Patch Management: ZENworks Brings the Patchwork Tools to the Table
Articles and Tips: article
Ron Tanner
01 May 2004
ZENworks patch management, powered by PatchLink Corporation, is the newest component of Novell ZENworks 6.5 which helps keep your systems up to date with the latest patches you choose to deploy. (ZENworks Patch Management is also available as a standalone product.)
The Need for Timely Defense
Damages from computer viruses worldwide are astonishing. The 2003 Computer Security Institute/FBI Computer Crime Lab and Security Survey1 estimates that 83 percent of organizations experiencing virus attacks in 2002 suffered an associated loss of US$27 million. Denial of Service attacks caused additional damages of more than US$65 million. The LoveLetter virus alone inflicted more than US$8.75 billion in damages worldwide in a year in which organizations suffered a total of US$17.1 billion in virus-related costs.
The affects of virus attacks are significant. According to ICSA Labs2, an information security services provider and product certification authority, 75 percent of organizations affected by viruses experienced loss of productivity, 69 percent experienced system unavailability and 62 percent experienced corrupted files. Additional effects included loss of access to data, unreliable applications and other business disruptions.
But not all computer viruses are effective in their destructive intentions; one of the most prolific attacks in the past year has come from the infamous Klez.H virus, which has infected more than 8 million systems so far according to Trend Micro3. The Klez.H virus carries a payload designed to thoroughly destroy all files on accessible local and network drives, but a minor bug in the fully developed code prevented the attack from being carried out. Had the code been free of errors, the damage to the 8 million affected systems would have been catastrophic.
In total, security experts have reported 49 new viruses between January 1 and February 4, 2004. The following viruses were released in January 2004 alone:
Bizten Trojan
Gaobot Worm
Mimmail Worm
Opaserv Worm
Backdoor.Sdbot Trojan
Xombe Trojan
Backdoor. Threadsys Trojan
PWSteal Worm
MyDoom Worm
Hostidel Trojan
HLLW.Chemsvy Worm
Dumaru Worm
Holar G Worm
While the potential for destructive virus behavior is frightening, be aware that the greatest impact of a virus on your enterprise is almost never due to its destructive actions, but rather to the clean-up efforts after the virus hits, as well as the negative impact on system availability and employee productivity. According to ICSA Labs, these costs are generally 50 times greater than the cost of the destructive virus behavior. No matter how benign, a virus infection has the potential to significantly impact your organization.
The Urgency is Growing
Virus infection rates have increased for six consecutive years, with 11 percent of all systems worldwide being affected. ICSA Labs reports that the median recovery time per incident was four days, and the median cost of such recovery per incident was US$9,000. While viruses are most often thought to affect end-user systems, viruses attack workstations and servers alike--with the average server-related attack affecting 37 servers per affected organization. Furthermore, ICSA Labs survey results reveal that 77 percent of enterprises reported server infections causing downtime with a median downtime of three hours. To better appreciate the urgency of this problem, consider the following example of a recent virus-related attack:
The SQL Slammer Worm
The SQL Slammer worm first appeared on January 25, 2003 exploiting a known buffer overflow bug in Microsoft SQL Server database (both server and desktop versions). The worm quickly propagated throughout organizations that failed to apply appropriate patches, demonstrating that even mission-critical applications such as databases can be susceptible to attack. Once installed, the worm continuously contacted other systems using random network addressing, automatically discovering and infecting other vulnerable systems and consuming considerable network bandwidth and processing time.
Just Get the Patch
David Aucsmith, chief technology officer of Microsoft's security business unit, recently wrote5, "[Microsoft has] never had vulnerabilities exploited before the patch was known." This implies that a virus is typically developed and released after a vulnerability has been discovered, publicized and a patch provided. Looking at the life of the Blaster virus, we see that a vulnerability was reported in the system on July 1, 2003. A bulletin (MS03-026) and patch were provided by Microsoft on July 16, 2003. By July 25, 2003, public code was released on the Internet that exploited this vulnerability. By August 11, 2003, the Blaster worm and other variants were discovered in systems. (See Figure 1.) Hackers today are actually reverse engineering the patches to better exploit the vulnerability, then releasing their viruses in hopes to catch those that have not applied the patch.
Currently, users combat viruses with virus pattern updates and patches for operating systems, virus scanners and applications. Security Focus4 reported 223 vulnerabilities in Microsoft products alone that required a patch in 2003. Security Focus reports a total of 35 vulnerabilities in all the product issues it tracked in January 2004.
Figure 1:
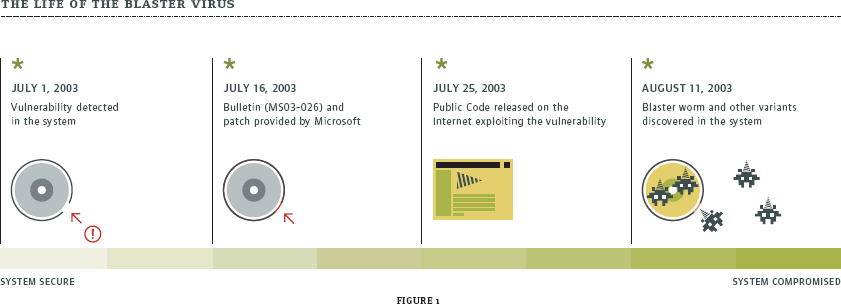
The problem is not that you simply can't get the patch for the vulnerability. Typically the problem is threefold: not knowing that the patch is available, the severity of the vulnerability and the applicability to your environment. Once you know the patch is available and should be applied to your systems, the next problem is applying that patch to all of your servers and desktops.
Even though the Blaster patch has been out for almost a year, Robert Lemos of CNET News reported on April 2, 20046: "New data from Microsoft suggests that at least 8 million Windows computers have been infected by the MSBlast, or Blaster, worm since last August--many times more than previously thought. The latest data comes from [Microsoft's] ability to track the usage of an online tool that its engineers created to clean systems infected with the worm."
"Since the January release of the tool, more than 16 million of the systems that connected to Microsoft's Windows Update service were found to be infected with MSBlast and were offered a patch and the use of the disinfecting tool," Lemos wrote. During the same time frame, roughly 8 million computer users used the tool to remove the worm and downloaded the patch to prevent reinfection. The virus is still attacking because the patch hasn't been applied to every vulnerable machine!
You've Got the Patch, Now What?
Today, if you're doing patch management, you're probably using SneakerNet (running around in your Keds manually patching each of your servers and desktops). Many system administrators today (and maybe you're one of them,) have to keep the patch state of each server either mentally or manually--either method is impossible.
According to Steve Ulfelder, a writer at Network World Fusion7, "...many network administrators essentially tracked patch status in their head, fixing holes on the fly. But in the past two years, the sheer complexity of networks and number of patches have rendered this approach ineffective."
The SQL Slammer and Blaster worms managed to wreak havoc despite the availability of patches to eliminate associated bugs. Even the release of patches causes significant problems for your organization because you have to dedicate resources to monitor security alerts; research associated problems; and acquire, test and implement the relevant patches on systems throughout your enterprise. The effort it takes to keep up with security alerts and patches for Microsoft Windows is overwhelming. The Forrester Research, Inc., January 2004 report, Best Practices: Desktop Security8 states: "A growing number of viruses, worms and other attacks threaten to compromise desktop security. The sheer volume of security threats, combined with the need to manage remote locations or business units, puts significant pressure on IT to develop standard security policies at the desktop. Remote or mobile users pose additional risks, but mobile access has also become a critical productivity enabler. The cost of responding to a single incident without consistent policies for antivirus, patch and configuration management can be extremely high. One company with 5,000 desktops estimated that the Blaster worm cost it $900,000 in IT costs alone. Legislation and compliance requirements also raise specific security issues for industries such as health care and financial services."
Let's make a quick calculation. Say you are the administrator of a medium-sized network of 10 servers and 1,000 desktops. Assuming a very conservative number of two patches need to be applied each week to these systems, you would need to perform 404 installations and reboots each day. Assuming a rapid 30 minutes for each installation and reboot, it would take you 202 hours each day to apply patches! If we consider the average US salary of a Network Administrator to be US$61,900 (as revealed by the 2003 InfoWorld Compensation Survey9), then it would cost approximately US$6,011.44 per day to install the patches on your systems. That would cost US$1,562,974.40 annually--the equivalent of more than 25 full-time network administrators solely dedicated to installing the patches. It's no wonder many systems aren't getting the patches they require.
Obviously, the biggest problem is deploying appropriate patches to each of your systems in a timely manner and also keeping track of which patches have been applied to which machines. Manually doing this simply won't cut it. It's cost-prohibitive and ineffective at protecting your systems.
ZENworks Patch Management Can Help
ZENworks Patch Management removes the burden of discovering, retrieving and deploying patches. Now, to deploy or not deploy the patch is your only question. ZENworks Patch Management automates the process by discovering security alerts, retrieving the patches and deploying the right ones to the right machines. In addition, saving you from those patch headaches, ZENworks Patch Management reduces the costs of ensuring that your systems are secure.
ZENworks Patch Management, powered by PatchLink Corporation, is made up of two main components: PatchLink Update Server and the PatchLink Update Agent. The server components are installed on your Windows servers and the agents need to be deployed to all of your managed devices. ZENworks Desktop Management can install those agents throughout your network. But if you don't have ZENworks Desktop Management, ZENworks Patch Management comes with its own Active Directory deployment tool and install executable.
Once your agents are deployed, they analyze all the software and patches that have been applied to the workstation or server using intelligent, patent-pending Patch Fingerprinting technology. That information is then automatically transmitted to the ZENworks Patch Management server. From there, the server determines the patches required for the systems in your environment.
After detecting the vulnerabilities in the system, ZENworks Patch Management automates the tedious process of researching and deploying the appropriate patches to each individual system based on its level of exposure. The necessary patches will be automatically delivered to each system and then applied appropriately. You can also configure ZENworks Patch Management to require a minimum set of patches for each system, based on its operating system and applications. ZENworks also makes sure each system that matches the specified configuration receives and has all appropriate patches applied. This ensures that all systems are protected, even new systems that are introduced into the network. Because ZENworks closely monitors your environment, if an application which requires a patch is installed on a system, ZENworks detects the installation and immediately sends and applies the needed patch.
How It Looks
ZENworks Patch Management is fully administered through a browser-based interface. When you initially launch the browser administration tool, you're presented with the home page. (See Figure 2.)
Figure 2: ZENworks Patch Management is fully administered through a browser-based interface.
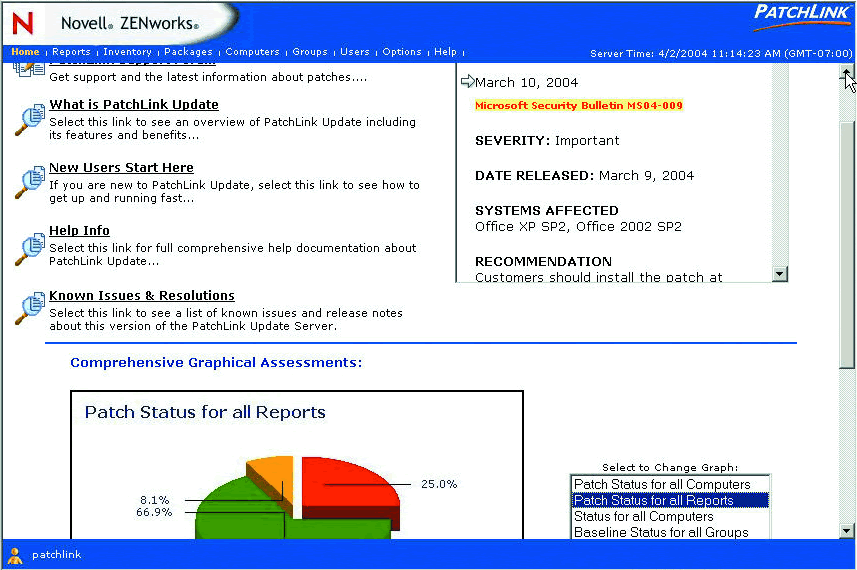
A scrolling window on the home page alerts you of any immediate or new security vulnerabilities, and is constantly updated by the back-end subscription services. You can also gain a sense of how the patches have been applied across your enterprise by a graphical representation.
You configure and manage your patch system from the main administrator's Web page. You also have access to all the reports which list all of the patches your systems require. (See Figure 3.)
Figure 3: You have access to all the reports which list all the patches your systems require.
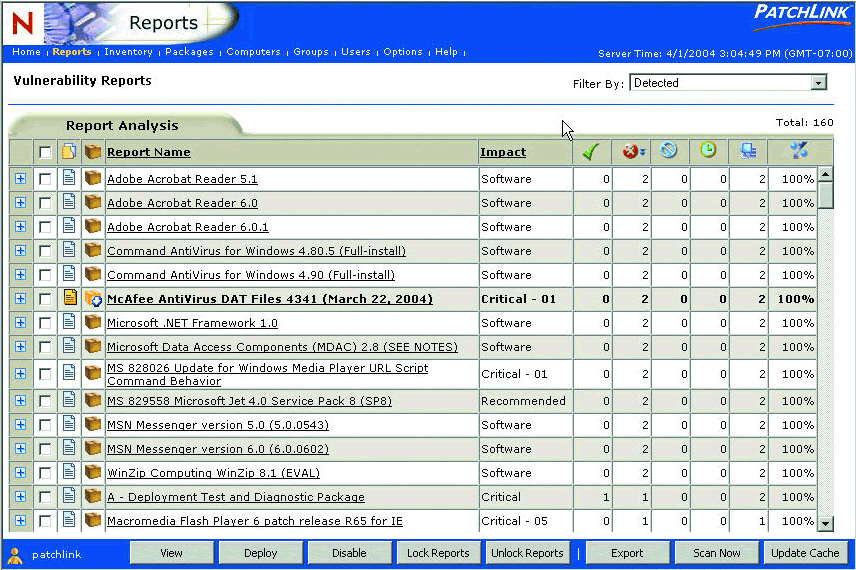
You can see all of the patches for the systems in your enterprise from the Reports page. Although ZENworks Patch Management can apply patches to many different types of systems, only the reports that are relevant to the systems in your environment are listed. Just click the plus sign to see the vulnerability report detail. (See Figure 4.)
Figure 4: Just click the plus sign to see the vulnerability report detail.
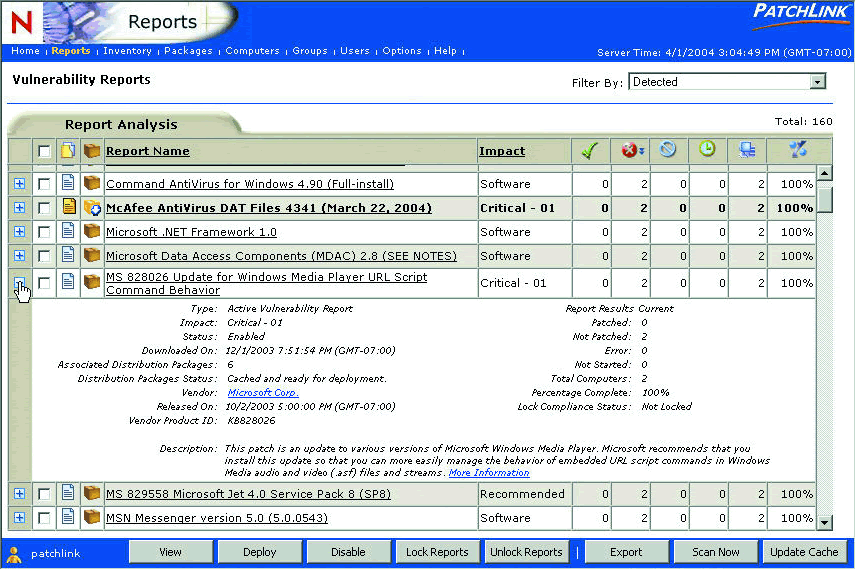
The vulnerability report detail provides information on the vulnerability and its severity, along with which programs need the patch. It also displays the number of systems in your environment that require the patch. This information includes the public security bulletin information, as well as PatchLink Systems' assessment of the problem. Each patch is tested and verified by PatchLink Systems prior to its release for your installation.
From here, you can choose to target individual machines with these patches.
Targeting All Machines
The overall goal of ZENworks is to make your life easier. It enables you to configure the system once through Policy-Driven Automation. Then it constantly monitors your system and automatically performs the necessary tasks. With ZENworks Patch Management, you can put patches into a Mandatory Baseline list of targeted groups, e.g., all machines running Windows XP. ZENworks Patch Management will then automatically make sure that every device running Windows XP has all mandatory patches applied to it.
To configure your system to automatically deliver patches to targeted groups, first select the Groups link to go to the Groups page. Then choose the group you want to target. For example, in Figure 5 the WinXP group is targeted. (See Figure 5.)
Figure 5: Notice that the targeted WinXP group here is a System Computer Group and is based on the Windows XP platform.
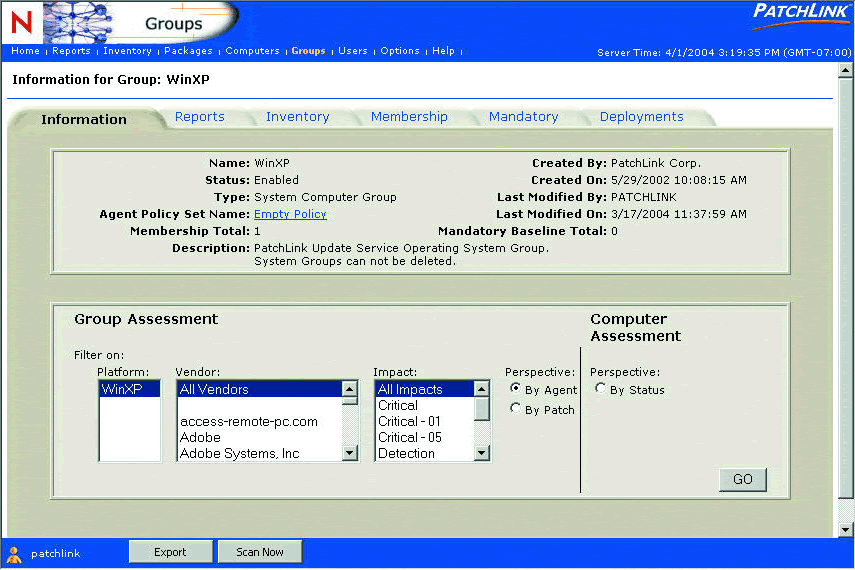
Notice that the group in Figure 5 is a System Computer Group and is based on the WinXP platform. This system group is automatically defined by ZENworks Patch Management; all devices carrying the Windows XP operating system will automatically be included in this group when the agent first communicates with the ZENworks Patch Server. Click on the Mandatory Baseline tab and you'll see the list of patches that have been identified as being required for all machines running Windows XP.
If you want to add a patch to the list, simply click the Manage button on that page and select the patches you want to require. After you have identified your required patches and placed them in the Mandatory Baseline list, ZENworks Patch Management automatically checks all Windows XP systems to verify that each required patch is installed. If one isn't, ZENworks automatically transmits the missing patch to that non-compliant system and installs it. (See Figure 6.)
Figure 6: If a required patch is not installed, ZENworks automatically transmits the missing patch to the non-compliant system and installs it.
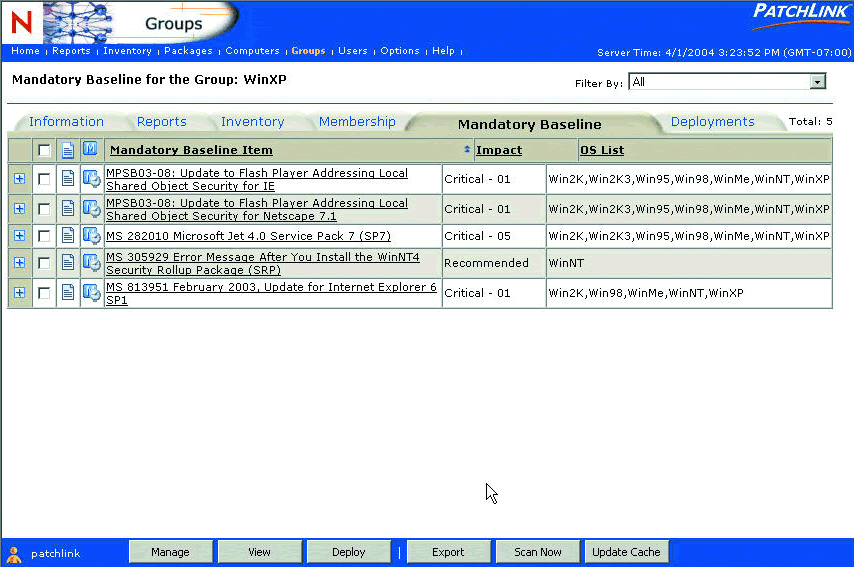
Now you can sit back and let ZENworks Patch Management take care of the time-consuming task of verifying the need for each patch, and then delivering and installing only those you deem necessary for your environment. ZENworks Patch Management addresses the most costly portion of patch management--the deployment of patches. Now you won't need those 24 extra network administrators at that exorbitant cost to keep your systems up to date.
Keeping You Up On The Latest Patches
Now that you have the detection and deployment in hand, ZENworks Patch Management can help you remain current with the latest patches. Periodically, the ZENworks Patch Management Server automatically connects with PatchLink servers in the network and downloads new patches as they are released.
After receiving notification of a vulnerability and patch, PatchLink automatically tests and verifies each patch. Once testing is complete, PatchLink servers transmit the vulnerability reports and patches out to your server.
After ZENworks Patch Management servers receive a new patch, the server notifies you via e-mail or the management console that the new patch has been received and can be applied in your environment. When you want to apply the patch across your entire enterprise, just add it to the groups you want to have it and ZENworks takes care of the rest.
Patch Transmission Security
To ensure that all patches that systems receive have come from a legitimate and trusted source, ZENworks Patch Management uses state-of-the-art security and encryption measures to validate that a patch is being received from a known source. All transmissions, whether through your network or via the Internet, are encrypted and require digital signatures. This gives you the comfort of knowing the patches came from a valid PatchLink service and that your ZENworks Patch Management system is deploying patches to workstations that are appropriate. Workstations in turn validate they are receiving patches from the appropriate ZENworks Patch Management server.
ZENworks 6.5 Gives It All
With the ZENworks 6.5 release, expected this summer, Novell will release ZENworks Patch Management in the box. ZENworks Patch Management is also available independently as a standalone product.
With ZENworks Patch Management subscriptions, you can easily deploy patches to all of your Windows and NetWare systems. With additional subscriptions, you can deploy to all of the PatchLink supported systems.
So now your employees don't have to experience loss of productivity, system unavailability or corrupted files from a virus infection because you didn't have time to deploy every patch that was needed on every machine. They don't even have to lose access to data or have unreliable applications. Let ZENworks Patch Management take that weight off your shoulders and automate the entire process so you can spend your valuable time doing those more important tasks you've never gotten around to. For additional information and to get started on automatically patching your systems today, visit www.novell.com/zenworks.
Notes:
www.trendmicro.com/vinfo/virusencyclo/ default5.asp?VName=WORM_KLEZ.H&VSect=S&Period=All
Best Practices: Desktop Security by David Friedlander and Jan Sundgren, January 30, 2004.
* Originally published in Novell Connection Magazine
Disclaimer
The origin of this information may be internal or external to Novell. While Novell makes all reasonable efforts to verify this information, Novell does not make explicit or implied claims to its validity.