The Human Face of NDS
Articles and Tips: article
01 Aug 1999
During BrainShare '99 in Salt Lake City, Dr. Eric Schmidt, Novell chairman of the board and CEO, unveiled digitalmeTM, a new initiative to help Internet users manage their digital identity. As Dr. Schmidt explains, "Managing identity is the key to creating networked communities and establishing trusted relationships among the myriad people, applications, services, and devices that now populate the Net."
Why is managing digital identity so important? To understand why managing digital identity is critical to the future of the Internet, you must understand some of the problems facing Internet users and, therefore, Internet companies today.
PROBLEMS FACING INTERNET USERS
In the last few years, the telecommunications world has done an incredible job of getting the Internet connected, making it scalable, and improving its performance. The world is connected in ways we would have never dreamed of several years ago. Just 4 1/2 years ago, getting on the Internet meant finding a Telnet/FTP client or using CompuServe. Can you believe that Netscape Navigator 1.0 shipped at the end of December 1994?
Now accessing the Internet is easy: When you purchase a new computer, Internet software is already installed, and when you launch this software the first time, it prompts you to enter the information needed to connect to your Internet service provider (ISP). If you are on the road, you can simply walk into a shopping mall and use a kiosk to access the Internet. The Internet has become so easy to use that people who one year ago wouldn't consider getting on the Internet can't wait to get connected now.
In addition, the number of services and products available on the Internet has grown in leaps and bounds. In 1993, there were just over 100 web sites; today, more than 1,200 new web sites go live every day. You can buy anything you want online, communicate with any interest group imaginable, and find out more than you probably want to know about any subject.
Using Pseudonyms
Despite the plethora of information available, however, I just get frustrated when I surf the Internet. For example, I am tired of filling out forms to join web sites, and then I often don't remember my username and password the next time I visit a particular web site.
I also hate that the Internet has proven to me that there are other people named Carrie Oakes, and if I want to visit a password-protected web site, I must become Carrie_Oakes123 or 9080Carrie. In the physical world, I am always known as Carrie Oakes although my passwords and personal identification numbers (PINs) are different. Because of these frustrations, I have actually limited my experience on the Internet.
The next technological improvement to the Internet will involve maintaining, leveraging, and controlling the relationships you want to have based on whom you want to be and whom you trust. This technological improvement will enable you to control how you log on to a web site, providing authentic sign-ons, duplicitous sign-ons, and anonymous sign-ons.
Getting to Know All About You
The more information a company knows about you, the more that information is worth to that company and others. Unfortunately, as users rush to use the Internet, the balance of power in privacy issues has shifted to the unscrupulous. For example, I recently completed a form in order to visit a web site. A few days later, I was spammed: I received an e-mail message advertising some products I might be interested in.
Since I was interested in those products, I returned to the web site. While I was there, I looked for a gift for my grandmother and purchased the perfect item. A few days later, I was spammed again. This time, however, I received an e-mail message advertising products that an 80-year-old woman might want to purchase. Why did the company first send me useful information and then three days later send me useless and annoying information? As an Internet user, I have no control over the information companies gather when I visit their web site.
Privacy advocates and zealots are consuming air and legislative time discussing the Internet's little secret--that is, how Internet-based companies are collecting information from Internet users and what these companies are doing with this information. Internet-based companies are building web sites that are looking for ways to get personal information about you and to provide you with personalized services. In fact, the Internet gives the term focused marketing a whole new meaning.
Unfortunately, most Internet users don't understand the costs of personalized services. They don't know that the information they give freely in exchange for Internet services is the reason why top Internet-based companies are valued so highly. Internet-based companies are gathering, acting upon, and selling Internet users' personal information in real time.
In fact, many web sites run applications that collect information about Internet users, and these users aren't even aware they are being "eyeballed." For example, while your browser is connected to a web site, that web site can run a software application that reads all of your cookie information, including cookie information for other web sites. With these kinds of applications readily available, imagine the kind of information a company can find out about you and other Internet users and the databases it can build.
Companies justify these actions by saying they can offer a whole new range of personalized, and might I add unsolicited, services. These companies argue that Internet users are willing to provide personal information for personalized services. However, these companies have forgotten or ignored users' rights to negotiate and to control personal information.
In the real world, private information moves slowly and can be protected. For example, if you are annoyed by excessive postal advertisements, you can write and ask to be removed from a mailing list. If you do not want someone to call you, you simply do not give that person your telephone number.
In the Internet world, however, information moves and proliferates so quickly that once you have lost control of your private information, it becomes easier to abandon that information than to regain control of it. The travesty is that private information is often collected surreptitiously without a user's cooperation.
Regulating the Unscrupulous
Associations and technologies are emerging to help put privacy policies in place. For example, BBB OnLine (http://www.bbbonline.org) is working to build users' trust and confidence in the Internet. The Platform for Privacy Preferences (P3P) project is working to create a library of privacy policies for creating web site forms, receiving and sending private information, and posting privacy statements. After these privacy policies are created, companies can standardize on them. (For more information about the P3P project, visit http://www.w3.org/P3.)
These associations are advocating that companies warn Internet users what information is being collected and how that information will be used. These associations are also promoting self-regulation, which would enable users to notify a company that they don't want their information shared with other companies.
However, the Internet community has been slow in accepting privacy policies, and many of the privacy policies in use are vague and may not be enforced. In addition, the U.S. government has started to hold legislative sessions to discuss what can be regulated and how the U.S. government can put policies in place to protect the innocent or the naive.
In Europe, the laws about privacy on the Internet are causing concerns with users because these laws may affect the type of services users can purchase. The European Union Assembly (EU), which includes communication ministers from 15 European countries, wants Internet users to have unfettered access to their personal information that is collected online and to be able to choose whether or not they want to disclose such information. In addition, the EU seeks tough penalties to protect users from fraudulent companies.
According to critics, however, the language of the EU's amendments is so vague that it would force ISPs to employ vast teams of lawyers and researchers. To protect themselves, ISPs would probably end up shutting down web sites without having definite proof of illegal activity.
In addition, Internet-based companies argue that the proposed EU amendments would stifle innovation. These companies also question how web sites based in non-European countries would be monitored. Recently, EU officials announced that EU member governments have negotiated a compromise that will set out some requirements and recommendations that are not overly restrictive.
Although Internet users are worried about privacy, most users don't support regulations or controls. Most Internet-savvy users realize that personalized services on the Internet can be attractive. For example, a web site that recalls your tastes and buying habits can save you time and find bargains that interest you. Most users also realize that creating strict policies and regulations for the Internet would stifle innovation and e-commerce.
To be the devil's advocate, however, I have noticed that when Internet users feel that they are being violated, the backlash can be both monumental and quick. For example, when Intel Corp. released its Pentium III tracking system (http://www.zdnet.com/pcweek/stories/news/0,4153,1014318,00.html) and Microsoft Corp. released its Win98 ID identifier (http://www.zdnet.com/zdnn/stories/news/0,4586,2222971,00.html), the negative response from Internet users made both companies abandon their plans for gathering information through these products.
THE ANSWER? TECHNOLOGY
Where is the middle ground in the controversy between regulation and unfettered innovation on the Internet? Technology that enables users to manage their digital identity. Of course, technology will never be able to completely protect users' privacy, but enabling users to control their personal information will definitely help.
Novell is well positioned to provide such a solution. The Internet chaos is crying out for a directory service, and Novell Directory Services (NDS) has been providing companies with mission-critical directory services for more than six years. As Dr. Schmidt explains, "The digitalme technology is the natural outgrowth of [Novell's] leadership in directories. It's the next step in the directory. It's putting your identity, what you care about, in the directory as well as all the things you manage."
Built on the foundation of NDS, the digitalme technology changes the industry's paradigm for managing information. This technology enables Internet users to act as their own personal network administrator. They can put information about themselves in a digital safe and then create polices to define the relationships they want on the Internet. (For more information about how NDS works as the foundation for the digitalme technology, see "NDS, the Only Way to Enable the digitalme Technology.")
With NDS and the digitalme technology, Internet users can create NDS objects that represent personal resources and information, such as ID cards, passwords, cookies, bookmarks, addresses, personal statistics, preferences, files, web pages, music, and media. After creating these objects, users can create profiles and policies to control how these objects are accessed.
For example, I have a credit card and a shipping address that I use to purchase products from certain Internet web sites. Each of these web sites is given specific, secure access to this information in NDS. If I get a new credit card or need to change my shipping information, I simply change the credit card information in NDS. NDS then ensures that each web site that has been granted access has the most up-to-date information.
In addition, NDS provides tracking capabilities. Internet users know exactly what personal information was sent to a web site and when it was sent.
HOW DOES THE DIGITALME TECHNOLOGY WORK?
Because the information users want to control is private, Novell's digitalme technology enables each person to create policies that grant access to his or her information. In addition, the information is encrypted when it is stored and retrieved.
The high level of protection afforded by the digitalme technology warrants the naming of the storage mechanisms: Users store their information and policies in a Safe object. Multiple safes are kept in a Vault object.
Novell and third-party developers provide client-based utilities, which Internet users can use to manage their identity information. After defining their personal resources and policies, users can then log on to the Internet, and NDS and the digitalme technology will enforce these policies.
Digital identities are not limited to people. Companies, like individuals, have different "faces" they want to present to different users. Services can also have a digital identity. Companies can store information about a service safely in a digital identity that is unique to that service.
In addition, the digitalme technology provides ways for Internet users to join and participate in online communities while enabling these users to control their digital identity. For example, by creating a digitalme profile, a person can share certain information with trusted requesters. The sharing of a profile is called a relationship. (See Figure 1. Profiles are explained in more depth later in this article.)
Figure 1: With Novell?s digitalme technology, Internet users can create profiles to share information with trusted requesters.
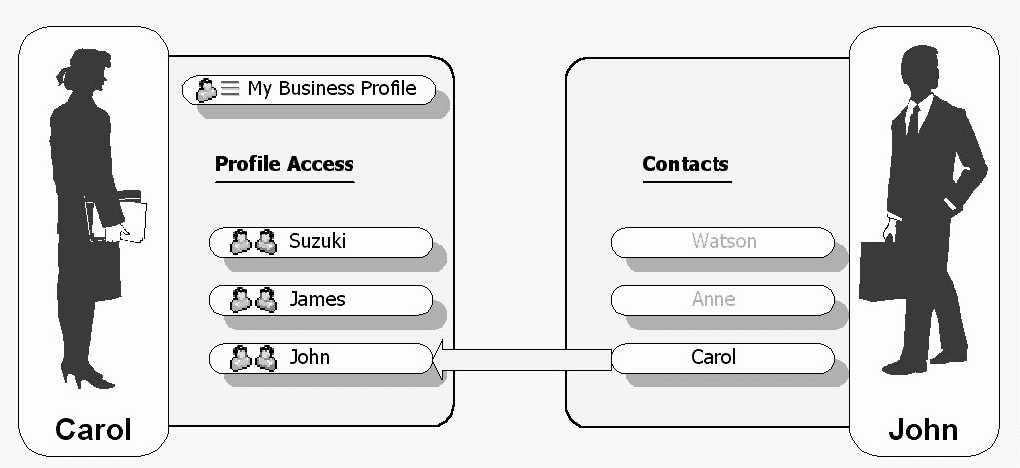
Each relationship enforces and tracks access from a specific entity to a specific profile in a user's Safe object. Although each relationship is one to one, there can be multiple and redundant relationships.
THE DIGITALME COMPONENTS
The digitalme technology includes the following components:
Identity server
Zero-byte client
Web server
Rapid Application Development (RAD) tools
Identity Server
The identity server holds the new NDS objects created for Novell's digitalme technology, such as Safe objects and Vault objects, and other services, such as account creation and NDS itself. Both Safe objects and Vault objects are container objects.
Each Safe object belongs to and is managed by a particular digitalme user. The user stores his or her identity information in this Safe object. By default, only the user has rights to the Safe object, since administrative rights are filtered. As the owner of the Safe object (and by extension the information contained therein), each user can set policies to determine access to his or her own information.
A Vault object can hold Safe objects and other Vault objects. There can be multiple Vault objects within a single NDS tree. A Vault object can be created as a subordinate container object to Organization, Organizational Unit, Locality, Domain, or other Vault objects. Multiple levels of Vault objects enable a hierarchy for ease of management and partitioning.
A company such as an ISP hosts the Vault object and creates a policy for each User object. This policy can limit the resources the user consumes or set password and login restrictions.
It is important to understand that although the host company creates policies for User objects and provides the physical storage for the digitalme information, this company does not manage Safe objects and all of the information stored in these objects. Only the user has rights to his or her Safe object.
The Vault object is defined in three layers, as explained below. (See Figure 2.)
Figure 2: Novell has defined the digitalme Vault object in three layers.
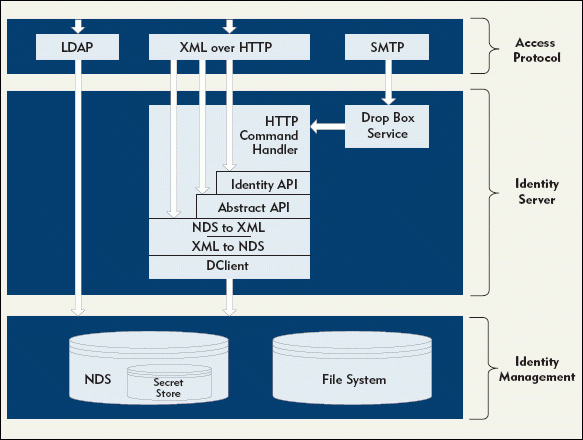
Access Protocol. Users access their information via industry standard protocols Lightweight Directory Access Protocol (LDAP) and HTTP. Secure Sockets layer (SSL) is available over both protocols to ensure security during the transmission of the data.
Identity Server. The identity server extends LDAP and HTTP to provide additional access to data stored in the Vault object. These extensions provide functionality such as Novell's secret store technology, transparent access to files stored at file locations in NDS, and the ability to set file access rights. The Identity server functions as an NDS access point and does not need to execute on every server in the NDS tree.
Identity Management. Standard NDS authentication and authorization methods are used to control access to information. Like any network operating system, NetWare can be vulnerable to intruders who have physical access to the server. To protect confidential information such as passwords and credit card numbers from any intruders, some digitalme information is stored in NDS using Novell's secret store technology. This secret store technology also provides a nonrepudiation feature, which means the host company cannot change a user's password and then log on as the user to obtain the user's secrets.
Zero-Byte Client
How do Internet users access the identity server? Internet users do not have to install a special digitalme client; they simply need a browser such as Netscape Navigator 4.x or Internet Explorer 4.x. When an Internet user wants to access digitalme features, lightweight JavaScript and Java applets are downloaded from the digitalme web site. This zero-byte client then accesses the identity server using standard protocols such as SSL, HTTP, or LDAP.
When the Internet user logs in to a digitalme web site, that user is prompted to enter NDS credentials. The user is then presented with a profiler, which is a graphical book that holds the user's profiles and provides management tools to help the user manage his or her information.
The profiler displays only the user's information; the profiler doesn't allow access to any other objects in the NDS tree. In addition, the profiler provides the following services:
Account Management. Users can edit unique credentials within their User object. For example, they can change their passwords or set user-defined preferences such as being listed or not being listed in the public address book.
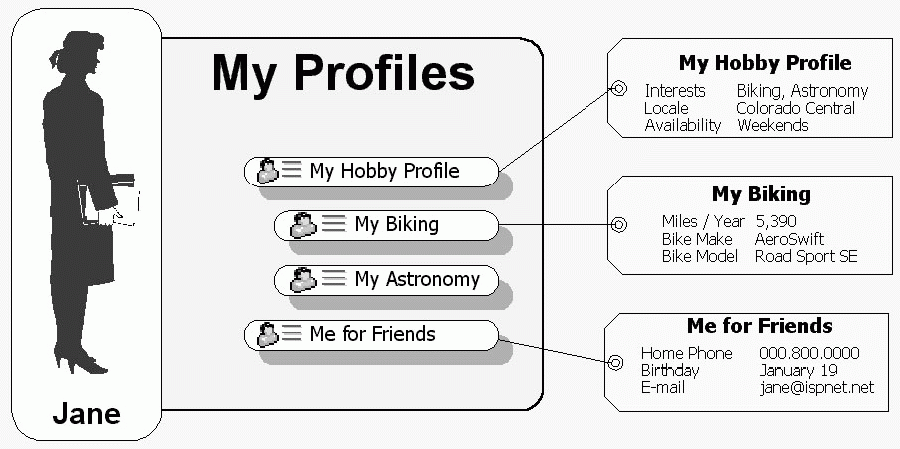
Profiles. Users can view, create, edit, and delete profiles, which are displayed graphically as meCards. (See Figure 3.) Profiles include text fields as well as graphical fields. For example, you can create a business profile with a professional picture, a personal profile with a sound file, or an anonymous profile without a picture. (See Figure 4.)
Figure 3: Internet users use this digitalme GUI to create profiles and policies.
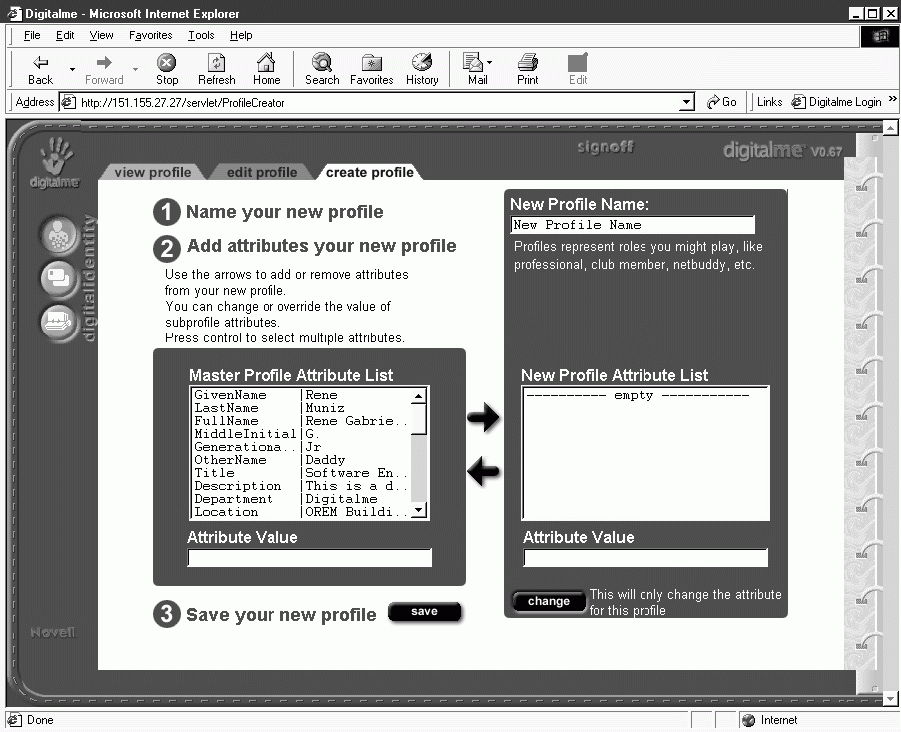
Figure 4: Internet users can create an unlimited number of profiles.
Relationships. Users can create, delete, and edit relationships to the meCards. For example, a user can create a profile that contains anonymous information and then grant a web site or a Group object access to that information.
Address Book. Users can keep a personal address book of contacts. The address book also allows the user to send meCards via standard e-mail clients.
Auto-Form Fill. When users must complete a form to join a web site, the zero-byte client can use the identity information in the User object to automatically complete the form for the user. The zero-byte client then saves the credentials for future access to this web site.
Autologin. When a user browses a web site that requests a username and password, the zero-byte client logs the user in with the appropriate credentials. Essentially, the user has a single sign-on to the Internet and does not have to remember multiple Internet identities.
Novell will continue to add new services to digitalme, including the ability to store bookmarks, files, preferences, and chat sessions. For example, Novell plans to add appropriate messaging, which is the ability to detect the presence of a user who is online and to send the user a message.
Web Server
Because the digitalme web server can be any best of breed server such as Solaris, Linux, Windows NT, or NetWare, companies can use their existing environment to host Novell's digitalme technology. The digitalme web server provides digitalme servlets and serves up Java applets and web pages to zero-byte clients.
RAD Tools
For the user, having a safe in which to store personal information is only as valuable as the services that take advantage of this information. One of Novell's goals is to attract partners to develop digitalme-aware services and applications. Toward this end, Novell is providing RAD tools, including Object Linking and Embedding (OLE) automation tools, Java Beans, and ActiveX controls. Using these tools, developers can easily take advantage of the NDS platform, writing applications and utilities that run on the digitalme technology.
INFOMEDIARY PLEASE
A recently released book entitled Net Worth: Shaping Markets When Customers Make the Rules (Hagel and Singer, Harvard Business School: Jan. 1999) introduced a new Internet marketing term, infomediary. Essentially, an infomediary is an agent that acts on a user's behalf to interact with online sites based on the policies the user creates. For example, with the help of an infomediary, a user could put out what amounts to a personal Request For Proposal (RFP) in search of the best deals for a product or service. A user might even use an infomediary to exchange valuable profile information for discounts or even cash. The infomediary could then use the power of demand to get better deals, thus creating a more competitive environment.
Although most people like the idea of using a personal agent, few companies can deliver such infomediary services because these services require a robust, scalable, and extensible directory service. Novell has announced that Citigroup and FirstUSA are testing the digitalme technology to create such infomediary services.
CONCLUSION
Novell's digitalme technology puts a human face on NDS. This technology also shows why a directory service is important and how powerful it can be. It will be interesting to see how many services and applications will be created with this new innovative perception of the directory.
Novell plans to launch the open beta version of the first digitalme web site on August 1, 1999. At this web site, you can download a beta version of the digitalme technology and developer kits. For more information about the digitalme technology, visit http://www.digitalme.com.
Carrie Oakes works for Novell as a systems engineer. Before joining Novell, Carrie was a systems integrator for 12 years.
* Originally published in Novell Connection Magazine
Disclaimer
The origin of this information may be internal or external to Novell. While Novell makes all reasonable efforts to verify this information, Novell does not make explicit or implied claims to its validity.