Mission: Possible
Articles and Tips: article
01 Mar 2005
If you've been paying any attention at all over the last couple of years, you've heard a tremendous increase in the noise surrounding identity-driven services. Identity gives you the ability to properly identify everything on your network, from users, to hardware, to applications. Once you can identify everything on your network, you can start to manage the interactions between these identities. This is the real power of identity: being able to define and manage the myriad relationships on your network. Power to control resources, protect data, improve efficiencies, and comply with organizational policy and government regulation.
While the preceding may not be a news flash, identity-driven administrative tools are still developing and evolving, and doing them right requires identity-enabled network underpinnings. (Can you say directory?)
Enter Novell. With its industry-leading Novell eDirectory, Novell has long been known as the directory company. Because relationship management relies heavily on a robust directory infrastructure to make it all possible, Novell is uniquely positioned to lead the way in identity-driven network administration and management, and Novell Open Enterprise Server benefits from several identity-driven capabilities that will open your eyes to the power in being identity-driven. So read on, and take a look at some of the management power that Novell is delivering.
Identity-driven Net Management
Novell iManager is the framework that makes Novell's identity-driven management strategy come to life. And one of the nicest things for you is that iManager isn't some brand new, unproven concept. Novell iManager was initially released as part of NetWare 6, when Novell looked down the road and recognized the need to disconnect management from operating system and location. This made it possible to "manage from anywhere." The Java-based Web interface of iManager offers a true platform-independent management framework that can be used from any workstation at any location to perform a broad array of network management and maintenance tasks.
iManager 2.5, which ships with Novell Open Enterprise Server, has been re-architected to use Novell exteNd Web Services platform, and functions as a management portal for Novell products and services. Open Enterprise Server runs iManager on a separate Admin instance of the Apache Web server that ships with Open Enterprise Server.
iManager provides you with a complete set of tools for managing the services and applications available with Open Enterprise Server. This is accomplished through an extensible framework, in which developers can create service- or application-specific plugins to the iManager environment to provide whatever administrative functionality is necessary. That means that the Novell iManager team isn't trying to anticipate every possible management need in Open Enterprise Server. Rather, each engineering team delivers an appropriate iManager plug-in along with its service or application.
Once installed, iManager has its own URL (<server IP or DNS address>/nps/iManager.html) from which you can access its entire range of management capabilities. (See Figure 1.)
Figure 1
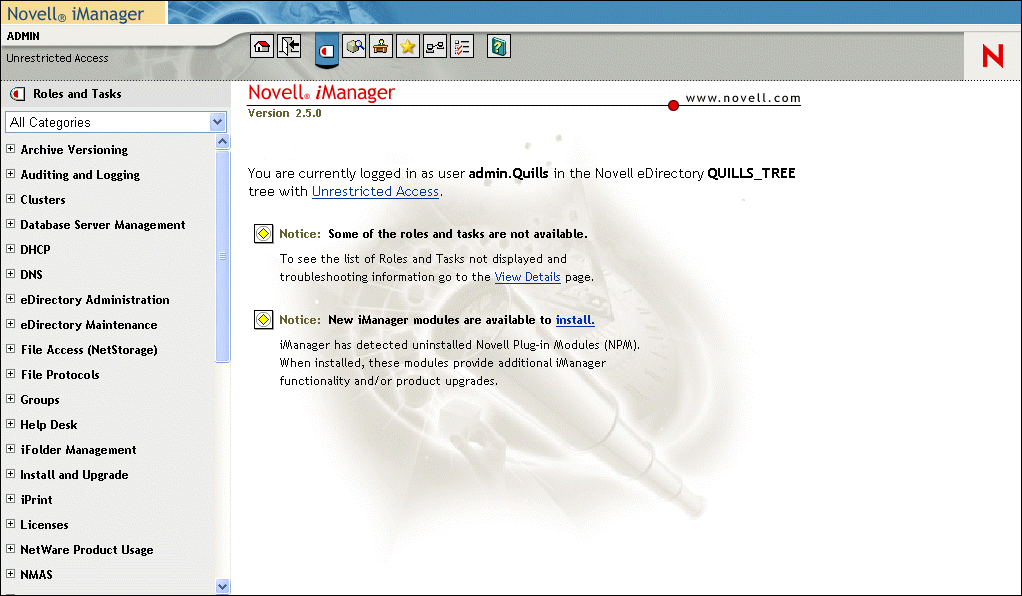
As shown in Figure 1, iManager is organized into three main sections, or frames:
Header Frame The Header frame is located at the top of the screen. Buttons provide access to the various views, or content categories, available through iManager, as well as an Exit link to close the browser window.
Navigation Frame The Navigation frame is located on the left side of the screen. It allows you to navigate among the various management roles and tasks associated with the selected iManager view. You will soon notice that what a user can see is constrained by their identity.
Content Frame The Content frame occupies the middle-right of the screen. When you select a link in the Header or Navigation frames, the appropriate information is displayed in the Content frame.
This look and feel is common for any management task available through iManager, so you never have to worry about unfamiliar tools again. This functionality by itself, reaches far across the breadth of the Novell product line.
Putting the "i" in iManager
So that's a great start, but how does this provide the identity-driven administrative capabilities we are all looking for? iManager provides a powerful role-based administration model, directory-enabled of course, that makes it relatively easy to divvy up the network management tasks in a way that eliminates the possibility of giving a user some administrative responsibility that results in them getting the "keys to the company."
iManager Role-Based Services (RBS) is based around the idea of tasks and roles. A task is a single discrete function, or operation, that can be assigned as a unit. A role is a specific set of tasks that a user is authorized to perform. Once assigned a role, or roles, a user's view in iManager is based on their role assignments. Because users must authenticate through the directory to access iManager, only the tasks assigned to the authenticated user identity are displayed. iManager 2.5 offers very granular configuration and assignment of network management responsibilities, and all RBS-related information is maintained in a set of RBS objects stored in the directory. (See Figure 2.)
Figure 2
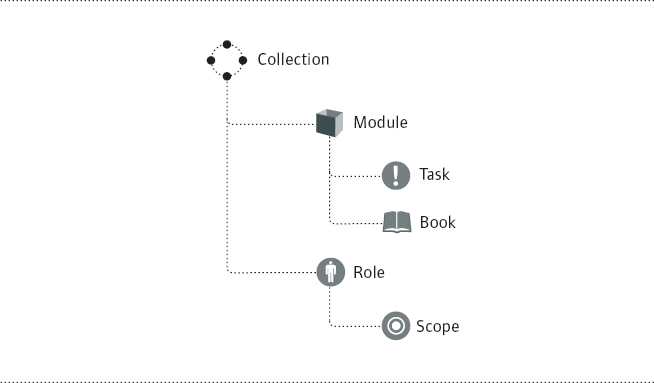
These object types include the following:
RBS Collection A container object that holds a set of RBS modules that will be assigned to a given portion of your eDirectory tree.
RBS Module A container inside the RBS Collection that organizes available RBS Tasks and Books into functional groups. RBS modules let you assign users responsibility for specific functionality within a product or service.
RBS Role Specifies the tasks that users (members) are authorized to perform. Defining a role includes creating an RBS Role object and linking it to the tasks that the role can perform. RBS roles can only be created in an RBS Collection container.
RBS Task Represents a linear process that can be performed via iManager. An RBS Task will look like a wizard utility that will guide you through the steps necessary to complete an operation. RBS Task objects are located only in RBS Module containers.
RBS Book Represents a variation on the RBS Task theme suitable for non-linear collections of configuration options that can be modified in any order or combination. For example, the attributes associated with a User object can be modified in iManager via the Modify Object RBS Book. RBS Books are located only in RBS Module containers.
RBS Scope Represents the context in the tree where a role will be performed, and is associated with RBS Role objects. This object is dynamically created and managed by iManager, so no additional administrative burden is created with the use of RBS.
All of your RBS configuration is handled, naturally, from the RBS Configuration in iManager. (See Figure 3.) From this screen you have full control over the structure of your role-based management system, including creating new Collections, adding/deleting Modules within Collections, and creating/assigning Roles to users.
Figure 3
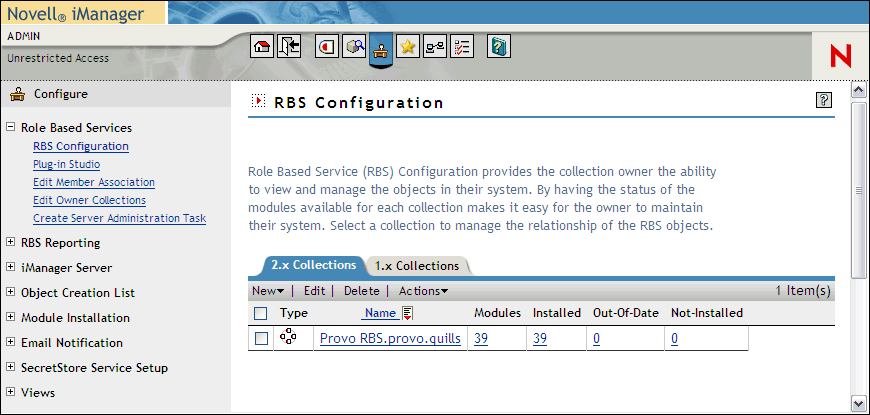
Not only that, but iManager 2.5 also offers a collection of RBS Reports that you can run regularly to keep track of your identity-driven management environment. This makes it simple to note outdated assignments, unused capabilities, and new ways to effectively leverage iManager to provide more efficient network administration.
The RBS capabilities of iManager provide a powerful framework for configuring and managing administrative access to your network. Leveraging RBS in your environment can greatly increase administrative security by granting each identity on the Net only that level of access necessary to accomplish its duties.
The Road to Healthy Living
iManager itself is an extensible management framework, and its RBS provides the ability to manage management. But that's just the first step. Novell has moved beyond the framework to provide other identity-driven management capabilities in Novell Open Enterprise Server that will make your life easier. One of these is Health Monitor.
Health Monitor is new technology released with Novell Open Enterprise Server. Now, you might remember with fondness the Health Monitor capabilities in Novell Remote Manager (NoRM). That proprietary tool is still available to monitor NetWare servers. However, since Open Enterprise Server isn't just about NetWare anymore, Novell needed a more generally applicable tool to provide monitoring of both NetWare and Linux resources. The new Health Monitor, available as a plug-in to iManager, is the logical evolution of NoRM's good ideas with regard to hardware monitoring.
Please Pass the WBEM
If you're going to open up a tool to make it more broadly applicable, the best way to do so is to leverage industry standards. That way, you greatly increase the ability of the tool to adapt and grow over time. Fortunately, a monitoring and management standard is already out there, and Novell is leveraging that standard to bring you Health Monitor. Web Based Enterprise Management (WBEM--pronounced "webem") is a set of management and Internet standard technologies developed to unify the management of enterprise computing environments. WBEM leverages open Web standards such as XML and HTTP to deliver well-integrated management tools. The WBEM standards are managed by the Distributed Management Task Force (DMTF) (www.dmtf.org).
WBEM has three main components:
Common Information Model (CIM) Describes a common format, language and methodology for collecting and describing management data.
XMLCIM Defines XML elements, written in Document Type Definition (DTD), which can be used to represent CIM classes and instances.
CIM Operations Over HTTP Defines a mapping of CIM operations onto HTTP that allows implementations of CIM to interoperate in a standardized manner.
These last two elements are combined into CIM-XML, a standards-based protocol for exchanging CIM information. CIM-XML carries an xmlCIM payload over an HTTP transport. With CIM-XML you are able to pass network monitoring and management data in standardized XML messages over the ubiquitous HTTP protocol.
CIM itself is an object-oriented model for describing computing and business entities in Internet, enterprise and service provider environments. It provides a consistent definition and structure of data using object-oriented techniques. CIM is comprised of two components:
CIM Specification Defines the language and methodology for describing management data and details for integration with other management models.
CIM Schema Provides the actual model descriptions and enables applications from different developers on different platforms to describe management data in a standard format so it can be shared among a variety of management applications. The CIM Schema includes models for systems, applications, networks and devices.
The WBEM set of standards and specifications has been around for a few years now, and has developed a strong following among those vendors interested in remote management of network devices. Now, Health Monitor brings you the benefits of a WBEM-enabled infrastructure as part of Novell Open Enterprise Server.
A CIMpler Way to Monitor your Servers
This first release of Health Monitor acts as a help desk for your Open Enterprise Server servers. It allows you to build lists of servers that you can monitor together. And when a problem arises, Health Monitor quickly guides you through the details so you can find the source of the problem and resolve it quickly. Health Monitor is comprised of three main components, all working together under the WBEM architecture.
Common Information Model Object Manager (CIMOM) Functions as the hub for CIM communications, and manages objects according to the CIM standard. A CIMOM functions as a CIM/WBEM service layer and interfaces Monitors with CIM Providers. The CIMOM module that is used with Novell Open Enterprise Server is named OWCIMOMD.
Providers Functions as the interface layer between a managed object and the CIMOM. The CIM Provider interfaces with a managed object (an Open Enterprise Server server in this case) and translates between CIM's standardized data format and the managed object's proprietary data format and management interface.
Monitors Functions as the management interface that communicates with Providers through the CIMOM. In the case of Health Monitor, the Monitor is the Server Monitor plug-in for iManager.
Health Monitor is available under the Servers category in iManager. From here, select Monitor Servers to open the Health Monitor interface and specify the server(s) that you want to monitor. Once that is done you are presented with a simple, yet powerful view of each server's status using the "stop light" metaphor: Green = Good, Yellow = Warning, Red = Danger. (See Figure 4.)
Figure 4
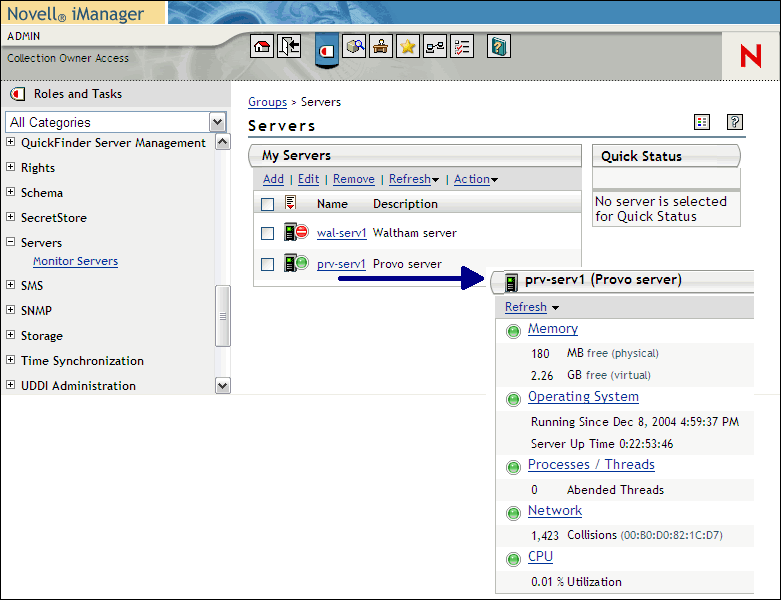
Note that it is still possible to monitor servers without the benefits of CIM/WBEM, but you are limited to querying a server to determine only if it is "up" or "down." Health Monitor refers to this capability as Simple Status, and it is available for any server in your environment. However, anything beyond Simple Status requires the ability to communicate with the server on a more meaningful level than a simple connection attempt, and that's where CIM/WBEM shows its worth. Without the CIM/WBEM standards, you would need a custom interface for each server type that you want to monitor. Because of CIM/WBEM, Health Monitor can accomplish the same level of monitoring, across multiple platforms, and from a single management interface.
The CIM/WBEM-enabled Robust Status view in Health Monitor provides much more comprehensive information about the servers you are monitoring. You can see the status of server memory, operating system, process/threads, network and CPU. (See Figure 4.) And not only that, but you can also drill down into each of these categories further to view the detailed operations of each server's major subsystems.
Because Health Monitor lets you build a list of servers to monitor, you can easily keep track of multiple servers at once with just a glance at My Servers. If you happen to spot a problem, you can quickly drill down to the source by following the trail of red indicators. For example, a red indicator by a server may lead you into the network category where you notice a high number of data collisions, indicating that network bandwidth may be very low at the moment.
Very nice, you might say, but where is the identity-driven aspect of all this? The answer to that question is two-fold. Remember, first of all, that you access Health Monitor through iManager, which means you can restrict access to the tool through the use of iManager's RBS capabilities. Second, Health Monitor is identity-aware in its own right. When you drill down into a server's statistics you are required to authenticate prior to being granted access. If you don't have sufficient rights to the server, then you don't get in.
By leveraging iManager, Health Monitor is able to provide robust server monitoring using a management interface common to both NetWare and Linux, and it does it in a secure fashion consistent with the overall Novell Open Enterprise Server security paradigm.
Live and Let Live
Up to now we have focused on the administrative environment in Open Enterprise Server, and how the identity-driven focus of Open Enterprise Server helps protect and secure your network administration. Let's turn our attention to helping administrators ease the burden of managing today's complex network environments. After all, Open Enterprise Server now offers two network platforms in a single product. If that's not a sign that a homogeneous network is a pipe dream then I don't know what is!
A heterogeneous network means different systems, different directories, different standards, and different ways of doing things. Worse than that, it means having to potentially do the same task multiple times in order to make sure that all systems get properly updated. Well...maybe not.
Novell has been offering a solution to the madness of managing disparate systems since 2000. Originally known as DirXML, and rebranded as Novell Nsure Identity Manager in 2004, Novell is leading the way in identity-driven infrastructure solutions. For an in-depth look at Nsure Identity Manager 2, check out the article in the November/December 2003 issue of Novell Connection magazine.
The simple fact is that heterogeneous environments are not going away. Once you stop fighting that reality it becomes a whole lot easier to develop a solution to the problem of managing identity across disparate systems. Instead of forced replacement of existing systems (a kind of scorched earth solution to the identity management problem), the strategy is a "live-and-let-live" focus on co-existence, and a measured migration to different systems where business drivers demonstrate that it makes sense.
To make this possible, Novell Open Enterprise Server includes Nsure Identity Manager 2 Bundle Edition, designed to allow Linux, NetWare and Windows systems to co-exist in harmony--and greatly reduce the blood pressure of your administrative staff.
Open Enterprise Server provides the ability to manage user accounts and synchronize passwords across the following directories. Read on to see how it all works.
Novell eDirectory
Novell Directory Services (NDS)
Windows NT Domains
Windows Active Directory
The Path of Least Resistance
Identity Manager account management and password synchronization works by putting Novell eDirectory at the center of your network environment in a kind of hub-and-spoke configuration. (See Figure 5.) From this configuration, it is possible to leverage eDirectory as a meta-directory to dynamically transform and synchronize user account and password information between other participating systems. To control when and how this occurs, you set synchronization policies based on your organization's needs.
Figure 5
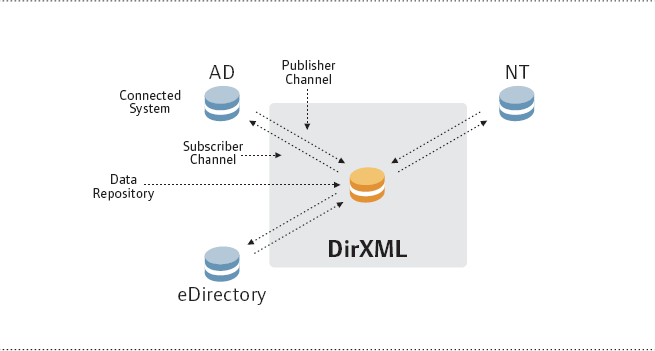
Identity Manager includes a graphical interface known as the Policy Builder, available through iManager of course, for creating the policies that control the flow of information between connected systems. Policy Builder steps you through the process of creating a policy to govern the flow of data between eDirectory and the selected system. All you have to do is select the appropriate channel (Subscriber = inbound, Publisher = outbound) and specify the conditions under which data will be transformed and synchronized between eDirectory and the selected system.
Once you have defined the policy, Policy Builder translates the rules you create into XML and applies it to the appropriate communications channel.
Take a Pass (on your password troubles)
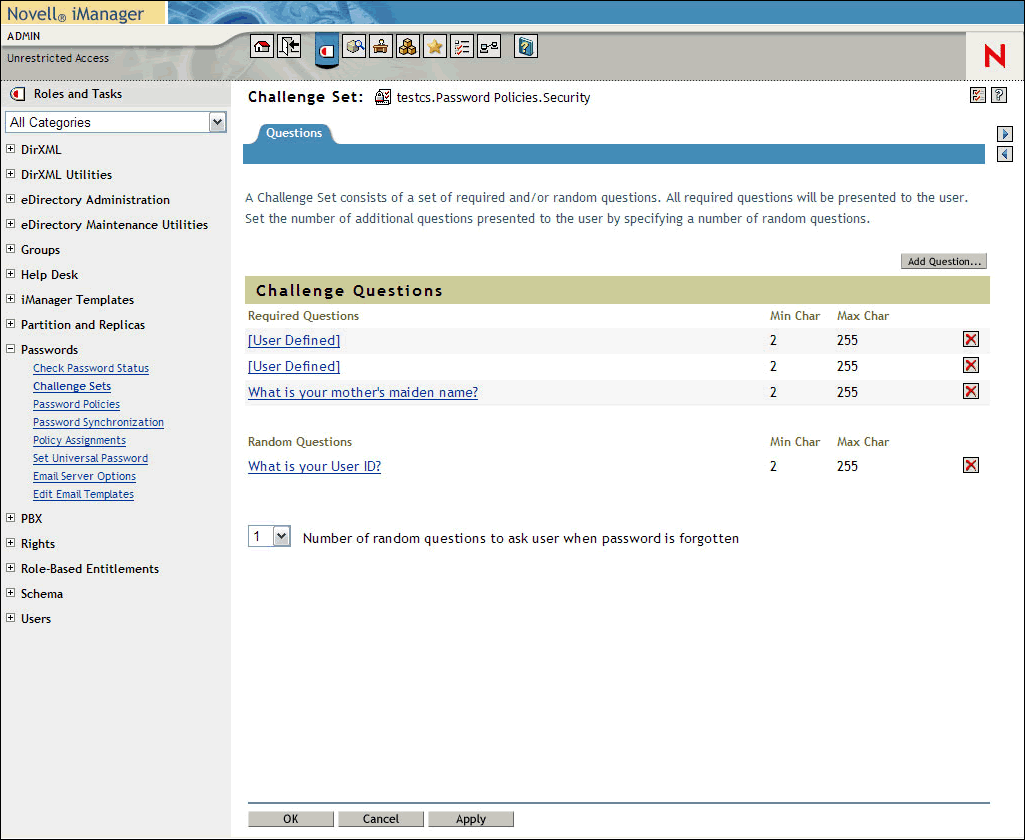
Once your policies are in place, you are ready to turn your attention to password management. Novell Open Enterprise Server with the Novell Nsure Identity Manager Bundle Edition can minimize the effort that your help desk personnel devote to managing user passwords. There are three aspects to the password battle, described below. The password management features of Open Enterprise Server are available in the Passwords category in iManager. (See Figure 6.) From here, you can walk through the process of managing your password environment--painlessly.
Figure 6
Password Policy: A collection of rules for creating and replacing user passwords. These rules specify what constitutes an acceptable password, including things such as minimum length and use of special characters.
Password Self-Service: An option you can enable as part of your Password Policy. It leverages the Universal Password available in Open Enterprise Server, and allows users to retrieve forgotten passwords, or reset passwords on their own, through the use of Challenge questions that can verify identity. When the Challenge is answered correctly, you can allow the user to reset their password, or e-mail them the forgotten password (or a hint to the forgotten password).
Password Synchronization: Once a user password changes, those changes are automatically updated across all connected systems. Because communications are bi-directional, password changes do not have to occur in eDirectory first. A change password event in a connected system will be propagated back to eDirectory, and from there to other connected systems, of course subject to the constraints of your Password Policy.
Together, these password management capabilities can offload a significant burden from your help desk staff. In fact, password-related issues typically comprise 30 percent of help desk calls. Does a 30 percent reduction in overhead sound like something worth pursuing?
Novell Open Enterprise Server--Identity-driven and loving it
In many ways, identity forms the basis for much of the computing that goes on in today's world. Banking, commerce, health care and government are just a few of those industries desperately interested in knowing who you are and what you are entitled to.
Your organization is really no different, possibly on a smaller scale, and the consequences of not being able to confidently answer the identity question can be just as grave for you as they are for those industries named above.
Novell Open Enterprise Server is leading the way in its use of identity- driven infrastructure with the goal of helping you build an environment that lets you answer the identity question. Through the identity-driven management tools of iManager, to the identity management capabilities bundled with Open Enterprise Server, to the identity-aware nature of most every Open Enterprise Server-related service, Novell is helping you make sure you can answer the identity question in the affirmative: "Yes, I know who they are and what they can access."
Know who they are, what they are entitled to, and keep them from mucking around in anything else. No matter who "they" ends up being, you can rest easy knowing that Novell Open Enterprise Server gives you the tools to properly manage identity.
Tweaking iManager
By default, iManager creates specific relationships between Tasks, Modules and Roles. However, you can modify task assignments, create customized Roles, or do most anything else you might need in order to align the RBS system to the realities of your network. iManager definitely rates high on the cool-O-meter, and you may be wondering just what is involved in tailoring the iManager for more customized use in your network. Well never fear, Novell has provided three powerful options for customizing iManager:
iManager provides a Plug-In Studio that lets you create your own RBS Tasks and Books through a simple wizard interface.
iManager Configuration options let you customize colors and branding of the iManager interface to that of your organization if you want.
If that's not enough, Novell provides a comprehensive iManager SDK as part of the Novell Developer Kit (NDK). The iManager SDK makes the entire iManager architecture available, including complete access to iManager APIs for creation of plug-ins, and the ability to create new "skins" for the iManager interface to completely adapt it to your organizational needs.
Information on the iManager SDK and the whole NDK is available online.
Health Monitor's Bright Future
As you may already suspect, the CIM/WBEM infrastructure is capable of a lot more than simple monitoring of server events. The CIM model supports bi-directional communications, meaning that Monitors can potentially send instructions to Providers instead of just receiving data. This opens the possibility for creating much more comprehensive management consoles that are capable of monitoring and managing devices from disparate vendors and systems from a common interface.
In fact, when coupled with a policy engine, a CIM/WBEM monitoring system can be transformed into a comprehensive management console capable of not only reacting to network problems, but also proactively identifying problem areas through the use of defined safe-operating ranges. When a monitored event leaves its defined operating range the system can automatically respond in some predefined fashion.
Does the future hold such robust functionality for Health Monitor? Keep your eyes on this space to see what develops!
Let Me See Your License Kid
There's no doubt that Novell Open Enterprise Server includes some tremendous identity management features. But make sure you distinguish between the Identity Manager capabilities available in Open Enterprise Server, Novell Nsure Identity Manager Bundle Edition, and the full version of Novell Nsure Identity Manager 2.0 that is available separately.
Once you've experienced the benefits of managing identities across NetWare, Windows and Linux, you can extend these same identity management capabilities to all of the other key systems in your environment, by simply licensing a full version of Novell Nsure Identity Manager.
By the way, make the move today to Nsure Identity Manager Professional Edition at $15 per identity--a discount of 40 percent off the list price. Visit www.novell.com/starterpack for more details. Act now! This offer ends April 30, 2005.
* Originally published in Novell Connection Magazine
Disclaimer
The origin of this information may be internal or external to Novell. While Novell makes all reasonable efforts to verify this information, Novell does not make explicit or implied claims to its validity.