Taipei County Government Secures Access to Its Assets
Articles and Tips: article
01 Jan 2002
When the year 2000 was nearing its end, Taipei County Government (www.tpc.gov.tw/english/index.htm) initiated a project to greet the millennium with a new approach to an old problem: managing users' access to network resources. The project was both reactive and proactive, with the intent being to solve existing and anticipated problems with managing user accounts and protecting network resources.
As planned, security project manager Jang-Ming Young began the project by researching Lightweight Directory Access Protocol (LDAP)-compliant directories. Taipei County Government hoped an LDAP-compliant directory would provide the foundation for a complete access-management solution. As Young searched the web, he found multiple documents pointing to Novell eDirectory as the LDAP-compliant directory of choice. As a result, Young contacted a local Novell partner--and the rest, as the cliché goes, is history.
Today, Taipei County Government runs a Novell access and security solution and has completed the first phase in its two-phase project. (Novell access and security solutions enable organizations to securely manage access to applications, databases, and platforms for all types of clients. For more information, see "Rethinking Security: Seven Steps to Tighten Network Security." For more information about the project, see "The Project Plan.") This solution protects network resources through multifactor authentication mechanisms and enables users to enter a single set of credentials to access all network resources to which they have rights. Perhaps more important, Taipei County Government's four Management of Information Systems (MIS) specialists can now centrally manage all of the hardware, software, and policies involved in authenticating and authorizing users to network resources.
During the course of the project, Young and others found products from other vendors that solved specific portions of their organization's problem. However, ultimately they concluded that only Novell has a complete solution that addresses every aspect of Taipei County Government's access-management problem. "Novell's proven track record in identity-based security solutions made it an easy choice," says Young. "With eDirectory, we have a centralized, easy-to-manage store for our users' identity information, which defines what users can access on the network."
THE NETWORK SITUATION
As the governing body for the largest of 16 counties in Taiwan, Taipei County Government has a sizable workforce. (See "Taipei County.") More than 1,700 employees work in the 27 departments within the adjacent pair of Taipei County Government buildings that are located in Banchiao, about 10 km (8.5 miles) southeast of Taipei city. (See Figure 1.)
Figure 1
The employees in these departments use approximately 1,500 workstations. Two hundred of these workstations are not connected to Taipei County Government's IP-based 100BaseT Ethernet LAN. The remaining 1,300 workstations are Windows 2000/NT/98 clients--virtually all of which are desktop PCs, with the exception of approximately 100 laptops.
Before implementing the Novell access and security solution, the Taipei County Government network consisted of four servers:
One Sun Solaris server that also ran iPlanet Messaging Server which was integrated with Netscape Directory Server running on the same server
One Windows 2000 server, which ran a custom-built Certificate Authority (CA) that was integrated with Netscape Directory Server and ran on top of Microsoft Internet Information Server (IIS)
Two Windows NT 4.0 servers with Service Pack 4, which ran several commercial and custom applications
THE PROBLEM
The problem was that to access applications and data--even the most confidential information--employees needed to enter only a password. Taipei County Government recognized that password-protection alone does not adequately protect important and confidential resources. For example, if an employee guessed an MIS specialist's password, this employee could have accessed other employees' e-mail messages, created or removed user accounts, and modified user privileges--to name only a few of the possibilities.
Compounding this problem was the fact that each of the 1,700 employees had multiple accounts, including two frequently used accounts: one account for the Netscape Directory Server and one account for Windows NT domains. Two frequently accessed accounts per user (not to mention their less-frequented accounts) was one account too many and caused the usual set of problems.
For one thing, employees had to enter a different set of credentials every time they switched between the applications in the Windows NT domains and the iPlanet messaging application. Aside from being annoying, this practice was inefficient and took time.
Admittedly, entering credentials and waiting to be authenticated takes only seconds--perhaps as few as ten seconds. However, even ten seconds adds up quickly when you have 1,700 employees entering credentials as many as three times a day. In fact, do the math using the hypothetical values of ten seconds and three times daily. Given these values, you can guesstimate that Taipei County Government employees were collectively spending approximately 71 hours per week doing nothing more than entering credentials and waiting to be authenticated.
In addition to costing users time, two user accounts per employee cost the MIS specialists time. As a network administrator, you're probably not surprised to learn that Taipei County Government employees frequently forgot one or both of the passwords to their user accounts. Consequently, the 14 engineers in Taipei County Government's IS&T department spent more time than they wanted assigning new passwords.
Help-desk issues aside, managing two accounts per user was impractical and time-consuming. For example, to manage access control rights for the Netscape directory, MIS specialists had to use the Netscape Directory Server console running on the Sun Solaris server. To control users' access rights to resources in the network's Windows NT domains, the MIS specialists had to use the Windows management application running on the Windows NT Primary Domain Controller (PDC). In other words, to manage user accounts, MIS specialists had to work on separate computers, use different applications, and, most important, understand dissimilar philosophies for setting access rights.
Not surprisingly, the MIS specialists found that the process of creating new user accounts and assigning appropriate privileges sometimes took as long as three days. Clearing accounts belonging to former employees commonly took more than a week. What was more disconcerting than the time involved in clearing accounts was the uncertainty involved: Without a central point of management for user accounts, MIS specialists frequently worried that they hadn't actually cleared all of the access rights to all of the resources to which a former employee had access.
Despite these problems, when Taipei County Government started its project, managing user accounts was tolerable. However, Taipei County Government was looking ahead. Like most organizations, Taipei County Government anticipated that its network would grow. Taipei County Government drew the logical conclusion: Without a solution to its access-management problem, protecting network resources and managing user accounts would become only more difficult, and consequently, the threat of a security breach would become even more likely.
THE NOVELL SOLUTION
By December 2000, the research stage of Taipei County Government's access-management project was well under way. By this time, Taipei County Government was determined to change its network situation and knew where it would start: by learning more about eDirectory.
Young's web research was not the only source pointing to eDirectory. eDirectory is "a hot solution in Taiwan right now," claims one Novell developer support engineer. Indeed, several other government agencies within Taiwan use eDirectory, and Taipei County Government had heard good reports from these agencies.
The local Novell partner that Young first contacted told Taipei County Government about other Novell products. Taipei County Government liked what it heard. Not surprisingly, Taipei County Government soon opted to standardize on eDirectory, which now serves as the foundation for its Novell access and security solution.
With a specific direction now in mind, Taipei County Government opened the bid for a project manager, and SecureInside won the bid. SecureInside (http://www.secureinside.com/) focuses primarily on helping Taiwan county and city governments with IS projects. (For more information, see "SecureInside.") As project manager for the Taipei County Government project, SecureInside made arrangements with Novell partners to set up the Novell solution.
SecureInside also contacted the vendors of products already running on Taipei County Government's network, asking these partners to integrate their products with eDirectory. For example, SecureInside contacted Network Security Technologies (http://www.nst.com.tw/), which developed the CA running on the Windows 2000 server. Network Security Technologies integrated this CA with eDirectory. The CA was previously integrated with Netscape Directory Server.
As with any project, Taipei County Government's access management project didn't progress in a strictly linear fashion, with each stage ending neatly and leading logically to the next stage. Nevertheless, the project did include the following definable stages:
Standardize on eDirectory 8.5.1
Consolidate user accounts with Novell Account Management 2.1
Enable multifactor authentication with Novell Modular Authentication Services (NMAS) 1.0 Enterprise Edition
Enable remote access with BorderManager Authentication Services (BMAS) 3.6
During the course of this project, Taipei County Government also deployed ZENworks for Desktops 3, which replaced a competing solution that the organization had purchased about one year earlier. ZENworks for Desktops 3 enables the MIS specialists to complete the following tasks:
Centrally create and manage Windows NT policies and profiles
Remotely control the network's 1,300 workstations
Automatically create client hardware and software inventories from a central location
Quickly react to and proactively act on virus problems
According to Young, ZENworks for Desktops 3 is "one-tenth the cost [of the competitor's solution] but ten times more powerful." (For more information about ZENworks for Desktops 3, visit www.novell.com/products/zenworks/desktops.)
Standardizing on eDirectory
To provide systems integration services, SecureInside initially contracted with UniBiz (http://www.unibiz.com.tw/) and later with Bizwave (http://www.bizwave.com/), both Novell partners. UniBiz was responsible for installing all of the Novell products running on Taipei County Government's network today, with the exception of NMAS. Bizwave contributed to the first half of the Taipei County Government's access-management project and continues to work on the second half.
To start the project, UniBiz installed NetWare 5.1 (www.novell.com/products/netware5) on two newly purchased IBM xSeries 300 servers. (See Figure 2.) Each IBM xSeries 300 server (www.pc.ibm.com/us/eserver/xseries/x300) is equipped with a Pentium 1 GHz processor, 1 GB of RAM, and an 18 GB hard drive.
Figure 2
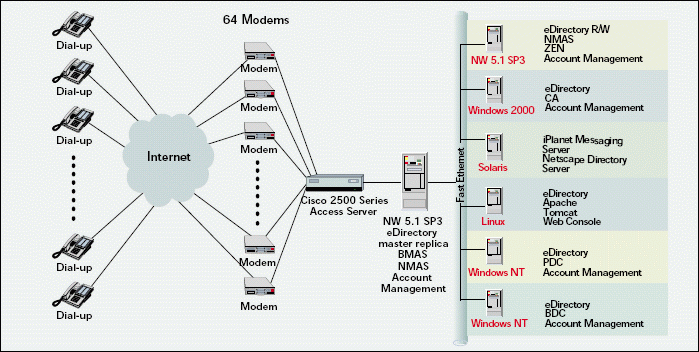
Next, UniBiz installed eDirectory 8.5.1 on the NetWare, Windows 2000, and Windows NT servers. UniBiz did not install eDirectory 8.5.1 on the Solaris server because Taipei County Government plans to migrate the Solaris server to Microsoft Exchange 2000. (For more information, see the "What's Done and What's Next?" section and the "The Project Plan.")
Because Taipei County Government runs so many different server platforms on its network, eDirectory is the logical choice for an LDAP-compliant directory on which to standardize. Recently named directory product of 2001 by Network Magazine, eDirectory is the only directory on the market that runs on all major operating systems including NetWare, Windows 2000/NT, and Solaris, as well as Linux, Compaq Tru64, UNIX, and soon, IBM AIX. (For more information about Network Magazine's Products of the Year awards, visit www.networkmagazine.com/article/NMG20010413S0005.)
As the cross-platform repository for all identity, policy, and access-control information, eDirectory is the foundation for the Novell access and security solutions. eDirectory is also highly scalable, with the ability to store and manage billions of objects while maintaining fast lookup speeds. (For more information, visit www.novell.com/products/nds.)
Consolidating User Accounts
To consolidate user accounts, UniBiz installed Novell Account Management 2.1 on the NetWare, Windows NT, and Windows 2000 servers. (See Figure 2.) Formerly named NDS Corporate Edition, Novell Account Management 2.1 is an eDirectory-enabled application that simplifies and unifies the management of user profiles on Windows 2000, Windows NT, Solaris, and Linux servers. (For more information about Novell Account Management 2.1, visit www.novell.com/products/nds/accountmanagement.)
For example, to install Novell Account Management 2.1 on the Windows NT servers, UniBiz ran SETUP.EXE from the Account Management CD and selected the Integrate Windows NT Domains with NDS option. By selecting this option, UniBiz successfully installed the Novell Account Management components and also ran the Domain Object Wizard, which transparently migrated all existing NT domains into eDirectory.
Once installed, Novell Account Management 2.1 created accounts in eDirectory for Taipei County Government's existing Windows NT user and group profiles. Next, Novell Account Management 2.1 made these accounts available to services running on the Windows NT servers through a process called redirection. Basically, redirection refers to a process whereby Novell Account Management 2.1 redirects to eDirectory any user requests for services running on the Windows NT or Solaris servers. (For more information, see "Redirecting to eDirectory Requests for Services in NT Domains.")
By running Novell Account Management 2.1 on the various server platforms, each of the 1,700 Taipei County Government employees now has a single user account in eDirectory. As a result, employees now have only one set of credentials they can use to access all of the network resources to which they have rights--regardless of the platform on which those resources run.
What may be more important is how consolidating user accounts has simplified user account management. MIS specialists now have the luxury of managing only one user account for each of the network's 1,700 users. In fact, the MIS specialists can complete all tasks related to managing user accounts using a management interface to eDirectory, such as ConsoleOne, eDirectory's Java-based administrative utility.
For example, when MIS specialists want to assign a new user access rights to applications in the Windows NT domains, they can do so using ConsoleOne. To move a user from one Windows NT domain to another, MIS specialists can again use ConsoleOne (and incidentally, they won't have to recreate or delete accounts to do so).
In addition to using the ConsoleOne interface to eDirectory, Taipei County Government's MIS specialists can also use a web management console. This web management console runs on a new Linux server that is running the Apache web server (http://httpd.apache.org/). The Linux server also runs Tomcat, a JavaScript Pages (JSP) engine also developed by the Apache Software Foundation (http://jakarta.apache.org/tomcat). (See Figure 2.)
By creating this console, Bizwave enabled MIS specialists to access Taipei County Government's eDirectory tree and to manage user accounts from any network client running a standard web browser. The MIS specialists can use this web console to perform tasks such as creating User, Group, and Organizational Unit (OU) objects and managing access control lists (ACLs).
Enabling Multifactor Authentication
Novell Account Management 2.1 alleviated the problems of managing multiple user accounts and, to some extent, increased network security. After all, users now have only one set of credentials to memorize and, therefore, are less likely to jot down these credentials as a means of remembering them. MIS specialists can manage user accounts from a central point. As a result, creating new accounts and assigning new access rights take less time. More important, in this context, clearing old accounts is easier--and no longer leaves the MIS specialists worrying that perhaps they have missed something.
Novell Account Management 2.1 clearly provides a better approach to managing user accounts and, thereby, offered the beginnings of improved security. To better protect network resources, however, Taipei County Government deployed NMAS 1.0 Enterprise Edition (www.novell.com/products/nmas).
NMAS 1.0 enables Taipei County Government to create authentication policies that require users to authenticate to eDirectory using login methods based on any type of login factor (such as passwords, smart cards, or fingerprints). As you can guess, NMAS 1.0 extends the eDirectory schema to allow for storage of additional authentication information, such as personal identification numbers (PINs) and fingerprints. In addition, the NMAS 1.0 Enterprise Edition (as opposed to the NMAS Starter Pack) enables Taipei County Government to create login sequences based on any combination of login factors so that employees have to enter one, two, or three factors to gain access to various network resources.
NMAS 1.0 supports various login methods through several authentication modules that Novell and third-party vendors provide. For example, Novell developed modules that enable users to log in using an eDirectory password or an X.509 v3 certificate. Third-party authentication modules include modules from ActivCard Inc., Identicator Technology (a division of Identix), RSA Security, SAFLINK Corp., and VASCO Data Security Inc. These authentication modules enable security vendors to integrate their authentication devices in an NMAS environment.
To deploy NMAS 1.0, Taipei County Government worked closely with Novell-trained engineers at Taiwan Developer Labs. Taiwan Developer Labs are sponsored by the Ministry of Economic Affairs (MOEA) and the Institute for Information Industry (III), a nonprofit organization chartered to help the Taiwanese government encourage the growth of the country's information industry. (For more information, visit www.iii.org.tw/portal/english.htm.) Taiwan Developer Labs are also sponsored and supported by Novell Worldwide Developer Support.
Taiwan Developer Labs installed the NMAS server software on the NetWare 5.1 server running the eDirectory master. (See Figure 2.) The engineers from the Labs also installed NMAS 1.0 client software on each of the network's 1,300 workstations. Next, Taiwan Developer Labs equipped most of the Taipei County Government network's workstations with smart card and fingerprint readers.
Integrating Tai-Hao Devices
Taipei County Government chose three authentication devices from Taiwan Tai-Hao Enterprise Co. Ltd. (www.tai-hao.com). All of the laptops and most of the desktop PCs, according to Tai-Hao representative Jerry Lai, are equipped with Tai-Hao's Smart Card Reader Keyboard F21KC (www.tai-hao.com/english/product/cardreader.html).
In addition, some of the desktop PCs are equipped with Tai-Hao's Smart Card Reader F21RCRB (www.tai-hao.com/english/product/cardkey.html). These smart card readers can read any smart card that supports the International Standardization Organization (ISO) 7816 standard. A few of the desktop PCs are also equipped with Precise Biometrics' Fingerprint Reader PB100SC (www.tai-hao.com/english/product/finger.html).
To enable the use of its devices with NMAS 1.0, Tai-Hao provided Taipei County Government with the following two authentication modules:
An authentication module for the fingerprint reader. Tai-Hao purchased the module for the fingerprint reader from Precise Biometrics (http://www.precisebiometrics.com/), a Swedish company that develops high-level security solutions based on fingerprint verification. Tai-Hao is the sole agent and distributor of Precise Biometrics' Precise 100 series of fingerprint readers in the Asia region. According to Lai, Precise Biometrics developed the NMAS modules for its Precise 100 series in cooperation with SAFLINK.
An authentication module for the smart card reader and smart card reader keyboard. Tai-Hao worked with engineers in Taiwan Developer Labs to develop the III NMAS Smart Card Login Method module for the smart card reader and smart card reader keyboard. "Tai-Hao appreciates Novell's cooperation [on this project] to a great extent," says Lai.
THE SEQUENCE TO SUCCESS
With the requisite hardware and software installed, the Novell-trained engineers from Taiwan Developer Labs worked with Taipei County Government to use several login sequences. Taipei County Government employees are now required to enter up to three login factors--an eDirectory password, a smart card, and a fingerprint--depending on the importance and each resource's relative level of confidentiality.
Setting up these login sequences required first creating Login Method objects in Taipei County Government's eDirectory tree. When the engineers from Taiwan Developer Labs installed NMAS 1.0, the installation program automatically created a Login Method container in the Security container in the eDirectory tree. The Novell engineers from Taiwan Developer Labs also created three Login Method objects in the Login Method container--one object for each of the Novell and third-party methods. In this case, the engineers created Login Method objects for each of the following methods:
eDirectory password
Tai-Hao smart card reader
Precise Biometrics fingerprint reader
The NMAS installation program also created a Login Policy container in the Security container. Novell engineers from Taiwan Developer Labs created four login sequences in this Login Policy container. These sequences are stored as properties of the Login Policy container object. The Novell engineers created the following login sequences:
eDirectory password
eDirectory password and smart card
eDirectory password and fingerprint
eDirectory password, smart card, and fingerprint
MAKING THE GRADE
Deploying NMAS 1.0 Enterprise Edition enabled Taipei County Government to make use of the NetWare 5.1 graded authentication feature. The graded authentication feature (first included with NetWare 5) tightens security through a combination of grades, security labels, and clearance levels. Basically, graded authentication better protects resources by requiring users to log in using a sequence that matches their security clearance, which must in turn match the grade of the resource they want to access. Naturally, users must also have the appropriate rights within eDirectory to access resources after they have been authenticated.
In this case, Novell engineers from Taiwan Developer Labs worked with Taipei County Government to label various resources and to grant particular users security clearance equivalent to one of the following possible combinations: Password, Password&Token, Biometric&Password&Token. According to Greg Wu, manager of the Taiwan Developer Labs, approximately 2,500 resources on Taipei County Government's network were graded at the Password&Token level, and 1,500 users were granted Password&Token security clearance. Only 25 volumes were graded at the Biometric&Password&Token security clearance, with a total of only five users granted equivalent security clearance.
What does this mean? Users who want to access volumes graded at the Password&Token level must have Password&Token security clearance. These users must also have rights to log in to the network using the network's password and token method--in this case, the Tai-Hao smart card method. Similarly, if users want to access volumes graded at the Biometric&Password&Token level, they need equivalent security clearance. They also need rights to log in to the network using the network's password, token, and biometric method--in this case, the Precise Biometrics fingerprint method.
NMAS in Action
For example, suppose that Patrick in Accounting is logging in to the network for the first time, or suppose that he is requesting Password&Token clearance for the first time. On the initial login screen, Patrick enters his eDirectory username and then clicks the Advanced button. (See Figure 3.)
Figure 3
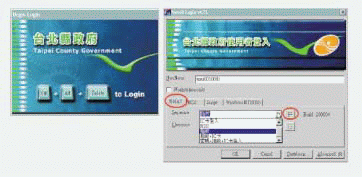
When Patrick clicks the Advanced button, two additional fields appear under the NMAS tab: Sequence and Clearance. Patrick enters the name of the login sequence he will use in the Sequence field--in this case, Payroll. Patrick then enters the clearance level he is requesting in the Clearance field--in this case, Password&Token. Both of these fields also have Browse buttons that enable users to choose from a list of available login sequences or clear-ance levels.
Patrick then responds to prompts by entering his password and swiping his smart card. When he clicks OK--assuming he has entered the correct information and that the MIS specialists have assigned him the clearance he has requested--he is authenticated to eDirectory. Patrick then gains access to the volume and partition that hold the payroll data (assuming his ACLs also grant this level of access).
Patrick completes these fields only the first time he logs in or each time he requests a login sequence and clearance level that differs from the login sequence and clearance level he last requested. Otherwise, Patrick enters only his username and Enter, after which the login sequence and clearance level he last entered are invoked. (For more information about what goes on behind the scenes during this login process, see "NMAS Under Cover.")
Enable Remote Access
Few users have access to the Taipei County Government network from outside its firewall, and employees must request special permission to gain this access. At this point, approximately only 100 employees have requested and received permission to access the network from outside the firewall.
To enable Taipei County Government's remote and mobile employees to access the network from outside the firewall, UniBiz first installed a Cisco 2500 Series Access Server (www.cisco.com/univercd/cc/td/doc/pcat/2500as.htm). The Cisco Access Server communicates with the BMAS 3.6 server that UniBiz installed on the NetWare 5.1 server that is running the eDirectory master replica. (See Figure 2.)
Both the Cisco Access Server and BMAS 3.6 support the Remote Authentication Dial-in User Service (RADIUS) protocol. (You can read about the RADIUS protocol in RFC 2138 and 2139. You can download these RFCs at http://www.ietf.%20org/rfc/rfc2138 and www.ietf.org/rfc/rfc2139, respectively.) Incidentally, the RADIUS services offered by BMAS are now available in NMAS 2.0.
To gain access to Taipei County Government's network, remote and mobile employees dial a local number to access the Cisco server. When prompted, these employees then enter their eDirectory username and password. This server uses RADIUS to pass this authentication information to the BMAS server. BMAS removes the eDirectory username and password from the RADIUS package and uses Novell Core Protocol (NCP) to pass this authentication information to eDirectory (running on the same server).
eDirectory then checks the received username and password against the username and password it has stored for each particular employee. If the information matches, eDirectory uses NCP to return to BMAS the decision to grant this employee access. BMAS then uses RADIUS to forward this decision to the access server.
Both the Cisco Access Server (as with any access server) and the BMAS RADIUS server (that is, the RADIUS. NLM running on the BMAS 2.6 server) are eDirectory clients. Thus, Taipei County Government's MIS specialists can manage both servers and can control users' access to those servers just as they manage and control access to other eDirectory objects.
WHAT'S DONE AND WHAT'S NEXT?
The Novell access and security solution is the solution that Taipei County Government was looking for. Because this solution has eDirectory at its core, the organization now has a central location for storing identity information, authentication credentials, and access control policies. With eDirectory and Novell Account Management 2.1, Taipei County Government now enjoys the effects of consolidated user accounts: Employees need enter only one set of credentials to access all of the network resources to which they have rights; MIS specialists manage access rights from a central location--including access rights for the 100 remote users who access the network via BMAS 3.6.
Most important in the context of this security-focused issue of Novell Connection, this solution better protects the organization's information systems. For one thing, because employees have only one set of credentials to memorize, they are less likely to write down these credentials and are thus less likely to compromise security. For another thing, MIS specialists now confidently assign from a central location the access rights employees need. Equally confidently, MIS specialists delete or disable access rights as needed.
Of course, Taipei County Government has increased security through its use of multifactor authentication methods enabled through NMAS 1.0. The organization no longer protects its most important and confidential resources with only passwords, which take no more than a good guess to break. Instead, Taipei County Government protects such resources with combined login factors.
To access these protected resources, employees with the necessary rights must enter an eDirectory password and a smart card. For some highly confidential resources, employees with rights must provide an eDirectory password, smart card, and fingerprint to gain access.
Taipei County Government has come a long way but still has a bit further to go to complete its planned access management project. For example, Taipei County Government plans to migrate to Microsoft Exchange 2000, for which it will install a new Windows 2000 server running Microsoft Active Directory. Naturally, the organization will integrate the resulting new accounts with eDirectory.
Taipei County Government also plans to upgrade to NMAS 2.0 and is considering deploying Novell SecureLogin, which enables true single sign-on. With Novell SecureLogin, Taipei County Government could optimize security by assigning employees separate passwords or other login factors to access various applications. However, the employees wouldn't need to even know about these separate credentials. Novell SecureLogin would handle the process of signing on to these applications behind the scenes. Employees would enter their eDirectory credentials (which may include a password, a smart card, a fingerprint, or any combination of the three) only once. Ever after, when employees attempt to access applications that require additional credentials, Novell SecureLogin would sign on to these applications on the employees' behalf.
Regardless of its future plans, Taipei County Government's new approach to its old problem is already serving its purpose. Employees now enjoy managing only a single set of credentials to access all network resources. MIS specialists now save a considerable amount of time by having only one user account to manage per employee. Finally, and arguably most important, Taipei County Government now knows it has taken at least preliminary steps to better protect and secure its information systems.
Linda Kennard works for Niche Associates, a technical writing and editing agency located in Sandy, Utah.
NMAS Under Cover
What happens behind the scenes when a Taipei County Government employee attempts to authenticate to the network's Novell eDirectory tree? Suppose employee Patrick has just completed the fields on the initial login screen. (See Figure 3.) The NMAS client running on Patrick's workstation stores the values Patrick enters in the Windows registry. When Patrick clicks OK, the regular Novell client invokes the NMAS client.
On Taipei County Government's network, the NMAS client establishes a connection with the NetWare 5.1 server that stores the eDirectory master replica, which holds a copy of Patrick's (and each other employee's) User object. (See Figure 2.) Using Novell International Cryptographic Infrastructure (NICI), the NMAS client and server create a secure pipe over which they can exchange encrypted authentication information.
The NMAS client next sends a message to the NMAS server. This message indicates all of the login methods that have been installed on this workstation client. Novell assigns numbers to each of the login methods enabled by Novell and third-party authentication modules.
For this example, suppose that the Tai-Hao smart card method is method 25 and the Precise Biometrics' fingerprint method is method 26. Patrick's workstation client has methods 25 and 26 installed, and Patrick is attempting to use both. The message from the NMAS client indicates that Patrick's workstation client can do methods 25 and 26. Suppose, for this example, that this message also indicates that the login sequence Patrick requested requires method 25 to be completed first, followed by method 26.
Upon receiving this message, the NMAS server invokes the Login Server Method (LSM) associated with method 25, which in this case is the executable code for the Tai-Hao smart card method. (This code is stored as a property of a Login Method object.) The NMAS server then sends a message to the client to DO 25 (in other words, invoke the Tai-Hao smart card method).
The NMAS client then loads the appropriate Login Client Method (LCM), which invokes its own Dynamic Link Library (DLL). The LSM and LCM use a protocol called Multi-Authentication Framework (MAF) to exchange, in this case, information about the Tai-Hao smart card method. During this process, the LCM invokes the method-specific user interface that requests the necessary login factors.
In this case, the user interface may request that Patrick swipe his card. The LCM forwards the information Patrick enters to the LSM. The LSM compares the information it receives with the information stored in eDirectory to ensure that Patrick has entered the correct information. If Patrick really is Patrick and the contents of his smart card are legitimate (that is, match the contents stored in eDirectory), the LSM returns a message to the LCM, indicating that this portion of the login sequence is done and successful. Both the LSM and LCM then return to NMAS.
When Patrick has completed method 25 (in this case, the Tai-Hao smart card method) and assuming his credentials have been accepted, the NMAS server confirms whether it has all of the information needed to authenticate Patrick or whether more information is required. In this case, Patrick must still complete method 26, the Precise Biometrics fingerprint method.
Consequently, the NMAS server invokes the LSM for method 26 and sends a DO 26 message to the NMAS client. The client responds by invoking the LCM for method 26, in other words, invoking the Precise Biometrics method. This process continues until the NMAS server is satisfied that it has received all of the information necessary to authenticate Patrick to eDirectory.
When the NMAS server is thus satisfied, it returns a message to the NMAS client indicating as much. The NMAS client then asks the NMAS server for Patrick's credentials, and the NMAS server retrieves and returns these credentials to the NMAS client. Patrick's credentials essentially indicate Patrick's clearance level for this session.
The NMAS client stores these credentials in a secret storage, and when Patrick attempts to access information, the server on which that information is stored asks Patrick's client for Patrick's eDirectory credentials. As requested, the NMAS client returns Patrick's encrypted credentials, at which point Patrick has an authenticated connection. Although this process may sound complex, it actually occurs within fractions of a second.
The Project Plan
To date, Taipei County Government has completed Phase 1 of its two-phase project to improve and extend access management:
|
PHASE 1 |
DONE? |
|
Consolidate user accounts and enable single sign-on Integrate user accounts on Windows NT and Windows 2000 servers with Novell eDirectory 8.5.1 using Novell Account Management 2.1 |
Yes |
|
Protect network resources through multifactor authentication Install Novell Modular Authentication Service (NMAS) 1.0 Enterprise Edition Integrate Tai-Hao smart card and fingerprint readers with NMAS 1.0 |
Yes |
|
Enable remote users to securely access the network via Remote Authentication Dial-In User Services (RADIUS) protocol Install BorderManager Authentication Services (BMAS) 3.6 |
Yes |
|
Integrate existing products (such as custom certificate server) with eDirectory 8.5.1 |
Yes |
|
Integrate custom Electronic Document Exchange application with Lightweight Directory Access Protocol (LDAP) |
Yes |
|
Install new Linux server running new web management console and integrate with eDirectory |
Yes |
|
PHASE 2
|
|
|
Extend Novell eDirectory 8.5.1 to entire county network |
No |
|
Migrate from iPlanet Messaging Server to Microsoft Exchange 2000 |
No |
|
FUTURE |
|
|
Provide online government services to residents of Taipei County through eDirectory-based solution |
No |
Redirecting to eDirectory Requests for Services in NT Domains
Novell Account Management 2.1 redirects users' requests for services running on various platforms to eDirectory. These platforms include Windows 2000 and NT, Solaris, and Linux. For example, to redirect to eDirectory users' requests for services running on Windows NT, Novell Account Management 2.1 replaces a key Microsoft file (called SAMSRV.DLL) with an eDirectory-based file.
On Windows NT, resources are created and managed in a database called the System Account Manager (SAM). Applications that need information from the Windows NT domain make requests to SAMLIB.DLL. These applications include those running on the NT server or on an NT workstation.
SAMLIB.DLL uses Remote Procedure Calls (RPCs) to communicate with SAMSRV.DLL. For applications being run on the server, this communication is done internally. For requests originating from a workstation, the RPC requests are sent to the server. After the server RPC receives a request, it is extracted and passed to SAMSRV.DLL. SAMSRV.DLL then accesses SAM, where the domain namebase is stored and performs the requested operation. (See Figure 4.)
Figure 4
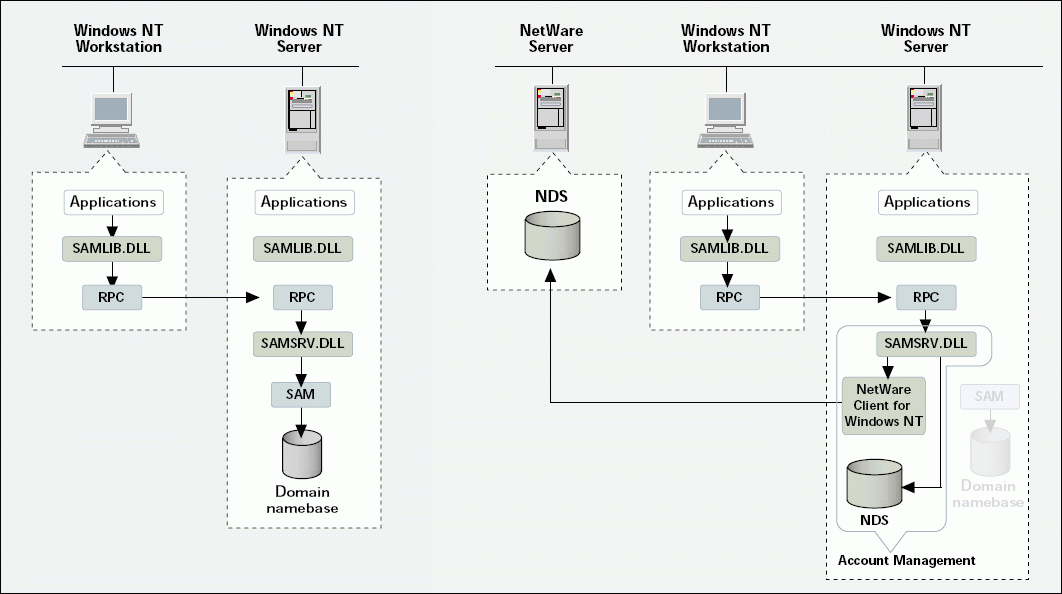
Novell Account Management 2.1 relocates Windows NT domains into eDirectory by replacing the Microsoft SAMSRV.DLL file with an eDirectory-based SAMSRV.DLL file. All application requests to the domain namebase are then redirected to eDirectory (which can reside on a NetWare server, an NT server, or both). eDirectory stores the User, Computer, and Group objects that take the place of the objects previously used from the domain. (See Figure 4.)
The advantage of this redirection is that all existing applications continue to work without any change. You can continue to use familiar Windows NT tools to manage accounts in eDirectory. eDirectory containers can scale into hundreds of thousands of objects, unlike NT domain objects, which are limited to a few thousand.
SecureInside
SecureInside offers more than systems integration services such as those it provided for the Taipei County Government access-management project. Founded in 1996, SecureInside helps government agencies in Taiwan deploy workflow solutions based on a public-key infrastructure (PKI).
For example, SecureInside helped Taipei County Government set up an electronic document-exchange solution that enables employees to apply, have approved, and follow-up on requests for leave, purchases, and reimbursement (for travel expenses, for example). Over the past five years, SecureInside has expanded this solution to include the Department of Land Administration's 107 offices and other government agencies as well, such as banks and courthouses within Taipei city and county.
Because SecureInside is a small company, it considers its partners, including Novell, critical to its success. "Novell is an important partner," says SecureInside senior manager Luke Lee. In fact, Lee adds, Novell products play a major role in all of the solutions SecureInside deploys and helps deploy throughout Taiwan.
Taipei County
The largest of the Western Pacific islands, Taiwan is roughly the size of Maryland and Delaware with a population nearly four times as large. Of the 22.5 million people who live in Taiwan, 3.6 million live in Taipei county alone--the most heavily populated of Taiwan's 16 counties. Taiwan's counties include the following: Taipei, Tao-yuan, Hsinchu, Miaoli, Taichung, Chang-hua, Yuanlin, Chiayi, Tainan, Kaoshiung, P'ing-tung, Taitung, Hualien, Nan'tou, Ilan, and P'enghu.
Like every county in Taiwan, Taipei county has its own government headed by magistrates and councillors. Magistrates are elected by popular vote for up to two four-year terms of office, while councillors are popularly elected for four-year terms of office. Taipei county's December 2001 elections placed 64 new councillors and secured a second term of office for Magistrate Chen-Chang Su.
* Originally published in Novell Connection Magazine
Disclaimer
The origin of this information may be internal or external to Novell. While Novell makes all reasonable efforts to verify this information, Novell does not make explicit or implied claims to its validity.