Security Central and Beyond
Articles and Tips: article
01 Apr 2003
What does it mean to be secure? These days, there are many things to be concerned about. So many, in fact, that you may find your head swimming with all the issues affecting network and data security in the 21st century. Consider the following:
The onset of war and terrorist attacks have made many take a much closer look at system reliability and security, and consider whether or not data may be available in these catastrophic situations.
A recent analysis of the SQL Slammer worm's path that ripped through the Internet (http://www.caida.org/outreach/papers/2003/sapphire/sapphire.html) indicates it was doubling in size every 8.5 seconds, and had infected 90 percent of the vulnerable hosts within 10 minutes of release!
"The 'virtual enterprise' model blurs boundaries. In other words, the threat factor is changing--'outsiders' are [now] 'insiders.' Ninety percent of all security breaches will come from inside the enterprise because people once considered outsiders are really insiders now that trading partners have access to each other's environment." --Price of Information Security, Gartner, 2001.
Threats from within, threats from without, electronic threats, physical threats--what's a network manager to do? Couple this with your users' constant need to access their information--from any place, at any time--and you have the makings of a serious tension headache. We're talking "turn out the lights and lie very, very still."
If that's not an option--and we all know it isn't--you may want to step back and look at the security of your network in a different way. This article can't describe every security feature in Novell solutions--that would require a magazine the size of an unabridged dictionary--but it can help you organize and present your security needs in a way that's more appropriate for the reality of today's complex network environments. Talking about security in a way that corresponds to the business issues your executives are wrestling with is a quick way to move what you have to say to the top of their agendas.
This is what Novell has been doing while fine tuning its vision (http://www.novell.com/solutions/): Novell Nterprise, Novell Nsure, Novell exteNd and Novell Ngage. While Nsure encompasses the bulk of Novell identity management and security infrastructure technology, adding Nterprise and exteNd to the mix rounds out your Net capabilities in those areas that directly affect Net security, but aren't specifically security components themselves. Wrapped around industry-leading Novell technologies, Novell Ngage gives you access to the guidance and expertise you need to pull everything together. (See Figure 1.)
Figure 1
Give 'em a Ring
Since network and data security overlay all aspects of network infrastructure and operations, it's clear network security isn't a single entity, but a collection of products, features and practices all working together in harmony. But before we all start chanting in unison, let's lay the foundation for our discussion:
The point of all your security efforts is to protect your systems and data while still making them available to your users. In today's world, they need access from a myriad of locations and through a variety of methods.
Security should be definable on an individual basis--not tied to a location or a specific type of hardware.
Even though users may want to get at anything from anywhere, safety dictates that you temper these exuberant wants with the recognition that one method of getting to data may not be as easily protected as another.
For just about any security play, the Internet will be your sandbox. That means standards are crucial, heterogeneous environments are the rule, and you won't know exactly what's coming around the bend. Don't hide from these facts; embrace them! Be the Internet.
To better evaluate these concepts, consider a pebble dropped in a still pond, and the concentric rings formed as the ripples move outward. Your network is doing the same thing (See Figure 2.) As users become more sophisticated, their need to access data and systems will move outward, away from the safety of the corporate headquarters (HQ) and into more-dispersed and less controlled environments.
Figure 2
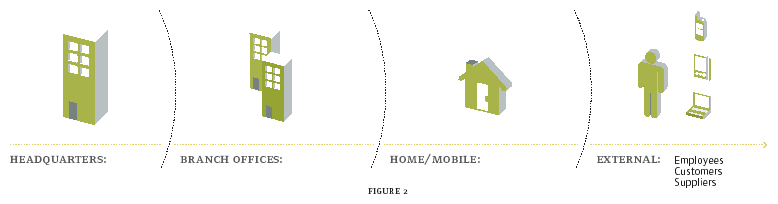
While contemplating the rings of your net may not inspire the same inner peace derived from studying ripples on a pond, it's a vivid metaphor for the movement of your net users away from a Brick-and-Mortar HQ.
Viewing your network security through this paradigm will help you map your current security practices and Novell's security capabilities to the business realities your executives are facing. You can demonstrate how security should be taken "along for the ride" in any new business initiative, and identify weaknesses in your current strategies and tactics that may cause problems as your business continues to push out and away from HQ.
Following is a look at the security challenges associated with the rings of your Net infrastructure--and how Novell solutions provide a harmonious blend of technologies and capabilities for delivering security across the spectrum. After all, it's your Net.
Ring 1 headquarters
Your HQ forms the basis for providing effective security processes and practices across all the rings of your Net. As such, it forms the foundation for most of your security solutions. This value will in turn "trickle down" to the other rings. In other words, the security plans you implement at HQ will be leveraged throughout the other rings. One ring to rule them all...
Because of this, it makes sense to meditate on three fundamental issues in order to evaluate your current level of security, and understand the value your current infrastructure is capable of providing across all rings in your Net:
Identity Management
A fundamental aspect of security in today's dispersed computing environments is the ability to recognize your users. Security is no longer about an office or cubicle, but a person--wherever that person may be. All aspects of security should be associated with, and delivered through, the concept of identity rather than location.
Novell eDirectory
(www.novell.com/edirectory/) forms the foundation of Novell Nsure solutions. Novell eDirectory offers a scalable, cross-platform foundation for enabling secure identity management solutions. eDirectory gives you the ability to create an electronic identity for most anything that touches your network, and then define the relationships between those different identities. Because an important part of relationships is access control, eDirectory provides the infrastructure to support granular access policies that can be applied anywhere.
Infrastructure Integration
With a robust identity and relationship foundation like eDirectory in place, you now need to consider how to create identity harmony within your existing infrastructure. Novell provides two powerful corollaries to eDirectory that can help your entire Net infrastructure feed from the same identity trough:
Novell Account Management
(www.novell.com/products/edirectory/accountmanagement/) lets you define and enforce a consistent security policy across your Net by synchronizing user accounts or identities across NetWare, Windows, UNIX and mainframe server platforms. Novell Account Management results in single sign-on across your Net infrastructure, centrally managed user accounts, passwords and authentication credentials, and account changes or updates that are instantly synchronized enterprise-wide.
DirXML
(www.novell.com/dirxml/) takes the idea of integration a step further to include databases and applications in addition to server platforms. DirXML builds on eDirectory to create XML "pathways" that automatically distribute new and updated identity information across every designated application and directory, based on your existing business rules. Communications can be one-way or bidirectional, and the authoritative source for specific types of data can be preserved. This greatly reduces data-management costs, while guaranteeing the accuracy and timeliness of common data across all your critical systems. Editor's Note: For more information on DirXML, look for the feature article that will appear in the May/June issue of Novell Connection magazine.
Ease of Management
With all your platforms and systems sharing identity information through eDirectory, the task of managing your Net infrastructure just became a whole lot easier. Can you feel the synergy? Better yet, eDirectory gives you a powerful Web-based management tool to make maintenance of your environment as simple as possible.
Since the release of NetWare 6, Novell has been on the path toward comprehensive Web-based management tools, powered by the Apache Web server that's now Novell's preferred Web server. iManager (see Figure 3), iMonitor and Novell Remote Manager (NoRM) give you the ability to "manage from anywhere," and provide a comprehensive set of administrative capabilities, including remote console for NetWare, so you have true flexibility to manage your Net as needed.
Figure 3
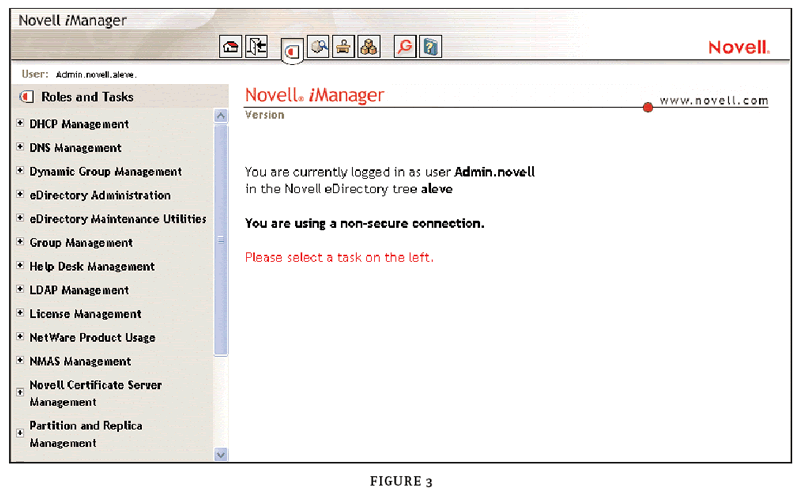
Novell iManager is an intuitive web-based tool available from any computer that has an internet connection and a web browser. You can even perform a number of administrative tasks, such as resetting a user's password from a Windows CE or Pocket PC handheld device!
Data and System Access
Users are the most important asset in your organization and at the same time its biggest security liability. Net security must be able to provide very granular access to the data and systems that users need, while at the same time protecting those users--and your Net--from themselves.
Closely related to identity management, data and system access capabilities let you define exactly how each identity may utilize the resources on your Net. These capabilities also include the concept of an infrastructure for managing and providing consistency across your Net with regards to access policy.
Access Management
One of the fundamental security aspects often overlooked is a sound corporate security policy (See Rethinking Security at www.novell.com/connectionmagazine/2002/01/security12.pdf). All the technology in the world won't solve your problems if you haven't properly defined your security plan and goals up front. One thing the technology can do is help you refine your existing policies as weaknesses become apparent over time. Here again, eDirectory plays an important role in providing the ability to properly manage authentication and authorization on your Net. Fundamental features such as an extensible schema, object inheritance and dynamic access controls, which have been part of eDirectory since its introduction nearly 10 years ago, provide the foundation for consistent access policies across your Net.
By leveraging the powerful foundation of eDirectory, Novell ZENworks (www.novell.com/zenworks/) further extends the policy-based management framework for implementing consistent security and access policies throughout your Net. By automating and standardizing all the mundane infrastructure management in your environment, you not only reduce costs, but free yourself up to concentrate on the strategic aspects of your Net. Instead of spending your day battling a thousand IT gremlins, you can begin looking down the road, developing your Net to serve the enterprise more effectively and helping users to be more productive. Now that's the kind of thing your executives will notice!
ZENworks now offers policy-based management for desktops, servers, mobile computers, handheld devices and on-demand application delivery via Web services or thin-client. This provides a comprehensive, strategic solution that lets your organization realize its full potential while still maintaining control over assets that are valued the most.
Advanced Authentication
SecureLogin (www.novell.com/securelogin/) provides single sign-on access to the network by encrypting and storing authentication credentials in any 100-percent compliant LDAP v3 directory. When used in conjunction with eDirectory, SecureLogin stores individual authentication information in the highly secure Novell SecretStore associated with each User object in eDirectory.
Novell Modular Authentication Service
(NMAS) (www.novell.com/products/nmas/) lets you implement a flexible access-control solution using one or more authentication methods to protect your data and systems. NMAS supports smart cards, proximity cards, tokens, biometrics in addition to PKI and simple and advanced passwords. Its integration with eDirectory provides centralized management of all the authentication methods you're using. NMAS lets you define a granular security policy based on data and system sensitivity, rather than forcing you into a cookie-cutter approach to creating your security plan.
Business continuity
What happens when the unthinkable occurs? Whether it's a hardware breakdown, a physical disaster or the latest iteration of the electronic bogeyman, your systems must be able to evade trouble and recover quickly in the event of a failure. The difficulty some vendors face is that they can't always simply bolt this type of security onto an existing product; it must be designed in from the beginning--and this typically isn't easy to do.
As the foundation for your Net security strategy, the security policies, processes and technologies you implement at Ring One will form value propositions that extend across all rings. The work you do here will pay big dividends as you begin to approach the needs and problems caused by users moving away from Ring One.
Avoid and Evade
Novell BorderManager (www.novell.com/bordermanager/) is one of Novell's principal answers to the question of "avoid and evade." Its powerful directory-integrated features let you effectively manage use of the Internet in both directions. BorderManager uses an array of features and technologies to monitor and restrict outgoing access, as well as restrict the breadth and manner of incoming communications and access.
In addition to the BorderManager access and security suite, Novell has always made security a primary concern in the design and architecture of its core products and solutions. Consider the following products which form the foundation of the Novell Nterprise offerings:
eDirectory was designed, not from any prior technology, but from the ground up as an enterprise solution. Initial development took place over nearly five years, with design decisions made based on existing standards and what would provide the most robust platform for the enterprise. This attention to detail resulted in such powerful features as multi-master architecture, extremely efficient inter-replica communications, the Novell International Cryptographic Infrastructure (NICI) and the tightly integrated Novell Certificate Server.
Similarly, for the past 20 years NetWare has been known as a stable and well-protected platform that's difficult to hack. How many stories have you heard about NetWare servers that stay up for years? How many viruses have you heard of that infect a NetWare server? And just about every NetWare server break-in includes a first step of "access the server console," which doesn't bode well for Internet threats.
GroupWise has shown it is largely invulnerable to the rash of e-mail viruses plaguing Internet users over the past few years. When all those other systems were dropping like flies, it was business-as-usual for GroupWise. How much is this peace of mind worth to you and your organization?
Beyond platform stability and resistance to attack, there are additional technologies you can leverage to develop robust business continuity. Clustering has been available since the days of NetWare 5, and has evolved to support up to 32-node clusters. Support for hot-swappable components, hardware and software RAID (software RAID 1 and RAID 5 are in NetWare 6.5), and robust storage management options are making it much easier to protect valuable data and recover that data, if necessary. (See Nakoma. The Future Looks Bright for Storage Management at www.novell.com/connectionmagazine/2002/10/nakoma92.pdf.)
Are your ears ringing yet?
As you can see, there's a lot to Ring One. As the foundation for your Net security strategy, the security policies, processes and technologies you implement at Ring One will form value propositions that extend across all rings. The work you do here will pay big dividends as you begin to approach the needs and problems caused by users moving away from Ring One.
Ring 2 the branch office
As you take that first step away from your HQ, the branch office presents similar security concerns to those described above, but on a much smaller scale. The most critical factor is one of integration. How can you extend all the HQ systems to support those at the branch office? This has typically resulted in significant additional expense in equipment, systems and support to link the branch office with HQ, and provide the same level of service and protection available directly at HQ.
While this is a Novell Nterprise solution to the problem of branch office integration, you can also apply Novell exteNd and Novell Nsure solutions to branch office integration. Organizations are looking to consolidate applications and services at HQ--that would be Ring One--while still making them available securely and efficiently to those branch office users--which would be Ring Two. This consolidation results in much greater efficiency and simplicity for your infrastructure by putting all your critical data in one place, where it can be properly managed and protected.
As described in Ring One, Novell Nsure identity management, data and system access techniques give you granular control over the Who, What, When and How of your Net. Meanwhile, Novell Nterprise Branch Office (www.novell.com/products/branchoffice/) resolves much of this problem by allowing you to create a multi-function appliance that efficiently links your branch offices to your HQ, using the Internet as your link--thus cutting the costs of pricey dedicated lines. Existing security and management policies are transparently extended to your distributed locations. (See Go the Distance with Novell Nterprise Branch Office at www.novell.com/connectionmagazine/2003/02/tech_talk_1.html.)
Ring 3 home users/mobile users
This is probably the fastest growing segment of your organization's employees--people who need to be productive from someplace other than a traditional office. This poses several new problems for your Net--the principal one being that you're no longer master of the domain. However, with a harmonious HQ security plan like that discussed for Ring One, you can overcome these obstacles and provide a useful--and secure--remote environment for those in your organization who need it.
Obviously, the key to remote computing is the Internet. You need the infrastructure to securely extend your presence onto the Net so employees can access what they need, using the tools they have available remotely. This infrastructure can be organized into three categories:
Web services
Although a highly overused term, "Web services" describes the ability to repackage your data and systems so they're consumable via a Web browser. No special client software is necessary.
Novell exteNd (www.novell.com/solutions/extend/) is a suite of business solutions that let you transform your current business functions into standards-based Web services, and securely deliver them via a portal or other Web application.
Novell NetMail is an easy-to-deploy email and calendaring system that simplifies the complexities and lowers the costs of deploying a traditional in-house e-mail system. NetMail easily integrates with any standards-based e-mail client, allowing your end-users to select their preferred mail client. NetMail makes it economical to support large numbers of mobile clients through a highly scalable, secure and extremely reliable e-mail system.
Novell iChain (www.novell.com/products/ichain/) provides a protective cover for your Web Infrastructure. It sits "in the flow" of Internet communications directed at your enterprise, and is capable of providing a variety of benefits: "SSLizer" dynamically protects your privileged communications; reverse proxy greatly enhances the scalability of your Web servers; and Web forms and data presentation can be dynamically personalized, based on the identity of the recipient.
NetWare 6.5 now includes some powerful new Java 2 Enterprise Edition (J2EE) capabilities that greatly enhance its ability to serve up applications to your Web users. (For more information on NetWare 6.5, check out The Grass Really is Greener.)
Web conduit
For our purposes, a Web Conduit is any product or technology that opens a channel to existing systems, rather than repackaging the systems themselves.
Novell BorderManager includes Virtual Private Network (VPN) services, which enable your company to securely connect the corporate intranet with other intranet sites, remote users and business partners, using the public Internet. The information transmitted across the VPN via the Internet is encrypted to prevent unauthorized access by eavesdroppers. In addition, the information is checked for accuracy to detect hacker tampering. BorderManager VPN services support both IP and IPX protocols, allowing users to connect to your corporate network via an Internet link. In addition, Novell BorderManager VPN services integrate with Novell eDirectory to simplify VPN management and administration. Novell BorderManager is highly scalable--it can support up to 256 sites per tunnel, and can handle up to 1,000 dial-in users per server. BorderManager offers VPN clients for all current Windows platforms.
Novell iFolder is a powerful new technology that allows users' files to automatically follow them everywhere. It provides secure, encrypted file storage to protect files from unauthorized access and automatically synchronizes any changes to iFolder files throughout the user's personal iFolder environment. For added security, you can even access iFolder files without copying them locally by using the NetStorage tool, available with NetWare 6, to provide WebDAV-based access to iFolder files. No client needed.
Managing remote devices
"IDC believes corporations will embrace policy-enforced client security (PECS) to deal with the explosive growth of mobile computing. We believe PECS will have a major impact on addressing the security concerns regarding "transitory users" (e.g., laptop, PDA and mobile users who move around)." IDC, 2003.
The key to policy enforcement is identity, and Novell knows more about identity than anyone else. The ZENworks suite of policy-based management tools was one of the first directory-enabled "killer apps" that plainly demonstrates the need for identity-based management. Now, ZENworks for Handhelds (www.novell.com/products/zenworks/handhelds/) makes it easy to centrally manage handheld devices. Your IT personnel can use ZENworks for Handhelds to distribute software or content to handheld devices, manage password and backup policies, maintain current hardware and software inventory records, and standardize handheld configurations for programs, buttons and more. As a result, end-users can enjoy uninterrupted access to essential resources without worrying about how to maintain their handheld devices.
Ring 4 external users
This ring represents your most distant Net users, including partners, suppliers and customers. Fortunately, the same Web-enabled infrastructure that provides a secure environment for your roving employees can also serve your external users. As with all security issues, the key is identity. Using eDirectory as the foundation of your identity management infrastructure makes it much easier to extend that environment to anyone with whom you might need to exchange or share information.
DirXML lets you create a separate directory tree for your external users and tie it directly to the internal systems used to manage data for and about those users. iChain then provides secure access and authentication to the Web applications and services you have developed and integrated via Novell exteNd.
Novell is also helping drive standards in this regard through participation in The Liberty Alliance--a consortium of companies collaborating to provide a standard for managing identities on the Internet in a decentralized manner. Designed for customer relationship management (CRM), it allows consumers to create accounts at a site that supports the Liberty standard, and link their identities to any affiliated sites at which they already have an account. A consumer can then sign on to a Liberty-enabled site using a single ID and password, and visit any other password-protected sites that support the standard without having to sign in again. You can learn more about Liberty Alliance and Novell participation and support for the effort at www.novell.com/solutions/liberty/.
Ringing the security bell
At the end of the day, security is a holistic blend of processes, products and technologies. The basis for the harmonious interaction of all these pieces is identity, and Novell has spent the last 10 years creating the most effective identity-management tools on the market. Novell's open, standards-based approach lets you integrate existing infrastructure and be better prepared for the uncertainties of the future.
You know the threats aren't about to go away, and your users' needs aren't going to get any less complex--so why not create a robust, identity-based infrastructure that lets you manage those threats while still providing your users with what they need as they ride the rings away from HQ and toward new business opportunities of the 21st century? Sounds like Novell is speaking your language.
Putting it into practice
The Novell vision describes a secure world without information boundaries. In the interest of "eating its own dog food", the Novell IS&T division has been making serious efforts to implement its strategy with its own employees.
Over the past few years, this effort has culminated in the creation of a secure Novell Innerweb (see figure 4) with a wide variety of services for novell employees. These services include:
Front-page access to company headlines and employee announcements
Internal Web pages for many Novell groups and departments, including Sales, Finance, Human Resources and many others.
A corporate directory powered by Novell eGuide
A portal for accessing and updating applications, installing printers via iPrint and storing corporate documents using iFolder accounts (without the iFolder client)
Direct portal access to the Novell IS&T department
Web-based access to GroupWise mailboxes
Figure 4
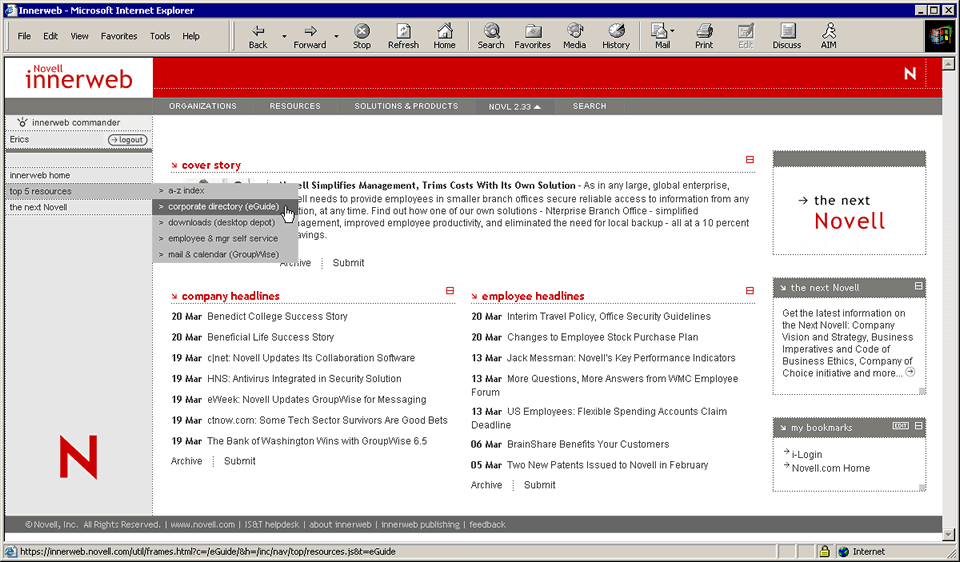
Novell is pushing the leading edge of identity-based infrastructure with its integrated web initiative. The Novell innerweb is an important step along this path.
These web services have greatly increased employee communication and productivity, and decreased the effort and cost of providing other forms of employee communication.
Employees enjoy greatly improved access to tools and resources without overburdening the help desk for support.
The innerweb is securely accessible using an employee's existing username and password from any location worldwide using a standard web browser. The self-service access to applications, benefits, and other self-serve information and services has significantly decreased help desk calls and enabled support personnel to spend their time where it's really needed.
But Novell isn't stopping there. The eDirectory foundation of the innerweb infrastructure makes it possible to create secure, customized web views for anyone interacting with Novell. This includes employees, customers, suppliers, partners and others to who Novell has granted access, via edirectory, who need to get to information and services.
The integrated web initiative, as it's known internally, allows Novell to pursue with all the associated business benefits, and to become a real-world model for its customers.
Technology answers to business questions
Unfortunately, it isn't just bits and bytes anymore. now that the technology bubble has burst, there's renewed interest in time-honored business traditions such as return on investment (ROI), competitive advantage and increased productivity. novell nsure solutions help you make the most of your investments, gain competitive advantage and increase productivity. check out http://www.novell.com/solutions/ for an in-depth look at business issues.
Business questions for which Novell Secure Identity Management solutions can provide answers include:
Following a merger or acquisition, how can I link our companies' heterogeneous systems and the data they share?
How can I automate business processes and reduce administrative costs?
How can I manage all user information, including access rights, from a central location?
How can I reduce password-related costs while improving security and the user experience?
How can I create a unified view of my customer information, while still allowing individual departments to maintain control of their data?
Similarly, there are business questions that can be answered via Novell data and system access solutions. For example:
How can I make sure my users, regardless of their location, always have the right tools and secure access to take care of business?
How can I prevent former users from accessing my network?
How do I maximize productivity and improve service for new employees?
How do I set up advanced ID systems, such as smart cards and fingerprint scans, to secure my sensitive data?
Many of the Novell Nterprise solutions and technologies address the issue of business continuity. While not security, per se, there are several business issues that can affect the security of your environment, and the security and reliability of your data and systems. Some questions you may encounter include:
More and more of my users are using mobile devices to access data and communicate. How can I securely meet these evolving computing needs?
How can I reduce the amount of time and money spent managing my expanding IT environment?
How can I keep my communication and collaboration services secure, while still making them easily accessible?
How can I make sure all my users, regardless of location, have safe, reliable access to all the data and systems they need?
These are just a few of the possible business issues you can solve for your executives. It's just a matter of putting your expertise--and Novell solutions--into language they can understand.
* Originally published in Novell Connection Magazine
Disclaimer
The origin of this information may be internal or external to Novell. While Novell makes all reasonable efforts to verify this information, Novell does not make explicit or implied claims to its validity.