i-Login
Articles and Tips: article
01 Feb 2002
You're probably well acquainted with Novell's vision of a world in which all types of networks--the Internet, intranets, and extranets, as well as corporate, public, and wired-to-wireless networks--converge into a single global network. Novell hopes to actualize this vision by delivering solutions built upon Net services software. Usually web-enabled, always directory-enabled, and inherently platform-independent, Net services software provides the key to blurring what are currently distinct and burdensome boundaries between diverse networks.
THE PROOF IS I-LOGIN
Officially launched on September 20, 2000, i-Login is Novell's internal implementation. To be more clear, i-Login is a Novell initiative to solve Novell internal problems using solutions built upon Net services software. The point of this initiative is to test and perfect these solutions in order to make them available to Novell customers.
From the outset, Novell IS&T was asked to shape i-Login with the following three goals in mind:
To dramatically increase new employee productivity
To make information and tools easily available to all employees
To extend network access to everyone, everywhere, on an increasing number of devices
These goals evolved into what now equate to three primary attributes of i-Login, which in turn map to its three fundamental solutions: Zero Day Start, i-Login.Net, and Internet Office. (For more information, see "Three i-Login Solutions.")
About one year ago, Novell Connection introduced you to i-Login and its Zero Day Start and Portal Services solutions. (For more information, see Novell Connection, Dec. 2000, pp. 6-20.) At that time, the benefits of these two solutions were for the most part conjecture, and Internet Office was just an idea.
Today, i-Login and its three primary solutions have been available for nearly 18 months. During that time, Novell has tracked the savings and benefits the company has experienced as a direct result of using the i-Login solutions--savings and benefits, in other words, that point to the i-Login payoff. This article describes each solution and outlines how it has benefited Novell.
ZERO DAY START
Zero Day Start sprang from a desire to better equip Novell's workforce. Specifically, Novell had two goals for Zero Day Start: First, Novell wanted to reduce the amount of time between the day new employees start their job and the day they finally have the tools required to do their job. Second, Novell wanted to instantly and automatically wipe clean all related user identity information the moment an employee left the company.
With the Zero Day Start solution, Novell is well on its way to realizing these two goals.
The Right DirXML-ection
To get started on Zero Day Start, Novell IS&T engineers did a systems assessment to help them better understand what systems were involved in getting a new employee work-related tools. What IS&T engineers found was a vivid reminder of just how complex business processes can become. (See Figure 1.)
Figure 1
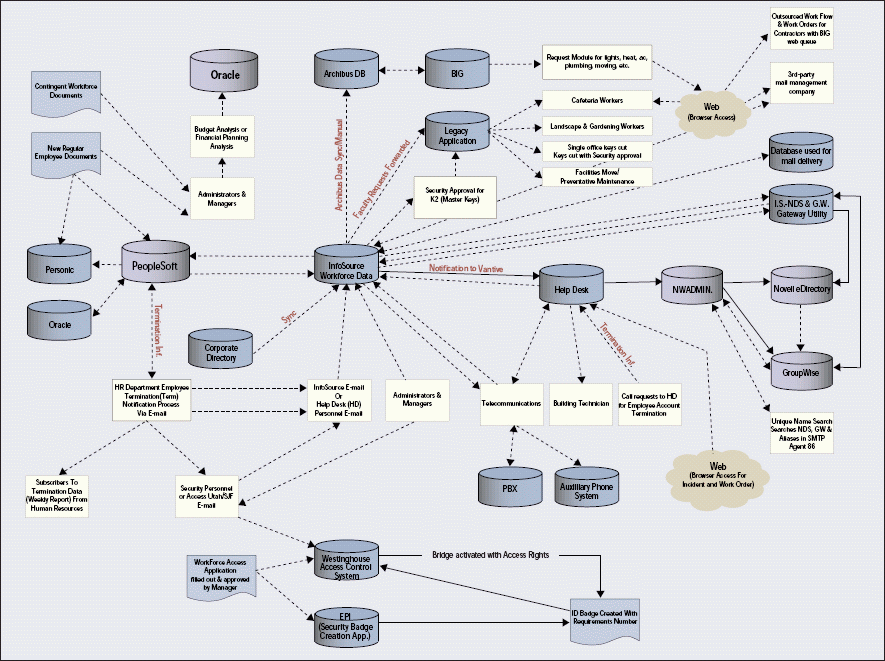
Novell IS&T engineers discovered new employee information in 17 databases and directories, including Novell eDirectory, a PBX database, PeopleSoft, a facilities database, and a building-access security database. Entering the information into those 17 databases required a lot of data-entry hours.
To reduce the data-entry hours involved in getting new employees the resources they need to do their job, Novell IS&T turned to eDirectory and Novell DirXML. At Novell, eDirectory serves as the central, secure repository for all user identity information. DirXML automates the delivery of user identity information to and from eDirectory and all other directories and databases on Novell's network.
Conceptually, Zero Day Start resembles a figurative directory wheel, with eDirectory as the central hub and DirXML as the metaphorical spokes that connect all other directories to this central hub. (See Figure 2.) More specifically, the central hub is an eDirectory tree called the Workforce tree.
Figure 2
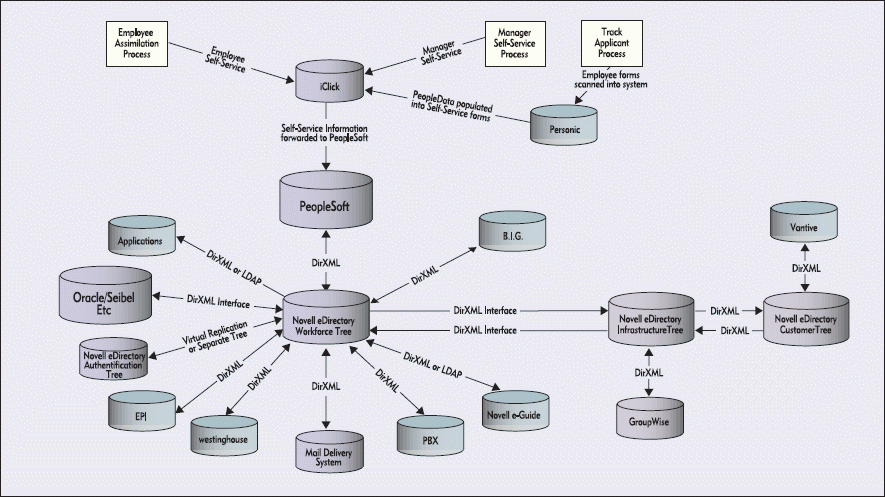
The Workforce tree has a flat structure that includes little more than a Novell Organization container holding the User objects that represent Novell's workforce. These User objects store essential information about Novell employees, including their first and last name; telephone, fax, pager, and mobile phone numbers; mail stop; identification number (called a Workforce ID); and their manager's name.
Using DirXML, Novell IS&T integrated many (and eventually will integrate all) of the directories and databases underlying Novell's applications and business systems. For example, Novell IS&T engineers integrated directories or databases for the following systems:
Metastorm e-work, a workflow system
PeopleSoft, an Human Resources (HR) system
Avaya PBX systems from Lucent Technologies
A Business Integration Group (BIG) facilities system
A Westinghouse security system
In addition to integrating the directories and databases underlying these systems, Novell IS&T has integrated another eDirectory tree. This tree includes an Organization container that holds the Server and Volume objects associated with Novell's directory-enabled applications, including GroupWise and Novell eGuide, a white-pages application.
For each of these directories and databases, Novell IS&T configured DirXML to either send information from the Workforce tree to another directory or to return information from another directory to the Workforce tree. As a result, Novell IS&T can synchronize selected information--in this case, user identity information--that is stored in disparate directories.
By using DirXML, Novell IS&T can also specify which directory will be the "master" of particular pieces of information. For example, Novell IS&T made PeopleSoft the master of employees' names. As a result, Novell can enter or change an employee's name only in PeopleSoft. This change is then replicated throughout the network.
The Directory Wheel in Motion
In general terms, Zero Day Start works as follows: When a new employee signs Novell's offer of employment, a Novell HR employee creates a new account in the PeopleSoft database. This new account triggers the creation of a new User object in the Workforce tree. The new User object in the Workforce tree, in turn, triggers entries or the creation of new accounts in other integrated directories and databases.
DirXML also pushes through to the BIG facilities database the information regarding the new User object in the Workforce tree. (BIG is a company that manages Novell's facilities in San Jose, California, and Provo, Utah.) Consequently (and with minimal manual intervention), a new employee is assigned an office.
The facilities system then pushes through to the Workforce tree the office number and the numbers of the telephone jacks and the network jacks in that office. DirXML then pushes that information through to the systems Novell IS&T has configured to accept this information.
The creation of the new User object in the Workforce tree also automatically enables access to directory-enabled applications, including GroupWise and Novell eGuide.
In addition, Novell IS&T uses DirXML to integrate the Westinghouse security system that controls employees' access to buildings. DirXML sends information regarding a new User object in the Workforce tree to the Westinghouse system. In turn, the Westinghouse system determines the security profile for the new employee (based on information such as his or her job title, manager, and home office). Based on this security profile, the Westinghouse system determines which buildings the new employee needs to access.
When new employees show up for their first day of work at Novell, they find a fully equipped office, the means to communicate with others via e-mail and telephone, and access to all of the data and applications they need.
The Tangible Benefits
Zero Day Start benefits employees and Novell. Employees benefit because Zero Day Start helps them feel as if they are part of the company the day they accept the job and enables them to be productive on their first day of work. Novell gains a number of benefits including significant administrative cost savings; strong, centralized control of user identity information; and more reliable user account information.
The administrative cost savings are among the most tangible benefits. By integrating its directories, Novell now needs to enter information about a new employee only once. Likewise, changes to user information are entered only once.
After this single entry, DirXML automatically updates all of the other directories that Novell IS&T engineers have configured to accept this addition or change. The result is a significant reduction in the time spent entering and re-entering the same information for each employee.
Novell estimates that Zero Day Start saves the company approximately U.S. $237,000 annually in data entry costs. Novell arrived at this cost estimate by calculating the approximate length of time spent on data entry for each new employee, which they found to be 2.83 hours. Novell then multiplied 2.83 hours by U.S. $62, which represents the base pay of all the employees involved in the new employee data entry processes (including the persons involved in creating an eDirectory account, creating a GroupWise account, setting up PBX service, and enabling remote access).
This calculation lead Novell to believe that they were spending approximately U.S. $175.46 on each new employee. This amount multiplied by 1,351 (the average number of new employees annually) equals U.S. $237,046.46.
With Zero Day Start, data-entry costs related to getting new employees everything they need to do their job have been reduced to the cost of the few minutes it takes someone in HR to create a new account in PeopleSoft. From that point forward, everything else occurs automatically and with minimal manual intervention. Novell estimates that it now spends only 10 to 15 minutes on data entry for each new employee.
Similarly, for terminations, Novell estimated that it spent approximately 1.13 hours on data entry. This meant that, based on a U.S. $62 hourly pay, Novell was paying U.S. $70.06 on each termination and approximately the same on each employee move. Today, an HR employee spends only a few minutes disabling a terminated employee's PeopleSoft account. All other accounts are then automatically cleared. Novell estimates that it now spends only 5 to 10 minutes on data entry for terminations.
I-LOGIN.NET--WHAT DO YOU NEED TO KNOW TODAY?
Zero Day Start provides immediate access to the physical and digital tools Novell employees need to do their jobs. i-Login.Net, Novell's customized portal, facilitates the delivery of these employees' digital tools. Novell IS&T and Novell Engineering jointly developed (and continue to refine) i-Login.Net to address some of the common problems associated with delivering digital assets--problems such as the inconvenience of scattered information, the hassle of multiple user accounts, and the irritation of limited access to services.
i-Login.Net is an intelligent portal that enables Novell employees to access information using only one set of credentials, which reveal employees' relationship with Novell. Several products help make i-Login.Net successful, including Novell iChain and Novell Portal Services.
Novell iChain
As the front end to i-Login.Net, Novell iChain enables Novell IS&T to create and then store policies in eDirectory. These policies help Novell IS&T manage the authentication and authorization of anyone attempting to access i-Login.Net.
Because Novell iChain runs on a Volera Excelerator appliance and runs only in reverse proxy mode, it both accelerates access to and protects the i-Login.Net portal. Novell iChain accelerates access to information by storing in cache all static data retrieved from internal servers. When a user attempts to access data that is already in cache, Novell iChain retrieves that data from cache and returns it immediately, without first having to access the internal servers where the information is stored.
As you probably know, reverse proxy mode helps protect information users can access via i-Login.Net by masking the IP addresses of the internal servers where requested information is actually stored. Novell iChain retrieves information and returns that information using its own IP address as the return address. This is the only IP address outside users ever see. (For more information about Novell iChain, visit www.novell.com/products/ichain2/details.html.)
Novell Portal Services
Novell Portal Services is a directory-driven portal framework that fully complies with the Lightweight Directory Access Protocol version 3 (LDAP v3) and is built around eXtensible Markup Language (XML) and java servlets. Novell Portal Services runs on any web server platform (including NetWare, Windows NT, Solaris, and Linux) running any web server that features a servlet engine and uses an LDAP v3-compliant directory (such as eDirectory 8.5 and 8.0).
At the time this article was written, Novell was using eDirectory 8.6 and running Novell Portal Services 1.0 on a Windows 2000 server. The Windows 2000 server was equipped with Microsoft Internet Information Server (IIS) and Tomcat, a JavaScript Pages (JSP) engine developed by the Apache Software Foundation (http://jakarta.apache.org/tomcat). (To further test Novell Portal Services 1.0, Novell also has instances of it running on NetWare 6 and Sun OS servers.)
Novell employees can access the i-Login.Net portal from a number of devices. For example (and as you would expect), users can access the i-Login.Net portal from any desktop or laptop running a standard web browser.
Users can also access some of the i-Login.Net portal services and will eventually be able to access all portal services using wireless devices that use the Wireless Access Protocol (WAP). (These wireless devices include wireless notebooks, mobile phones, and Personal Digital Assistants [PDAs].) For example, using Compaq iPAQ Pocket PCs over Novell's wireless LAN in Provo, building technicians access and update Novell's IS&T issue database via i-Login.Net.
LET ME IN, LET ME IN
To access the i-Login.Net portal, Novell employees simply enter the correct URL: www.i-Login.net. This request to access the portal first hits an L4 switch just inside Novell's firewall. The L4 switch redirects this HTTP request to Novell iChain, and iChain responds by returning a login screen. Employees then enter their credentials, and iChain uses that information to perform an LDAP query against eDirectory to determine whether or not to authenticate a particular employee.
Assuming Novell iChain authenticates the employee, it redirects the employee to the i-Login.Net portal server, to which iChain also passes the employee's credentials within the HTTP header. The portal server removes the employee's credentials from the HTTP header and uses this information to perform its own LDAP query against eDirectory. The portal server checks this employee's Container, Group, and User objects to determine which portal features are appropriate for this employee. The portal then returns a screen that has been customized based on this employee's relationship with Novell.
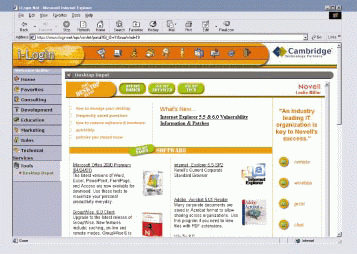
Consequently, the i-Login.Net portal home page (like other i-Login.Net portal pages) is roughly the same for each Novell employee in terms of its default appearance. (See Figure 3.) However, the i-Login.Net portal home page is different for each employee in terms of its content.
Figure 3
Gadget Convenience
An employee's relationship with Novell determines the gadgets the employee sees on the home page (and, in fact, on all the i-Login.Net portal pages). Gadgets are basically web-based applications that function as conduits to full-fledged services. (For more information, see "Novell Portal Services: A Better Way To Build a Desktop," Novell Connection, Dec. 2000, pp. 22-32.) Since i-Login.Net was launched, it has featured gadgets for Novell eGuide, Yahoo! News, GroupWise Mail, and GroupWise Calendar--to name only a few.
Having an infrastructure that allows only select employees to access particular gadgets comes in handy at times, Cox points out. For example, in the weeks before July 2001, when Novell announced that it had completed its acquisition of Cambridge Technology Partners (CTP), certain people within both companies needed to access both companies' white pages. According to Cox, Novell IS&T spent only about one week making this happen.
Novell IS&T engineers simply created a new container, the Cambridge container, in the Workforce tree. Next, the IS&T engineers migrated user information from Cambridge's Microsoft Exchange system, where Cambridge stored its employees' user identity information. (Later, IS&T engineers configured a DirXML driver between the Cambridge Exchange system and eDirectory.)
Novell IS&T engineers then created another instance of eGuide on the portal. The Novell eGuide gadget that had been on the portal all along pointed only to the Novell container. The new eGuide gadget pointed to both the Novell container and the Cambridge container. IS&T engineers assigned access rights to this new instance of eGuide to those few individuals in both companies that required access. Thus, by "using eGuide, iChain, and Portal Services, [Novell was] able to easily allow user information from both companies to be available only to select individuals," Cox says.
Portal Links
Employees see links on the home page to some or all of the following portals:
MySales.novell.com
Marketing.novell.com
ourBenefits.i-Login.net
The links employees see depend on their relationship to Novell. For example, MySales.novell.com and Marketing.novell.com provide links to information relevant to individual sales, marketing, and support personnel such as the following:
Personal sales quotas
Customer account and pipeline status
Marketing programs
Project time lines
Activity calendars
Metrics and status tracking
Budget and financial information
Novell IS&T plans to roll out other such departmental portals for all of Novell's departments.
The ourBenefits portal enables employees to create an account for their partners. This account then enables spouses or partners of Novell employees to access information anytime about benefits, including health insurance records, retirement account status, and vacation account status.
To create an account for their partner, employees enter their partner's first name, last name, and e-mail address and then create a password. When employees submit this information, eDirectory automatically creates a User object for the employee's partner in a special container (the Benefits container). The User object name is the employee's username followed by -br (which stands for benefits recipient). For example, if the employee's username is lmiller, the object name associated with the account that this user sets up for her partner would be lmiller-br.
Of course, some i-Login.Net features are available for all Novell employees to see and use--regardless of their relationship with Novell. For example, since we last wrote about i-Login, Novell IS&T has added iPrint and i-deNtity, which are services available to all Novell employees.
iPrint From Anywhere
Like most corporate employees today, Novell employees move around a lot--moving not only between buildings but also between sites. Every time a Novell employee changes a location, the printing environment changes. To help these myriad mobile employees more easily find and use printers regardless of the Novell building they're in or site they're visiting, Novell IS&T created the iPrint service.
Basically, here's how the iPrint service works: Suppose a Novell employee who typically works in Building K at Novell corporate headquarters in Provo goes to Building H. Further suppose this employee needs to print a document.
To find a printer, the employee accesses i-Login.Net and clicks the iPrint icon. The employee is prompted to select his current location. (In the future, Novell IS&T plans to enable the iPrint system to automatically detect a user's location.)
After the employee indicates his location, iPrint returns a map, showing the make and location of the nearest printers. (See Figure 4.) When the employee clicks on a printer from any Windows client, iPrint automatically configures this printer for use with this particular client, and this employee can print.
Figure 4
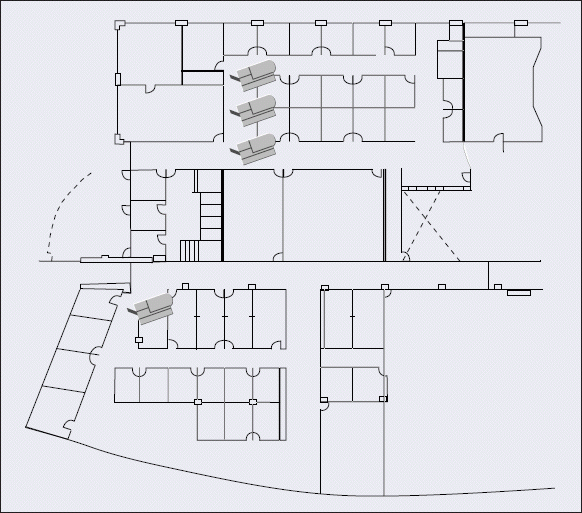
To date, Novell IS&T has created maps for Novell's corporate headquarters in Provo, Utah, as well as offices in Herndon, Virginia; Salt Lake City, Utah; San Jose, California; Bracknell, England; and Sydney, Australia. Novell IS&T has also created iPrint maps for the offices in Cambridge, Massachusetts.
i-deNtity
i-deNtity enables Novell employees to manage their own user identity information using what Novell IS&T calls the authentication triangle. As the name suggests, the authentication triangle refers to three things users can know and enter to access various resources: a password, a personal identification number (PIN), and a secret question-answer combination. Employees create their own password, PIN, and secret question-answer combination when they first sign up for an i-Login.Net account.
In part, the goal in creating i-deNtity was to minimize help-desk calls by enabling users to reset their own credentials when they forget them. At any time, employees need remember only two of the three credentials in the authentication triangle.
For example, suppose an employee attempts to log in and forgets her password. She can access the i-deNtity utility, which asks if she's forgotten her password. The i-deNtity server then prompts the employee to enter her PIN. If the employee remembers her PIN, the i-deNtity server prompts the employee to answer her secret question. If the employee answers correctly, then she can change her password.
Other combinations are equally true. For example, if an employee can't remember his secret question and answer but can remember his password and PIN, then he can change his secret question and answer. Similarly, if an employee can remember his secret question and answer as well as his password, then he can change a forgotten PIN.
When employees create a PIN as part of the i-Login.Net credentials, this PIN by default becomes the PIN for the Novell phone system. For example, employees use this PIN when accessing their voice mail. Employees also have the option to use this PIN to place long-distance calls. Employees can opt to always use the PIN or specify certain times of day when they will use the PIN (to ensure that no one else uses their phone when they are away, for example).
i-deNtity also provides a helpful reminder to users as to which set of credentials they should use when attempting access to various resources. For example, when Novell employees attempt to access a Novell web site that requires authentication (without going through i-Login.Net), they can look for the i-deNtity icon. When they see the i-deNtity icon, they know that they need to use their i-Login.Net credentials to access that particular site.
INTERNET OFFICE
Novell's third initiative to make the services employees need accessible from literally anywhere on the Internet stemmed from an apparent change in today's concept of work. Not long ago, work was a physical location with a physical infrastructure that required buildings, wiring, desks, computers, and physical links between buildings--however distant. You needed that infrastructure--one of those physical places--to access corporate information.
Two years ago, Novell's WAN reflected this concept of work. Novell ran dedicated links to all of its field offices. These links provided simple, secure, and fast access to corporate services. However, these 110 WAN links to all Novell offices, connecting its 20,000 workstations and 5,000 employees, cost more than U.S. $9 million annually.
The irony is that much of this cost was being wasted on employees who weren't even in the office. Like most corporations today, Novell has a sizable mobile and remote workforce. In fact, Cox estimates that within any 30-day period, at least 40 percent of Novell's employees are working out of the office.
Novell vowed to create an environment that reflected today's concept of work as being an activity, not a place. As Novell CIO Ken Anderson explains, Novell wanted to "move the office to the people rather than moving the people to the office." Enter Internet Office.
To convert remote offices to Internet Offices, Novell IS&T engineers took the infrastructure out of the remote offices, centralized all services in Provo, and provided a high-bandwidth Internet link for each Internet Office. Now, whether employees are in or out of the office, they access corporate network services in precisely the same manner--by connecting to the Internet, using a web browser, and either entering the URL for i-Login or using BorderManager VPN 3.6. (For more information about accessing network services, see the "NOMAD" section.)
To date, Novell has taken down the WAN infrastructure and converted approximately 70 branch offices (including Chicago, Illinois; Toronto, Canada; Bracknell, England; and the Philippines) to Internet Offices. In the United States, Novell IS&T has installed T1 lines for all of its offices. In many cases, the 1.5 Mbps that the T1 line provides is significantly faster than the dedicated line it replaced. Some of the dedicated lines ranged from only 128 to 512 kbps. The best news is that the fast pipes to the Internet cost approximately five million dollars less annually than the dedicated WAN links.
NOMAD
An important first step to enabling the Internet Office was to outsource secure remote access to the Internet. Novell IS&T enabled this remote access through a separate but related solution called Novell Mobile Access Delivery (NOMAD). NOMAD is an internal name for Novell's internal approach to remote access and is not a product. However, NOMAD is an example of the Novell Remote Access solution, which will be available through Novell Sales and Consulting beginning early in 2002.
NOMAD replaced the toll-free numbers that four years ago provided only a handful of remote and mobile employees access to Novell's network. Admittedly, the toll-free lines were convenient. After all, this seemingly free door to the corporate network enabled employees to download the files they needed from anywhere within the United States and Canada. However, widespread use of the toll-free number was costing Novell a lot of money.
In addition, the access servers supported only dial-up connections from the comparatively sluggish 56 kbps (or slower) modems and represented the single "In" door to Novell's network. Users with access to a Digital Subscriber Line (DSL) or cable modem could not access the corporate network using other faster methods of Internet access.
Beyond that, Novell's remote and mobile workforce does not travel only within the United States and Canada, and outside that area, the toll-free line was unusable. Employees had to pay and request reimbursement for costly and not-always-reliable toll lines they used to dial in to the Provo-based access servers from across the globe.
Obviously, avoiding the expense of toll-free lines by setting up local access points at every location from which employees would require access was costly and impractical. After all, Novell's mobile employees travel from one end of the globe to the other, accessing the network from places such as Australia, Venezuela, Finland, Norway, Singapore, and Thailand.
To provide access to the corporate network from virtually anywhere without incurring atrocious toll-free or long-distance fees, Novell contracted with UUNET, a WorldCom company. This leader in Internet communications solutions owns and operates a global network with points of presence (POPs) in thousands of cities throughout North America, South America, Europe, Africa, and Asia Pacific. (For more information about UUNET, visit www.uu.net.) Along with its gateway partners, UUNET provides the POPs that enable Novell employees to access the Internet from virtually anywhere in the world using, in many cases, a local telephone number.
Although Novell outsources physical access to the Internet, it maintains control over account management, authentication, and access control through the use of Novell Modular Authentication Services (NMAS) Enterprise Edition 2.0 and BorderManager VPN Services 3.6. Essentially, NMAS 2.0 helps Novell employees authenticate to Novell's eDirectory tree using the RADIUS packets received from UUNET servers. NMAS 2.0 thus helps Novell employees access the Internet by way of Novell's UUNET account. Once on the Internet, Novell employees can access i-Login.Net, and from there, they can access many of the resources they need.
When information, services, or applications are not available via i-Login.Net, Novell employees can use BorderManager VPN Services 3.6 to access the corporate network from the Internet. Ultimately, the VPN services will no longer be necessary: Novell plans eventually to make all services available through i-Login.Net (using Novell iChain and Novell Portal Services).
As Novell demanded and Novell IS&T intended, NOMAD's combination of global Internet Service Provider (ISP) services and Novell Net services software enables employees to access corporate data from virtually anywhere in the world. Access to corporate data via NOMAD is simple, fast, and secure.
Also, as Novell hoped and Novell IS&T planned, NOMAD saves Novell a lot of money. In fact, Novell's remote access costs are lower than ever, despite the fact that remote use of its corporate network has significantly increased over the last 21/2 years. Prior to NOMAD, Novell spent approximately U.S. $1.2 million per year on remote access costs. NOMAD has reduced these costs by 70 percent or more.
Novell OnDemand Services
The second enabling technology for Internet Office is Novell OnDemand Services 1.5, which enabled Novell IS&T to integrate Novell's web and Windows 32-bit applications with i-Login.Net. To date, Novell IS&T has integrated 16 web applications (including Trilogy, Hyperion, Consulting Reports, Direct Expenses Reports, and WebVantive for iPaq) and 17 Windows 32-bit applications (including PeopleSoft, GroupWise, and ConsoleOne).
Novell OnDemand Services is an eProvisioning solution that enables Novell IS&T to deliver in real-time its web and Windows 32-bit applications. OnDemand Services can also deliver documents, digital certificates, disk space, online classifieds, video files, and music files. (For more information, see "Novell OnDemand Services Simplifies the Delivery of eProvisions," Novell Connection, Oct. 2001, pp. 27-37.)
OnDemand Services' DeFrame component enables employees to download web and Windows 32-bit applications from anywhere on the Internet. To access the interface for OnDemand Services, employees click Desktop Depot from the i-Login.Net home page. (See Figure 5.)
Figure 5
When a Novell employee attempts to launch an application from Desktop Depot (delivered via the OnDemand DeFrame component), OnDemand Services checks eDirectory to ensure the user has rights to this application and to determine on which Windows or Citrix terminal server the application is running. Next, the OnDemand server establishes a session between the terminal server running the requested application and the user's workstation.
Applications delivered via OnDemand Services' DeFrame component remain on the server at all times. Only keystrokes, mouse clicks, and video bits cross the wire. As a result, the user's workstation does not need to be running the Novell Client 32 software. In fact, users can launch DeFrame applications without manually installing any client software. Instead, DeFrame automatically loads the appropriate client software required to access the Windows or Citrix terminal server on which the application is actually running. Perhaps more importantly, in this context, because the applications remain on the server and little information actually crosses the wire, users get great performance, regardless of their connection to the Internet.
CONCLUSION
The three i-Login solutions break down former barriers between Novell's intranet, extranet, the Internet, and its corporate WAN. Those borders no longer matter--at least not to Novell employees.
Linda Kennard has been writing articles for Novell Connection for more than six years. Linda is a senior writer for Niche Associates, an agency that specializes in writing and editing technical documents. Niche Associates is located in Sandy, Utah. (For more information about Niche Associates, visit the Niche Associates' web site at www.nicheassociates.com.)
Three i-Login Solutions
|
Attribute
|
Solution
|
Description
|
|
Automatic Provisioning |
Zero Day Start |
i-Login services are immediately available to users from the moment their job with Novell starts or changes. |
|
Intelligent Portal |
i-Login.Net |
i-Login services are delivered through an intelligent portal, which ensures that users can access what they need to know from a single location using one name and password and based on their relationship with Novell. |
|
Access from Anywhere |
Internet Office |
i-Login services are securely accessible from anywhere on the Internet. |
* Originally published in Novell Connection Magazine
Disclaimer
The origin of this information may be internal or external to Novell. While Novell makes all reasonable efforts to verify this information, Novell does not make explicit or implied claims to its validity.