Bright Ideas: Efficient Windows Management with ZENworks 6.5 Suite
Articles and Tips: article
09 Dec 2004
Novell ZENworks is the complete IT management solution that allows you to manage the entire lifecycle of desktops, laptops, servers and handheld devices. With ZENworks, you get an end-to-end identity-driven systemsmanagement solution that automates IT management processes through your network using business policies. Those policies describe how ZENworks is to behave in your environment. The latest version of ZENworks offers a full-featured set of integrated tools that give you an intelligent way to manage all the resources of your diverse systems through your asset lifecycle with a single solution. It decreases, and in many cases eliminates, administrative burdens, increasing enterprise-wide business efficiency.
Novell ZENworks gives you an easy, automated way to manage all of your diverse systems and changing work environments, across multiple server platforms and multiple operating system environments and versions. Administrators save time through efficient, centralized management and users gain simple and seamless access to the resources they need from anywhere, even the Internet. Research shows that companies which deploy Novell ZENworks can eliminate 36 percent of employee downtime.
In this article, we discuss how ZENworks 6.5 functions in a strictly Windows environment, as well as some best practices to provide maximum efficiency and performance for your ZENworks systems in any environment. We discuss only Active Directory environments, but these features and concepts work equally as well in an NT Domain system.
What is ZENworks?
ZENworks consists of eight components that manage various devices in your system: Desktop, Server, Linux, Data, Handheld, and Patch Management, along with Personality Migration and Software Packaging. (See Figure 1.)
Figure 1: ZENworks provides complete IT resource management for enterprise wide efficiency.
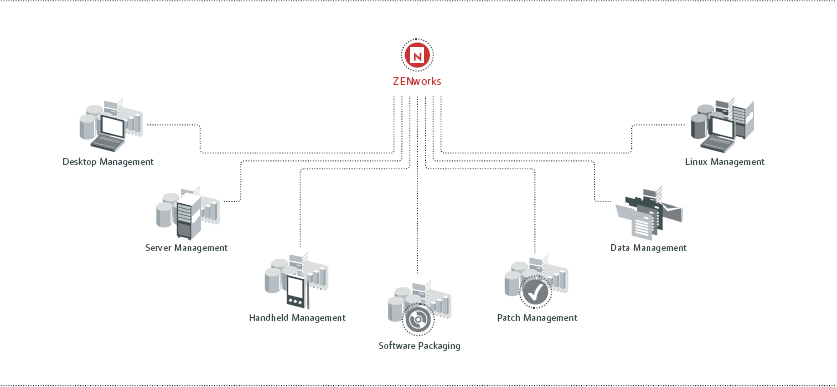
ZENworks Desktop Management provides capabilities to image your workstations and laptops, bringing users' desktop personalities along to the new OS. You can also use ZENworks to deliver and heal applications, deliver operating system policies, diagnose problems via remote control, and manage your devices through business policies that you administer from a central location.
ZENworks Server Management provides support for delivery of installation and update packages and content to your servers. ZENworks Server Management also monitors your servers and system traffic, alerting you when your systems or networks need attention. In addition, ZENworks Server Management provides inventory and remote management functions for your servers.
ZENworks Linux Management provides the delivery and installation of application, OS and updated RPM files to your Linux devices. ZENworks Linux Management takes the pain out of RPM files by automatically determining the RPM file dependencies and installing any updates or dependent RPMs that must be installed.
ZENworks Data Management takes users' data files from their laptops and workstations and automatically encrypts the files and synchronizes them to a Web server for safe keeping. ZENworks Data Management will also synchronize these files back down to any number of devices, keeping your users' various systems up to date with their latest data files. Users may also download and upload these files from any browser.
ZENworks Handheld Management delivers policies to manage and secure your PDA devices on your network. ZENworks Handheld Management delivers applications and content to your handheld devices, performs inventory and even retrieves files off of the device and sends them back to the central server.
ZENworks Patch Management analyzes all of the devices in your environment and compares them to known patches that are automatically delivered to your local ZENworks Patch Management server from PatchLink's centralized systems. Once determined that a patch is required in your system, the patch, with your approval, is automatically delivered and installed on all systems in your environment. More than 33 vendors deliver patches to PatchLink, which verifies them and then publishes them electronically to your local ZENworks Patch Management server. With ZENworks Patch Management, you won't be caught without the appropriate patches on your systems.
ZENworks Personality Migration captures the desktop settings along with personal configurations such as bookmarks, application settings, background and users' OS configurations as well as system-wide system settings. In addition to the personality, ZENworks Personality Migration also collects the user's data files. The data, applications and personal settings can then be restored to the same or another machine, as well as another operating system or updated application. With ZENworks Personality Migration, a user can be up and running on his new machine or system quicker because it's more familiar with the custom personality restored.
ZENworks Software Packaging provides a customized version of InstallShield's AdminStudio product. AdminStudio ZENworks Edition captures and creates MSI files from scratch and even converts your existing AXT/AOT files to MSI installations. AdminStudio ZENworks Edition contains a tool named Tuner which helps you create MST files to customize your MSI installations. Lastly, ZENworks Software Packaging contains a distribution tool that automatically creates Application and Distribution objects in your eDirectory for delivery of MSI applications to your desktops, laptops, servers and users.
Active Directory Windows Environments Before ZENworks
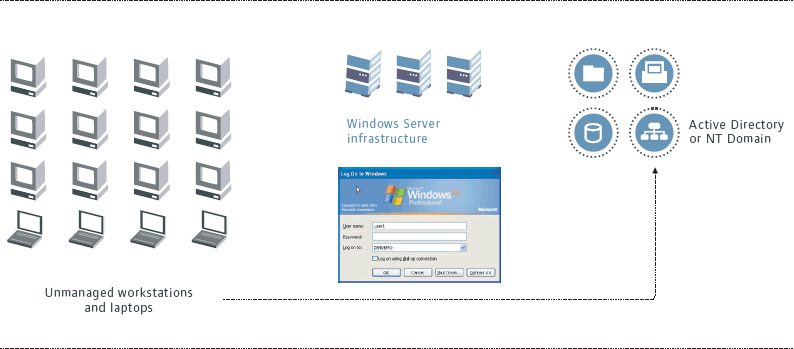
A computer that is a member of the domain in an Active Directory environment will allow the user to log into Active Directory through the Windows client. When the user logs into the workstation, any group policies and user environments that are saved on the server are downloaded to the computer and the user's desktop is presented.
After being prompted by the Windows client on an unmanaged workstation, when a user enters their username and password for their Active Directory account, the Windows client authenticates them to Active Directory and downloads their desktop information. (See Figure 2.)
Figure 2: User on an unmanaged workstation will be prompted to provide their user name and password for their Active Directory account.
Introducing ZENworks To Your Active Directory Windows Environment
Now let's see what happens in this Active Directory environment when we add ZENworks into the picture.
Adding ZENworks Server Components
The first step in introducing ZENworks into your environment is to install the ZENworks server components on a backend server. ZENworks consists of three back-end components: eDirectory, ZENworks Middle-Tier server and ZENworks server. (See Figure 3.)
Figure 3: ZENworks consists of three back-end components: eDirectory, ZENworks Middle-Tier server, and ZENworks server.
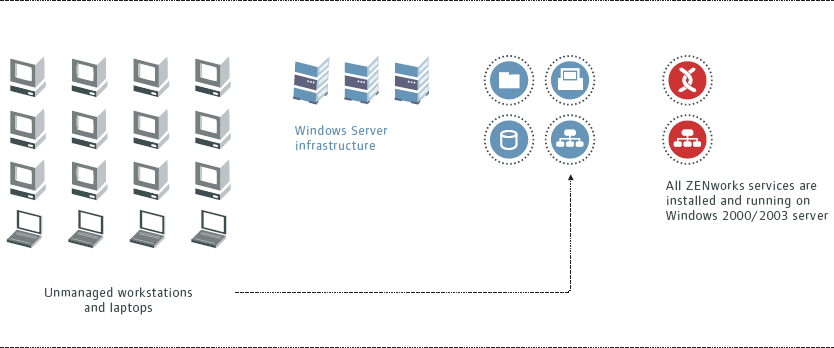
The ZENworks server contains the services that support the various ZENworks features. The ZENworks Middle-Tier Web server is responsible for receiving requests from managed workstations and servicing those requests by either communicating with Windows file systems or to the ZENworks server. Responses to those requests are then communicated back to the managed workstations via the ZENworks Middle-Tier server.
All of the ZENworks back-end services may be installed on Windows 2000 or Windows 2003 servers. ZENworks back-end services don't require a dedicated server, so they can be installed on any of your back-end servers. You may want to consider some performance and scalability issues for your environment, but we'll talk about those later.
Once you install the back-end components, install the agent on the devices you want to manage.
Adding ZENworks Management Agents
To manage a device through ZENworks, you must install the ZENworks Management agent on that device. Although you can install the agent on the desktop in several ways (e.g., manual installation, login scripts, etc.), ZENworks includes a tool called the Agent Distributor that remotely connects to any desired workstation and automatically installs the agent. Workstations can be targeted either by entering a DNS or IP Address or by selecting computers from an Active Directory or NT Domain.
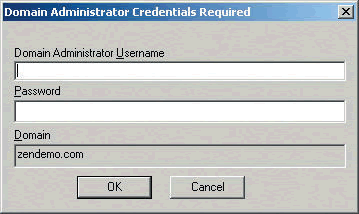
You can launch the Agent Distributor from a Windows desktop or server. When first launched, the distributor application displays a dialog prompting for the domain administrator and credentials. (See Figure 4.)
Figure 4: The Agent Distributor will prompt for the domain administrator and credentials.
Once you enter the authentication information, the distributor application prompts for the agent MSI file and the workstations you want to target. (See Figure 5.)
Figure 5: Once the authentication information is entered, the distributor application will prompt for the agent MSI file and the targeted workstations.
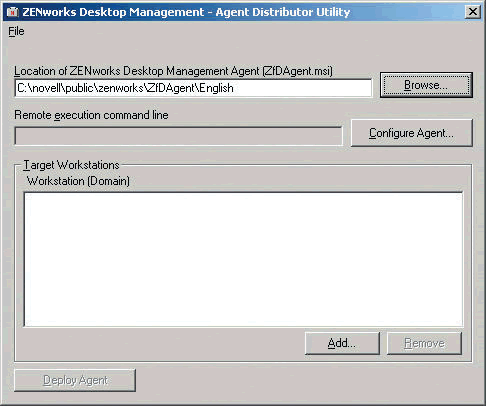
From this dialog, clicking the Add button allows you to browse through the domain and select the target computers. When you have selected all of the computers you want to receive the agent, click OK to return to the same dialog with a list of your targeted computers. (See Figure 6.)
Figure 6: The Agent Distributor utility will display a list of the target workstations.
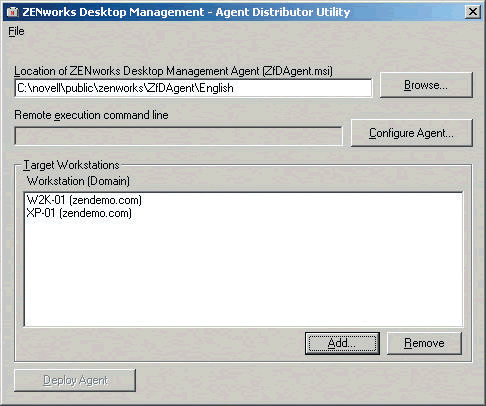
Now click the Configure Agent button and configure the settings you want the agent to deploy. (See Figure 7.)
Figure 7: Choose the Desktop Management Agent settings wanted for the target workstations.
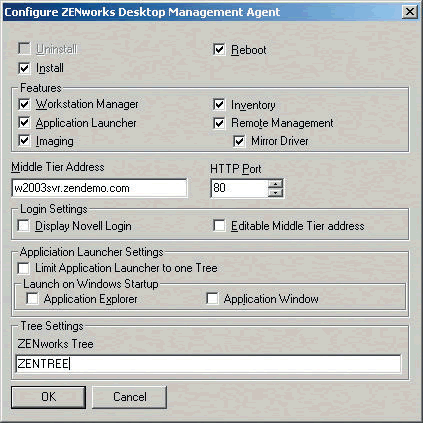
From the Configure ZENworks Desktop Management Agent dialog, identify all of the agents you want installed, including Workstation Manager, Application Launcher, Imaging and Inventory. Also specify the DNS name or IP address of the Middle-Tier Web server that will accept requests from these devices. You can also configure the agent to limit its search to a single eDirectory tree and whether you want the Application Window or Application Explorer to automatically start at each user login.
Once the agent is configured, click OK. Then you are back to the Agent Distributor dialog where you can click on the Deploy Agent button to begin the process of authenticating to the remote computer and installing the agent. You'll see a status dialog which keeps you informed on the progress of the deployment.
Adding Nsure Identity Manager into the Mix
When the ZENworks Management Agent communicates with the ZENworks back-end services it authenticates to eDirectory as either the workstation or as the user. To authenticate as the user to eDirectory, and make that authentication silent, the username and password must be identical to the username and password stored in Active Directory. If the username or password does not match between the two directory services, the user is prompted for an alternate username and password for eDirectory. Normally, you don't want that to happen.
To keep usernames and passwords synchronized, ZENworks includes Novell Identity Manager (formerly DirXML) with the drivers for Active Directory and NT Domains and password synchronization. Using Novell Identity Manager, the system automatically creates users in eDirectory and synchronizes the passwords between Active Directory and eDirectory.
Active Directory Environment with ZENworks Deployed
Now let's closely follow the steps that occur in the Active Directory environment when your ZENworks back-end services are installed and the workstation has the ZENworks Management Agent running.
Step 1
The Workstation Boots When the workstation boots up, the ZENworks Management Agent service automatically starts. The agent first tries to communicate with the Middle-Tier Web server and authenticates as the workstation to eDirectory. If this is the first time the workstation has attempted to communicate with ZENworks and a policy has been configured to import workstations, then ZENworks automatically creates a workstation object in eDirectory to represent this device.
If any policies, applications or content have been associated with this device in eDirectory, the workstation receives this information and begins to process the associations, i.e., place the content, enforce the policies or install the application.
Step 2
The User Logs In When the user logs into the workstation, the Windows Client prompts them to enter their Active Directory username and password. (See Figure 8.)
Figure 8: After the Desktop Management Agent is installed, the user logs into the workstation just like they did without the agent.
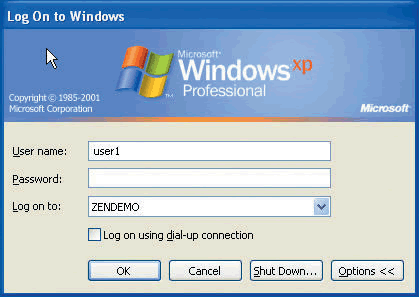
When the user enters the username and password, the ZENworks Management agent retrieves these credentials and uses them to automatically connect to the Middle-Tier Web server and authenticate to eDirectory. If the credentials match, the user is silently authenticated to eDirectory. If the credentials do not match, then the user is prompted to enter credentials for ZENworks.
Once the user is authenticated to eDirectory, the ZENworks Management agent and ZENworks Application Launcher communicate with the Middle-Tier Web server and retrieve any policies, content or applications associated to the user in eDirectory. The associated components are then transmitted to the workstation and installed or presented to the user.
Step 3
File Retrieval When the user clicks on a ZENworks delivered application, for example, it is often necessary for the ZENworks Management agent to retrieve the files from the back-end services and install the application onto the local workstation.
When the ZENworks Management agent needs to retrieve files from back-end servers in the environment, it first attempts to get these files using the standard Windows Kerberos/CIFS protocols. These protocols are used to retrieve files from standard Windows shares on remote servers. If the user has appropriate rights to read the requested file, then it is downloaded and installed on the workstation.
If the request through CIFS fails (traditionally because the workstation is not connected to the LAN environment), then ZENworks attempts to retrieve the files through the ZENworks Middle-Tier Web server. First, the request is sent to the Web server. Then the Web server attempts to retrieve the file using the standard CIFS protocol and the credentials of the user. If the user has rights to those files on the share, then the Web server retrieves those files from the back-end server and forwards them to the workstation through the Web server.
Using the Web server to retrieve the files allows ZENworks to continue to deliver its services even if the user is connected through the Internet and does not have direct LAN or VPN access to the enterprise network. Also, this method doesn't compromise security because ZENworks uses the credentials of the user to access those files, allowing Active Directory rights to dictate if those files should be accessed.
Importance of the Middle-Tier Server
As you can see the ZENworks Middle-Tier server plays an important role in delivering ZENworks services to the managed workstations. To provide maximum scalability and performance, ZENworks allows you to have any number of Middle-Tier servers in your environment. Each ZENworks Middle-Tier server then delivers features and content to their connected workstations. (See Figure 9.)
Figure 9: ZENworks Middle-Tier servers deliver features and content to their connected workstations.
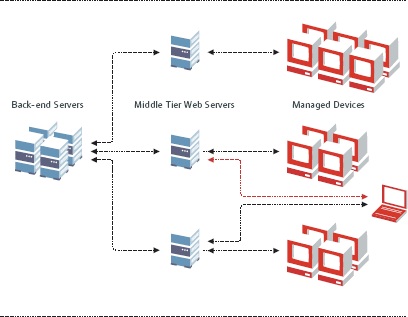
Each workstation is assigned a local Middle-Tier server that services their requests locally. Laptops that move from location to location can get their Middle-Tier Web server address as part of a DHCP tag. This allows them to always be connected to the local Middle-Tier server and get the best performance for their current area.
Middle-Tier Server Availability, Scalability and Performance
Because the ZENworks Middle-Tier server is critical in a pure-Windows environment, you must consider the reliability, scalability and performance of your Middle-Tier servers.
Scalability Versus Performance
Scalability is often defined as the ability to increase processing by adding more resources. Performance refers to the response times presented under a typical load. Note, however, that increasing scalability does not necessarily increase performance. The goal of scalability is to provide a constant, acceptable performance even as the load increases.
You can scale by adding additional hardware, such as CPUs and memory, to the server (known as scaling up), or by adding additional servers to a server farm that share the load (known as scaling out). With each scaling method, be familiar with the bottlenecks that can arise within the system so you choose the best method.
Scalability Versus Availability
Availability is defined as the ability for a resource to be accessed. You can achieve high availability when a resource is always available and users can consume it at any time. Although a greater scale may provide some perceived increases in availability, a single point of failure may still exist if resources are stored on only a single server.
You can only achieve high availability through the use of additional resources such as server farms.
Middle-Tier Performance
Several factors contribute to the scale that can be achieved on a Middle-Tier server. The following factors have the greatest impact:
Speed and number of CPU processors on the Middle-Tier server
Connectivity speed between Middle-Tier server and eDirectory
Amount of data to push to each user and workstation, particularly force-cache applications and policies
Amount of RAM available on the Middle-Tier server
Staggered login times and launcher refresh intervals
Using these factors, approach the architecture for Middle-Tier installations by first improving the hardware speeds on the Middle- Tier server. Once the Middle-Tier server is not experiencing high utilization, the next bottle neck would be the connection between the Middle-Tier server and the eDirectory server. Address this with a higher-speed connection between these two machines.
In addition, the Middle-Tier server in a Windows environment uses IIS as its Web server. When IIS is initially installed, it is not tuned efficiently to handle a large number of connections. Consider reviewing the tips and tricks found in a Microsoft whitepaper on how to tune a Web server.
Outside of tuning your hardware and software parameters to provide the best performance of your Middle Tier to your environment, additional configurations and architectures can be employed to increase the scalability and availability of the Middle-Tier server.
Deliver Data Through File Servers
The load on an individual Middle-Tier server is greatly reduced if the application data, etc., is retrieved via a local file server. ZENworks 6.5 automatically attempts to connect to the server through the local Windows CIFS protocols.
You can only retrieve files from a local server, however, if you have a LAN or VPN connection. The workstations that retrieve information through the Internet and are not connected to the LAN must receive their distributions through the Middle-Tier server.
You should also use the Random feature of the ZENworks Application Launcher to direct the workstations to connect at randomly different times during a specified timeframe. This spreads the number of users connecting and retrieving files across that timeframe rather than all users connecting at the same time, e.g., first thing in the morning.
Multiple Web Servers
Performance will increase as you send fewer users to a single Middle-Tier Web server. To accomplish this, direct ZENworks Management Agents on different machines to different Middle-Tier servers. A registry key maintains the DNS/IP address of the Middle-Tier server that should be contacted by the agent. You can set this address differently for sets of users during installation.
Although different users are sent to separate Middle-Tier servers, the application objects can still refer to the same storage server.
Round-Robin DNS Addressing
If you want to enhance the availability of your Middle Tier within your environment, introduce more Middle-Tier servers into the network and use DNS addressing techniques to provide a set of IP addresses for a given DNS name. (See Figure 10.) With DNS addressing, when a client requests the IP address of a given DNS name, the DNS server returns different IP addresses. This spreads the load across multiple Middle-Tier servers. When a Middle-Tier server is successfully connected, that agent uses that Middle-Tier server until the session terminates.
Figure 10: You can enhance the availability of Middle Tier servers by introducing more servers and using DNS addressing techniques.
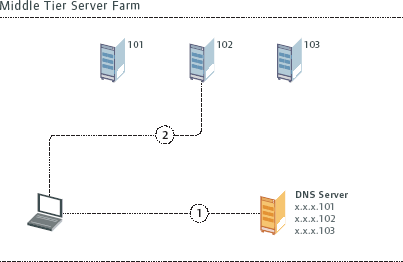
However, Round-Robin DNS has a disadvantage: it does not detect when a server in the group is disabled. This can affect the performance of the ZENworks Management Agent if it attempts to establish connections to a disabled server.
Remarkable Results:
On average, ZENworks helps companies achieve a:
42 percent increase in IT staff efficiency
45 percent increase in IT management staff productivity
$1,263 per person savings in annual user productivity
1,012 percent three-year ROI
Quantifying the Business Benefits of Consolidated IT Resource Management, IDC, October 2003
Web Switching
An alternate technique, the use of an L4 or higher switch, can be used to provide increased scalability and availability. Administer these switches to provide access to several servers being referenced by the same IP address. Then you can give your agents the same IP address and yet receive the benefits of multiple Middle-Tier servers. This configuration provides all of the benefits of the DNS Round-Robin techniques just described. A Load-Balancing switch is aware of the loads of each of the individual servers and uses that knowledge to distribute requests. Load-Balancing switches can also quickly detect when a device becomes disabled and can use this information to route requests away from the disabled device.
Additionally, when selecting a Load-Balancing switch, make sure the switch allows the agent to establish and maintain a session with the Middle-Tier server. (See Figure 11.)
Figure 11: Switching can be sustained using Microsoft's Load Balancing software.
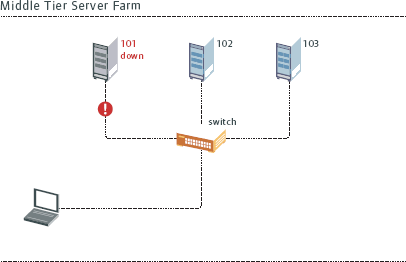
You can also sustain switching with Microsoft's Network Load Balancing software.
Improved Performance with ZENworks 6.5
Novell has improved the efficiencies in ZENworks 6.5 over the previous ZENworks 6 product to increase the throughput of the Middle-Tier server. The following performance improvements have been measured:
Authentication . . . . . . . . . . . . . . . . 83 percent improvement Policy Distribution . . . . . . . . . . . . . 82 percent improvement Application Refresh . . . . . . . . . . . . . 27 percent improvement Distribution of a 16MB Application . . . . . . 54 percent improvement
ZENworks 6.5 Best Practices Web Seminar Series
Each session of the series covers a critical piece of the resource management puzzle. By attending all five, you'll receive a complete, practical overview of how ZENworks 6.5 best practices can lead you to a more efficient, cost-effective resource management solution.
Efficient Windows Management
Learn how ZENworks 6.5 can help you reduce the cost of owning and managing Windows desktops and servers with all-new tools for agent deployment, optimized application distribution, application self-healing, identity-based policy management, personality migration, hardware and software inventory and much more ? all in a pure Windows environment.
Automated Patch Management
Failure to apply critical security patches quickly exposes your organization to attacks from viruses, worms and other Internet threats. Attend this seminar to learn how ZENworks 6.5 can help you detect software vulnerabilities early, automatically deploy patches to all the machines that need them and implement tighter security controls throughout your business.
Secure and Stable IT Environment
November 9, 2004, 1:00 p.m. EST
Learn how ZENworks 6.5 increases the integrity and stability of your whole IT infrastructure by helping you maintain a consistent, standardized operating environment that minimizes risks and reduces vulnerabilities through identity-based Policy-Driven Automation.
Leading Linux Resource Management
December 14, 2004, 1:00 p.m. EST
ZENworks 6.5 offers the most complete Linux Resource Management solution in the industry. Attend this seminar to learn how you can track, test and deploy software across all your Linux desktops and servers, quickly and consistently apply patches and software updates to all your Linux systems, and create a consistent, standardized Linux operating environment.
Rapid OS Migration
January 11, 2005, 1:00 p.m. EST
ZENworks 6.5 automates and accelerates the process of migrating to a new operating system. This seminar will show you how to develop a clear plan of action and perform a system-wide OS migration that dramatically lowers your costs and minimizes disruptions to your business.
Register today!
Conclusion
ZENworks 6.5 provides a strong ROI and efficient Windows desktop management. You can use all of its features in a pure Windows environment?right out of the box?without disrupting the user's traditional workflow!
To register for the ZENworks 6.5 Best Practices Web Seminars, visit the seminar web site.
ZENworks 6.5 runs on Windows 2000/2003 servers and does not require the Novell Client 32 to be installed throughout your environment. ZENworks also includes a leading meta-directory solution as well as software to keep your ZENworks system synchronized to your Active Directory environment. And lastly, ZENworks provides enterprise-wide tools to help you remotely distribute the agent to all devices in your system.
ZENworks 6.5 architecture allows for scalability and performance to support from the smallest to the largest enterprises. ZENworks helps you efficiently manage your Windows network. With policybased automation of your business process, it leaves you alone to complete those other tasks that are more strategic to your company.
For more information about Novell ZENworks see the product site.
* Originally published in Novell Connection Magazine
Disclaimer
The origin of this information may be internal or external to Novell. While Novell makes all reasonable efforts to verify this information, Novell does not make explicit or implied claims to its validity.