Control Freak
Articles and Tips: article
01 Jun 2005
On March 8, 2005, Designer Shoe Warehouse (DSW) announced to customers that it could no longer be trusted--well, that's not precisely what it said, but that's what customers heard. Between December and March, hackers gained access to a database for customer credit card information from 103 of the retailer's 175 stores. Scrambling to regain its foothold with shoe-savvy customers, DSW offered to fund credit reports for anyone with a new to three-month-old pair of its cost-wise designer shoes. That's a lot of credit reports, and at roughly $20 US a pop, a lot of money. But financing credit reports is the least of the retailer's worries: wait until foot-fancy victims of identity theft start to sue.
You could try to convince yourself that this fiasco is an isolated incident, but as a network administrator, you know better. Hackers don't restrict their attention to retailers but happily break into any company's system, regardless of its industry. In fact, one out of every five of the 300 IT professionals who responded to a national survey conducted in October 2004 admitted that hackers gained unauthorized access to their company's network. (For more information, see the article online.)
More to the point in this case, hack attacks are only one of the many attacks that threaten daily to reduce productivity and increase network costs. Virtually every organization that uses the Internet (and what organization doesn't?) is vulnerable to an ever-growing list of attacks--viruses, worms, denials of service, spam, Web site defacements, application exploits and insider Net abuses.
Many of these threats appear to be getting worse. Take spam, for instance. AOL alone blocks 780,000,000 spam messages from its member mailboxes daily. Unless we radically change the way we route e-mail, spam is projected to account for 70 percent of messages by 2007. (For more spam numbers, see the article online.)
The situation on the worm front is equally dire. When the Code Red Worm blasted the Internet in July 2001, it infected roughly 359,000 computers in fewer than 14 hours. (See Mark Egan, The Executive Guide to Information Security, Addison-Wesley, 2005, p. 5.) That sounds dramatic until you compare it to MyDoom, which was intercepted at a rate of 100,000 instances per hour at the height of its outbreak in January 2004. To date, MyDoom boasts an impact of $4 billion US, not counting the cost of the many MyDoom variants still circulating. (See Egan, The Executive Guide, pp. 5, 11.)
Layered Lines of Defense: Integrate 'Em
To effectively protect your company's network (or your corner of the network) from such a wide range of ever-multiplying, increasingly complex threats, you need an equally wide range of security products. You should start with a firewall, but you can't stop there. Layering several security applications on top of your firewall is essential for adequate protection. (For more information, see "Don't Leave it All to the Firewall," Computerweekly.com, Nov 9, 2004.)
One approach to filling these layers is to buy separate security applications. But do you really want to do that? Attempting to understand, install and manage separate applications isn't easy. In fact, doing so potentially creates a barrier about as trustworthy as the fabled dike in Haarlem (which leaves you playing the part of Hans Brinker). More important, installing and managing a collection of products is a costly and time-consuming venture that might be more than you can manage single-handedly.
Novell offers an attractive alternative to this fragmented approach to perimeter security: the SUSE LINUX-based Novell Security Manager powered by Astaro. Novell Security Manager offers a complete set of fully integrated, perimeter-security applications. As a soft appliance, Novell Security Manager offers all of these applications in a single package, which simplifies and reduces the cost of deploying and managing the protective layers you need at your network's edge.
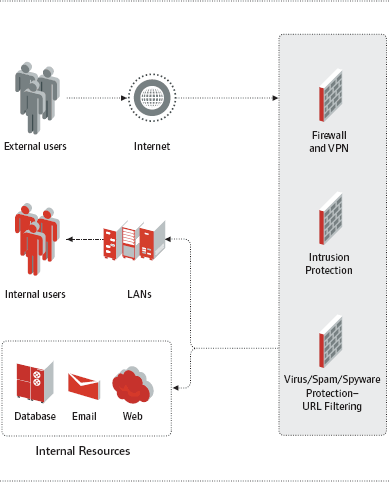
Figure 1: The SUSE LINUX-based Novell Security Manager powered by Astaro offers seven layers of protection in a single package.
Why Astaro?
When asked, Novell product manager Rob Sabey is eager to explain why Novell chose technology from Astaro Corporation (www.Astaro.com) to power Novell Security Manager: "We did some exhaustive research into the industry," Sabey shares, "and ultimately found Astaro to be unequaled running on Linux."
Jointly headquartered near Boston, Massachusetts and in Karlsruhe, Germany, Astaro has been developing security products since the year 2000. Astaro software has won several industry awards from sources such as LinuxWorld, Linux Journal and PC Magazine. (For information about Astaro awards, see their awards site.) Astaro technology now protects more than 20,000 networks in 60 countries for organizations such as Siemens, Stanford University and Los Alamos National Laboratory. Astaro's strong support for open source development complements Novell's commitment to become the open source provider. Fittingly, Novell Security Manager offers enhanced security applications that are based upon several open source projects, including Snort, an intrusion detection engine; the Apache SpamAssassin Project; OpenSSH; and FreeS/WAN, an implementation of Internet Protocol Security (IPSec) and Internet Key Exchange (IKE) for Linux.
Security in a Snap
Novell Security Manager combines seven fully integrated security applications in one package, which makes the solution easy and cost effective to install, deploy and manage. These applications provide the following security services (See Figure 1):
Firewall services
Virtual Private Network (VPN) gateway services
Virus protection
Intrusion detection and prevention
Spam blocking
Content filtering
Spyware protection
You install the complete set of Novell Security Manager applications in one simple process that takes an estimated 15 minutes. The server on which you install Novell Security Manager should be the only link between your internal and external networks. To begin the process, you insert the single Novell Security Manager disk into a bootable CD-ROM drive of a server that meets the minimum system requirements:
Minimum Pentium II or compatible CPU
256 MB RAM
8 GB SCSI/IDE hard drive
At least 2 PCI Ethernet network cards
After you boot the server from the CD-ROM drive, you navigate through the console-based Installation Menu, which guides you through the first few steps required to configure your system parameters. Thereafter, you configure and manage the system using WebAdmin.
As you can guess from the name, WebAdmin enables you to manage Novell Security Manager securely from wherever you have access to a browser and an Internet connection. With intuitive point-and-click operations, you can perform virtually all administrative functions over a link secured through Secure Sockets Layer (SSL) encryption. For example, you can use WebAdmin to do the following:
Define and edit security policies
Define networks and network groups
Define users and user groups
Manage backups and updates
Set up Syslog
Define proxy services
Configure VPN connections
Create Network Address Translation (NAT) rules
Configure Quality of Service (QoS) rules for bandwidth management
Define rules for packet filtering
Deploying Novell Security Manager is easier and less time-consuming (and therefore less costly) than installing separate products. In Measuring the Value of Integrated Perimeter Security, The Tolly Group demonstrates that deploying the integrated set of security applications that power Novell Security Manager takes significantly less time than deploying a collection of industry-leading products. Tolly tested two top solution sets: one anchored by Juniper Networks (formerly NetScreen) firewall products and the other anchored by Check Point Software firewall products.
The Tolly Group evaluated the solutions in the context of supporting an organization with 1,200 employees. As part of its evaluation, Tolly Group engineers simulated a complete deployment process, from configuring internal network servers to backing up all configurations and restoring them on a replacement system. This process took Tolly testers fewer than 10 hours to complete with the integrated set of applications available with Novell Security Manager. In contrast, the top solution sets took Tolly testers three to four times longer to deploy, with one solution set requiring nearly 40 hours to complete.
The integrated set of applications available with Novell Security Manager was also significantly easier and less time-consuming to manage. In fact, Tolly testers determined that during the first year alone, managing the top solution sets took roughly twice as long as managing the integrated applications that power Novell Security Manager. Specifically, the Juniper/NetScreenbased solution required 137 hours of support services for a set of typical management tasks over a 12-month period. The Check Point-based solution required 184 hours for the same. Managing the integrated applications that power Novell Security Manager consumed only 71 hours. (For more information, see www.tolly.com/DocDetail.aspx?DocNumber=204128.)
Strong Security Yields High Returns
In addition to being cost-effective to install, deploy and manage, Novell Security Manager maximizes your return on investment simply by doing its job. By securing your network, Novell Security Manager helps you skirt the costs associated with security breaches--and these costs can be sizable.
For example, mi2g estimates that the gamut of cyber security breaches (including hack attacks, malware, denial of service attacks and spam) cost the world economy as much as $578 billion US in 2004. (The London-based mi2g is a digital risk assessment company. For more information, visit www.mi2g.com.)
Through its seven applications, Novell Security Manager protects your network from seven different angles, helping you to avoid the financial and productivity losses to which weak security gives rise.
Great Wall of Fire
The Novell Security Manager firewall filters all in- and outbound communications traffic, serving as a strong first line of defense against unauthorized access to internal systems.
To hide your internal systems from users and systems on the Internet, the firewall uses Network Address Translation (NAT) and masquerading to dynamically translate private IP addresses into public IP addresses.
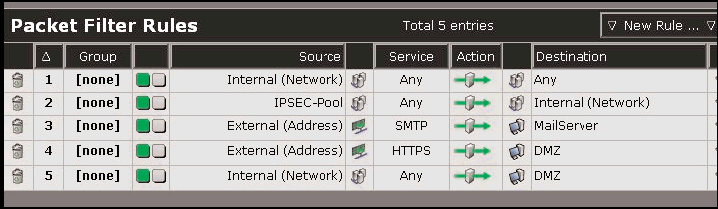
The Novell Security Manager firewall checks packets using sophisticated methods such as stateful inspection and deep packet filtering. These methods enable the firewall to examine not only packet headers but also content. This means that using WebAdmin you can create highly specific rules for blocking or allowing traffic. (See Figure 2.) As you would expect, you can create rules to block or allow traffic based on source and destination addresses and port numbers. You also can create rules that permit or deny packets based on the protocol used and on specific features or commands unique to that protocol. For example, you can create rules that deny FTP packets containing Put or Get commands.
Figure 2: Using WebAdmin, you can create highly specific rules that the Novell Security Manager firewall uses to block or allow traffic.
The Novell Security Manager firewall also guards against denial of service attacks, which surfaced as the second most costly security breach among respondents to the 2004 CSI/FBI survey. (For more information, see www.gocsi.com.) The Novell Security Manager firewall guards against denial of service attacks by monitoring the handshaking that occurs between internal and external servers attempting to establish a connection. For example, to guard against Transmission Control Protocol (TCP) SYN flooding, the firewall verifies that TCP packets flagged SYN (synchronize) and ACK (acknowledge) are legitimate and that their sequence numbers are logical.
In addition, the Novell Security Manager firewall includes comprehensive proxies for all of the commonly used Internet protocols, including the following:
HTTP
Domain Name Service (DNS)
Socks
POP3
Simple Mail Transfer Protocol (SMTP)
These proxies prevent direct connections between internal and Internet systems and, more important, scan packet contents to ensure they conform to the rules you create. Using WebAdmin, you easily enable and disable specific protocols by enabling or disabling the associated proxy. By default, and as any truly secure firewall should, the Novell Security Manager firewall disables all proxies. You also control which of the proxies' features are enabled (such as content filtering and caching) and which of your internal systems can use each proxy.
Private Communications over the Public Net--VPN Gateway
Integrated with this firewall, the Novell Security Manager VPN gateway enables your organization to use the Internet for a secure, cost-effective, remote-access solution rather than lease private lines. As one of the fully-integrated applications, the VPN gateway enables you to easily deploy and manage VPNs. The Novell Security Manager VPN gateway supports VPNs built using Point-to-Point Tunneling Protocol (PPTP), Layer 2 Tunneling Protocol (L2TP) or IP Security (IPSec).
The strong point of a PPTP VPN is that it requires minimal configuration at both ends of the connection--your end and the user's end. Users need enter little more than the IP address of your VPN gateway to get things going. You need to enable the PPTP VPN feature and walk through a few simple screens in WebAdmin that enable you to specify preferences for settings such as encryption strength. The PPTP VPN encrypts data using Microsoft Point-to-Point Encryption (MPPE), which uses the Rivest, Shamir and Adleman (RSA) algorithm and supports 40-bit or 128-bit keys stateside and 40-bit keys outside the U.S. (The supported encryption strengths are dictated by PPTP and MPPE--not the VPN gateway.)
VPNs built using IPSec are generally considered more robust and secure because IPSec supports several transmission options and more and stronger encryption algorithms. For example, when you set up an IPSec VPN, the Novell Security Manager VPN Gateway enables you to choose to transmit data in one of two modes: transport or tunnel.
In transport mode, the VPN gateway does not encapsulate IPSec VPN packets but ensures packet integrity and offers you the option to encrypt packet payloads.
In tunnel mode, the VPN gateway encapsulates IPSec VPN packets (both their headers and payloads) in a new packet, adds a new packet header and again ensures packet integrity while offering the option of encrypting packet payloads.
The Novell Security Manager VPN gateway's IPSec VPN function supports several different encryption methods:
Data Encryption Standard (DES) (56 bit)
3DES (168 bit)
Rijndael (128, 192 and 256 bit), selected by the National Institute of Standards and Technology (NIST) as the candidate for the Advanced Encryption Standard (AES)
Serpent (128-bit), a NIST finalist for AES
Twofish, also a NIST finalist for AES
Blowfish, the predecessor to Twofish
The Novell Security Manager VPN gateway integrates well into your existing environment, offering support for several different clients and authentication sources. The IPSec VPN function supports the native Windows IPSec client, any other IPSec client (that complies with the IPSec standard), the Astaro Secure Client and the Mac OS X VPN client, enabling you to mix and match these clients to balance ease of implementation with the level of security required for different user groups. You can authenticate IPSec VPN users against Novell eDirectory, a Remote Access Dial-In User Services (RADIUS) server or Active Directory.
Stop the Spread--Virus Protection
Whether or not users are connecting to your network by way of a VPN, any time they send or receive email, they could be sending or receiving a virus. While seemingly only irritating, viruses cost organizations an estimated $100,000 US in recovery costs per event, according to the ninth annual Virus Prevalence Survey conducted by ICSA Labs. (For more information, see the report online.) mi2g estimates that malware cost the global economy as much as $202 billion US in 2004, which works out to roughly $336 US per Windows-based computer. (For more information, see www.mi2g.com.) The point is, viruses are costly, so stopping them has become a top priority.
Novell Security Manager Virus Protection helps your organization block viruses by scanning inbound and outbound regular and Web-based email. Virus Protection scans messages and attachments exchanged using regular e-mail programs over standard e-mail protocols (SMTP and POP3). It also scans messages and attachments that users access by way of their browsers over HTTP and FTP.
Novell Security Manager Virus Protection employs multiple detection methods to detect and block viruses that spread via e-mail and Web traffic:
Using virus signatures, Virus Protection compares regular and Web-based e-mail messages and attachments with known patterns contained in a database of 100,000 virus signatures maintained by Kaspersky Lab (www.kaspersky.com). Kaspersky Lab is a global leader in anti-virus expertise, continuously monitoring the Internet for new viruses from three labs around the world.
Virus Protection uses sophisticated rules heuristics to identify messages and attachments that contain patterns and behaviors that resemble known classes of viruses.
Virus Protection executes suspicious code (such as archived files or scripts and macros) in a protected environment to determine whether or not it is safe.
Using WebAdmin, you tailor Novell Security Manager Virus Protection to meet the needs of your organization. For example, you can specify that questionable messages be dropped, rejected with error notification to the sender, passed through to the recipient with a warning or quarantined for later evaluation.
No Trespassing--Intrusion Protection
Viruses are a costly nuisance, but the threat of network intrusion is potentially even more dire--and increasingly common. Of the respondents to the 2004 ECrime Watch survey, 43 percent reported an increase in e-crimes and intrusions from the previous year, and 70 percent admitted that their organization's network had suffered at least one e-crime or intrusion. (CSO magazine conducted the 2004 E-Crime Watch survey in cooperation with the CERT Coordination Center and the U.S. Secret Service. For more information, see the report online.)
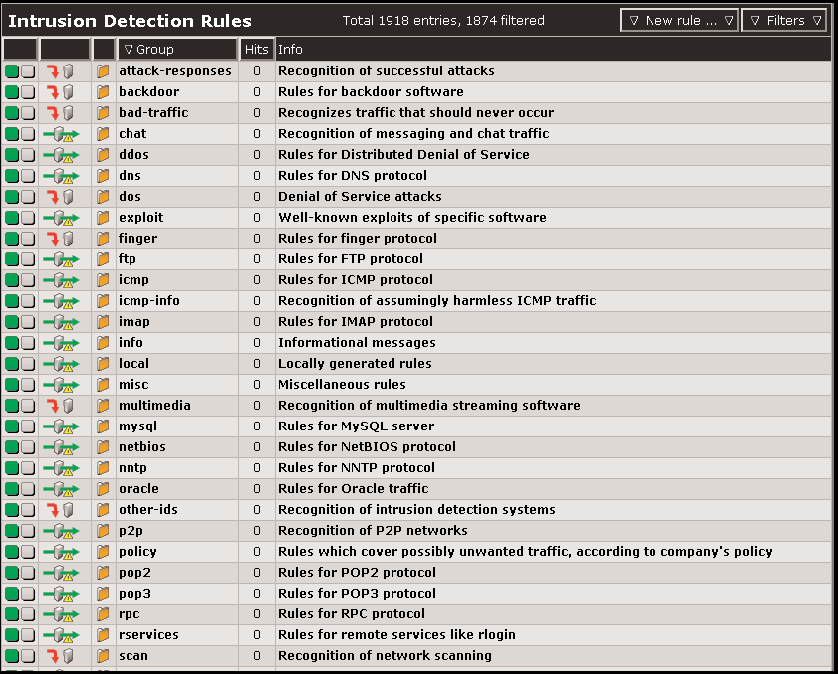
To protect your organization from intruders, Novell Security Manager Intrusion Protection scans inbound network traffic and consults the Snort database. (See Figure 3.) The largest open source intrusion detection project, the Snort database contains more than 2,000 patterns indicative of a variety of attacks:
Hostile probes, port scans, backdoor probes, illegitimate interrogations and host sweeps
Denial of service attacks (such as TCP SYN floods)
Attacks that exploit weaknesses in network protocols such as DNS, FTP, ICMP, IMAP, POP3, RPC, SNMP and x11
Attacks that exploit application programming errors in internally-developed software and Common Gateway Interface (CGI) scripts, as well as in popular applications and databases, such as Oracle, MySQL, ColdFusion and FrontPage
Attacks that exploit the vulnerability of messaging and chat traffic
Figure 3: To protect your network from intruders, Novell Security Manager Intrusion Protection consults the Snort database, which contains more than 2,000 patterns indicative of a variety of attacks.
When Novell Security Manager Intrusion Protection identifies patterns that point to an intrusion, it notifies you about the incident. You set the thresholds that indicate when you want to be notified about suspicious traffic. You also can configure Intrusion Protection to work with the firewall to immediately block what it pegs as intruder traffic. In other words, Novell Security Manager provides both intrusion detection and intrusion prevention.
You tailor Novell Security Manager Intrusion Protection to suit your organization's performance needs. You can enable, disable or customize any of the 2,000 rules that detect intrusion patterns or create new rules of your own. You also can dictate that Intrusion Protection perform certain classes of tests only on traffic from specific servers. For example, you can configure the system to execute e-mail-related tests only on traffic to and from your e-mail servers. The rules you change or add are applied immediately; you don't need to reboot the firewall for them to take affect.
Slicing Spam
Compared to the threat of network intrusion, spam might sound like some kind of joke and little cause for worry. But don't be fooled: spam takes a significant toll on employee productivity--and lost time is lost money. The 2004 National Technology Readiness Survey revealed that Internet users in the United States spend an average of three minutes deleting spam every day they use e-mail. This means that the 169.4 million adults that are online are collectively wasting 22.9 million hours per week trashing spam. Based on the average wage, that's $21.58 billion US a year just to get rid of unsolicited messages. (For more information, see www.rhsmith.umd.edu/ntrs.)
Apply this three-minute average to the number of employees in your organization and work out costs using their average wage. How serious does spam look now?
Novell Security Manager Spam Protection detects and blocks unsolicited e-mail messages to spare your network users from the annoyance (and your organization the cost) of spam. On each incoming e-mail message, Spam Protection performs a series of tests to accomplish the following:
Sender Address Verification and other tests determine whether messages come from legitimate e-mail servers
Realtime Blackhole Lists check e-mail addresses against databases of known spammers
Header Analysis checks packet headers for false or altered information and for addresses with invalid characters (such as !, % and /)
Body Analysis identifies words and word patterns that are typical of spam
Based on the results of the tests you have enabled or disabled, Novell Security Manager Spam Protection assigns each message a score that indicates the probability of it being unsolicited. Messages with scores that exceed thresholds that you set or that are from a blacklisted source are dropped, rejected with error notification to the sender, passed to the recipient with a warning or quarantined, depending on the rules you create. You also can create whitelists and blacklists to specify e-mail sources that you know to be legitimate and illegitimate, respectively.
Rule the Surf--Content Filtering
Like spam, searching the Web for fun takes a toll on productivity--and you might be surprised how often your network users are out joy-surfing. Of the 500 U.S. employees interviewed for the Websense Web@Work survey, 51 percent confessed to spending between one and five hours per week surfing the Web at work for personal reasons, with the average being 3.3 hours per week. (For more information, see the report online.) If your company has only 10 employees who make only $20 US per hour, then, based on this average, your organization is paying its employees a combined total of $33,000 US a year for nothing.
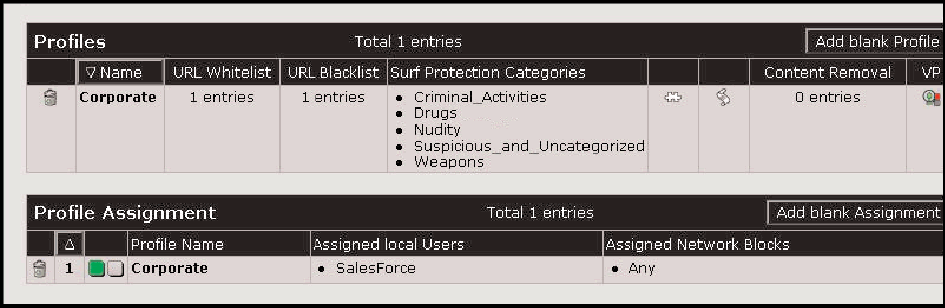
Novell Security Manager Surf Protection increases employee productivity by blocking inappropriate activities on the Web during working hours. (See Figure 4.)
Figure 4: Novell Security Manager Surf Protection increases employee productivity by blocking inappropriate activities on the Web during working hours.
Using WebAdmin, you define Web access policies quickly and precisely, choosing from among 60 categories of inappropriate Web content such as pornography, online shopping, illegal software, music and computer games. As users request Web pages, Novell Security Manager Surf Protection checks a database of 20 million Web addresses. Maintained by Cobion (a division of ISS, www.iss.net), this database is the largest available for any commercial URL filtering system. In addition, Surf Protection accurately identifies questionable Web sites using the white- and blacklists that you create and several other classification methods, including the following:
Text Classification to rate Web pages using factors such as the frequency of word occurrences and word combinations
Optical Character Recognition to capture and analyze text on images
Visual Object Recognition to categorize Web sites based on symbols, logos and trademarks
Porn Detection to identify pictures with high concentrations of non-facial flesh, using flesh tone images and face recognition
Similarity Comparison to compare new images with similar images from already-classified Web sites
To ensure high performance, Novell Security Manager caches URLs as they are requested so that it needs to reference the master database only the first time a URL is requested.
Spy versus Spyware
Like spam and surfing, spyware (and its sidekick adware) slows productivity, in this case by subjecting users to a constant flux of pop-ups. But spyware does more than that. For one thing, it increases demands on your already-taxed help desk, which has to field the calls for help to remove spyware. Spyware also slows computer performance, particularly older PCs with limited memory. Perhaps most concerning, spyware gathers and transmits information about how your users are using their computers. In the worst case scenario, spyware tools called keyloggers can record and transmit users' keystrokes, which can reveal the very passwords that protect your network.
Like spam, spyware is a money-maker for somebody somewhere, so as you would expect, it is an increasingly common problem. In fact, of the 352 IT managers who participated in the Websense Web@Work survey, 92 percent estimated that their organization's network had been infected by spyware at some point. (See the report online.)
Desktop anti-spyware products are a start to solving the problem, but are not ideal for a network of any size. For one thing, they detect and remove spyware only after it's already on the inside. For another thing, do you have the time--is it even possible--for you to check and maintain every single client?
Novell Security Manager Spyware Protection detects and blocks spyware at the network's edge. Spyware Protection also ensures that if users plug in an already-infected laptop, the spyware source of the infection is unable to transmit information to the Internet.
To detect and block spyware traffic, Novell Security Manager Spyware Protection compares HTTP traffic against the Cobion/ISS content-filtering database, which continuously searches more than 2 million Web sites to identify sources of spyware. This database is the largest and most current database of its kind and continues to grow.
Referencing the Web content database, Novell Security Manager Spyware Protection determines whether a requested URL is a spyware URL and whether a server to which data is being sent is a spyware server. Spyware Protection can then block the spyware infection or spyware communication.
Currency
Novell Security Manager starts at $315 US (354 Euros) for one server license plus ten devices. With this license, the Novell Security Manager firewall, VPN gateway and Intrusion Protection are activated and ready to roll. You can activate Virus, Spam, Surf and Spyware Protection with the Secure E-Mail and Secure Web subscriptions, at a cost of $341 US (383 Euros) and $380 US (426 Euros), respectively.
A Secure E-mail subscription activates Virus and Spam Protection for e-mail traffic.
A Secure Web subscription activates Virus, Surf and Spyware Protection for Web traffic.
Finally, because a security product is only as secure as it is current, you need upgrade protection, which starts at $66 US (74 Euros). Upgrade protection ensures that you automatically receive the latest patches and updates for your base software and for your subscriptions.
In other words, for one Novell Security Manager server and ten devices, the base software, both subscriptions and upgrade protection will cost you $1,101 US (1,168 Euros). I'll leave you to calculate the cost of your alternatives. red N
Firewall
During May 2001, the two T1 trunks between Gibson Research Corporation (GRC) and the Internet were repeatedly flooded with millions of malicious 1500-byte IP packets. The distributed denial-of-service attacks blocked both legitimate inbound and outbound traffic. After several days of attacks, GRC approached the FBI, which informed the company that until it suffered economic damages totaling USD $5,000, no crime had even been committed. (For more information, see the report online.)
Intrusion Protection
When Vitek Boden was denied a position working on a computerized sewerage system for the Maroochy Shire Council in Queensland, he sought revenge. For four months, Boden repeatedly hacked undetected into the system, causing countless malfunctions. The most serious of these malfunctions led to the release of hundreds of thousands of liters of sewage into public areas along Australia's Sunshine Coast. (For more information, see the report online.)
Virus Protection
Despite widespread virus reports, users are enticed to double-click unsolicited e-mail attachments. The Zafi.D virus spread like Christmas cheer last December by disguising itself as a happy holiday greeting. As of February 23, this trick was still working, accounting for 27.6 percent of reported virus attacks. A Sober.K variant, responsible for 10 percent of reported attacks, takes a decidedly different approach to luring users, many of whom can't resist the promise of Paris Hilton in the flesh. (For more information, see Paris Hilton Worm Spreads, Feb 23, 2005.)
Spam Protection
When spam takes a server down at SparkNet Interactive, customers notice. As an e-zine marketing firm, SparkNet handles two million e-mail messages daily. Each spam attempt costs $300 to $500 US in out-of-pocket expenses alone. As of March 2005, spam cost SparkNet $3,000 US, which is already about half the amount that it spent in 2004. (For more information, see The Cost of SPAM.)
Security Speak
Computer Virus Executable code that replicates. Computer viruses attach themselves to files and thereby spread quickly. Viruses typically deliver some sort of payload, which might be an annoying message or a program designed to destroy files or reformat hard drives. Viruses also can cause trouble by consuming storage space and memory, thereby degrading performance.
Trojan A type of malware that causes damage, unexpected system behavior and compromises the security of systems but does not replicate. (A Trojan that replicates is technically a computer virus with Trojan qualities.)
Malware Malicious or unexpected program or code, such as a computer virus, Trojan or worm.
Deep Packet Filtering A firewall filtering method that permits or denies packets based on their actual contents rather than only their header information. (Static filtering permits or denies packets based only on source and destination address and port numbers.)
Network Address Translation (NAT) A method that firewalls use to map all of your internal IP addresses to its own "safe" IP address, rendering internal systems essentially invisible to users and servers on the Internet. Denial-of-Service (DOS) Attacks Disruptions to a network service (provided by an e-mail or Web server, for example) through various means to prevent legitimate users from using the service. A common denial-of-service attack involves flooding a server with requests for service.
Intrusion Detection A system that gathers and analyzes information from various areas within a network to identify possible security breaches, including attacks from outside and inside the network (that is, intrusions and misuse, respectively). (Novell Security Manager provides both intrusion detection and prevention.)
Virtual Private Network (VPN) A method for providing remote users with secure access to your network over a public telecommunication infrastructure, most commonly the Internet. VPNs are less costly than expensive counterparts, such as owned or leased lines. Through tunneling protocols, VPNs create virtual tunnels for your data by encrypting it at the sending end and decrypting it at the receiving end.
Intrusion Prevention A system that, like an intrusion detection system, monitors network traffic for suspicious activity. However, an intrusion prevention system also takes immediate action when it determines that the network has been penetrated. Action is based on rules created by the network administrator. (Novell Security Manager provides both intrusion detection and prevention.)
Worm A virus that resides in active memory and duplicates itself. Worms use parts of an operating system that are automatic and usually invisible to the user. Worms are typically noticed only when their uncontrolled self-duplication consumes system resources to the point of slowing or halting system performance.
Spyware Protection
InternetWeek.Com recently reported that British authorities foiled an attempted bank robbery, at the root of which was an increasingly popular form of spyware called a keylogger. The thwarted criminals were preparing to transfer £220 million from the London offices of a Japanese bank to ten different bank accounts. (Keyloggers Foiled in Attempted $423 Million Bank Heist, March 17, 2005.)
* Originally published in Novell Connection Magazine
Disclaimer
The origin of this information may be internal or external to Novell. While Novell makes all reasonable efforts to verify this information, Novell does not make explicit or implied claims to its validity.