Aud-it
Articles and Tips:
01 Feb 2006
Let's talk about the iPod for a minute. I love mine. I was introduced to the technology last year by my boyfriend who had me convinced I was nothing but prehistoric if I didn't have those distinct white ear buds in my ears while exercising or taking public transportation. Since then I've used my iPod to train for a triathlon, to help avoid conversation on airplanes and, just this last August, I even used it to usher in our wedding soundtrack. What a perfect union; us and our iPods, I mean.
But wait. Now there's an iPod Nano. It's impossibly small, has a color display and up to 14 hours of battery life. How could something so good get even better? That's just the question you might find yourself asking when you hear Novell is releasing the next version of Novell Audit (formerly Novell Nsure Audit) early in 2006.
Now let's step back and talk about why you should audit in the first place and what the previous versions of Audit did for you. Then I'll cover the new features and product enhancements you'll enjoy shortly with Audit 2.0. And, if you have them, stick those white ear buds in and read this article with some enlightening music in the background. I recommend something with trumpets.
Why Audit?
Whether you have healthcare records, product designs, payroll and employee information or financial histories, your company network has information that must be secure. As you know, that's no small feat.
To protect your electronic assets, you probably have security policies to ensure compliance with government regulations, such as the Health Insurance Portability & Accountability Act (HIPAA), the Sarbanes-Oxley Act, the Gramm-Leach-Bliley Act or the United Kingdom's Data Protection Act.
Whatever the case, as a network administrator, you likely translate those security policies into system-wide rules that enforce the various external and internal policies.
After you've implemented your auditing strategy, you need a way to assess overall compliance with company-wide policies, respond quickly to violations, pull and analyze logged data and produce reports to prove that all your regulations are being met. To sum it up, you have to know and regulate what's going on in every corner of your network--at all times. Feeling overwhelmed yet?
Past Versions
Novell (Nsure) Audit 1.0 shipped in 2003 providing a replacement for Auditcon and Novell Advanced Auditing Services (NAAS), as well as a logging foundation for Novell products such as Identity Manager, iChain, BorderManager and eDirectory. Audit is the result of years of experience Novell has under its belt developing some of the most secure enterprise software solutions in the industry.
Versions 1.0.1 - 1.0.3 soon followed the initial release and focused on improving stability and fault tolerance, standardized the event format and introduced additional notification channels.
What Comprises Audit?
Novell Audit is a client-server solution with four primary components:
Platform Agent the client portion of the Novell auditing system. The Platform Agent receives logging information and system requests from authenticated applications and transmits the information to the Secure Logging Server.
Secure Logging Server the server component of the Novell auditing system. The Secure Logging Server manages the flow of information to and from the Novell auditing system. In other words, it receives incoming events and requests from the Platform Agents, logs information to the data store, monitors designated events, and provides filtering and notification services. You can also configure it to automatically reset critical system attributes according to a specified policy.
Data Store the repository where audit data is stored. Novell Audit protects log data from record modification, insertion or deletion by allowing only one program component, the Secure Logging Server, to write events to the data store. Using its available channel drivers, Novell Audit can log events to the following storage devices:
Flat file in the file system
MySQL database
Oracle database
Microsoft SQL Server database
Syslog database.
Reporting Applications Novell Audit provides two tools you can use to generate reports from MySQL, Microsoft SQL Server and Oracle data stores.
Novell Audit Report is a Windows-based, Open Database Connectivity (ODBC)-compliant application that can generate reports from Oracle and MySQL data stores. It includes predefined reports and you can integrate it with Crystal Reports to get full custom-reporting capabilities.
iManager is a browser-based, Java Database Connectivity (JDBC)-compliant application that can generate reports from MySQL data stores.
How Does Audit Work?
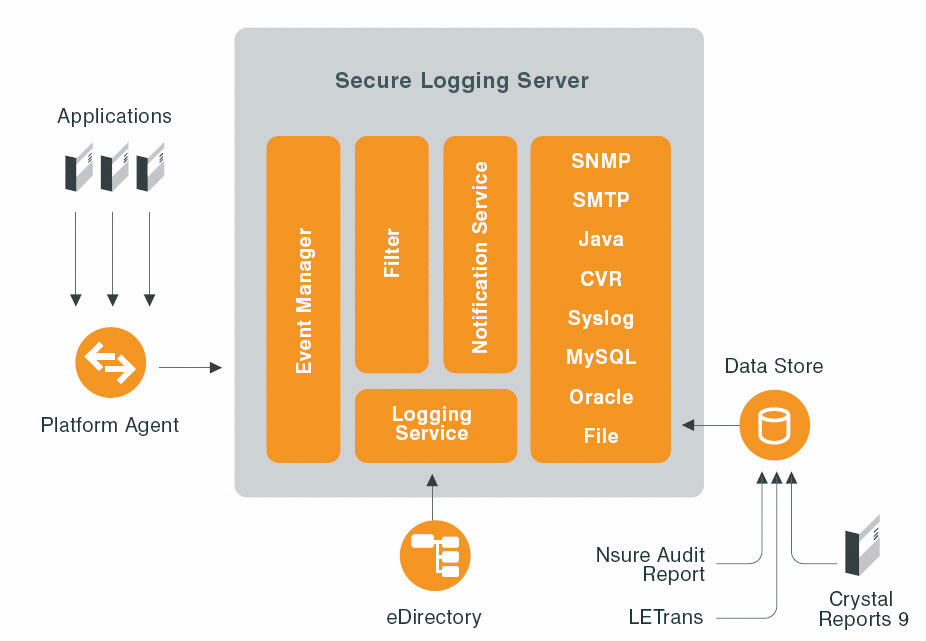
In basic terms, these components work together like this: the Platform Agent collects event data from the Logging Applications running on the server or workstation. (See Figure 1.) In nonrepudiative mode, the Platform Agent (or Logging Application) then digitally signs each event before transmitting it over a mutually authenticated and encrypted connection to the Secure Logging Server. (For more information on nonrepudiation and signing, see Audit Signing and Chaining below.)
Figure 1: You can get a bird's-eye view of each application that is plugged into Audit and logging events to the Platform Agents.
The Platform Agent and Secure Logging Server establish this secure communication channel using Transport Layer Security (TLS).
The Secure Logging Server writes the data to a persistent data store, such as My SQL, Oracle or a flat file. The reporting applications query the data store and generate reports. Simultaneously, the Secure Logging Server evaluates the data to determine if any alerts are required or if any monitored values have changed.
Diagram 1: New to Novell Identity Manager 3
Audit Signing and Chaining
Novell Audit helps you achieve nonrepudiation through a process Novell refers to as the signing and chaining of events. In the context of auditing, nonrepudiation means that you log and record event data in such a way that you can prove that events have not been tampered with and that your record is complete. And that's important--especially in today's society.
Novell Audit components work together to protect the integrity of your logged data by signing and chaining events. Here's how:
Signing is the process whereby the Platform Agent (or, in some cases, the Logging Application) affixes a digital signature to each event it receives before forwarding the event data to the Secure Logging Server. This signature enables the Secure Logging Server to verify the integrity of the event data it receives and thus ensure that the event data has not been tampered with.
Chaining is the process whereby the Platform Agent (or in some cases, the Logging Application) includes a hash of the previous event (from the same Logging Application) with each new event from a given Logging Application. The hash (along with the data from the next event) is also signed. This hash enables the Secure Logging Server to verify that all events are in the data store and that none of them have been removed.
Through signing and chaining, Novell Audit protects your data against various types of security breaches, such as rogue administrators attempting to cover their tracks.
What's New with Novell Audit 2.0
NEW PRODUCT FEATURES
Windows Event Collector
The Window Events Collector runs as a service on Windows 2000 / XP / 2003. This new feature retrieves events from the various Windows event logs including:
Application log
Security log
System log
Directory Service log
File Replication Service log
Domain Name Server (DNS) log. Windows events are collected and sent to the Secure Log Server for processing by Novell Audit.
New Notification Channel
Audit 2.0 implements the Java Message Service (JMS) channel as a JMS Producer client application. It receives event messages from the Novell Audit event notification system, maps the event information into JMS messages and sends them to a JMS bus. JMS Consumer applications can then retrieve the JMS messages from this destination.
Log File Parser
The Log File Parser allows consumption of existing text logs without needing to instrument the application. This means that Novell Audit can collect events from applications--previously not possible--by harvesting events from text-based log files such as syslog on both UNIX and Linux systems, Apache Error Logs and ZEN Application Launcher logs. (See Figure 2.) The events are parsed and formatted in the Novell Audit event structure so they can be processed by Novell Audit. The Log File Parser has a simple user interface, allowing administrators to quickly integrate new application data in Novell Audit.
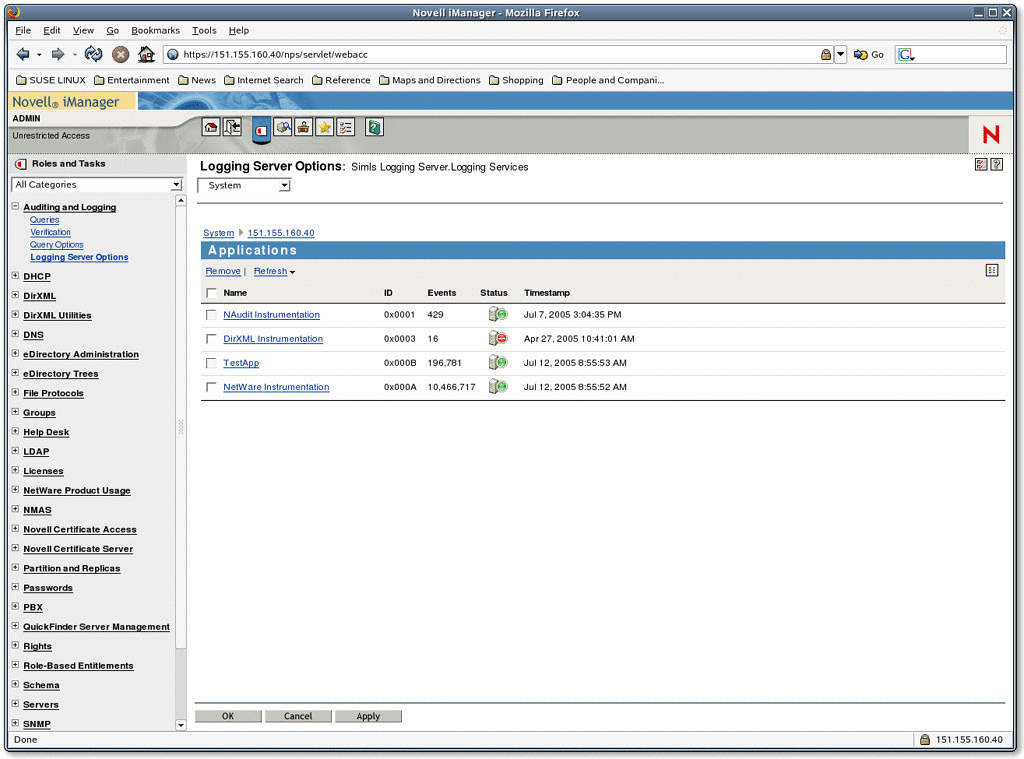
Figure 2: You can harvest connection statistics such as the number of clients connected and the number of events being logged for each client.
NEW PRODUCT ENHANCEMENTS
Monitoring
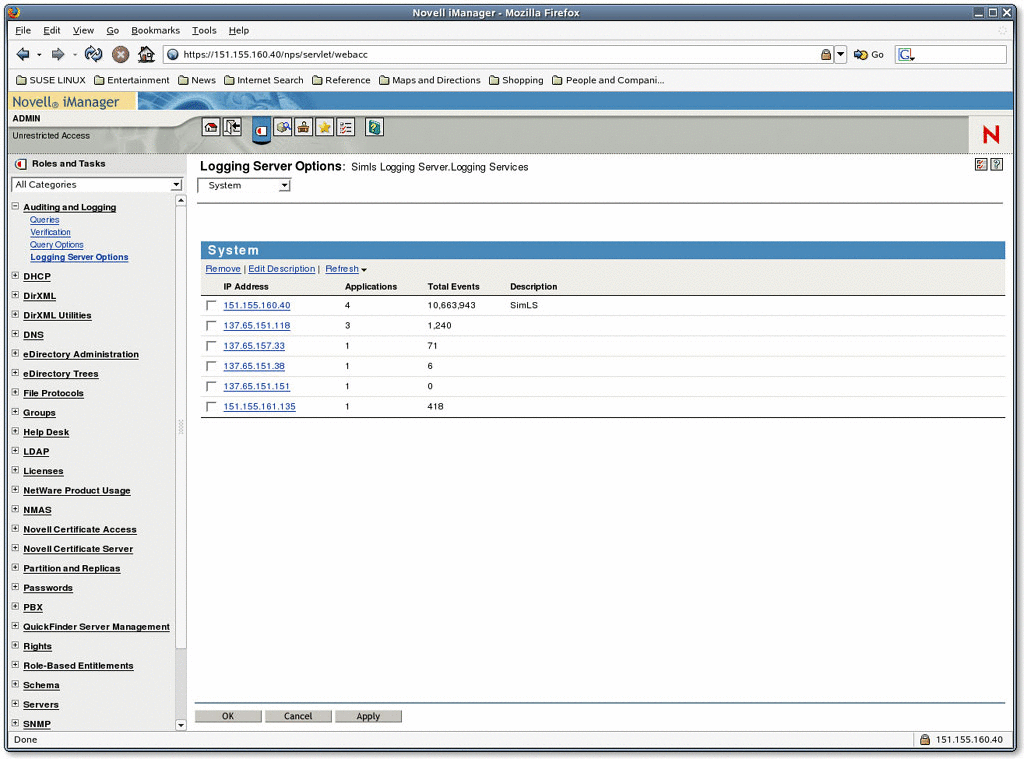
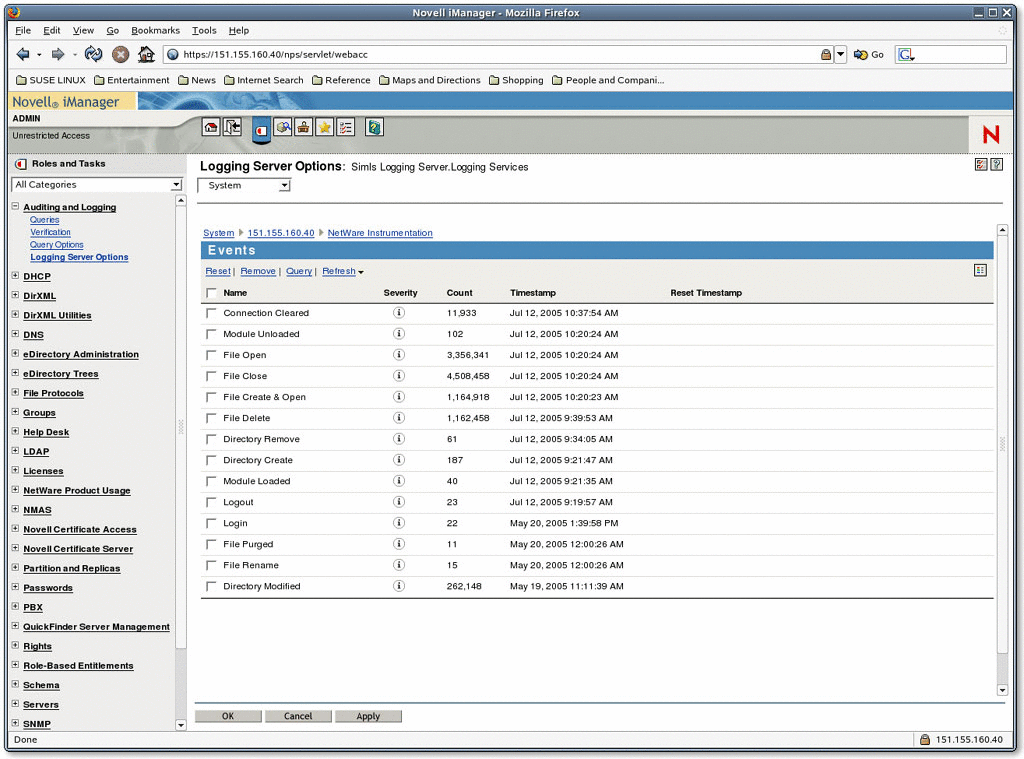
The Monitor channel provides logging system statistics in the easy-to-use management Web tool--iManager. (See Figure 3.) When the Monitor Channel object is enabled, each Secure Logging Server object includes the Monitor tab as one of its Logging Server options. The Monitor tab provides the following information:
total number of events logged during the current server uptime
average number of events logged per second (this is averaged over a three-second interval)
IP addresses and descriptions of the clients (Platform Agents) currently logging events to the current Secure Logging Server (See Figure 4.)
applications logging events to each Platform Agent
events logged by each agent.
Improved Event Filtering
In previous versions of Novell Audit, all event notification filtering took place at the Secure Logging Server rather than with the Platform Agents. Novell Audit 2.0 allows administrators to implement event filters at the Platform Agent using each logging application's associated application object. Pushing event filtering down to the Platform Agent minimizes traffic between the Platform Agent and the Secure Logging Server, decreases the load on the Secure Logging Server, and conserves disk space in the central data store.
Figure 3: Using the easy management tool iManager, you can gather real-time server statistics such as memory used, running time, total connections and events received.
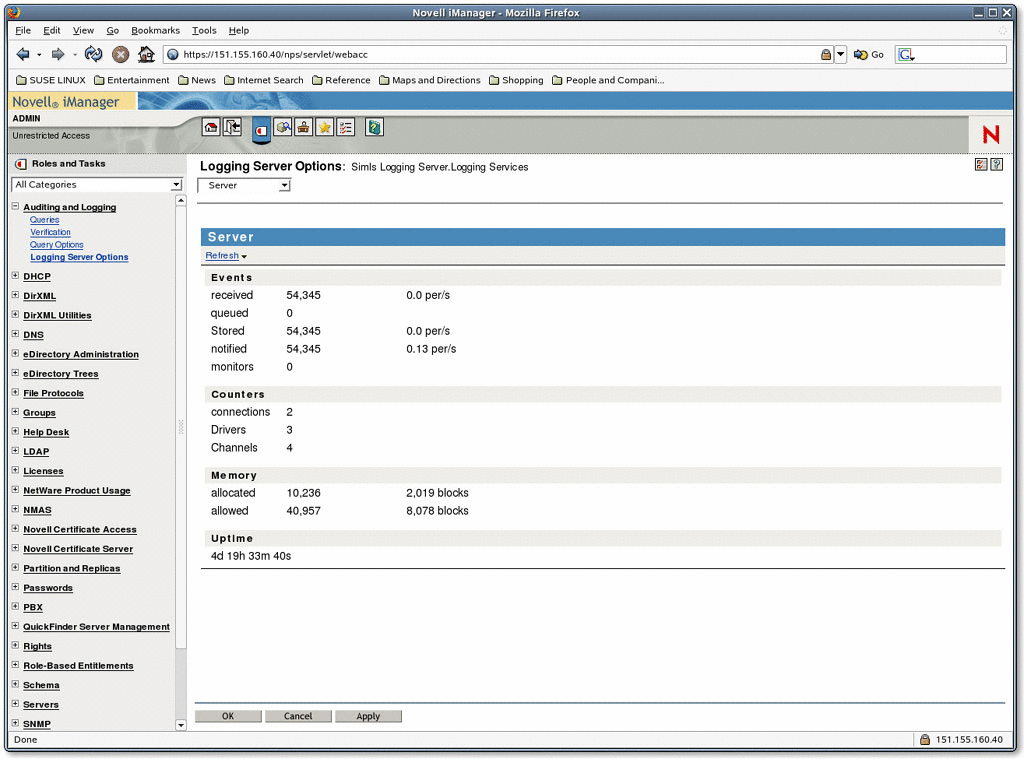
Figure 4: You can drill down even further and monitor each event being logged and how often they are coming in.
As you can see, previous versions of Novell Audit have successfully simplified the job of securing your network since 2003. But just like my iPod and the Nano, the product has gotten even better. With features enhancing everything from collecting, monitoring, filtering and notifying of event data, this is definitely a good thing--made even better.
Novell Audit 2.0 At a Glance
Components
Platform Agent
Secure Logging Server
Data Store
Reporting Applications
New Features
Windows Event Collector
New Notification Channel
Log File Parser
Enhancements
Monitoring
Improved Event Filtering
* Originally published in Novell Connection Magazine
Disclaimer
The origin of this information may be internal or external to Novell. While Novell makes all reasonable efforts to verify this information, Novell does not make explicit or implied claims to its validity.