Password
Articles and Tips:
01 Feb 2006
As you arrive at work, you worry whether today might be the day. You approach your computer with trepidation and turn it on. At the login screen, you slowly punch in your special row of asterisks and click the OK button. After a few seconds your worst fears are realized; you're informed you have 14 days to come up with a new password. You turn your mouse pad over, scratch off your current password and try to think of something you haven't used before.
As you type in your pet's name, you're informed of some new security requirements that your new password must meet. These new requirements include special characters, upper-case letters, numbers and the length of the password. Aghast, you look around at the items on your desk for inspiration, but nothing comes.
This is the mindset of your typical network user. The last thing they want to hassle with is password management. This type of user is not trying to come up with a password scheme based on mathematical algorithms that maximize the security of the network. All they want is to quickly change their password to something they will remember in 10 minutes. Beyond their system password, if they have to access a network application which requires user credentials, they tend to act a lot like electricity: when discharged, electricity heads to ground by way of the path of least resistance.
A user's path of least resistance is to choose the same password for the application that they use to log in to the system. In math, we refer to it as the "least common denominator," where the user has one common password which is easy to remember and is based on something simple or common to them. Isn't it ironic that the strict security policies put in place to safeguard the network, end up having the opposite affect?
To go one step further, factor in the number of network or Internet-based applications that the user needs to access. In many organizations, users access upwards of eight different systems or applications. These applications might include CRM systems such as SAP, terminal emulation to legacy main frame applications or even custom, internally developed Web applications.
Each application has its own unique password-change policy and format requirements. In this scenario, the Nirvana of a single, simple password for all applications lasts only a few days, after which the variation of password requirements and combinations explodes exponentially forcing the user into what could be considered the 10th ring of hell; in Dante's The Divine Comedy, Virgil guides Dante through the nine rings of hell. Had Dante written in the 21st century, he surely would have included a 10th ring dedicated to the types of suffering endured by you and your users, due to out-of-control identity and password management issues.
Direct and Hidden Costs of Password Management
According to different analyst reports, suffering in that 10th ring costs enterprises anywhere from $25 to $50 USD every time a user calls the help desk with a password-related issue. For an organization with 10,000 users, this could easily cost more than $100,000 per year. This yearly, hard cost doesn't take into account the soft costs associated with the loss of productivity while users wait for passwords to be reset.
In an effort to cope with and reduce the suffering that passwords cause, users often turn to the corporate-banned SNUMP method of password control. SNUMP, better known as "Sticky Note Under the Mouse Pad," helps users maintain password lists without having to program master control spreadsheets or attend Memory seminars. While this may decrease a network user's suffering, it increases the suffering of those who are trying to safeguard the network. You've been trying to eliminate the SNUMP method for years without success. The harder you try to impose greater security on the network, the less secure it actually becomes. But now, with the latest release of Novell SecureLogin, you can be saved from password hell.
Novell SecureLogin 6.0
Novell SecureLogin 6.0 provides enterprises with fast and easy access to corporate resources using a single, secure login. Users authenticate once to the network and from then on, SecureLogin streamlines and automates access to their applications and resources. SecureLogin 6.0 also allows you, as an administrator, to take control of credential management. SecureLogin becomes the password broker between all of the network applications and your end users. By creating secure password policies and associating them with users and the network applications, you can affect your organization in several positive ways. You can:
increase the security of the network data and applications by enforcing strict password requirements and policies without having to place that burden on the shoulders of your users
reduce the help desk costs with regard to password-related issues
improve user productivity by streamlining their access to network applications and by reducing the time wasted calling the help desk with password-related issues
facilitate compliance with new government regulations for identity, privacy, policy enforcement, and audit and authentication services.
What's New in SecureLogin 6.0
Novell SecureLogin 6.0 incorporates significant enhancements. Some of the most important of these are a new user interface; improved management capabilities, including integration with iManager; added support for Mozilla Firefox; a new Web Wizard; significant out-of-the-box application support; and the new ability to use advanced security methods, such as smart cards and biometric devices.
1 New User Interface
SecureLogin 6.0 has a redesigned user interface for easier navigation. The new interface includes a two-panel display with a browse tree on the left and a display of the user's settings and options on the right. (See Figure 1.) Novell enriched the interface with graphics to help identify tools, settings and user information. Novell also implemented customer usability feedback to make it more intuitive when you create or modify new application definitions and linkedlogin credentials.
Figure 1: SecureLogin 6.0 has a new user interface that incorporates a tree view on the left for easier navigation and the settings and options on the right.
2 Improved Management Capabilities
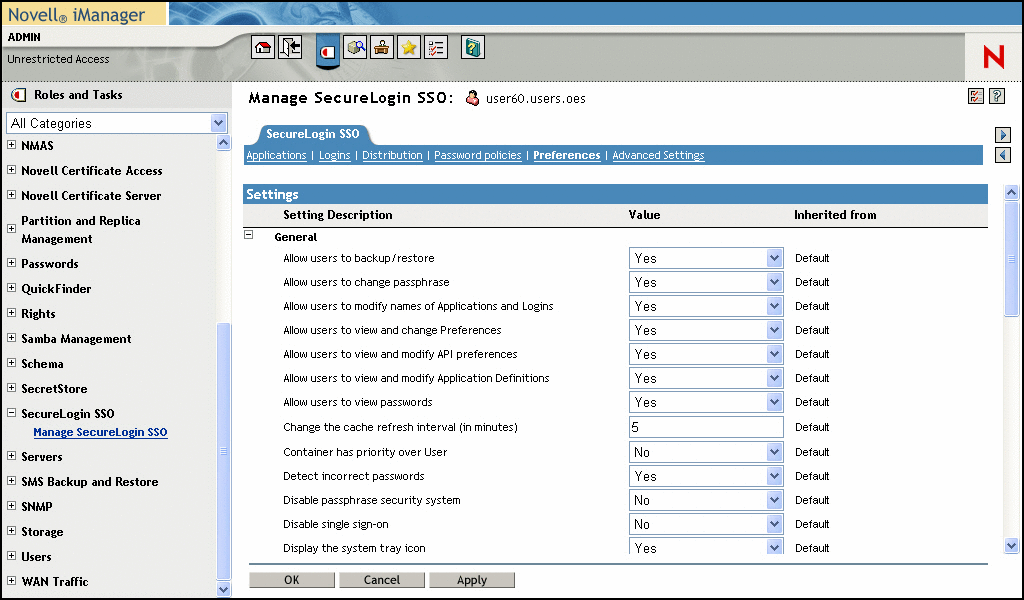
You can now integrate and manage SecureLogin 6.0 with iManager, the Novell Web management utility. As iManager continues to take over for ConsoleOne, this integration continues the progress to centralize all of the management utilities via the Web. Also, Group Policies are now supported in 6.0, which improve managing application access and credentials. Group Policies extend the existing capability of managing at the user and container level; hence, you have greater flexibility and control to implement your security policies. (See Figure 2.)
Figure 2: SecureLogin 6.0 is now integrated with iManager, the Novell Web administration tool. This enables you to administer SecureLogin from anywhere with a browser and an Internet connection.
If you're using LDAP as your directory, or if you have multiple directories because of mergers or acquisitions, a new tool simplifies administering access rights in LDAP. Available in LDAP mode, this tool has a tree-style utility that lets you browse to an LDAP object and assign rights to it. Previously, you had to know and enter the fully qualified object name, including the location context. That was prone to user error, but the new utility resolves that issue.
3 Support for Mozilla Firefox
A significant addition, the Web Wizard now supports Mozilla Firefox. In the middle of 2005, Firefox reported that it had surpassed 50 million downloads. Touted as a more secure browser than Internet Explorer, many enterprises have adopted and standardized on Firefox. One benefit of the new Firefox support is that all scripts and application definitions you create for Firefox, also work on Internet Explorer, and vice versa. Few environments have a homogeneous browser installation; by adding Firefox support, you have a greater internal reach and a bigger impact when you implement your security policies across your organizations.
4 Updated Application Support
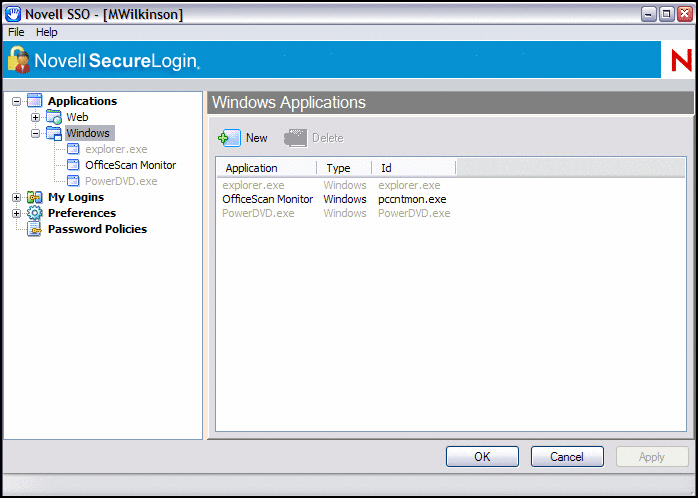
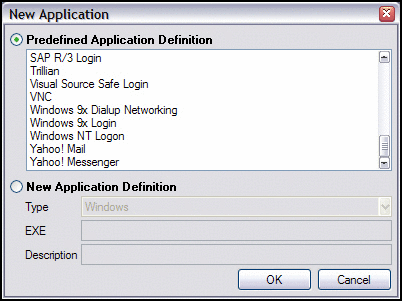
SecureLogin also now has an expanded application definition library. It provides out-of-the-box support for several Windows applications; for example, SAP, SQL Server, Novell GroupWise; terminal-based applications; and configurations for several popular Web sites such as Yahoo!Mail and Hotmail. (See Figure 3.) SecureLogin also now supports Java-based applications and extended add features that support the advanced requirements you have for complex Web applications. You can even configure it to look for applications that load prior to SecureLogin, such as iFolder, and pass credentials to the waiting applications for authentication.
Figure 3: SecureLogin 6.0 has expanded its application definition library and provides immediate support for several Windows applications, terminal-based applications, and configurations for several popular Web sites. You can also easily add your own applications.
5 Improved Web Wizard Functionality
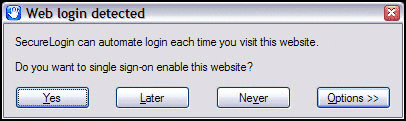
The improved Web wizard functionality in version 6 makes the single sign-on process on Web sites quicker and easier for everyone. The SecureLogin Web Wizard appears the first time a user visits a Web site that requires user credentials. The user is prompted to enter their credentials which are quickly captured for later use. This simple, onestep process enables Web sites to provide users with seamless, hassle-free access when they visit again. (See Figure 4.)
Figure 4: Through single sign-on, SecureLogin can automate the log-in process when users revisit sites that require credentials and log in passwords.
You can also use some of the advanced features to shorten the time and simplify the process of getting a user into an application to do their work. Normally, a user might have to log in to a remote system, launch and authenticate to an application, possibly answer some questions or respond to popups, and then navigate within the application to get to their desired area. SecureLogin can now automate that entire process based on the click of a single application icon.
6 Advanced Security Methods
You can now configure SecureLogin, in conjunction with Novell Modular Authentication Services, to add additional levels of security into your environment--at the most important places. These additional levels of security include support for smart cards, tokens and biometric devices.
A smart card is a small credit-card sized authentication device that includes a programmable microchip that can store data and perform cryptographic functions.
Tokens are small hand-held devices that generate one-time passwords for authentication. Several token methods exist, but the most common is when a user provides their credentials and is given a random number challenge. That random number challenge is entered into the Token device, which will issue the appropriate response for authentication.
Biometric devices are scientific devices that analyze a human body characteristic and compare it to a stored data version of the same characteristic. These characteristics can include fingerprints, eye retinas and facial characteristics. You can integrate smart cards, tokens and biometric devices at strategic areas to enforce strong proof of identity before allowing access to sensitive or confidential applications or data. You can now take complete control and lock down access to your data because of the added support and integration of these advanced Novell Modular Authentication Services security devices to SecureLogin. SecureLogin also tracks and captures network authentication and access events, which can be reported and audited using Novell Audit.
What's in a Version Number
If you're familiar with the previous release of SecureLogin, you might have recognized a significant change in the version number. While there have been significant improvements and additions to the product, the answer to the version number is quite simple: Active Card, Protocom and Novell have collaborated and released different versions of SecureLogin in various forms. Active Card recently acquired Protocom and the combined entity is now called Active Identity. Active Card had a previous release of their software which was version 5.5. Even though the last Novell release was version 3.51, the next logical release number to help synchronize the products across partners was 6.0.
Conclusion
Password and identity management are serious topics that require serious attention, especially in large organizations. Most organizations today deal with these issues by treating the symptoms rather then implementing a cure; in reality, they're just chasing their own tails and increasing the size of the 10th ring of hell. SecureLogin 6.0 has everything you need to take back control of your networks while lowering your costs and increasing the security of your systems as well as the productivity of your users. It also facilitates and simplifies conformance to government and corporate regulatory requirements. Now you can alleviate your own pain and remove the need for anyone to use the SNUMP method of password management. Instead of letting that 10th ring get bigger, you can get rid of it--with SecureLogin 6.0.
Certified Security
Novell SecureLogin 6.0 now includes new advanced-security libraries. These new libraries are Federal Information Processing Standard (FIPS) 140-2 compliant. FIPS 140-2 is a standard published by the National Institute of Standards and Technology (NIST) that outlines the U.S. Federal government security requirements implemented in IT products to deal with Sensitive, but Unclassified (SBU) data use. FIPS 140-2 has also been adopted by the Canadian government's Communication Security Establishment (CSE). The previous release of SecureLogin included the OpenSSL libraries, but these libraries were not FIPS approved. Cryptographic modules used in IT products must satisfy the requirements outlined by the FIPS 140-2 standard to be considered FIPS compliant. The FIPS 140-2 standard describes the requirements for four different levels of security. The requirements outline the various aspects of designing and implementing a secure cryptographic module. Examples of these aspects include module interfaces, key management, cryptographic algorithms and software security. FIPS 140-2 certification is required for companies who want to sell products that include cryptographic modules to the U.S. Federal Government. In addition, with the increased awareness and pressure to implement other regulatory requirements, such as those imposed because of Sarbanes-Oxley, the financial community has begun to specify FIPS 140-2 as a required checkbox for purchase consideration.
* Originally published in Novell Connection Magazine
Disclaimer
The origin of this information may be internal or external to Novell. While Novell makes all reasonable efforts to verify this information, Novell does not make explicit or implied claims to its validity.