Thin Is In
Articles and Tips: article
01 Jul 2000
Assuming you've read the related article entitled "Bright Minds, Big democity," you already know something about the value of thin-client computing and how Novell is demonstrating this technology on its democity web site http://www.democity.novell.com). What you may not know is how difficult it can be to manage this technology on your company's heterogeneous network without the proper network management tools. This article explains how NDS eDirectory, NDS Corporate Edition, and ZENworks for Desktops 2 can simplify the task of managing a heterogeneous network, allowing you to experience the full benefit of thin-client technology.
STRIKING A BALANCE
Thin clients look similar to PCs. As the name suggests, however, thin clients are thinner. (See Figure 1.) Because thin-client servers fully process network applications and data, thin clients do not require a sophisticated operating system. Thin clients also require a great deal less RAM and processing speed than PCs. They also have no need for expansion slots or drives, whether hard, floppy, or CD-ROM.
Figure 1: Thin-client computing fully processes applications and data on a server and limits the amount of information sent between client and server.
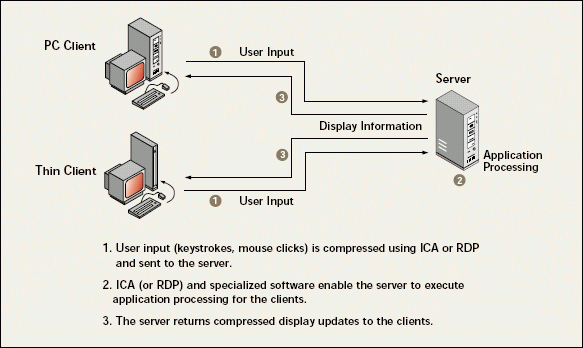
Consequently, thin clients have no risk of hard-disk-related problems. Users who have thin clients cannot endanger the network by loading viruses from personal floppy diskettes, installing software that causes conflicts and crashes, or copying company programs and proprietary data.
If problems occur on the client side, Citrix Systems Inc.'s MetaFrame 1.6 supports session shadowing. (MetaFrame is server-based software that provides additional client and server functionality.) With this feature, you can view a user's display or control the mouse and keyboard for remote support or training.
Although installing thin clients can be highly advantageous, thin clients pose no serious threat to the existence of traditional PCs or laptops. For one thing, thin clients aren't portable. For another, thin clients can be set to a maximum of only 256 colors. Applications that require high-quality graphics, such as sophisticated CAD programs, are best left on PCs. PCs are also required for multimedia programs on CD-ROM or for users who need e-mail service or access to a floppy disk drive.
In addition, many users will probably need to run everyday applications, such as word-processing programs, from PCs. For example, if users need to work with a number of applications simultaneously and continuously throughout the day, convenience would dictate that the applications be processed on PCs rather than on thin-client servers.
The bottom line is that your company's network is likely to include a mixture of thin clients and PCs. More to the point, you will need some way to make this hodgepodge interoperable and manageable before introducing thin clients to the network becomes more of a hindrance than a benefit.
You must also consider users. In a mixed network environment, users may not only use a variety of workstations throughout the day but may also be directed by MetaFrame to use resources on any server in a thin-client server farm. You will probably want to spare users the anxiety of adjusting to different desktop views and instead provide a consistent look and feel that travels with users from one network device to the next.
ZEN AND THE ART OF MIXED NETWORKS
ZENworks for Desktops 2, by virtue of its integration with NDS eDirectory, can provide the interoperability and manageability your company needs for its venture into thin-client computing. For example, with ZENworks for Desktops 2, you can create policy packages, store them in NDS as objects, and then associate the policy packages with users or workstations that you also import as NDS objects.
Policy packages are comprised of individual policies that specify what resources and rights are available to each user, as well as how the desktop should look on any workstation to which the user has been granted rights. You can even create policy packages to coincide with tasks or roles that are associated with groups of users, such as salespeople or engineers, or the physical location of the workstation, such as a branch or the home office.
All of the policy packages that apply to a particular user create that user's digital persona. With NDS eDirectory's cross-platform capabilities, you can apply a user's digital persona across all devices on the network. Using a standardized desktop interface, the user can authenticate to NDS eDirectory once and access all the resources to which that user has rights. Parallel directories do not have to be maintained for PCs and thin clients, eliminating redundant management. In addition, the appearance of users' desktops is now constant.
RESOURCES WILL BE ASSIMILATED
In today's world, redundant resource management can be one of a company's biggest expenses. Duplicate user account information is input and managed in numerous databases and directories across the network. Thin-client servers can compound this problem. Like all Windows NT-based operating systems, Windows NT Server 4.0, Terminal Server Edition (TSE) requires the use of Windows NT domains. (TSE is the first multiuser version of Windows NT.) If your company's network includes more than one NT domain and you want to grant users access to NT resources across the network, you must also establish trust relationships between the domains.
When a user logs in to an NT domain, the Primary Domain Controller (PDC) or one of the Backup Domain Controllers (BDCs) validates that user's username and password through the centralized Security Accounts Manager (SAM) database. The user then has access to all resources in that domain and every trusting domain as well.
However, logging in to an NT domain through SAM will not provide users with access to the network's non-NT resources. How will you manage and grant users access to thin clients, Solaris servers, mainframes, and PCs that are running an operating system other than Windows NT?
If you install Novell's NDS Corporate Edition on top of NDS eDirectory on your Windows NT servers, you can use Novell's Domain Object Wizard to migrate NT domains to the NDS tree. In other words, you can turn NT domains into NDS domain objects.
As a result, you will no longer need to establish and maintain complicated trust relationships or manage NT and non-NT resources separately. You can manage every resource on your company's network through NDS eDirectory.
In addition, users will have to log in only once to NDS eDirectory and access all authorized resources across the network. By virtue of a user's digital persona in NDS, that user is also guaranteed that desktop views will remain consistent from one workstation to the next and from any server in a server farm. (For more information about NDS Corporate Edition, visit http://www.novell.com/products/nds/ndscorporateedition.)
democity showcases the ability of NDS Corporate Edition to consolidate all of the resources on your company's network. The democity Windows NT and Solaris servers are running NDS Corporate Edition. (For UNIX servers, a command line tool, migrate2nds, migrates accounts from /etc files, NIS, or NIS+ directories into NDS eDirectory.)
Although the democity Citrix servers could run NDS Corporate Edition, these servers are not actually running this software. To control access to the Citrix servers, democity uses instead a ZENworks policy called Dynamic Local User (DLU).
WHO WAS THAT MASKED USER?
With the DLU policy, you can grant users access to thin-client servers without creating Windows NT domains or trust relationships. You don't even have to create individual user accounts in the SAM database or use the PDC to validate users. Anonymous user accounts can be created on the fly.
When a user first authenticates to NDS eDirectory, it will determine if any ZENworks policies should be applied to the user. If the DLU policy should be applied to the user, ZENworks queries the SAM database to see if the user has a valid SAM account. If an account does not exist for the user, ZENworks dynamically creates an anonymous account that is in accordance with the user's ZENwork's policy package.
In this way, the user not only gains access to NT resources without authenticating separately to the PDC but is also guaranteed the same desktop view with which the user is already familiar on non-NT devices. To cut down on administration, user accounts can be deleted from the local SAM database when the user logs out.
If you need to grant users temporary access to NT resources, as democity does, you can deploy the DLU policy so that you don't have to maintain SAM accounts for users or assign these users to NT domains. This solution does have a drawback, however: Because of the anonymity involved, you cannot easily track user activity. In addition, you need NDS Corporate Edition to consolidate other network resources, such as Solaris and UNIX servers.
PLAYING TO THE PC ADVOCATE
You can also use the DLU policy to grant users access to PCs running Windows NT. In fact, ZENworks for Desktops 2 offers numerous benefits specifically tailored to the needs of a network using PCs.
For example, ZENworks for Desktops 2 leverages the power of NDS eDirectory to remotely distribute, from a central location, applications and upgrades to PCs that need to run those applications locally. With ZENworks for Desktops 2, you can create Application objects in NDS and associate these objects with particular Workstation, User, Group, or container objects. The applications can then be automatically deployed where needed.
ZENworks for Desktops 2 also offers additional security for PCs. For example, PCs are more vulnerable to viruses than thin clients are. You can protect PCs and your network with Network Associates' VirusScan, which is included in ZENworks for Desktops 2. You will receive notification of updates as well as Simple Network Management Protocol (SNMP) alerts if a virus is detected.
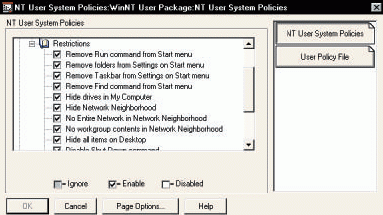
You can also lock down the desktops so that PC users cannot install unauthorized hardware or software. (See Figure 2.) You can restrict access to local drives and even the Start|Run menu. In addition, the ZENworks' snAppShot utility records an application in its pristine state so that registry and .ini files damaged by users can be automatically replaced with a clean copy. (For more information about NDS eDirectory and ZENworks, visit http://www.novell.com/products/nds and http://www.novell.com/products/zenworks/desktops.)
Figure 2: You can lock down network desktops using workstation and user policies.
CONCLUSION
Although thin-client computing promises timely and quick access to information and the end of performance nightmares, the reality may be less than ideal. Your company will probably end up with a mixture of thin clients and PCs, an environment that will undoubtedly compound your network management headaches and confuse users even more.
Novell has a solution that can deliver on the promise of thin-client computing. By combining thin-client technology with NDS eDirectory and ZENworks for Desktops 2 on democity, Novell has shown how you can integrate thin-client hardware and software with legacy network equipment to create a network that meets the needs of users and is easily managed.
* Originally published in Novell Connection Magazine
Disclaimer
The origin of this information may be internal or external to Novell. While Novell makes all reasonable efforts to verify this information, Novell does not make explicit or implied claims to its validity.