Managing Windows 2000 Group Policies with ZENworks for Desktops 3
Articles and Tips: article
Consultant
AppNet Solutions
rbender@appnetsolutions.com
01 Sep 2002
Novell's ZEnworks for Desktops v3.x introduced support for Windows 2000 Group Policies, which allows user-based policies, such as desktop settings and restrictions, to be associated with Workstation objects. This AppNote explains how to integrate these group policies with ZENworks and provides an example of how this helped simplify network management in an academic lab environment.
- Introduction
- Overview of Windows 2000 Group Policies
- Integration of Group Policies with ZENworks
- Example: Academic Lab Environment
- Conclusion
|
Topics |
group policies, Windows 2000, workstation management, ZENworks for Desktops |
|
Products |
ZENworks for Desktops 3 |
|
Audience |
network administrators |
|
Level |
intermediate |
|
Prerequisite Skills |
familiarity with network management concepts |
|
Operating System |
NetWare, Windows 2000 |
|
Tools |
none |
|
Sample Code |
no |
Introduction
With version 3.x of ZENworks for Desktops, Novell introduced support for Windows 2000 Group Policies. This support provides the network administrator with a great deal of flexibility when associating policies to users and workstations. One example of this additional flexibility is the ability to associate user-based policies, such as desktop settings and restrictions, to Workstation objects.
For example, suppose a college wants to enforce user-based policies on all workstations in their labs, while leaving the students' personal computers and the faculty/staff desktops unaffected. The students, faculty, and staff will be using the same login ID on all computers (lab and personal) and each of these computers has the Workstation Manager loaded. But how do you enforce user-based desktop settings and restrictions on specific workstations while using the same user ID? If the policy is associated to a user, it will be enforced on any workstation that this user logs into.
This AppNote describes a method of managing Windows 2000 Group Policies through ZENworks for Desktops. This method provides a solution for assigning desktop restrictions, which previously were only available through the user policies, to specific Workstation objects.
Overview of Windows 2000 Group Policies
In Windows 2000, Group Policies allow you to define configurations for groups of users and computers. The Group Policy settings that you create are contained in a Group Policy Object (GPO), which is in turn associated with selected Active Directory objects, such as sites, domains, or organizational units (OUs). This provides centralized policy-based management of users' desktops (a concept that ZENworks users have been familiar with for some time).
Group Policies are defined using the Group Policy snap-in for the Microsoft Management Console (MMC). This snap-in extends the functionality of the System Policy Editor and provides enhanced capabilities for specifying user and computer configurations.
Possible Windows 2000 Group Policy Settings
This section lists many of the possible policy settings in the User and Computer Administrative Template sections within the MMC Group Policy snap-in. This list may be helpful in determining which policies you want to enforce.
User Configuration (Administrative Templates)
|
Windows Components
|
|
|
Windows Explorer |
Hide the common dialog places bar Hide the common dialog back button Hide the dropdown list of recent files Enable Classic Shell Remove the Folder Options menu item from the Tools menu Remove File menu from Windows Explorer Remove "Map Network Drive" and "Disconnect Network Drive Remove Search button from Windows Explorer Disable Windows Explorer's default context menu Hides the Manage item on the Windows Explorer context menu Only allow approved Shell extensions Do not track Shell shortcuts during roaming Hide these specified drives in My Computer Prevent access to drives from My Computer Hide Hardware tab Disable UI to change menu animation setting Disable UI to change keyboard navigation indicator setting Disable DFS tab No "Computers Near Me" in My Network Places No "Entire Network" in My Network Places Maximum number of recent documents Do not request alternate credentials Request credentials for network installations |
|
Task Scheduler |
Hide Property pages Prevent task run or end Disable drag-and-drop Disable new task creation Disable task deletion Disable Advanced menu Prohibit browse |
|
Windows Installer |
Always install with elevated privileges Search order Disable rollback Disable media source for any install |
|
Internet Explorer
|
|
|
Search: Disable search customization Search: Disable find files via F3 within the browser Disable external branding of Internet Explorer Disable importing and exporting of favorites Disable changing Advanced page settings Disable changing home page settings Use Automatic Detection for dial-up connections Disable caching of Auto-Proxy scripts Display error message on proxy script download failure Disable changing Temporary Internet files setting Disable changing history settings Disable changing color settings Disable changing link color settings Disable changing font settings Disable changing language settings Disable changing accessibility settings Disable Internet Connection wizard Disable changing connection settings |
|
|
Disable changing proxy settings Disable changing Automatic Configuration settings Disable changing ratings settings Disable changing certificate settings Disable changing Profile Assistant settings Disable AutoComplete for forms Do not allow AutoComplete to save passwords Disable changing Messaging settings Disable changing Calendar and Contact settings Disable the Reset Web Settings feature Disable changing default browser check Identity Manager: Prevent users from using Identities |
|
|
Internet Control Panel |
Disable the General page Disable the Security page Disable the Content page Disable the Connections page Disable the Programs page Disable the Advanced page |
|
Offline Pages |
Disable adding channels Disable removing channels Disable adding schedules for offline pages Disable editing schedules for offline pages Disable removing schedules for offline pages Disable all scheduled offline pages Disable channel user interface completely Disable downloading of site subscription content Disable editing and creating of schedule groups Subscription limits |
|
Browser menus |
File menu: Disable Save As... menu option File menu: Disable New menu option File menu: Disable Open menu option File menu: Disable Save As Web Page Complete File menu: Disable closing the browser and Explorer windows View menu: Disable Source menu option View menu: Disable Full Screen menu option Hide Favorites menu Tools menu: Disable Internet Options... menu option Help menu: Remove "Tip of the Day" menu option Help menu: Remove "For Netscape Users" menu option Help menu: Remove "Tour" menu option Help menu: Remove "Send Feedback" menu option Disable Context menu Disable Open in New Window menu option Disable "Save this program to disk" option |
|
Toolbars |
Disable customizing browser toolbar buttons Disable customizing browser toolbars Configure Toolbar Buttons |
|
Persistence Behavior |
File size limits for Local Machine zone File size limits for Intranet zone File size limits for Trusted Sites zone File size limites for Internet zone File size limits for Restricted Sites zone |
|
Administrator Approved Controls |
Media Player Menu Controls Microsoft Agent Microsoft Chat Microsoft Survey Control Shockwave Flash NetShow File Transfer Control DHTML Edit Control Microsoft Scriptlet Component Carpoint Investor MSNBC |
|
Start Menu and Task Bar
|
|
|
Remove user's folders from the Start Menu Disable and remove links to Windows Update Remove common program groups from Start Menu Remove Documents menu from Start Menu Disable programs on Settings menu Remove Network & Dial-up Connections from Start Menu Remove Favorites menu from Start Menu Remove Search menu from Start Menu Remove Help menu from Start Menu Remove Run menu from Start Menu Add Logoff to the Start Menu Disable Logoff on the Start Menu Disable and remove the Shut Down command Disable drag-and-drop context menus on the Start Menu Disable changes to Taskbar and Start Menu Settings Disable context menus for the taskbar Do not keep history of recently opened documents Clear history of recently opened documents on exit Disable personalized menus Disable user tracking Add "Run in Separate Memory Space" check box to Run dialog box Do not use the search-based method when resolving shell shortcuts Do not use the tracking-based method when resolving shell shortcuts Gray unavailable Windows Installer programs Start Menu shortcuts |
|
|
Desktop
|
|
|
Hide all icons on Desktop Remove My Documents icon from desktop Remove My Documents icon from Start Menu Hide My Network Places icon on desktop Hide Internet Explorer icon on desktop Do not add shares of recently opened documents to My Network Places Prohibit user from changing My Documents path Disable adding, dragging, dropping and closing the Taskbar's toolbars Disable adjusting desktop toolbars Don't save settings at exit |
|
|
Active Desktop |
Enable Active Desktop Disable Active Desktop Disable all items Prohibit changes Prohibit adding items Prohibit deleting items Prohibit editing items |
|
Active Desktop (cont.) |
Prohibit closing items Add/Delete items Active Desktop Wallpaper Allow only bitmapped wallpaper |
|
Active Directory |
Maximum size of Active Directory searches Enable filter in Find dialog box Hide Active Directory folder |
|
Control Panel
|
|
|
Disable Control Panel Hide specified control panel applets Show only specified control panel applets |
|
|
Add/Remove Programs |
Disable Add/Remove Programs Hide Change or Remove Programs page Hide Add New Programs page Hide Add/Remove Windows Components page Hide the "Add a program from CD-ROM or floppy disk" option Hide the "Add programs from Microsoft" option Hide the "Add programs from your network" option Go directly to Components wizard Disable Support Information Specify default category for Add New Programs |
|
Display |
Disable Display in Control Panel Hide Background tab Disable changing wallpaper Hide Appearance tab Hide Settings tab Hide Screen Saver tab Activate screen saver Screen saver executable name Password protect the screen saver Screen Saver timeout |
|
Printers |
Disable deletion of printers Disable addition of printers Browse the network to find printers Default Active Directory path when searching for printers Browse a common web site to find printers |
|
Regional Options |
Restrict selection of Windows 2000 menus and dialogs language |
|
Network
|
|
|
Offline Files |
Disable user configuration of Offline Files Synchronize all offline files before logging off Action on server disconnect Non-default server disconnect actions Disable "Make Available Offline" Prevent use of Offline Files folder Administratively assigned offline files Disable reminder balloons Reminder balloon frequency Initial reminder balloon lifetime Reminder balloon lifetime Event logging level |
|
Network and Dialup Connections |
Prohibit deletion of RAS connections Prohibit deletion of RAS connections available to all users Prohibit connecting and disconnecting a RAS connection Prohibit enabling/disabling a LAN connection Prohibit access to properties of a LAN connection Prohibit access to current user's RAS connection properties Prohibit access to properties of RAS connections available to all users Prohibit renaming LAN connections or RAS connections available to all users Prohibit renaming of RAS connections belonging to the current user Prohibit adding and removing components for a LAN or RAS connection Prohibit enabling/disabling components of a LAN connection Prohibit access to properties of components of a LAN connection Prohibit access to properties of components of a RAS connection Prohibit access to the Network Connection wizard Prohibit viewing of status statistics for an active connection Prohibit access to the Dial-up Preferences item on the Advanced menu Prohibit access to the Advanced Settings item on the Advanced menu Prohibit configuration of connection sharing Prohibit TCP/IP advanced configuration |
|
System
|
|
|
Don't display welcome screen at logon Century interpretation for Year 2000 Code signing for device drivers Custom user interface Disable the command prompt Disable registry editing tools Run only allowed Windows applications Don't run specified Windows applications Disable Autoplay Download missing COM components |
|
|
Logon/Logoff |
Disable Task Manager Disable Lock Computer Disable Change Password Disable Logoff Run logon scripts synchronously Run legacy logon scripts hidden Run logon scripts visible Run logoff scripts visible Connect home directory to root of the share Limit profile size Exclude directories in roaming profile Run these programs at user logon Disable the run once list Disable legacy run list |
Computer Configuration (Administrative Templates)
(can be associated to either Users or Workstations through ZENworks)
|
Windows Components
|
|
|
Internet Explorer |
Security Zones: Use only machine settings Security Zones: Do not allow users to change policies Security Zones: Do not allow users to add/delete sites Make proxy settings per-machine (rather than per-user) Disable Automatic Install of Internet Explorer components Disable Periodic Check for Internet Explorer software updates Disable software update shell notifications on program launch Disable showing the splash screen |
|
Task Scheduler |
Hide Property Pages Prevent Task Run or End Disable Drag-and-Drop Disable New Task Creation Disable Task Deletion Disable Advanced Menu Prohibit Browse |
|
Windows Installer |
Disable Windows Installer Always install with elevated privileges Disable rollback Disable browse dialog box for new source Disable patching Disable IE security prompt for Windows Installer scripts Enable user control over installs Enable user to browse for source while elevated Enable user to use media source while elevated Enable user to patch elevated products Allow admin to install from Terminal Services session Cache transforms in secure location on workstation Logging |
|
System
|
|
|
Remove Security option from Start menu (Terminal Services only) Remove Disconnect item from Start menu (Terminal Services only) Disable Boot/Shutdown/Logon/Logoff status messages Verbose vs. normal status messages Disable Autoplay Don't display welcome screen at logon Run these programs at user logon Disable the run once list Disable legacy run list Do not automatically encrypt files moved to encrypted folders Download missing COM components |
|
|
Disk Quotas |
Enable disk quotas Enforce disk quota limit Default quota limit and warning level Log event when quota limit exceeded Log event when quota warning level exceeded Apply policy to removable media |
|
Logon |
Run logon scripts synchronously Run startup scripts asynchronously Run startup scripts visible Run shutdown scripts visible Maximum wait time for Group Policy scripts Delete cached copies of roaming profiles Do not detect slow network connections Slow network connection timeout for user profiles Wait for remote user profile Prompt user when slow link is detected Timeout for dialog boxes Log users off when roaming profile fails Maximum retries to unload and update user profile Add the Administrators security group to roaming user profiles |
|
DNS Client |
Primary DNS Suffix |
|
Printers
|
|
|
Allow printers to be published Automatically publish new printers in Active Directory Allow pruning of published printers Printer browsing Prune printers that are not automatically republished Directory pruning interval Directory pruning retry Directory pruning priority Check published state Web-based printing Custom support URL in the Printers folder's left pane Computer location Pre-populate printer search location text |
|
|
Network
|
|
|
Offline Files |
Enabled Disable user configuration of Offline Files Synchronize all offline files before logging off Default cache size Action on server disconnect Non-default server disconnect actions Disable 'Make Available Offline Prevent use of Offline Files folder Files not cached Administratively assigned offline files Disable reminder balloons Reminder balloon frequency Initial reminder balloon lifetime Reminder balloon lifetime At logoff, delete local copy of user's offline files Event logging level Subfolders always available offline |
|
Network and Dialup Configuration |
Prohibit configuration of connection sharing |
Integration of Group Policies with ZENworks
Windows 2000 Group Policies are associated to User and Workstation objects through user and workstation policy packages. Figure 1 shows the Windows Group Policy within a workstation policy package. As with the other policies, you must check the "Enabled" box before you can configure the policy. Also notice that we are viewing policies for WinNT-2000.
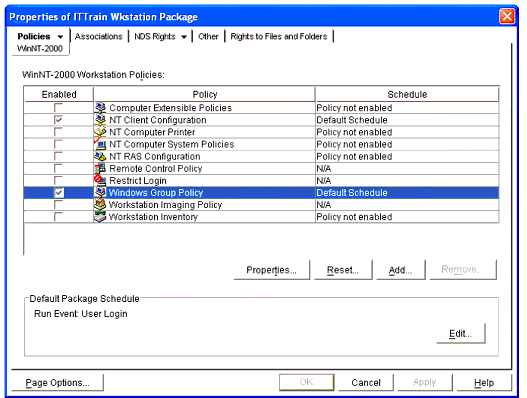
The Windows Group Policy within the Workstation Policy Package.
Figure 2 shows the Properties window for the Group Policy. The first field, "Network location of existing/new Group Policies", specifies where the actual group policy files will be (or already are) stored. The User or Workstation objects that are to be associated with this policy must have Read and File Scan rights to this directory.
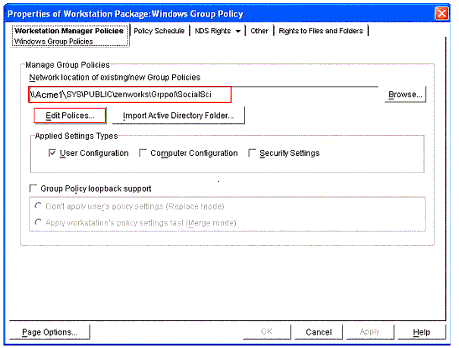
Properties windows for the Windows Group Policy.
Clicking the Edit Policies button will start the Microsoft Management Console (MMC) with the Group Policy snap-in (see Figure 3). This console will allow you to configure the desired policies. If the directory specified in the network location does not contain an existing policy, the policy files will be created-otherwise, the existing policies will be modified.
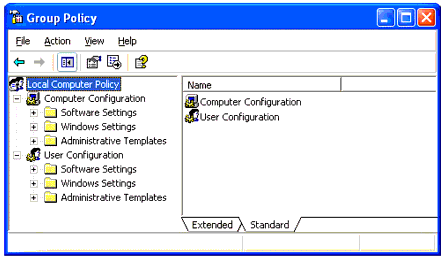
The Group Policy snap-in for the MMC.
Make sure you run the MMC from the same OS as the workstation where they will be applied. Windows XP, for example, has additional options which are not available in Windows 2000.
You'll notice that there is no Exit command under the File menu; you have to click on the X in the top-right corner of the MMC to exit and save your settings. When you exit the MMC and save your policy, the directory structure shown in Figure 4 will be created in the network location that you specified in the Windows Group Policy Properties window.
Note: TID #10065126 (available at http://support.novell.com) explains how Group Policies are created using ConsoleOne (and the MMC) on the administrator's workstation without modifying the policies on that particular workstation.
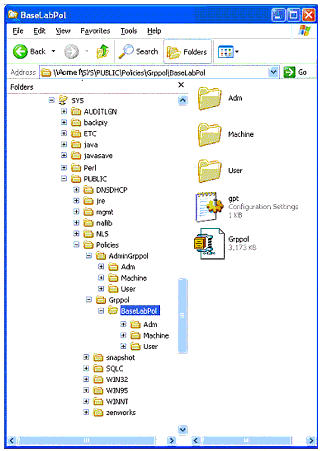
Network location of Group Policies.
The "Applied Settings Type" (circled in Figure 5) is a very important setting in this example. It tells ZENworks which set of Windows 2000 Group Policies is to be applied: User, Computer, or Security. In this example, only settings made in the User Configuration section of the MMC will be applied. This is the setting which allows us to apply User-based policies to workstations. The term "user- based" policies refers to any setting made under the "User Configuration" section of the Group Policy MMC. Without this setting, you would only be able to apply these settings to User objects.
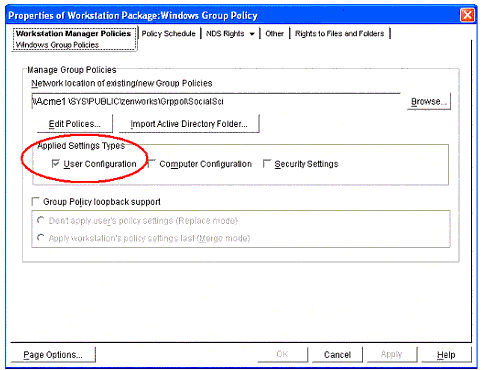
The Applied Settings Types setting.
Group Policy Directories on the Workstation
Group Policy files that are associated to the User and/or Workstation are copied down to the desktop when associated. The following directories are created on the workstation and displayed on the workstation as shown in Figure 6.
C:\winnt\system32\GroupPolicy.WMOriginal. This folder contains the original Group Policy settings for this desktop. The contents of the local GroupPolicy folder (C:\winnt\system32\GroupPolicy) are copied to the GroupPolicy.WMOriginal before the ZENworks policies are applied.
C:\winnt\system32\GroupPolicy.UserCache. If the Group Policies are associated through a ZENworks User Package, this folder is created. Only the specific policies included in this user policy package are stored in this directory. When the user logs out, the contents of this folder are removed, leaving only the GroupPolicy.WksCache and GroupPolicy.WMOriginal information.
C:\winnt\system32\GroupPolicy.WksCache. Similar to the UserCache folder, if the Group Policies are associated through a ZENworks Workstation Package, this folder is created. It contains the specific policies for this policy package.
C:\winnt\system32\GroupPolicy. This directory exists before ZENworks applies the appropriate Group Policies. It is the local Group Policy folder which contains the original Group Policies for the workstations before any new policies are applied. This folder will also contain the final version of the Group Policies which will be applied to the workstation by Windows.
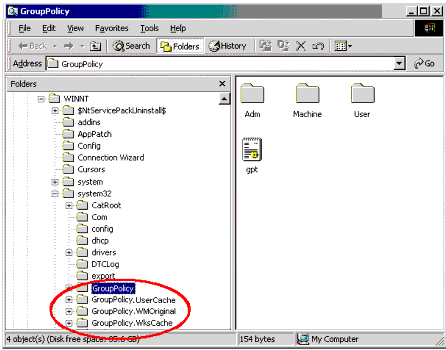
Group Policy directories on the workstation.
The sum of the WksCache, UserCache, and WMOriginal makes up the contents of what gets stored in the GroupPolicy folder. If both a user policy package and workstation policy package specify Group Policies to be applied, the addition of the GroupPolicy.WMOriginal, GroupPolicy.UserCache and GroupPolicy.Wks- Cache folders make up the contents of the GroupPolicy folder.
By default, the Group Policies defined in the User policy package are applied last. However, ZENworks for Desktops v3.2 provides Group Policy loopback support which gives you the ability to specify whether policies are merged or replaced. This is configured via the "Group Policy loopback support" setting located in the Properties window of the Windows Group Policy within the workstation policy package (just below the Applied Settings Type setting described previously). The two possible settings are defined as follows:
"Replace" indicates that the user policies defined in the workstation's Group Policy replace the user policies.
"Merge" indicates that the user policies associated through User and Workstation policy packages are combined. If the policy settings conflict, the user policies in the ZENworks workstation policy package take precedence over the policies specified by the ZENworks user policy package.
If you don't configure this feature, the Group Policies associated through the User policy package are applied.
Example: Academic Lab Environment
This section presents a real-world example of implementing Windows 2000 Group Policies in an academic lab environment. This solution helped a university IT department meet a special set of requirements. Figure 7 shows the design of the eDirectory tree used in this example.
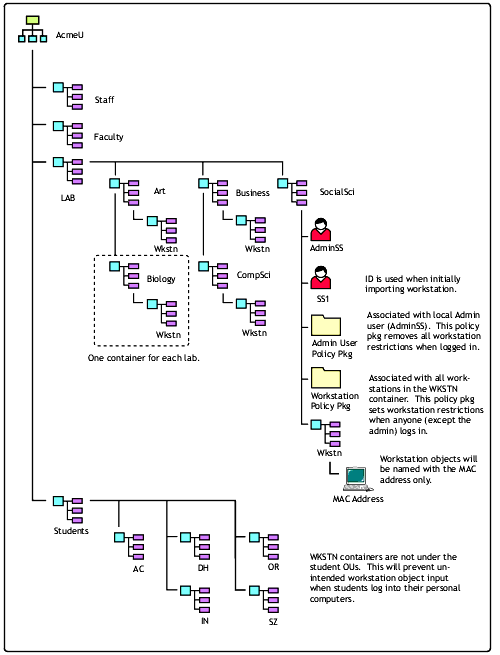
Sample eDirectory tree design for an academic lab environment.
Importing the Workstations
Before you can apply Windows 2000 group policies to workstations, the Workstation objects must be imported into the tree. This section briefly describes the method used to import the lab workstations into eDirectory. This method was chosen because of the initial constraints of the project-namely, that only lab workstation were to be imported. (Student, faculty, and staff personal computers were not to be imported at this time.)
To avoid using a local hosts file on each workstation and multiple import servers, this configuration uses a single import server. The import policy is set up to create the Workstation object in the WKSTN container relative to the user. So, in this example, the local lab administrator (AdminSS or SS1 in the sample tree) must be the first user to log in at the workstation so that it is imported properly.
Since the workstation import policy is globally associated to the server, all workstations (with Workstation Manager installed) will attempt to import themselves. The requirements for this phase of the project called for importing of lab workstations only, not student, faculty, or staff computers. One solution to this problem would have been to uninstall Workstation Manager from these excluded workstations. However, Workstation Manager was already installed on most of the workstations (including the students' personal computers). Removing or disabling it on all of these workstations was not feasible, largely because most of the workstations are unavailable during the summer. To work around this problem, the import policy was configured to import workstations into the WKSTN container below the user's context. If that container doesn't exist, the import fails and the following error is recorded in the C:\WSIMPORT.LOG file (assuming Workstation Manager is loaded):
*****(4)***** 08/22/02 09:25:32 am WSREG-v3.0 This log file is reporting activity on a WM_USER_LOGIN_EVENT event. WSREG-v3.0 While contacting the Work Station Import Service, an error -1 was encountered, and error description <Could not locate the target container.> was reported. WSREG-v3.0 Registration will not occur for this event. WSREG-v3.0 The program finished running.
When the faculty and staff workstations are ready to be imported, all you would need to do is add a WKSTN container under the Staff or Faculty OU.
Associating the Workstation Policies
Once the lab workstations are imported into the appropriate container, a workstation policy package (which is defined for each lab container) is associated to each lab WKSTN container. The Group Policy is enabled in each of these policy packages.
Each group policy is configured to use the same definition which we decided to store in sys:\public\policies\Grppol\Baselabpol. One benefit to storing the policies under the sys:\public directory is that all users already have Read and File Scan rights to this directory. If a particular lab needs a unique Group Policy configuration, the policy for that lab can be configured to access another directory. For example, if the SocialScience lab needed a special configuration, the Group Policy could be configured to point to the sys:\public\policies\grppol\ SocialSciPol directory.
Through a User policy package, another Group Policy is associated to the local lab administrator (in this example, AdminSS.SocialSci.Lab.AcmeU) which disables all desktop restrictions. As discussed earlier, user-based group policies override workstation-based policies by default. This allows the lab administrators to make the necessary modifications to the workstations as needed.
Logging In to the Lab Workstations
Another constraint of the project was that all students, faculty, and staff would use their own IDs to log in to the lab workstations (increasing accountability and consistency). Dynamic Local User (DLU) was the obvious solution for this requirement; however, it did raise a problem. The problem was how to keep the DLU from being created on the non-lab workstations, since this action could change the functionality of existing applications and desktop configurations. Fortunately, ZENworks has a feature that allows you to enforce DLUs only on particular workstations (see Figure 8). We used this configuration to enforce DLUs on only the lab workstations.
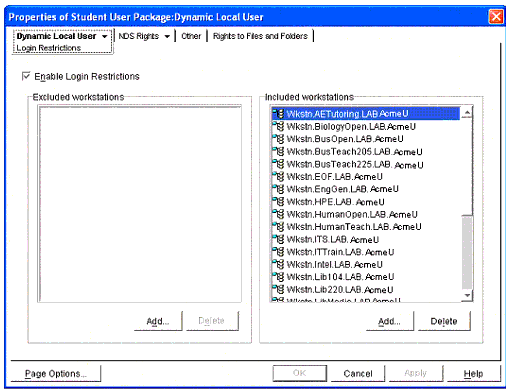
DLU Login Restrictions being applied to a student's User Policy Package.
This solution was just a bit short of perfect. If you log in to the network as a user that is associated to a DLU policy from a workstation which was not included in the login restriction, you'll receive the security message shown in Figure 9.
DLU error message, which can be disabled via a registry setting.
This message is only informational, but it can be alarming to users.
The good news is that you can disable this message; the bad news is that this involves changing a registry setting. In the lab configuration, we set up a NAL application to automatically make the change on non-lab workstations, but the users would still see that message the first time they logged in. Details about the registry setting to disable this message can be found in TID #10070003, available at http://support.novell.com/cgi-bin/search/searchtid.cgi?/10070003.htm.
Note: If a local Windows user exists that has the same name as the eDirectory account, the DLU will not be created. Windows will use the existing local account.
Conclusion
This AppNote has shown how Novell's ZENworks for Desktops 3 can provide flexible enforcement of Windows 2000 Group Policies. In particular, it explained how user-based policies can be associated to particular workstations. While your project may not have the same constraints as the example project described in this AppNote, I hope some of the ideas presented here will help you use the powerful features of ZENworks to find a solution to your unique set of requirements.
For more information about ZENworks for Desktops 3, see the product Web site at http://www.novell.com/products/zenworks.
Additional References
For more information on Windows 2000 Group Policies and other topics discussed in this AppNote, see the following references (in addition to those cited previously):
Windows 2000 Group Policy White Paper (http://www.microsoft.com/windows2000/techinfo/howitworks/management/grouppolwp.asp)
Introduction to Windows 2000 Group Policies (http://www.microsoft.com/windows2000/techinfo/howitworks/management/grouppolicyintro.asp)
TID #10065126 "How Group Policies Work" (http://support.novell.com/cgi-bin/search/searchtid.cgi?/10065126.htm)
If you're having problems applying Group Policies in ZENworks for Desktops 3.x to a Windows 2000 workstation, you can enable logging as a troubleshooting step. See TID #10058023 "Group Policy Logging" at http://support.novell.com/cgi-bin/search/searchtid.cgi?/10058023.htm.
If policies are not being applied to the workstations correctly, you may need to clear all of the Windows Group Policy settings from the computer. See TID #10059171 "Clearing Local Workstation Policies" at http://support.novell.com/cgi-bin/search/searchtid.cgi?/10059171.htm.
* Originally published in Novell AppNotes
Disclaimer
The origin of this information may be internal or external to Novell. While Novell makes all reasonable efforts to verify this information, Novell does not make explicit or implied claims to its validity.