BorderManager: Managing Virtual "Borders" Between Corporate Networks and the Internet
Articles and Tips: article
01 Jul 1997
Shows how BorderManager works with existing products to deliver enhanced security, single point-of-management capability, managed access to Internet resources, enhanced performance, and reduced cost.
- Introduction
- The Intranet/Internet Performance Gap
- Business Models as Different as Night and Day
- Providing an Integrated Solution
- Support for Open Standards
- Maintaining Intranet Security
- Accelerating Performance
- Enabling Implementation of Virtual Private Networks
- Managing and Administering with Ease
- Supporting Existing Infrastructures
- Novell BorderManager
- Securing Your Intranet's Internet Connection
- The IntranetWare Platform
- Conclusion
Introduction
Businesses in every industry and in every country are turning their corporate networks into Internet-enabled intranets to help them compete. Corporate networks that incorporate Web and other Internet technologies-intranets-can put the Internet's vast resources at employees' fingertips. Using the Internet as a backbone for intranets can provide competitive advantages such as closer contact with remote employees, customers, and vendors-reliably and economically.
The term "border services" is a category describing the boundary area between the corporate network and the Internet. Novell is delivering the security, management, high performance, and easy access needed to extend corporate networks or intranets to the Internet by introducing a unique suite of open technologies and services. This suite of open services includes proxy, cache, circuit gateways, Virtual Private Network (VPN) technology, routing, and remote access.
Novell's offering represents a unique combination of open technologies and services. Shipping as a stand-alone software solution, Novell BorderManager works in concert with existing networking products-including Novell and non-Novell technologies-to deliver:
Enhanced security with single-point-of-management capability
Managed access to Internet resources
Enhanced networking performance
Reduced network operating cost
In a nutshell, Novell BorderManager helps businesses take advantage of the Internet without compromising the security, management, reliability, and performance they've come to expect from their corporate network.
Businesses are moving to intranets to better manage user bandwidth, improve the quality of available information, and accelerate information delivery. And they need to do all this while managing computing resources, network and Internet access, and associated costs. When an organization connects to the Internet, it risks exposing confidential internal information to millions of people beyond the enterprise network's "border."
Because corporate networks have management tools and security mechanisms to protect sensitive information and the Internet doesn't, connectivity issues need to be taken seriously and incorporated in a business' planning process. Only then can an Internet- connected intranet be considered a safe business resource. This article outlines key issues surrounding intranets-including security, implementation, and performance-and discusses technologies that can enhance security while boosting performance and reducing overall network costs.
The Intranet/Internet Performance Gap
Technical discrepancies between corporate intranets and the Internet are slowing many organizations' drive to connect. From a user perspective, there is a noticeable performance slowdown and quality degradation in accessing the Internet when compared with a corporate intranet. Internal LANs, for example, have bandwidths ranging from 10 to 100 megabits per second.
The bandwidth of Internet access links, on the other hand, generally ranges from 14.4 kilobits per second to 1.5 megabits per second. Aggravating this performance gap is the fact that both the number and size of files on the World Wide Web are growing rapidly-fueled by the increasing use of graphics and streaming audio and video.
Since corporations need robust Internet access to stay competitive, most IT vendors are offering products for implementation at the level of Web browsers and servers. But this isn='t the end of the story. While Internet access through departmental Web servers or user PCs is a relatively easy first step, solid productivity, security tools, and administrative tools for Web-enabled networks can and should reside at the connection between the intranet and the Internet.
Security Isn't an Issue, It's the Issue
In a recent survey of businesses, 42 percent of the companies surveyed experienced unauthorized use of their computer systems in the previous 12 months. Only 37 percent reported no unauthorized use, and 21 percent of those surveyed didn't know if their systems had been breached or not. Less than 17 percent of respondents who experienced computer intrusions reported them to law enforcement.
Figure 1: Computer Security Issues.
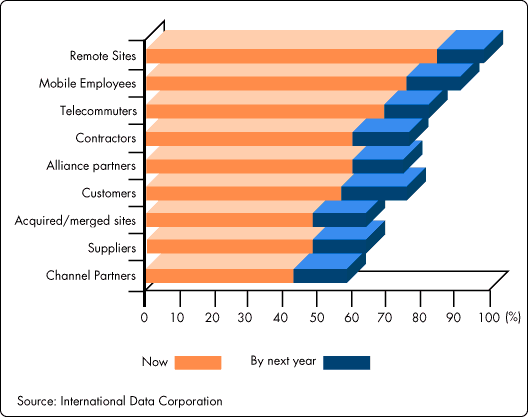
Source: Computer Security Institute's 1996 CSI/FBI Computer Crime and Security Survey
The Internet community, with its freewheeling, no-holds-barred approach, threatens at times to undo all the progress that's been made in network communications. The Internet is a technological wonder, to be sure. With no manageability in sight for overall performance, however, the Internet is also a gaping security breach waiting to happen to corporate intranets. Vandals are poised at the gate to steal business-critical data or send viruses tearing through organizations. On the other side-your side-employees are chatting, surfing, buying stock, and (hopefully) doing some work.
Thousands of companies are rushing to use the Internet for a simple reason-it has millions and millions of users. Of course, that's the same reason the Internet is far less secure than nearly any private network. Productivity is on the rise at many companies that have Internet-enabled their networks.
Web browsers and servers provide quick, easy, near-universal access to information for users and groups; those same software tools also raise potential security problems. With thousands of widely available Web tools, technologies, and information available to friends (vendors and partners) and foes (hackers) alike, there will always be someone out there knocking (or hacking) at your electronic door.
Business Models as Different as Night and Day
The Internet is based on a model of free speech, unlimited access, and no charge for usage. Corporate intranet business models differ significantly, with imperatives such as secure, controllable global access and charges levied for specific services. This mismatch between corporate networks and the Internet is becoming obvious as the Internet moves from its academic and research paradigm to a business and commercial paradigm.
Connectivity requirements for organizations dictate that an Internet access solution reconcile Internet/intranet disparities in security, management tools, and business models. To be effective, this connectivity solution must:
Provide an integrated intranet security and management solution
Maintain tight, manageable security
Be easy to manage and administer
Improve user productivity with quicker access to more information
Support existing infrastructures
Allow the implementation of virtual private networks (VPNs)
Support open standards
Accelerate performance
Providing an Integrated Solution
An integrated Internet access solution is easier to implement and far easier to use and manage than the alternative. What's more, integrated services at the border are inherently more secure than an integrated mixture of vendor solutions resident on network operating systems, in client PCs, or on network Web servers. Placing connection services at the intranet-to-Internet border yields several critical advantages. It lets organizations:
Monitor and manage both inbound and outbound access
Manage both intranet and Internet resources as effectively as conventional LAN services
Increase the reach of network management utilities to include heterogeneous, multivendor browsers and Web servers
Implement performance accelerators at the border to reconcile performance mismatches
Support for Open Standards
Implementing an intranet requires an integrated solution that supports open standards for easy integration between the corporate intranet and the Internet. Open standards support allows organizations to combine best-of-breed technology in all areas, including protocol stacks, Web browsers, and Web servers.
Maintaining Intranet Security
An Internet access solution must provide flawless security in two directions-inbound and outbound. Inbound security protects the intranet from unauthorized access by people on the Internet. Outbound security manages and focuses access to Internet resources by internal users.
The overall solution must implement a standard Internet firewall security architecture, which defines a three-tiered model comprising packet filters, circuit-level proxies, and application-level proxies.
Packet filters use routers to filter information coming to and from a network, checking each packet against access controls and blocking packets from unknown sources.
Circuit-level proxies provide a general virtual circuit relay between the Internet and intranet desktop applications. (Unlike application-level proxies, circuit-level proxies provide access control at the session layer.)
Application-level proxies, similar to circuit-level proxies, relay all data between the Internet and intranet desktop applications. (Application-level proxies intercept all traffic and apply content-based semantic access controls prior to relaying the data.)
For maximum effectiveness, the security system should provide multiple levels of access control, including:
Host control, to determine which hosts can be accessed
Application-level control, to determine which applications can be accessed (For example, allowing users access to World Wide Web and FTP applications, but denying access to news group applications.)
Content control, to allow control over which network files and documents are accessed (Content control is the finest degree of granularity.)
In addition, the administrator needs to be able to tailor each of these levels to specific users and user groups.
Security should also provide authentication services in which different levels of authorization are granted, depending upon the user's entry location-such as a local workstation, the Internet, or a dial-in connection. Authentication should support leading authentication standards for virtual networks and electronic commerce. These standards include Point-to-Point Tunneling Protocol (PPTP) to provide security for remote users accessing intranet resources from a serial connection to the Internet.
In addition to multiple-level access control and authentication, the security system should provide end-to-end information encryption. This requirement is particularly important for virtual private networks (VPNs) and online transactions. The encryption mechanism should support leading encryption standards, such as IP SEC, for virtual networks and electronic commerce.
Security for an intranet-to-Internet connection needs to be flexible and easily adaptable to organizational security policies. An administrator should be able to manage security from a central location to reduce the risk of holes in the security screen. In addition, the administrator should be able to configure security only once for the entire network, with all systems used to implement security sharing a common configuration. Finally, security should protect the network from viruses, hostile applications, worms, and logic bombs on incoming files.
Accelerating Performance
Due to the increasing use of images and other large files, such as video and audio streams, Internet traffic is growing at a rapid pace, slowing overall Internet performance. It is essential for an intranet-to-Internet connectivity solution to use state-of-the art acceleration technology to offset performance disparities between intranets and the Internet.
Proxy caching moves frequently accessed Internet information, such as Web pages, from the Internet to the "border" between the corporate intranet and the Internet, bringing the information closer to the users who need it. This approach minimizes traffic on the Internet and the primary Web server and reduces the number of node-to-node hops between users and data.
Adding more intelligence to proxy caching can further reduce delays. For example, a hierarchical caching system in which each cache knows the content of all other caches can direct the client to the nearest cache where the data is stored if the needed data isn't in the local cache or if it is a first-time access.
Multiple-level access control is another factor that improves performance by eliminating traffic due to the use of unauthorized or unessential applications, or traffic due to users surfing to nonproductive Web sites.
Enabling Implementation of Virtual Private Networks
Implementing a dedicated network connection between branches, from one company to a supplier or customer, or for telecommuting, ensures secure, private networking-but it's expensive. VPNs, on the other hand, establish secure, encrypted connections across low-cost public Internet links. And, VPNs established with border software don't need custom desktop or laptop software for mobile or remote users. To allow flexible and secure VPNs, an intranet solution must do all of the following:
Allow configuration of multiple VPNs on a single enterprise network
Ensure administrative control over who participates in each VPN
Enable sending secure data over the public network
Prevent unauthorized users from breaking into the intranet by hiding the intranet's topology from non-VPN users
Managing and Administering with Ease
The ability to create VPNs is a strong economic benefit of intranets, allowing organizations to use the Internet as a backbone for enterprise networks. However, expanding enterprise networks into WANs that include the Internet can dramatically increase network complexity and complicate network management. An effective intranet-to-Internet solution lets administrators manage VPNs from a central location with the same ease with which they manage LANs.
Supporting Existing Infrastructures
Organizations have significant investments in current information systems and networks. It is imperative that a border solution leverages existing IT investments by accommodating:
Popular desktop operating systems, including DOS/Windows, Windows 95, Windows NT Workstation, Macintosh System 7, UNIX and network computer workstations
Popular NOSs, including IntranetWare, Windows NT Server and UNIX
Popular network transport protocols, including TCP/IP and IPX/SPX
Widely used Web browsers, including Netscape Navigator and MS Explorer
Existing applications and scripts, including WinSock, CGI, PERL and Visual Basic
In addition, the connectivity solution between the intranet and the Internet should let administrators gather information, such as user IDs, resources, break-in attempts, security holes, data accessed, performance bottlenecks, and under-utilized resources-all from a central location--using this information to tune and optimize the network.
Novell BorderManager
Novell software services at the border between intranets and the Internet let organizations connect their intranets to the Internet in an integrated, flexible, and secure manner while boosting performance and productivity. Because Novell BorderManager is a natural extension of IntranetWare, the software is an ideal solution for networks small or large. These services add three components:
Security services to leverage Novell Directory Service (NDS) filtering, circuit gateway and proxy server technologies to provide firewall-class security
Intelligent proxy caching to accelerate performance of Internet operations and optimize use of WAN bandwidth
Virtual private networks to allow organizations to use the Internet as an economical medium in implementing WANs
Figure 2: Novell software for border services provides a complete, integrated solution for intranet-to-Internet connection security, manageability, and performance.
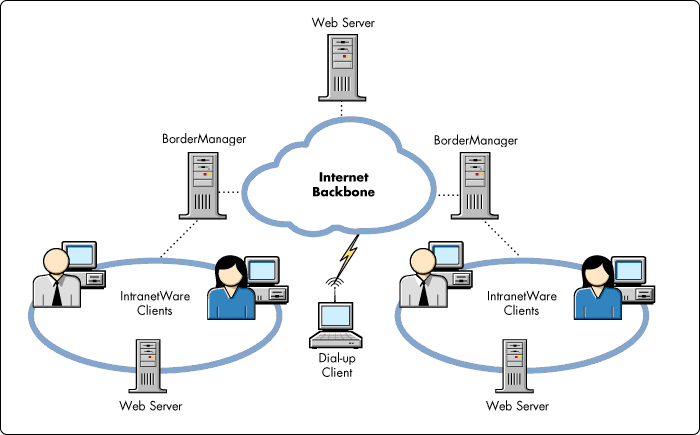
Novell software for services at the intranet-to-Internet border includes a runtime version of IntranetWare as the server operating system. The software integrates with NDS to provide a single point of administration for the border area across the entire enterprise.
Securing Your Intranet's Internet Connection
If your business uses the Internet, a firewall is absolutely essential. But you really need much more than a simple firewall. Novell software secures and manages the border where the corporate intranet meets the Internet. Novell BorderManager lets IT management manage access to information at key network check points. The organization can set policies to manage or limit access to approved business purposes only, with gateway filtering of all network traffic, whether inbound or outbound. Novell software enables the following:
Access to Internet services from the intranet--Employees increasingly need to access the Internet as more and more information and services are added to it. People conducting market research, for example, must be able to access and use the World Wide Web. However, for both legal and productivity reasons, organizations need the ability to manage this access.
Access to intranets from remote locations--Employees need to access and share information and services like E-mail on the corporate intranet; many employees need to access the intranet from remote locations. Remote users include employees who travel or workgroups that are widely dispersed. In addition, customers, business partners, and outside contractors often need to access corporate information and services on the intranet.
Links to geographically dispersed sites--Novell software allows organizations to combine sites into virtual private networks running on top of existing enterprise networks. These VPNs combine the corporate intranet and the Internet, letting organizations serve multiple constituencies, both external and internal, over the same network. An added value is that each constituency sees only the VPN it is authorized to use. Also, VPNs allow organizations to "push" data over the Internet closer to users for faster access, which increases user productivity and reduces network traffic.
The IntranetWare Platform
IntranetWare continues the evolution of NetWare into a full-service intranet and Internet- access platform. This modern platform builds on the distributed services of NetWare 4.11, integrating intranet and Internet technologies to deliver a comprehensive network solution.
Today's IntranetWare solution includes:
A high-performance Web server
The Netscape Navigator Web browser
A gateway between industry-standard TCP/IP and IPX networking protocols
A multiprotocol router for wide area network and Internet connections
Industry-leading performance with fast protocol stacks and a file system that operates at the kernel level for maximum speed.
Security is paramount when organizations connect their private networks to the Internet. Novell software services at the border will deliver two major security capabilities:
Access control from the Internet to the intranet--Potential intruders from the Internet will not be able to penetrate the intranet. Approved users, however, will have managed access to intranet resources from the Internet.
Monitor and manage Internet access by users on the intranet-The types of Internet services users can access can be managed to meet corporate policy or legal requirements.
Novell software for services at the border operates on multiple levels: the packet level, the circuit level, and as an application proxy. At each level, the software provides a combination of services, including address translation, authentication, and filtering. With these capabilities, Novell provides enhanced firewall-class security for all platforms in your network.
Address Translation
With Novell software at the border, all users share a common IP address, which enhances security by hiding intranet addresses from Internet-based intruders. In addition, the address-translation capability of the gateway creates proper external addressing, even resolving duplicate network addresses when necessary. This simplifies network administration by allowing administrators to set up internal network addresses as required, without worrying about external addressing.
Figure 3: Novell BorderManager provides multiple levels of security.
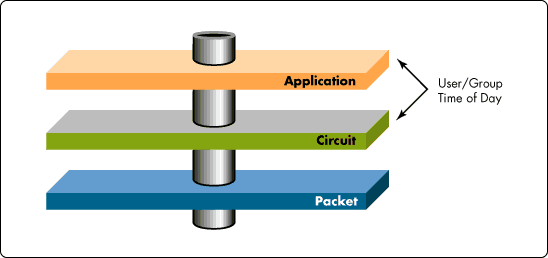
Packet Filtering
Novell software provides packet-level filtering and optional logging of the following information:
Source or destination host IP addresses to restrict access to or from IP hosts
Source or destination IPX addresses to restrict access to or from IPX hosts
IP protocols/port to restrict access to HTTP, FTP, Gopher, etc.
IPX protocol to restrict access to certain types of NetWare Core Protocol (NCP) requests
Packet-level functionality includes both dynamic and static IP network address translation. Dynamic IP network address translation maps all source addresses to a single IP address. Static IP translation maps individual source addresses to fixed IP addresses and is commonly used for accessing resources outside the border server, such as a Web server or FTP site.
Circuit-Level Proxy
The Novell circuit gateway supports IP and IPX clients with appropriate gateway-enabled protocol stacks. The software establishes a control channel between the client and the gateway in which the gateway authenticates the user to the directory using NDS authentication. NDS authentication makes users of the circuit gateway and proxy server identifiable and allows control of access by users or user groups.
Circuit gateway filtering further leverages NDS by allowing the security administrator to define access control rules once for the entire network, independent of the number of circuit gateways deployed in the network. From that point on, all access will be through the IntranetWare gateway. All sessions connected through the circuit gateway use the common circuit gateway address, masking the original IP address of the requestor.
Authentication
The circuit gateway authentication capability of Novell software services at the border lets organizations manage and focus access by all users or user groups. The gateway establishes a control channel between the client and the gateway, which authenticates users to NDS and makes them identifiable to the border services software.
Access Control
NDS provides common access control to all intranet and Internet resources and services, allowing circuit gateways and HTTP application proxy servers to share authentication and access control services. Common access control simplifies access by permitting users to gain access to all network services through a single login.
Because the Novell software at the border can determine who a user is through NDS, it can apply access control to individual users and groups. The software grants access to non-authenticated users based on global access restrictions, and grants access to authenticated users based on their inherited NDS rights.
HTTP Application-Level Proxy
The HTTP application proxy provides access control when URL requests are made from browsers that have CERN proxy support. The HTTP application proxy shares access control information with the circuit gateway. Users are allowed access to URLs based on their inherited NDS rights. Non-authenticated users are allowed access to HTTP, FTP, and Gopher URLs based on global access restrictions.
The HTTP application proxy server also supports Secure Sockets Layer (SSL) tunneling, allowing an encrypted path between the client and server. All requests passed through the proxy use the common proxy address, masking the original IP address of the requestor.
Proxy Caching Services
Novell delivers dramatically increased performance and improved WAN bandwidth for Web server access through advanced proxy caching technology. Preliminary benchmarks indicate that advanced Novell proxy caching technology delivers from 4 to 10 times the performance and scalability of competitive proxy caches built on general-purpose operating systems.
Novell's proxy cache server implements high-performance caching for Web browsers, copying frequently used information on a local server. Proxy caches can be applied to geographically dispersed internal Web sites or to World Wide Web sites. By caching data on a LAN-based proxy server, IntranetWare reduces requests across the WANCtypically by more than 60 percent. Organizations can realize two and a half times as much throughput over the same physical WAN connection without purchasing expensive, higher-bandwidth WAN connections.
Intelligent Caching to Improve Performance
Novell proxy caching is based on next-generation Harvest/Squid proxy cache research to deliver superior functionality in an open standards environment. Novell intelligent proxy caching enhances performance significantly by using proxy cache hierarchies. Hierarchical proxy caching increases performance dramatically because this approach allows first-time access and cache-miss data to be fetched from the optimal nearby border server without going all the way to the source Internet Web server. Intelligent proxy caching also improves first-page caching performance by detecting and pre-fetching online images and documents, even before the browser requests them.
Novell proxy cache software provides negative caching of Web pages that cannot be located. The proxy cache service intercepts and responds to requests for Web pages that are negatively cached to off-load network and Web server use. Novell also provides reverse proxy cache acceleration (sometimes referred to as HTTPD acceleration), which allows content publishers to push information from their Web servers out to border servers to reduce loading on their Web servers.
Proxy Cache Tuning
Administrators can tune and optimize Novell proxy cache performance and network bandwidth access based on:
Total disk and RAM available
Least recently used (LRU) pages
HTML page/file size
Time to live (TTL) tags
Cost to retrieve the page (hops/link costs)
Virtual Private Network (VPN) Services
Novell VPN services let users run private networks securely over the Internet, providing a wide range of WAN connectivity options, including Point-to-Point Protocol (PPP) over leased lines, Integrated Services Digital Network (ISDN) lines, analog dial-up lines, as well as frame relay and X.25. VPNs typically use tunneling to accomplish connection between sites. The tunnel appears to IP and IPX stacks as a point-to-point WAN medium, which makes the entire public network infrastructure appear as a single point-to-point link to a VPN, simplifying connection.
Figure 4: Tunneling provides a secure link between locations.
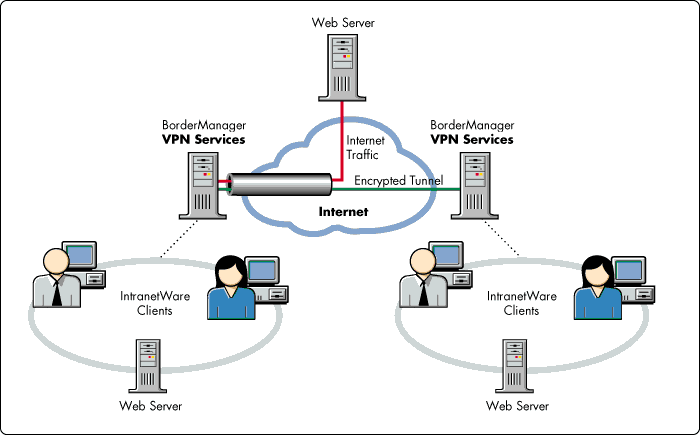
Novell tunneling takes advantage of maintenance traffic-reduction techniques, such as header compression and efficient WAN routing updates, to deliver high bandwidth for applications over the VPN. Tunneling also allows VPN sites to share address and routing information without exposing information to the public network. Also, tunneling allows the use of multiprotocol traffic over a single-protocol network like the Internet. For example, an organization can use both IP and IPX over the Internet--even though the Internet itself supports only IP traffic.
Novell employs the RC2 encryption algorithm because the software implementation of this algorithm delivers performance for WAN lines up to T1 speeds. RC2 implementation also supports symmetric multiprocessing (SMP), allowing it to take advantage of multiprocessing hardware to increase encryption speed.
Remote Access
Novell uses the Point-to-Point Tunneling Protocol (PPTP) for authenticating remote clients accessing a site from the Internet. This method allows multiprotocol access using an IP tunnel in either of two ways: they can use PPTP-enabled clients configured to establish tunnels with intranet servers, or remote users with standard PPP dialers on their computers can dial into an Internet service provider (ISP) that supports PPTP.
Key Management
In the absence of key management standards to distribute encryption keys between sites, Novell VPN technology employs a master/slave relationship to simplify key management. In setting up a VPN, the administrator manually transmits the public key from each slave site to the master site. At the same time, the master automatically distributes its authentication key to each of the slave sites. The master then distributes all the authentication keys it has received to all the slave sites automatically, signing each message using its authentication key. This allows the slave sites to validate messages from the master site.
Centralized Administration
Novell BorderManager installs easily, providing a simple migration path for IntranetWare servers and clients. The administrator can upgrade IntranetWare servers to include border services through the IntranetWare upgrade install capability. And, using NWAdmin or any SNMP-enabled console, administrators can easily manage Novell software for border services using NDS from a central location in the same manner as other IntranetWare components.
The console presents all border services to the administrator as a consolidated and unified facility, ensuring easy and secure management. To simplify management even further, all Novell border servers share a single set of access control rules from NDS. As a result, control rules are the same regardless of the border servers that users traverse. This means even dial-in, remote access authorization for PPTP is seamlessly integrated with NDS and your intranet.
Transaction Logging
Administrators can view and report incoming and outgoing requests and transactions in both common and extended formats. Through transaction logs, administrators can quickly identify security attacks, resource over- and under-use, misuse of network resources, and trends to plan and optimize resource and security deployment across the enterprise.
Simple Browser Configuration
To take advantage of Novell software for border services, users simply point their browsers at the IntranetWare proxy server. Once this is done, the browser automatically directs all requests through the proxy server. And, users only have to perform this simple procedure once.
Conclusion
Novell is well positioned to provide a border solution as the developer of NetWare and IntranetWare-the world's most popular intranet solution. The NetWare platform has long been the network of choice, with more than 60 million users worldwide-65 percent of the world's installed base. That's more than three times the installed base of UNIX, Novell's nearest competitor, and it's more than 10 times the installed base of Windows NT Server.
Using IntranetWare to securely connect intranets to the Internet, organizations can position themselves to take advantage of the Internet's nearly universal reach and rapidly growing wealth of information and services. Large organizations can use IntranetWare to strengthen and streamline their network operations and maintain a competitive edge. Also, small organizations can quickly establish an extensible, controllable worldwide presence without large investments.
* Originally published in Novell AppNotes
Disclaimer
The origin of this information may be internal or external to Novell. While Novell makes all reasonable efforts to verify this information, Novell does not make explicit or implied claims to its validity.