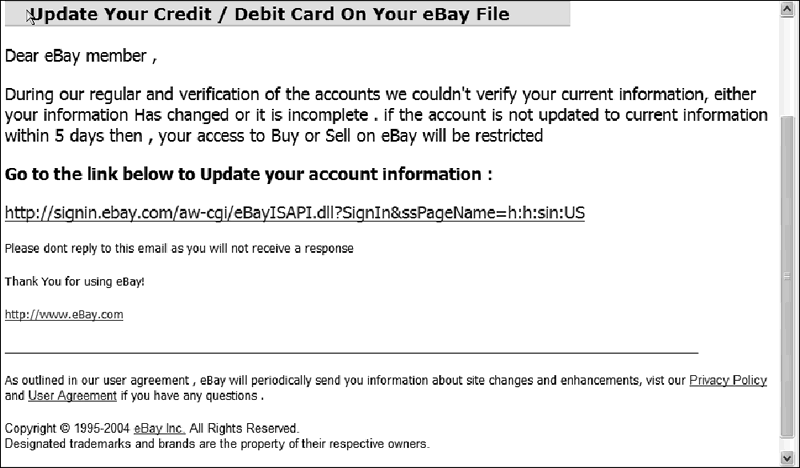
Relatively new schemes called "phishing" or "spoofing" send e-mails that look like they are from a legitimate financial or Internet company and ask for identifying information like account and social security numbers. (See Figure 3.) To avoid being taken in by these schemes, never give out any identifying information in the e-mails or pop-up windows that appear when you click on a link in an e-mail. Check the legitimacy of the e-mail's claim by typing the appropriate URL in the address bar and searching for any information on the email's claim. You may also want to call the company to check the request's legitimacy.
Figure 3
The Novell Solution
Novell GroupWise, Novell's leading communication software solution, solves many of the problems users encounter in securing e-mail. Because many harmful viruses or hoaxes are now launched by simply previewing a message, GroupWise has eliminated the automatic preview window that other e-mail applications like Outlook include. When users can't automatically preview a message, they can control which messages they open and therefore reduce security risks. GroupWise is also equipped with anti-spam and junkmail filters that keep potentially harmful or inappropriate messages sorted away from legitimate messages. For sensitive outgoing information, GroupWise includes an encryption feature and also allows the user to attach digital certificates.
To further protect sensitive information like company organization or payroll reports and information, Novell offers another solution: the Secure Enterprise Dashboard. A company can use this secure interface to transfer reports and private financial information only among those who should see the information. Because Secure Enterprise Dashboard does not use an e-mail client, but instead travels within the company network, managers can be sure the information is safe from security risks. But, as always, there are potential security holes if users don't practice the few security precautions listed above.
Termination Guidelines
Q.
I've been burned by former employees breaching the security of our network. What can I do to guard against this happening in the future?
A.
Popular spy movies make it seem like security breaches come from outside sources gaining access to unauthorized information. Although this sometimes is the case, often disgruntled former employees that still have access to the systems and inner-workings of a company are to blame for attacks or security leaks. The delay in revoking network access and other privileges from these employees, due to the time and bureaucracy involved, can open security holes difficult to patch.
Below are a few things managers can do to reduce the risk former employees may pose:
Immediately contact your HR department to let them know who you are hiring or terminating, so they can immediately erase the person from company rolls and permissions.
Document all employee actions that lead to termination. If you can prove the termination was justified by citing specific actions, the employee is usually less disgruntled and less apt to be a security risk later.
Ask for any security devices such as key cards, ID badges or parking passes at the time of termination. If the employee no longer has access to the physical building, it will be harder for the person to be a security risk.
If you suspect that an employee will be upset at the termination, contact security before termination. Having security on hand in extreme situations can prevent last-minute vengeful security risks.
The Novell Solution
One part of the Novell Nsure solution, Novell Nsure Identity Manager, connects all identifying programs so that entering a termination order in the HR program automatically revokes the rest of the employee's privileges, including e-mail and network access. However, this feature only works if managers communicate with HR.
Anti-virus Software Guidelines
Q.
Even though all our users have anti-virus software installed on their computers, we still have problems with viruses leaking through. What can I do to minimize the holes in our system?
A.
Most companies have at least one, if not several, anti-virus programs installed on users' computers. Because these programs rely primarily on known virus definitions to scan systems, you must update them often to keep the definitions current. Although IT professionals can automatically update the network's virus protection, users need to update their own computers. When users don't update them, they may introduce security holes and allow new viruses into the system that the anti-virus software does not recognize. The following are a few things IT personnel can do to plug these security holes and let users know the importance of updating:
Educate users about potential problems if they don't implement updates. Many users feel a false sense of security with anti-virus software installed. They usually do not know how the software works and the importance of updating virus definitions. When you educate them about the potential risks, they are more likely to update their programs when asked.
Give your users incentives for implementing updates. These simple rewards can motivate users to spend the necessary time to update.
Show that updating anti-virus software is easy and encouraged, not prohibited. Some employees are so scared of violating security rules, they are not sure if they should update the software on their own computers. Others think updating is too technical or takes too much time. By educating your users about the ease and appropriateness of updating, you will reduce their fears and motivate them to do it on their own.
Make IT personnel available to help users update their systems. Some users just need someone to walk them through the process for the first time. Because updating is so important to security and can reduce larger security problems in the future, it is in IT professionals' best interest to reduce the problems by spending time to help update instead of spending time later to patch a security hole or virus attack.
Conclusion
Organizations constantly struggle to find the balance to provide users access to needed resources while minimizing security vulnerabilities. Despite best efforts and technology, vulnerabilities will always remain. As a result, the security of any computer network ultimately rests in the hands of the end users. This makes the need to educate and train them an absolute necessity. By utilizing guidelines such as those listed above, a sound security policy and training program can be implemented to minimize the security exposure that your organization faces. 
BrainStorm, Inc. is the Novell Authorized End-User Training Partner and develops solutions that help your end users fully utilize Novell tools. BrainStorm offers training services and materials, including Quick Start Cards, for the Novell Linux Desktop, OpenOffice.org, GroupWise, Virtual Office and other desktop applications. Contact BrainStorm at 1.801.229.1337 or online www.BrainStormInc.com.
* Originally published in Novell Connection Magazine
Disclaimer
The origin of this information may be internal or external to Novell. While Novell makes all reasonable efforts to verify this information, Novell does not make explicit or implied claims to its validity.