Who What When Where
Articles and Tips:
01 Feb 2006
You know that business success depends on having the right tools and information available to the right people when they need them. That requires you to effectively manage identities--the people and the resources throughout your enterprise.
It's fairly straightforward: With identity management, you more easily improve service, resolve security weaknesses and reduce IT administrative costs. Without it, new employees sit idle, waiting for access to needed business--tools--while former employees have access to those tools for days, or even weeks, after they leave.
Okay, you're thinking--nothing new there. Identity management has become a necessity for today's enterprises. What is new is the technology that provides identity and effective control over both automatic processes and those that require human intervention.
The new solution streamlines approval processes and enables delegation of authority while providing self-service features that ease the management burden on your staff. It does all that by leveraging, rather than replacing, your existing business processes and technology investments.
Identity Management Through the Complete User Lifecycle
The recently released Novell Identity Manager 3 helps you securely manage identity and access for your ever-changing user community through complete management of the entire user lifecycle across all systems and organizational boundaries. It lets you deliver first-day access to essential resources, synchronize passwords across connected systems, instantly modify or revoke access rights and enforce security and regulatory compliance.
For resources that require human approval, the system automatically notifies appropriate approvers and enables them to quickly and easily provide or deny access. (See Figure 1.) It even allows them to easily delegate authority when necessary.
Figure 1: Novell Identity Manager 3 delivers advanced workflow-based provisioning capabilities, automating the entire process each time a resource is requested, even if human approval is required.
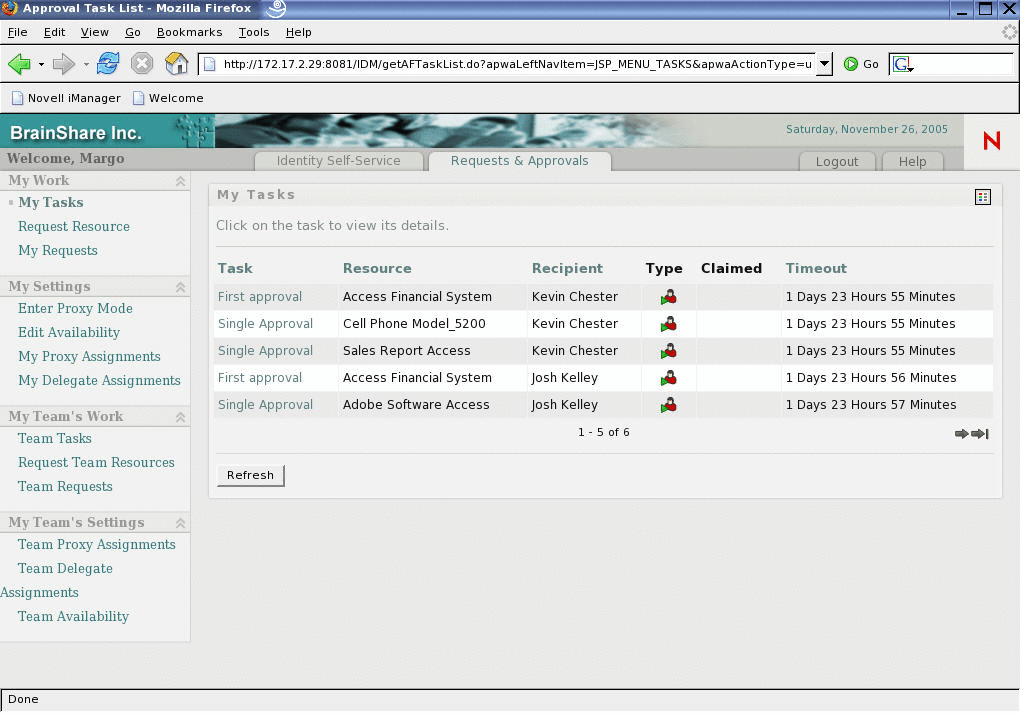
From the time an employee walks through the door on his first day with your company until he closes the door on his last, Identity Manager 3 has you covered--whether the processes can be done automatically or need human intervention. You get all this from three important capabilities of Identity Manager 3: automated role-based provisioning, workflow-based provisioning and password management.
Let's take a look at how each of these work to bring you the agility and security you need.
1 Automated Role-Based Provisioning
Using your business rules, Identity Manager 3 automatically provisions resources to your users based on their roles and relationships in your organization. New employees can access everything they need on their first day on the job--without your team manually entering user information on multiple systems. You get more done with fewer people, which saves you money and lets your staff focus on more strategic projects.
For example, let's say the HR manager at Sacred Heart Medical Corporation (SHMC) has just entered a record for Stanford Oveson, a new physician at one of its hospitals. In response, Novell Identity Manager 3 automatically:
creates accounts in other applications based on Dr. Oveson's role as a physician; in turn, those accounts provide authoritative identity information. For example, SHMC uses Microsoft Exchange for e-mail addresses. Microsoft Exchange creates the e-mail address soveson@shmc.com, and Identity Manager 3 communicates that to all connected systems.
transforms data into appropriate formats for each system. For example, PeopleSoft uses a phone number format of xxx-xxx-xxxx, while the Microsoft Exchange format is (xxx)xxxxxxx. Identity Manager automatically formats each correctly.
updates all relevant information in all connected applications. For example, PeopleSoft shows that Dr. Oveson works at the company's hospital in Chicago, so Identity Manager creates an Exchange mailbox for him in the Chicago container. When Dr. Oveson later moves to the group's hospital in Austin, Texas, Identity Manager automatically repeats the synchronization process.
2 Workflow-Based Provisioning
Obviously, there are times when you don't want to--or can't--completely automate the provisioning of all resources. Sometimes a human needs to decide whether a resource should be granted. No problem: a new Identity Manager add-on module integrates humanbased, or "workflow," provisioning. In other words, the Provisioning module for Identity Manager electronically manages and streamlines the entire process each time a resource is requested, even if human approval is required.
With Identity Manager 3, there is one system for both automatic and human-based provisioning, and one Identity Vault that stores all provisioned information. The benefits are obvious: no more paper chase since all requests are made and approved electronically, and the automated approval process lets people get to work as quickly as possible.
On his first day at work, Dr. Oveson opens the new Identity Manager Web-based User Application to see what resources are available and how he can get approval to use them. On that browser page is a list of resources he can simply click to initiate the workflowapproval process for each.
Dr. Oveson wants access to the Oracle financial system, so he clicks to request access to that resource. Hospital policy requires that his request be approved by both Judith Allen and Steven Chapman in HR. Identity Manager 3 automatically e-mails Allen with the request. She simply clicks a link to bring up the approval form, then clicks the appropriate place on the form to approve the request.
Between patient visits, Dr. Oveson accesses the User Application to check the status of his request. He sees that Allen has approved his request, but Chapman's approval is still pending.
In the meantime, Steven Chapman--who is vacationing in Cancun--decides to check his e-mail. Using a browser available in his hotel lobby, he logs in and discovers a long list of approval tasks that he forgot to assign to someone else while he was gone. Chapman e-mails his manager and asks if he can temporarily reassign the approvals on his task list to another manager. Since Kathryn Johnson is an assistant manager with responsibility for Oracle financials, Chapman's manager assigns her to be Chapman's authorized delegate for all Oracle requests. Within minutes, Johnson receives Dr. Oveson's request for access to Oracle financials. Because doctors are not normally allowed to see hospital financials, Johnson denies the request. Hospital policies were protected with a few simple clicks, even though one of the approvers was lounging on the beach in Mexico.
Before leaving on his next vacation, Chapman can delegate authority to appropriate department heads, their assistants, or even temporary proxies. He can do the same thing the next month, when he'll be busy preparing annual reports.
Simply put, Identity Manager 3 lets you make sure that provisioning approval decisions are always made by appropriate authorities with direct responsibility for the involved employees. It also lets you avoid delays if people are out of the office or swamped with other work.
3 Password Management
Normally, an employee who forgets his password must call the help desk for a password reset--eating up his own valuable time and driving up support costs. But with Novell Identity Manager 3 you can synchronize a user's passwords to provide a single password to all systems. Users are more likely to remember a single password. But if they don't, they can receive hints or change the password through the User Application tool. Users can also manage their passwords using the native password interfaces in systems such as Microsoft Windows. (See Figure 2.)
Figure 2: Novell Identity Manager 3 makes it easy for users to manage their own passwords, enabling users to remember, create, change and reset their password without calling the help desk.
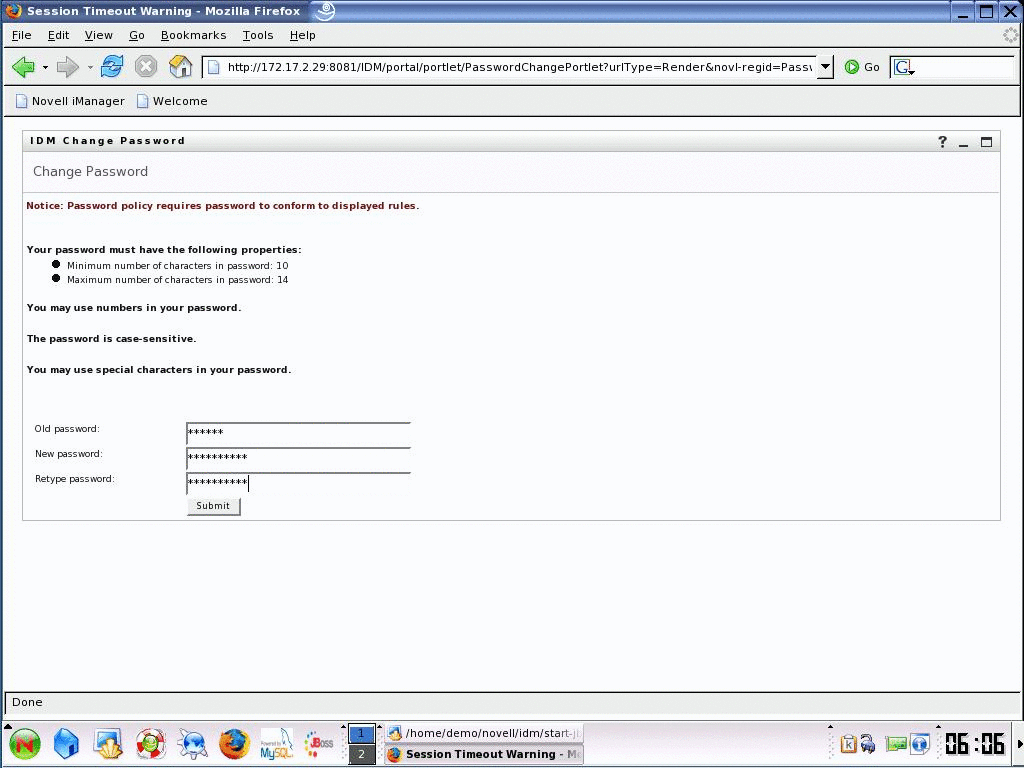
When Dr. Oveson forgets his password, the User Application comes to the rescue. It allows him to remember, create, change and reset his own password without calling the help desk and taking up an IT administrator's time.
When Dr. Oveson visits the User Application he is given one of the following administrator-defined options:
Password hint The administrator decides whether the system delivers the hint immediately on the screen or by e-mail.
Password reset with challenge and response One or more challenge questions are displayed on screen. These can include questions originally created by Dr. Oveson himself, by the Identity Manager administrator, or a combination of both. When Dr. Oveson answers the questions correctly, he is permitted to change his own password. The new password is automatically checked for policy compliance, then updated and synchronized with all connected systems.
With Identity Manager, you can ensure that passwords your users set are secure: you can create and enforce strong, system-wide password policies to protect your company against password-related attacks.
Reassignment and Provisioning
The capabilities of Identity Manager 3 combine to help you manage the user's complete lifecycle. For example, several years after he transfers to the hospital in Austin, Dr. Oveson is promoted to chief of staff at that facility. The promotion, of course, generates a number of changes in his identity information--and creates the need to update numerous records. With only a single change in the HR system, Identity Manager 3 propagates the identity information throughout the enterprise. Here's what happens as a result of that single entry:
Dr.Oveson is automatically given access to the new systems he needs as chief of staff.
Access is instantly shut off to the systems he is no longer allowed to use.
When Dr. Oveson moves from his office on the third floor to the new chief of staff office complex, his address is automatically updated in the system, and the update is distributed to all affected applications.
Dr. Oveson now reports to a new manager. All systems are updated--for example, the appropriate employee-to-manager relationship is changed in the financial applications, which affects the expense-report approval process.
A valuable time-saver in cases of promotions and transfers, the feature is also a vital security measure. With a single change, you can revoke user access rights across all systems in real time. As a result, former employees and business partners are completely deprovisioned when their business relationship with you ends. You gain instant protection against disgruntled exemployees, remove access to sensitive information, and eliminate lingering service expenses tied to former employees' user accounts.
The Right Identity Management Foundation
Identity is a common thread in many of today's enterprise security issues. And without a common identity foundation, each new solution you add creates another silo of identity and adds to your security problems.
Novell Identity Manager 3 removes barriers between your business systems and enables information to securely flow to your authorized users. You have the foundation you need to securely deliver the right resources to the right people--anytime, anywhere. Your business rules are used by the system to recognize and immediately deliver the right resources to the right people based on who they are and their role or relationship with your organization.
Created with market-leading technology and extensive experience in implementing complex identity management solutions, Novell Identity Manager 3 provides you with an identity management foundation that can support your complex business environment and evolving business practices. With the innovative solutions in Identity Manager 3, Novell can help your business gain the agility required for future growth, while retaining the world-class security you've come to expect from Novell.N
Reduced Complexity with Visual Design
Another exciting new feature of Novell Identity Manager 3 is Designer, a set of visual configuration tools that provide a simple, yet powerful way to design and configure what you implement. (See Figure 3.) With Designer, you can:
graphically model your implementation
re-use configurations to help reduce deployment time frames
create and test "what-if" scenarios before you deploy them to ensure proper policy definition
automatically generate project documentation of all implementation details
work offline to safely configure implementations outside of the production environment
maintain project version control
define and manage policies such as data transformation, placement and matching.
Figure 3: Novell Identity Manager 3 reduces the cost and complexity of identity management implementations with Designer for Identity Manager, a new set of visual configuration tools.
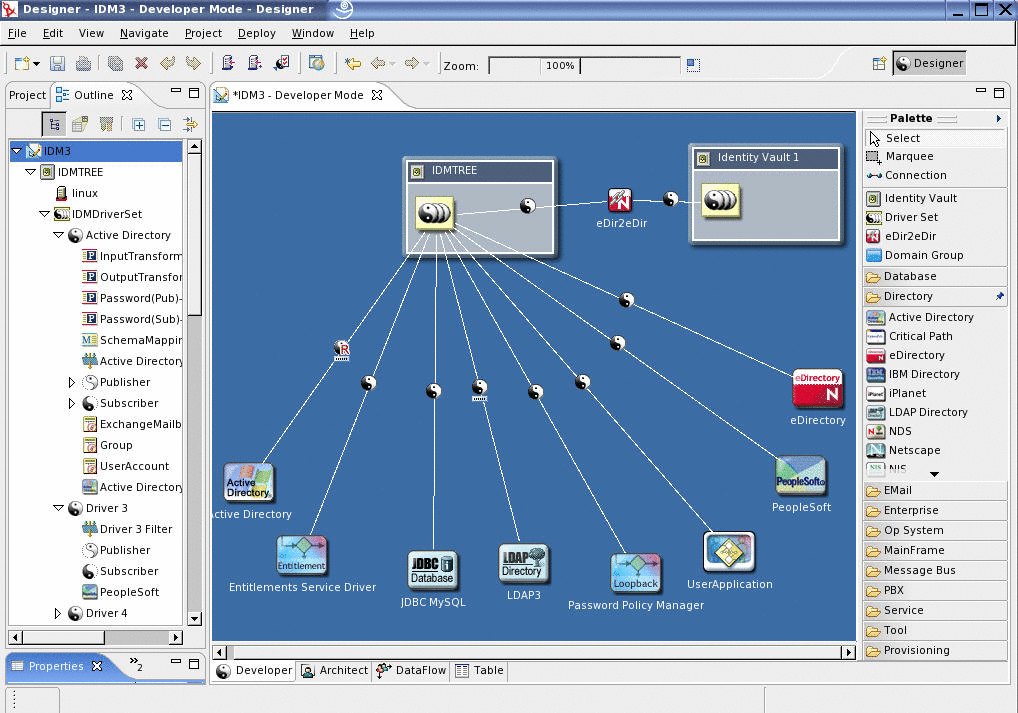
* Originally published in Novell Connection Magazine
Disclaimer
The origin of this information may be internal or external to Novell. While Novell makes all reasonable efforts to verify this information, Novell does not make explicit or implied claims to its validity.