Great Walls of Fire
Articles and Tips:
01 Jan 1997
Picture this: You connect to the World-Wide Web (WWW), and your organization'shome page appears by default. This time, however, you are shocked to seelarge color photos of Jennifer Aniston from NBC's"Friends"andAdolf Hitler--which are particularly shocking because they are surroundedby rows of gray swastikas. Who do you work for anyway? The"UnitedStates Department of Injustice,"as the WWW site reads? In this scenario,you work for the United States Department of Justice and are staring atthe efforts of an online vandal who managed to litter the Department's sitewith electronic graffiti last August.
Although attacks such as this one are relatively harmless, many otherattacks on computer systems connected to the Internet are not. For example,by invading a computer system at MCI, hackers stole nearly 50,000 creditcard numbers, and Digital Equipment Corporation (DEC) claims to have lostmillions of dollars worth of software to the infamous hacker Kevin Mitnik.Worse yet, such attacks are increasingly common: The CERT Coordination Center,a U.S. government-funded organization based at Carnegie-Mellon Universityin Pittsburgh, Pennsylvania, says that the number of reported Internet securityincidents rose from 130 in 1990 to more than 2,400 in 1995.
TCP/IP--IT'S SO INSECURE
Attacks are possible (even relatively easy) because the Internet wasdesigned to be an open system that facilitates the free exchange of information,rather than a secure system that restricts such exchange. Not surprisingly,TCP/IP, the protocol suite that governs communications over both the Internetand increasingly popular intranets, is inherently insecure, as are mostof the services that run over TCP/IP networks, such as FTP services andthe Domain Naming System (DNS). (For information about vulnerable Internetservices, see "Weak Links.")
Consequently, if you need to use TCP/IP services and have an Internetor intranet connection, you need a firewall to protect your network. Ofcourse, if you have top secret information on your network (such as anythingpertaining to national defense), you don't need a firewall--you need a pairof wire cutters. Because no firewall can guarantee the absolute safety ofyour network under all possible circumstances, extremely sensitive informationshould not be connected to a TCP/IP network. However, for most commercialorganizations, implementing a firewall is as basic and necessary a steptoward protecting your network as locking the door is to protecting yourhome.
WHAT IS A FIREWALL?
Outside the computer industry, a firewall is a barrier that preventsa fire from spreading. Similarly, within this industry, a firewall is abarrier that prevents a figurative fire from reaching your network: A firewallthwarts hackers' attempts to access your network, preventing them from copying,changing, or destroying information or consuming bandwidth, memory, or processingpower.
This protective barrier is a collection of components (such as routersand gateways) configured to enforce a specific access control policy betweentwo networks--your network (a trusted network) and any other network (anuntrusted network). A firewall usually protects a trusted network againstthe Internet but can also protect against any other untrusted network, includinganother network on the same corporate intranet. A firewall sits betweena trusted network and an untrusted network, protecting information on thetrusted network by filtering incoming and outgoing packets--all of whichmust pass through the firewall--to ensure that only authorized packets pass.
Like all network security mechanisms, a firewall is based on a clearlydefined security policy, which describes, among other things, the type ofTCP/IP traffic your firewall should consider"authorized."Forexample, your company's network security policy should indicate whetheryou will restrict users' access to particular TCP/IP services and the extentto which you will limit access. The policy will help you decide which firewallcomponents you need and how to configure these components to create a barrierthat will maintain the restrictions you specify. (For more information aboutsecurity policies, see "The Security Catch 22")
CONVENIENT CATEGORIES--NOTHING MORE, NOTHING LESS
The level of protection firewalls provide and the way they offer thatprotection vary widely. However, broadly speaking, most commercially availablefirewalls fall into one of four categories:
Packet-filtering firewall
Circuit-level gateway
Application-level gateway
Stateful inspection firewall
Few firewalls belong in only one of these categories, and fewer stillexactly match the definition I will offer for any one category. Nevertheless,these definitions reflect the key capabilities that differentiate one firewallfrom another.
Packet-filtering Firewall
A packet-filtering firewall is a router or computer running softwarethat has been configured to screen incoming and outgoing packets. A packet-filteringfirewall accepts or denies packets based on information contained in thepackets' TCP and IP headers. For example, most packet-filtering firewallscan accept or deny a packet based on the packet's full association, whichconsists of the following:
Source address
Destination address
Application or protocol
Source port number
Destination port number
All routers (even those that are not configured to filter packets) routinelycheck the full association to determine where to send the packets they receive.However, a packet-filtering firewall goes one step further: Before forwardinga packet, the firewall compares the full association against a table containingrules that dictate whether the firewall should deny or permit packets topass.
A packet-filtering firewall scans these rules until it finds one thatagrees with the information in a packet's full association. If the firewallencounters a packet that does not meet one of the rules, the firewall willapply the default rule. A default rule should be explicitly defined in thefirewall's table and, for strict security, should instruct the firewallto drop a packet that meets none of the other rules.
Rules to Live By
You can define packet-filtering rules that indicatewhich packets should be accepted and which packets should be denied. Forexample, you could configure rules that instructed the firewall to droppackets from specific untrusted servers (generally calledhostsonthe Internet), which you would identify in the table by their IP addresses.You could also create a rule that permitted only incoming e-mail messagestraveling to your mail server and another rule that blocked incoming e-mailmessages from an untrusted host that had flooded your network with severalgigabytes of data in the past.
In addition, you can configure a packet-filtering firewall to screenpackets based on TCP and User Datagram Protocol (UDP) port numbers. Configuringa firewall in this way enables you to implement a rule that tells the firewallto permit particular types of connections (such as Telnet and FTP connections)only if they are traveling to appropriate trusted servers (such as the Telnetand FTP server, respectively). However, the success of such a rule dependson a TCP/IP network convention: Servers (and clients) generally run particularTCP/IP applications over particular ports (often referred to aswell-knownports), but servers are not required to use these ports.
For example, TCP/IP servers usually run Telnet over port 23. To restrictincoming Telnet sessions to a specific trusted server, you would first createa rule that told the firewall to permit all packets requesting destinationport 23 on destination address 123.45.6.7 (the IP address of your Telnetserver). You would then create another rule that told the firewall to denyall other incoming packets requesting destination port 23 on all other destinationaddresses.
Packet-filtering rules are more complex to create than these basic examples suggest. For a more complex example, refer to the configuration rules forCisco routers, which are posted on the Internet. (See the answer to number11 of the 20 most frequently asked questions [FAQs] about firewalls at ftp://ftp.greatcircle.com/pub/firewalls. For a list of other useful resources, see "Trusted Resources.")
Low Cost for Relatively Low Protection?
The primary advantage of using a packet-filtering firewall is that it provides some measure of protection for relatively low cost and causes little to no delay in networkperformance. If you already have an IP router with packet-filtering capabilities,setting up a packet-filtering firewall will cost no more than the time ittakes to create packet-filtering rules. Most IP routers, including thosemanufactured by Novell, Cisco Systems, and Bay Networks, can filter incomingand outgoing packets. (For more information about Novell's NetWare MultiProtocolRouter and other security mechanisms in IntranetWare, see "IntranetWare's Built-in Lines of Defense." Also, for information about upcomingsecurity solutions from Novell, see "Novell's New Security Services for the Internet)
Although the cost of a packet-filtering firewall is attractive, thisfirewall alone is often not secure enough to keep out hackers with morethan a passing interest in your network. Configuring packet-filtering rulescan be difficult, and even if you manage to create effective rules, a packet-filteringfirewall has inherent limitations. For example, suppose you created a rulethat instructed the firewall to drop incoming packets with unknown sourceaddresses. This rule would make it more difficult--but not impossible--fora hacker to access at least some trusted servers with IP addresses: Thehacker could simply substitute the actual source address on a maliciouspacket with the source address of a trusted client.
A packet-filtering firewall cannot differentiate between a forged sourceaddress and a real source address. If a packet has a valid source address,the firewall will let the packet pass, assuming that other information inthe packet's full association also meets a"permit"rule.
Address spoofing, as this form of attack is called, is common.In fact, during only a few weeks in the summer of 1995, the CERT CoordinationCenter received more than 170 reports of IP address spoofing attacks, manyof which resulted in successful break-ins.
Layer Upon Layer
In addition, a packet-filtering firewall primarilyoperates only at the network layer of the Open Systems Interconnection (OSI)model. (See Figure 1.) The OSI model, which wasdeveloped by the International Standards Organization (ISO), identifiesthe seven layers at which computers communicate, ranging from the physicalmedia over which they communicate to the applications they use to communicate.
Figure 1: A packet-filtering firewall examines network-layer data in every incoming and outgoing packet.
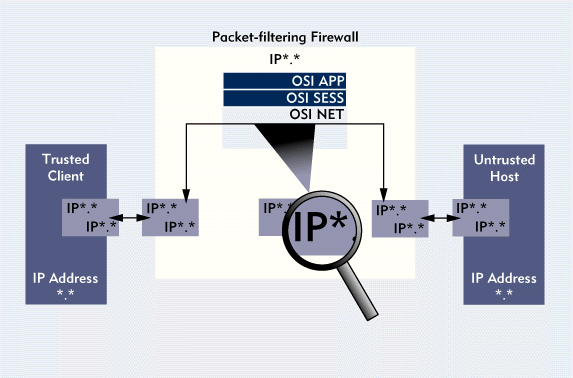
All firewalls rely on information generated by protocols that functionat various layers of the OSI model. Knowing the OSI layer at which a firewall operates is one of the keys tounderstanding different types of firewalls. Generally speaking, the higherthe OSI layer at which a firewall filters packets, the greater the levelof protection the firewall provides.
Because a packet-filtering firewall generally checks information onlyin IP packet headers, sneaking packets through this type of firewall isrelatively easy: A hacker simply creates packet headers that satisfy thefirewall's rules for permitting packets. Beyond that, a packet-filteringfirewall cannot detect the contents of a packet.
Circuit-level Gateway
A circuit-level gateway monitors TCP handshaking between packets fromtrusted clients or servers to untrusted hosts and vice versa to determinewhether a requested session is legitimate. (See Figure 3.) To filter packets in this way, a circuit-level gateway relies ondata contained in the packet headers for the Internet's TCP session-layerprotocol. Because a circuit-level gateway filters packets at the sessionlayer of the OSI model, this gateway operates two layers higher than a packet-filteringfirewall does.
Figure 3: A circuit-level gateway examines session-layer data in the initial packets exchanged between a trusted client and an untrusted host to verify that a requested session is legitimate.

Monitoring Handshaking--Circuitously
To determine whether a requestedsession is legitimate, a circuit-level gateway uses a process similar tothe following: A trusted client requests a service, and the gateway acceptsthis request, assuming that the client meets basic filtering criteria (suchas whether DNS can locate the client's IP address and associated name).
Next, acting on behalf of the client, the gateway opens a connectionto the requested untrusted host and then closely monitors the TCP handshakingthat follows. This handshaking involves an exchange of TCP packets thatare flagged SYN (synchronize) or ACK (acknowledge). These packet types arelegitimate only at certain points during the session.
The first packet of a TCP session is flagged SYN, indicating a requestto open a session. This packet contains a random initial sequence number.For example, the trusted client might transmit a SYN packet with 1000 asthe initial sequence number. (See Figure 4.)
Figure 4: A circuit-level gateway ensures that SYN and ACK packets are transmitted at legitimate times during TCP handshaking and verifies the numbers transmitted with the packets.

As Figure 4 illustrates, the return packetfrom the untrusted host is flagged ACK, acknowledging the receipt of theclient's SYN packet. The ACK packet contains a number that is next in thesequence established by the trusted client. In this example, the untrustedhost would transmit an ACK packet numbered 1001.
The untrusted host would also transmit a packet with an initial sequencenumber, such as SYN 2000, for its side of the connection. The trusted clientwould then transmit an ACK 2001 packet, acknowledging receipt of the untrustedhost's SYN packet and marking the end of the TCP handshaking.
A circuit-level gateway determines that a requested session is legitimateonly if the SYN flags, ACK flags, and sequence numbers involved in the TCPhandshaking between the trusted client and the untrusted host are logical.
Pipe Proxies
After a circuit-level gateway determines that thetrusted client and the untrusted host are authorized to participate in aTCP session and verifies the legitimacy of this session, the gateway establishesa connection. From this point on, the circuit-level gateway simply copiesand forwards packets back and forth without further filtering them.
The gateway maintains a table of established connections, allowing datato pass when session information matches an entry in the table. When thesession is completed, the gateway removes the associated entry in the tableand closes the circuit this session used.
A circuit-level gateway relies on special applications to perform copyand forward services. These applications are sometimes calledpipe(orgeneric)proxiesbecause they establish a virtual circuit,or pipe, between two networks and then allow packets (generated by one ormore types of TCP/IP applications) to pass through this pipe. (For a definitionofproxyand other terms related to firewalls, see "Firewall Lingo.")
Seldom Standalone
Because pipe proxies generally support severalTCP/IP services, a circuit-level gateway can extend the number of servicessupported by an application-level gateway, which relies on application-specificproxies. In fact, most circuit-level gateways are not stand-alone productsbut instead are packaged with application-level gateways such as TrustedInformation Systems, Inc.'s Gauntlet Internet Firewall; DEC's AltaVistaFirewall; and ANS, Inc.'s ANS Interlock. (For more information about theproducts mentioned in this article, see "Finding Out More.")
For example, DEC's AltaVista Firewall runs one application-specific proxyfor each of at least six common TCP/IP services, including FTP, HyperTextTransport Protocol (HTTP), and Telnet. In addition, the DEC firewall providesa circuit-level gateway to support other common TCP/IP services, includingGopher and Simple Mail Transfer Protocol (SMTP), for which the firewalldoes not run an application-specific proxy.
Proxy Server Protection
A circuit-level gateway provides oneother important security function: It is a proxy server. Although the termproxy serversuggests a server that runs proxies (which is true ofa circuit-level gateway), the term actually means something different. Aproxy server is a firewall that uses a process calledaddress translationto map all of your internal IP addresses to one"safe"IP address.This address is associated with the firewall from which all outgoing packetsoriginate.
As a result, on a network with a circuit-level gateway, all outgoingpackets appear to have originated from that gateway, preventing direct contactbetween the trusted network and the untrusted network. That is, a circuit-levelgateway's IP address is the only active IP address and the only IP addressthat the untrusted network is aware of. Thus, a circuit-level gateway andother proxy servers protect trusted networks from spoofing attacks.
Circumventing Circuits
A circuit-level gateway does have oneinherently vulnerable characteristic, however: Once a circuit-level gatewayestablishes a connection, any application can run across that connectionbecause a circuit-level gateway filters packets only at the session layerof the OSI model. In other words, a circuit-level gateway cannot examinethe application-level content of the packets it relays between a trustednetwork and an untrusted network.
Because a circuit-level gateway does not filter individual packets butblindly relays packets back and forth across established connections, ahacker on an untrusted network could possibly slip malicious packets pastthe gateway. The hacker could then deal directly with an internal server,such as a WWW server, which may not be as carefully monitored or configuredas the firewall itself.
As long as the initial TCP packets exchanged between the trusted WWWserver and the untrusted host met the handshaking criteria, the gatewaywould establish a connection and copy and forward subsequent packets--regardlessof their content. To filter the application-level content of individualpackets generated by particular services, you need an application-levelgateway.
Application-level Gateway
Like a circuit-level gateway, an application-level gateway interceptsincoming and outgoing packets, runs proxies that copy and forward informationacross the gateway, and functions as a proxy server, preventing any directconnection between a trusted server or client and an untrusted host. However,the proxies that an application-level gateway runs differ in two importantways from the pipe proxies that a circuit-level gateway uses:
The proxies are application specific.
The proxies can filter packets at the application layer of the OSI model.
Application-specific Proxies
Unlike pipe proxies, application-specificproxies accept only packets generated by services they are designed to copy,forward, and filter. For example, only a Telnet proxy can copy, forward,and filter Telnet traffic. If a network relies only on an application-levelgateway, incoming and outgoing packets cannot access services for whichthere is not a proxy. For example, if an application-level gateway ran FTPand Telnet proxies, only packets generated by these services could passthrough the firewall. All other services would be blocked.
Application-specific proxies tend to be sparse versions of their applicationcounterparts. For example, Trusted Information Systems' Gauntlet InternetFirewall supports incoming Internet mail with a proxy that has 700 linesof C source code. The proxy's counterpart, the Internet standard Sendmailapplication, has approximately 20,000 lines of code. More than 50 percentof the other proxies that Gauntlet Internet Firewall supports contain fewerthan 1,000 lines of code each. The premise behind using applications basedon minimal code is that small programs are easier to understand and manageand are, therefore, inherently more secure.
Application-level Filtering
Unlike a circuit-level gateway, anapplication-level gateway runs proxies that examine and filter individualpackets, rather than simply copying them and blindly forwarding them acrossthe gateway. Application-specific proxies check each packet that passesthrough the gateway, verifying the contents of the packet up through theapplication layer (which is the highest layer) of the OSI model. (See Figure 5.) These proxies can filter particular kindsof commands or information in the application protocols the proxies aredesigned to copy, forward, and filter.
Figure 5: An application-level gateway runs a proxy for each application the firewall must support, ensuring that no direct contact occurs between a trusted client and an untrusted host.

Raptor Systems, Inc.'s Eagle, ANS' ANS InterLock, and Secure ComputingCorporation's Sidewinder Security Server include application-specific proxiesfor FTP, HTTP, and Telnet. These gateways include utilities that enableyou to filter specific commands used by FTP, HTTP, and Telnet. For example,you can configure Raptor Systems' Eagle (and other application-level gateways) to prevent users from using the FTP Put command. This Put command enablesanyone who can access an FTP server to write to it. Many network administratorsprohibit use of the Put command to limit the risk of someone damaging informationstored on an FTP server or disabling the server altogether (by uploadinggigabytes of data to consume the server's memory and processing power, forexample).
An application-level gateway filters information at a higher OSI layerthan a packet-filtering firewall does and is usually easier to configure.For example, Raptor Systems' Eagle restricts the FTP Put and Get commandsby default, as well as restricting Telnet, Gopher, and HTTP services. Toenable these services, you would use Eagle's Hawk management utility, whichhas a graphical interface (as do the management utilities for most application-levelgateways). Using the Hawk utility, you would access the Rules by Destinationscreen and then select the services you wanted to enable.
Other Security Features
In addition to filtering packets, mostapplication-level gateways log activities and, more importantly, note significantevents through various means (such as using an auditory signal). For example,Secure Computing's BorderWare Firewall Server maintains logs that recordthe source and destination addresses of packets associated with attemptedor successful entries into your system, the time these attempts were made,and the protocol used. Milkyway Networks Corporation's Black Hole also logsall activities and alerts you of potential intruders via e-mail or pager.Likewise, both Secure Computing's Sidewinder Security Server and RaptorSystems' Eagle log firewall activity and alert you of potential intrudersvia e-mail or pager.
What's Out There?
Most application-level gateways run on UNIXoperating systems. Milkyway Networks' Black Hole is representative of alarge portion of the application-level gateways available: Black Hole requiresa scalable processor architecture (SPARC) processor running a Sun or Solarisoperating system.
Secure Computing's BorderWare Firewall Server and Trusted InformationSystems' Gauntlet Internet Firewall are exceptions to the UNIX-platformrule. Both gateways use proprietary operating systems and run on Pentium-basedPCs. Gauntlet Internet Firewall's operating system ships preinstalled onan Intel Pentium-based PC (although this gateway is also available on aSPARC-based workstation).
Global Internet's Centri Firewall and Raptor Systems' Eagle also runon a Sun or Solaris operating system as well as on Windows NT Server.
You can implement these application-level gateways on a TCP/IP-enabledNetWare network. To enable your IPX-based network for TCP/IP, you must installan IP-to-IPX gateway or install TCP/IP protocol stacks on each NetWare clientthat will use the application-level gateway. For example, you can installIntranetWare, which includes Novell's IPX/IP gateway, allowing you to easilyenable your network for TCP/IP. You can also use Novell's LAN WorkPlaceor LAN WorkGroup products to enable your network for TCP/IP.
Transparency--Ah, There's the Rub!
An application-level gatewayis one of the most secure firewalls available, but some vendors (usuallythose that market stateful inspection firewalls) and users claim that thesecurity an application-level gateway offers has a drawback--lack of transparency.Ideally, an application-level gateway would be as transparent as it is secure.Users on the trusted network would not notice that they were accessing Internetservices through a firewall. In reality, however, users often experiencedelays or must perform multiple logins before they are connected to theInternet or an intranet via an application-level gateway.
Although most vendors claim that application-level gateways are transparent,many vendors recommend that you configure the gateway to require user authenticationbefore users access an untrusted network, a process that foils true transparency.For example, you could configure Milkyway Networks' Black Hole to enableusers to access an untrusted network without having to log in to the gatewayat all. However, Milkyway Networks recommends that you configure Black Holeto require users to log in to the gateway either once during a predefinedperiod of time or once for each requested session.
Similarly, you can configure user access to Trusted Information Systems'Gauntlet Internet Firewall to be nontransparent or transparent. In nontransparentmode, a user connects to the gateway's proxy (for example, the Telnet proxy)and tells the proxy what host to connect to. After this initial interactionwith the proxy, the user sends and receives information as if there werea direct connection between the trusted client and the untrusted host. Intransparent mode, the user issues a command as if he or she were connectingdirectly to a remote host, but the gateway intercepts the request and establishesthe connection unobserved.
Other firewall vendors that market products as application-level gatewayshave tried to overcome the transparency problem. For example, CyberGuardCorporation and NEC Technologies, Inc. use a version of the SOCKS protocol(rather than application-specific proxies) to route TCP/IP services acrossCyberGuard Firewall and PrivateNet, respectively. SOCKS is a proposed InternetEngineering Task Force (IETF) standard that provides transparent authenticationservices for clients requesting connections to devices through firewalls.However, a SOCKS server is not transparent to network administrators: Youmust modify the applications running on each client that will use the firewall.
Also, although SOCKS includes other security features (such as private-keyand public-key encryption), it does not filter individual packets. Therefore,the products that rely on SOCKS might fall justifiably into the realm ofcircuit-level gateways rather than application-level gateways.
Stateful Inspection Firewall
A stateful inspection firewall combines aspects of a packet-filteringfirewall, a circuit-level gateway, and an application-level gateway. Likea packet-filtering firewall, a stateful inspection firewall operates atthe network layer of the OSI model, filtering all incoming and outgoingpackets based on source and destination IP addresses and port numbers.
A stateful inspection firewall also functions as a circuit-level gateway,determining whether the packets in a session are appropriate. For example,a stateful inspection firewall verifies that SYN and ACK flags and sequencenumbers are logical.
Finally, a stateful inspection firewall mimics an application-level gateway:The firewall evaluates the contents of each packet up through the applicationlayer and ensures that these contents match the rules in your company'snetwork security policy. (See Figure 6.)
Figure 6: A stateful inspection firewall examines application-layer data in incoming and outgoing packets. The firewall substitutes its own IP address for the source address on outgoing packets.
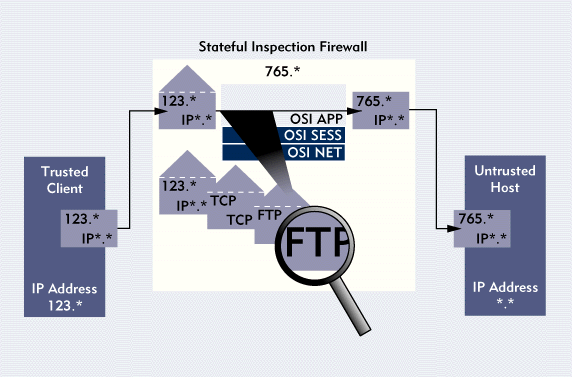
Better Performance, Same Level of Security?
Like an application-levelgateway, a stateful inspection firewall can be configured to drop packetsthat contain specific commands. For example, you could configure a statefulinspection firewall to drop FTP packets containing a Put or Get command.
Unlike an application-level gateway, however, a stateful inspection firewalldoes not break the client-server model to analyze application-layer data.An application-level gateway requires two connections: one connection betweenthe trusted client and the gateway and another connection between the gatewayand the untrusted host. The gateway then relays information between thetwo connections. Although some people insist that this configuration ensuresthe highest degree of security, other people argue that this configurationslows performance unnecessarily.
A stateful inspection firewall, on the other hand, does not require twoconnections, allowing a direct connection between a trusted client and anuntrusted host. To provide a secure connection, a stateful inspection firewallintercepts and examines each packet up through the application layer ofthe OSI model.
Rather than relying on application-specific proxies (and thus limitingusers to the services for which you are running a proxy), a stateful inspectionfirewall relies on algorithms to recognize and process application-layerdata. These algorithms compare packets against known bit patterns of authorizedpackets and are theoretically able to filter packets more efficiently thanapplication-specific proxies.
Because a stateful inspection firewall allows a direct connection betweena trusted client and an untrusted host, some people believe this firewallis less secure than an application-level gateway. However, other peopleargue that using a direct connection makes a stateful inspection firewallperform better than an application-level gateway at no cost to security.
What's Out There?
A stateful inspection firewall is a popularsolution for securing Internet and intranet connections because this firewallis transparent to users, scrutinizes data at the highest OSI layer, anddoes not require you to modify clients or run a separate proxy for eachservice that runs over the firewall. In fact, Check Point Software Technologies,Ltd.'s FireWall-1, which is one of the most popular commercial firewalls,is a stateful inspection firewall. Credited with coining the termstatefulinspection, Check Point began selling FireWall-1 in 1993 and now owns40 percent of the firewall market.
Another leading stateful inspection firewall is ON Technology's ON Guard.Designed specifically to protect NetWare 3.11, 3.12, and 4 networks, ONGuard runs on a standard, Intel-based 486 PC. Because ON Guard can filterboth IP and IPX packets, you can use ON Guard to protect your NetWare networkfrom Internet or intranet IP traffic and to protect some of your NetWareservers from internal, unauthorized IPX traffic.
One of ON Guard's strengths is Secure32OS, a 32-bit operating system.Because Secure32OS is proprietary, it is inherently more secure than a firewallthat relies on a general-purpose operating system, such as Windows NT orUNIX.
General-purpose operating systems are not specifically designed as firewallsand have millions of lines of code. Operating systems based on complex codeare more susceptible to bypass attacks, in which hackers get around thefirewall through a security hole in the operating system. As a result, hackersoften search operating system code for weaknesses.
ON Guard also offers common firewall features. For example, like application-leveland circuit-level gateways and other stateful inspection firewalls, ON Guardfunctions as a proxy server. As a result, ON Guard effectively protectsyour network from IP address spoofing attacks, random IP address scanning,and broken FTP chains, which allow hackers to spoof internal IP addressesand steal data when an FTP port is open. ON Guard also protects againstdenial-of-service attacks, in which repeated data requests overload a serverand render it inaccessible.
If hackers attack your network successfully, ON Guard will notify youof the attack. Like other stateful inspection firewalls, ON Guard monitorsfirewall transactions, maintaining a log and alerting you of suspiciousactivities (such as repeated high-speed FTP requests from multiple IP addresses).You can be alerted via e-mail, pager, or auditory alarm.
DON'T BE CARELESS
Stateful inspection firewalls are among the most secure firewalls availabletoday and"fooling them can be a lot of work,"according to JonMcCown, a network security analyst for the U.S. National Computer SecurityAgency (NCSA). Nevertheless, stateful inspection firewalls, like all firewalls,are not 100 percent effective. So why bother implementing a firewall atall? You should implement a firewall for the same reason you protect yourhome by locking your doors, despite the fact that this safety measure doesnot guarantee that an intruder cannot enter your house. Leaving an Internetor intranet connection without a firewall is a careless, open invitationto would-be intruders.
Linda Boyer works for Niche Associates, an agency that specializesin technical writing and editing.
Finding Out More
|
Company
|
Product
|
Product Type
|
Contact Information
|
|
ANS, Inc. |
ANS InterLock |
Application-level Gateway* Circuit-level Support |
1-800-456-8267 or 1-703-758-7700 http://www.ans.net |
|
Check Point Software Technologies, Ltd. |
FireWall-1 |
Stateful Inspection Firewall |
1-800-429-4391 or 1-415-562-0400 http://www.checkpoint.com |
|
CyberGuard Corporation |
CyberGuard Firewall |
Application-level Gateway |
1-800-666-4273, ext. 5615, or 1-954-977-5615 http://www.cyberguardcorp.com |
|
Digital Equipment Corporation (DEC) |
AltaVista Firewall |
Application-level Gateway |
1-800-336-7890 or 1-508-486-2308 http://altavista.software.digital.com |
|
Global Internet |
Centri Firewall |
Application-level Gateway |
1-800-682-5550 or 1-402-436-2171 http://www.globalinternet.com |
|
Milkyway Networks Corporation |
Black Hole |
Application-level Gateway |
1-800-206-0922 or 1-613-596-5549 http://www.milkyway.com |
|
NEC Technologies, Inc. |
PrivateNet |
Application-level Gateway |
1-800-NEC-INFO or 1-408-433-1549 http://www.privatenet.nec.com |
|
ON Technology |
ON Guard |
Stateful Inspection Firewall |
1-800-767-6683 or 1-617-374-1400 http://www.onguard.on.com |
|
Raptor Systems, Inc. |
Eagle |
Application-level Gateway |
1-800-9EAGLE6 or 1-617-487-7700 http://www.raptor.com |
|
Secure Computing Corporation |
BorderWare Firewall Server, Sidewinder Security Server |
Application-level Gateway |
1-800-334-8195 or 1-416-813-2000 http://www.sctc.com |
|
Trusted Information Systems, Inc. |
Gauntlet Internet Firewall |
Application-level Gateway |
1-888-FIREWALL or 1-301-527-9500 http://www.tis.com |
* All of the application-level gateways listed include circuit-level gateway support for several TCP/IP services not covered by the application-specific proxies.
Firewall Lingo
Like any niche market, the firewall market is laden with jargon. As you begin to investigate the firewalls that are currently available, you will probably encounter the terms defined below in most firewall literature and discussions:
APPLICATION-LEVEL GATEWAY
An application-level gateway ensures that a trusted client and an untrusted host have no direct contact. This gateway filters all incoming and outgoing packets at the application layer of the Open Systems Interconnection (OSI) model. An application-level gateway runs application-specific proxies that forward information generated by particular TCP/IP services through the gateway.
BASTION HOST
A bastion host is a gateway computer that runs firewall software and is situated between a trusted network and an untrusted network. Circuit-level gateways, application-level gateways, and stateful inspection firewalls are all bastion hosts.
CIRCUIT-LEVEL GATEWAY
A circuit-level gateway ensures that a trusted client and an untrusted host have no direct contact. A circuit-level gateway accepts a trusted client's requests for specific services and, after verifying the legitimacy of a requested session, establishes a connection with an untrusted host. After the connection is established, a circuit-level gateway copies packets back and forth--without further filtering them.
DEMILITARIZED ZONE
See Screened Subnet.
DUAL-HOMED GATEWAY
A dual-homed gateway is a computer that runs firewall software and has two network interface boards: One board is attached to an untrusted network, and the other board is attached to a trusted network. A dual-homed gateway relays information between the two networks and prevents any direct contact between them. Both circuit-level gateways and application-level gateways are dual-homed gateways.
FIREWALL
A firewall is a protective barrier built with a collection of components (such as a router and a gateway running firewall software) that are configured to enforce a specific access control policy between a trusted network and an untrusted network. All incoming and outgoing packets must pass through this barrier, which permits only authorized packets (as defined by the local network security policy) to pass.
HOST-BASED FIREWALL
A host-based firewall is a firewall system that includes a bastion host (a general-purpose computer running firewall software). A host-based firewall usually includes a circuit-level gateway, an application-level gateway, a hybrid of both gateways, or a stateful inspection firewall.
PACKET-FILTERING FIREWALL
A packet-filtering firewall is a router or a computer running software that has been configured to block certain types of incoming and outgoing packets. A packet-filtering firewall screens packets based on information contained in the packets' TCP and IP headers, including some or all of the following:
Source address
Destination address
Application or protocol
Source port number
Destination port number
PROXY
A proxy is an application running on a gateway that relays packets between a trusted client and an untrusted host. A proxy accepts requests from the trusted client for specific Internet services and then acts on behalf of this client (in other words, serves as proxy for this client) by establishing a connection for the requested service. The request appears to originate from the gateway running the proxy, rather than from the client. All application-level gateways use application-specific proxies (that is, modified versions of specific TCP/IP services). Most circuit-level gateways use pipe, or generic, proxies that offer the same forwarding service but support most TCP/IP services.
PROXY SERVER
A proxy server is a firewall that uses a process called address translation to map all trusted clients' IP addresses to the IP address associated with the firewall. Thus, the firewall's IP address functions as a proxy address.
ROUTER-BASED FIREWALL
A router-based firewall is a packet-filtering router. Not everyone in the industry agrees that a packet-filtering router alone is a firewall. Many people insist that only a system that includes a dual-homed gateway is a firewall. However, other people argue that a packet-filtering router is a firewall because the router meets important firewall criteria: The router is a computer through which incoming and outgoing packets must pass and through which only authorized packets can pass.
SCREENED DUAL-HOMED GATEWAY
A screened dual-homed gateway is a dual-homed gateway that is guarded by a packet-filtering router.
SCREENED SUBNET
Also referred to as the demilitarized zone, a screened subnet is a collection of computers that are shielded from both the trusted network and the untrusted network by packet-filtering routers and by gateways.
STATEFUL INSPECTION FIREWALL
A stateful inspection firewall examines the contents of individual packets at all layers of the OSI model, from the network layer to the application layer. To perform this task, this firewall relies on packet-filtering algorithms to examine and compare each packet against known bit patterns of authorized packets.
IntranetWare's Built-in Lines of Defense
IntranetWare is Novell's solution for companies that want to use the Internet and intranets to distribute and access information. IntranetWare includes NetWare 4.11, Novell Web Server, Netscape Navigator, NetWare MultiProtocol Router (MPR), and Novell's IPX/IP gateway. NetWare MPR and the IPX/IP gateway provide two lines of defense against unauthorized users who try to access your network via the TCP/IP-based Internet or your company's intranet. (For information about security solutions from Novell, see "Novell's New Security Services for the Internet.")
NETWARE MPR--A PACKET-FILTERING ROUTER
As a software-based router with packet-filtering capabilities, NetWare MPR provides the first line of defense for an IntranetWare network. Using the FILTCFG NetWare Loadable Module (NLM), a command-line utility that runs on a NetWare MPR server, you can configure NetWare MPR to filter both incoming and outgoing packets based on source and destination IP addresses and port numbers. You can also configure NetWare MPR to filter packets generated by FTP, HyperText Transfer Protocol (HTTP), or Telnet. For example, you could configure rules that would instruct NetWare MPR to drop all FTP packets except those traveling to a particular internal server.
INTRANETWARE'S IPX/IP GATEWAY--A NATURAL FIREWALL
The IPX/IP gateway provides the second line of defense for IntranetWare networks. The purpose of the IPX/IP gateway is to enable IPX clients to use Internet or intranet services without having to run TCP/IP. Instead, a WINSOCK.DLL file on each client wraps TCP packets in IPX (rather than IP). Before routing the packets to an untrusted host, the IPX/IP gateway strips the IPX headers from the packets and replaces these headers with IP headers.
From the viewpoint of the untrusted host, all packets appear to have originated from the gateway's IP address. By eliminating the need for an IP address on every workstation, the IPX/IP gateway can be the only IP address on the network--effectively shielding IntranetWare clients from the untrusted host.
Transparent Security
The WINSOCK.DLL file makes gateway operations transparent to users. Using Netscape Navigator, a user types in a host name such as www.novell.com. Netscape Navigator asks the WINSOCK.DLL to resolve the entered host name--for example, to find the IP address associated with the host name www.novell.com. The WINSOCK.DLL file passes the request to the IPX/IP gateway, which resolves the host name by contacting the Domain Naming System (DNS), a database that maps host names to IP addresses and vice versa. The user's workstation receives the IP address (such as 130.57.2.6) from the IPX/IP gateway and returns it to Netscape Navigator. Netscape Navigator, in turn, asks the WINSOCK.DLL file to open a connection to port number 80 (HTTP) at the host's IP address (for example, 130.57.2.6, the World-Wide Web [WWW] server at www.novell.com).
The WINSOCK.DLL file then opens a connection to the IPX/IP gateway and requests that the gateway open a connection to port 80 at the host's IP address (130.57.2.6 in this example). Next, the IPX/IP gateway establishes a connection to the untrusted host on behalf of the user's workstation. As the workstation exchanges information with the untrusted host, the gateway replaces the IPX packet headers with IP packet headers and vice versa.
Restricting Outgoing Traffic
The IPX/IP gateway also includes an access control mechanism. You can restrict outgoing packets based on the host (by way of the IP address) or based on the service (by way of the port number). To restrict packets based on the host, you would use the IPX/IP Gateway Host Restrictions page in the NetWare Administrator (NWADMIN) utility. To restrict packets based on the service, you would use the IPX/IP Gateway Service Restrictions page.
On an IntranetWare network, these pages are available for User, Group, Organization, and Organizational Unit objects. For example, you could use a Group object's IPX/IP Gateway Service Restrictions page to limit several users' access to a WWW browser (service HTTP on port 80) between 1 p.m. and 5 p.m. To verify the legitimacy of a trusted client's request, the IPX/IP gateway checks the NDS database before it opens a connection between the trusted client and an untrusted host.
IPX Attacks Remain Theoretical
IP-to-IPX gateways, including Novell's IPX/IP gateway, Quarterdeck Corporation's IWare Connect, and FTP Software's NOV*IX for Internet, are natural firewalls. That is, these gateways necessarily act on behalf of trusted clients requesting services on IP networks and thus shield trusted clients from untrusted hosts. Theoretically, a persistent hacker could find a way into and back out of these gateways, but no such attacks have yet been reported. According to Jon McCown, a network security analyst for the U.S. National Computer Security Association (NCSA), attacks on IPX clients by way of an IP-to-IPX gateway remain theoretical: "I haven't really heard anyone talking about forcing their way backward through an IP-to-IPX gateway," McCown says. However, don't get overly confident--where there's a will, there's a way.
Novell's New Security Services for the Internet
Novell is currently polishing firewall technologies for IntranetWare, including a circuit-level gateway and a HyperText Transport Protocol (HTTP) application proxy. Called IntranetWare Border Services, these technologies enhance both performance and security on IntranetWare networks. IntranetWare Border Services offers the following: proxy cache services, virtual private network (VPN) services, and security services.
Proxy cache services store frequently accessed Internet or intranet HyperText Markup Language (HTML) pages in a local area cache, delivering requested pages four to 10 times faster than they would be delivered without a proxy cache.
VPN services set up authenticated, encrypted tunnels over the Internet, ensuring that packets sent across these tunnels remain confidential. Thus, VPN services enable companies to run private networks securely over the Internet. VPN services use a proprietary encryption tunneling method based on a 40-bit implementation of RC2, a data encryption algorithm. (Novell will follow this release with a 128-bit implementation of RC2 for use within the U.S.) The RC2 encryption algorithm delivers reasonable performance for WAN lines up to T1 speeds and supports symmetric multiprocessing, enabling this algorithm to use multiprocessing hardware to increase encryption speed.
Security services include packet-filtering, circuit-level gateway, HTTP application proxy, and address translation technologies to protect your intranet from the Internet.
PACKET-FILTERING
With IntranetWare Border Services, you can filter and log the following packet information:
Source or destination host IP addresses to restrict access to and from particular Internet hosts
Source or destination IPX addresses to restrict access to and from particular network clients or servers
IP port number to restrict access to particular types of Internet protocols, such as FTP and HTTP
IPX protocol information to restrict access to particular types of NetWare Core Protocol (NCP) requests
CIRCUIT-LEVEL GATEWAY
IntranetWare Border Services also includes a circuit-level gateway that supports IP and IPX clients running appropriate gateway-enabled protocol stacks. This gateway first establishes a control channel with the client attempting to initiate a session with an untrusted host. The gateway then consults Novell Directory Services (NDS) to verify that the user requesting the session is authorized to do so. If the user is authorized, the gateway establishes a connection with the host, then copies and forwards the ensuing packets.
Because the circuit-level gateway consults NDS before establishing an Internet connection, you can use NDS to control users' Internet access rights, just as you use it to control their network access rights. Using the NetWare Administrator (NWADMIN) utility, you can restrict User and Group object rights to Internet sessions based on protocol (such as HTTP, FTP, and Telnet) and on host address or domain name. You can also specify the time during which you want these restrictions enforced. For example, you could specify that the Everyone group could not access the ESPN host between 8 a.m. and 5 p.m., thus restricting users within this group from accessing that host during business hours.
The circuit-level gateway maps the source addresses on outgoing packets it services to its own IP address, masking the addresses of the trusted clients or servers sending the packets.
HTTP PROXY
The HTTP proxy is an application-level gateway that filters HTTP packets. Like the circuit-level gateway, the HTTP proxy consults NDS before establishing a connection to verify whether a user is authorized to initiate the requested session. If the user is authorized, the HTTP proxy establishes a connection with the untrusted host and copies, forwards, and filters the ensuing packets.
The HTTP proxy maps the addresses on the outgoing packets it services to its own IP address, masking the addresses of the clients or servers sending those packets.
ADDRESS TRANSLATION
IntranetWare Border Services also provides network address translation for systems such as Macintosh or UNIX, which cannot run the gateway-enabled protocol stacks that the circuit-level gateway and HTTP proxy require. In addition, IntranetWare Border Services provides address translation for both IPX and IP packets. IPX address translation maps all IPX source addresses to a single IPX network, enabling you to form VPNs that include duplicate IPX addresses.
IP address translation is dynamic or static. Dynamic IP address translation maps all source addresses to one IP address, effectively masking the actual IP address associated with trusted clients or servers that access the Internet (without using the circuit-level gateway or HTTP proxy). Static IP address translation maps individual source addresses to fixed IP addresses and is commonly used to allow access from the Internet to resources on your intranet, such as World-Wide Web (WWW) and FTP servers.
To sneak a peak at IntranetWare Border Services, check out Novell's latest version of Early Access Release, which you can order from http://www.novell.com/intranetware/ear.
The Security Catch 22
The U.S. National Computer Security Association (NCSA) recommends that your company's network security policy in-clude a service access policy and a firewall design policy. Your service access policy should include a list of the Internet services to which you want to control users' access. This service access policy should also address restrictions on access methods such as Serial Line Internet Protocol (SLIP) and Point-to-Point Protocol (PPP) connections.
Addressing other access methods is important because if users cannot access the Internet services they want through your network connection, they will probably try to use another connection. For example, if you used a gateway to restrict access to the Internet and prevented users from browsing the World-Wide Web (WWW), users might create a dial-up PPP connection to access WWW services.
A service access policy is based on one of two principles:
Allow no access from the Internet to your network, but allow access from your network to the Internet.
Allow limited access from the Internet to your network, authorizing only selected systems such as mail servers.
A firewall design policy should define rules for implementing your company's service access policy. (For information about the NCSA's guidelines for firewall design policies, visit http://www. ncsa.com, and select the Firewall Policy Guide link.) Your company's firewall design policy should indicate how suspicious or trusting your company wants to be. In other words, your company's rules will fall either on or between one of two principles:
Deny everything except that which is explicitly permitted.
Permit everything except that which is explicitly denied.
Implementing rules based on the first principle creates a firewall that is unquestionably more secure than a firewall built by implementing rules based on the second principle. However, implementing rules based on the first principle could inconvenience your users and will certainly be more costly than implementing rules based on the second principle. Implementing rules based on the second principle creates a firewall that is somewhat vulnerable to attack but will probably be more user friendly and less costly.
Despite vendor claims to the contrary, when it comes to implementing network security of any kind--firewalls included--you face a catch 22: secure but costly and inconvenient, or insecure but inexpensive and convenient.
Trusted Resources
Setting up a firewall for your company can be a complex undertaking. For more information about firewalls, check out the following resources:
FTP://INFO.CERT.ORG OR HTTP://WWW.CERT.ORG
The /pub/cert_advisories directory contains a list of CERT advisories, which are documents that provide information about how to work around known security problems. CERT advisories might also warn you of ongoing attacks.
The /pub/cert_summaries directory contains a list of past CERT summaries, which are documents that point out the types of attacks that have been reported.
HTTP://WWW.NCSA.COM
The U.S. National Computer Security Association (NCSA) site contains the NCSA Firewall Policy Guide. This site also offers a list of NCSA-certified firewalls and includes links to other World-Wide Web (WWW) sites that contain more information about these firewalls. The NCSA tests products to determine whether they provide reasonable business functions while protecting against a standardized suite of attacks. Certified products include Check Point Software Technologies, Ltd.'s FireWall-1; ON Technology's ON Guard; and Trusted Information Systems, Inc.'s Gauntlet Internet Firewall.
Outlink is a research firm that specializes in information security and publishes The Firewall Report, which helps you stay abreast of the firewall products and services that are available.
The Firewall Report is a collection of Internet and intranet firewall Product Profiles and Supplier Profiles. Covering 20 market-leading firewalls, these profiles offer unbiased, technical explanations of each product and the supplier responsible for the product's development and after-market support.
You can download samples of the Product Profiles and Supplier Profiles, which are ZIP PostScript files, from the Outlink home page.
HTTP://WWW.TELSTRA.COM.AU/PUB/DOCS/SECURITY
This site contains links to papers that industry-recognized security experts have written about Internet security.
FTP://FTP.GREATCIRCLE.COM/PUB/FIREWALLS
This Internet site features answers to frequently asked questions (FAQs) about firewalls. This site also contains links to information about books and papers that focus on firewalls.
The U.S. National Institute of Standards and Technology's Computer Security Resource Clearinghouse contains dozens of links to security-related sites.
FIREWALLS AND INTERNET SECURITY: REPELLING THE WILY HACKER
Although this book is slightly dated (published in 1994), it provides a good introduction to common Internet security holes and explains how to build a firewall. The authors, Cheswick and Bellovin, are senior researchers at AT&T Bell Laboratories and are recognized as experts on the subject of firewalls. (This book was published by Addison-Wesley, ISDN 0-201-63357-4.)
Weak Links
Security problems are inherent to virtually all common Internet protocols and services.
DOMAIN NAMING SYSTEM
Domain Naming System (DNS) is a distributed database that maps usernames and host names to IP addresses and vice versa. For example, DNS could map a host name such as iago.nds. research.novell.com to the IP address 183.10.335.3.
DNS also stores information about your company's structure, including how many computers with IP addresses are in each domain. One of the problems inherent in DNS is that it is difficult to hide the DNS database from unauthorized users. As a result, DNS is an obvious place for hackers to search for trusted host names.
FTP
Because FTP supports the transmission and character set translation of text and binary files, it is widely used on the Internet to share files. FTP servers store documents, programs, graphics, sounds, and other kinds of archived data.
Some FTP sites restrict access to authorized users with passwords, but many sites provide public access to their archives through the anonymous FTP option. You should not use the anonymous FTP option to grant a specific group of people access to your FTP server. If you use the anonymous FTP option, you should ensure that all of the files on your FTP server are public files and can be shared with everyone connected to the Internet.
SENDMAIL
Sendmail is a common e-mail program. With approximately 20,000 lines of code, Sendmail is complex and, therefore, vulnerable to hackers. Also, Sendmail exposes network information, such as the sender's network IP address, which hackers can use in address spoofing attacks to sneak past a packet-filtering firewall.
SIMPLE MAIL TRANSFER PROTOCOL
Simple Mail Transfer Protocol (SMTP) is the Internet's e-mail transport service. One security problem with SMTP is that you cannot verify the Mail From address in the headers of e-mail messages. As a result, hackers can send a large number of e-mail messages to your network, potentially overloading your mail server.
TELNET
Telnet is an Internet service that generally requires users to log in to a Telnet server to initialize and authenticate a session. With Telnet, users' workstations act as dumb terminals on the untrusted host, so these users can enter commands that will let them access files and run programs.
When users log in to a Telnet server, they usually type an account name and password. Hackers can log Telnet sessions and possibly configure the Telnet program to record username and password combinations.
TCP/IP
TCP/IP is a protocol suite used to route packets between computers on the Internet and intranets. TCP/IP's security problem stems from the information in its packet headers, which hackers can subvert. For example, a hacker could forge source address information on malicious packets, so they appeared to originate from a trusted client.
WORLD-WIDE WEB
The World-Wide Web (WWW) is an application that enables users to browse the Internet or intranets for information. The most useful tool on the WWW is also its weakest feature: Hypertext is a tool that cross-indexes WWW sites, allowing users to easily move from one site to another. To cross-reference these sites, hypertext links must include information about how to access other systems. Using this information, hackers can corrupt your WWW site or access restricted files that are stored on your WWW server.
* Originally published in Novell Connection Magazine
Disclaimer
The origin of this information may be internal or external to Novell. While Novell makes all reasonable efforts to verify this information, Novell does not make explicit or implied claims to its validity.