Implementing SecuGen's Fingerprint Recognition Technology with NMAS 2.0
Articles and Tips: article
Sr. Systems Engineer
SecuGen Corporation
schandler@secugen.com
01 Sep 2001
In today's highly-connected business environments, securing business-critical data is a vital concern. One of the most problematic areas of security is user authentication. Fortunately, the increasing popularity of biometric devices is making it easier to ensure that users logging in to the network are really who they say they are. This AppNote provides an overview of what is involved in implementing SecuGen's fingerprint recognition devices with Novell Modular Authentication Service (NMAS).
- Introduction Introduction
- Background on Biometrics Background on Biometrics
- SecuGen's Fingerprint Technology SecuGen's Fingerprint Technology
- Implementation Overview Implementation Overview
- Conclusion Conclusion
|
Topics |
biometrics network security, user authentication |
|
Products |
Novell Modular Authentication Services (NMAS), SecuGen biometric devices |
|
Audience |
network administrators, developers, integrators |
|
Level |
intermediate |
|
Prerequisite Skills |
familiarity with NetWare architecture and administration via ConsoleOne |
|
Operating System |
NetWare 5.1 or higher, Windows NT 4 SP5 or higher, NDS eDirectory 8.51 |
|
Tools |
ConsoleOne |
|
Sample Code |
no |
Introduction
In the 21st century, corporations depend on their networked resources to control their most valuable assets: intellectual property and data. Today, data on servers represents the core asset of most companies. With identity theft on the rise, it is critically important to ensure that the right people are accessing this information, that they are not being impersonated, or that someone else is not using their account to log in, even with the authorized user's consent.
Where passwords or other methods may be deemed too weak or inconclusive in validating the credentials of an individual trying to access networked resources, biometric authentication can be used to effectively prove that those requesting access are really who they say they are. Biometric authentication methods do not rely on passwords (something you know, which can be forgotten), nor do they rely on a smart card or other token (something you have, which can be stolen or lost). Instead, they rely on unique physical characteristics of the individual-something you are.
Novell Modular Authentication Service (NMAS) Enterprise Edition 2.0 allows customers to secure their Novell- managed environment by using multi-factor security/authentication mechanisms. In NMAS, "multi-factor" means more than one type of authentication mechanism can be assigned to and enforced for a specific user. This type of authentication can be set up as a graded login-the type of access and permissions available to a user can be assigned based on the authentication mechanisms used.
This AppNote describes how security hardware from SecuGen Corporation can be implemented with the NMAS software to form a powerful yet cost-effective means of authenticating users in a Novell environment.
Background on Biometrics
Iris and retinal scan technologies are the most secure methods of biometric authentication, since the eye provides the richest source of individual data types on the human body. However, this method has location, power, and condition variables associated with it that limits the technical application of such devices and makes mass deployment difficult. It is invasive (lasers are fired into the eyes of the individual being scanned) to the point that some users experience extreme discomfort. In addition, iris and retinal technology costs considerably more than other biometric methods.
Voice identification is a low-cost authentication method. However, voice changes caused by sore throat, hoarseness, or the common cold can make identification difficult or impossible.
As a static biometric method, fingerprint technology is considered the best choice for most applications because of its accuracy, speed, reliability, non-intrusive interfaces, and cost-effectiveness.
SecuGen's Fingerprint Technology
SecuGen manufactures a line of optical fingerprint identification devices which includes its EyeD Mouse, EyeD OptiMouse, EyeD Hamster, and EyeD Keyboard.
The advantages of using SecuGen's fingerprint technology are many:
Durability. SecuGen hardware is comprised of a shell with a patented, scratch-proof surface lens over a prism that directs data to a CMOS sensor unit. The CMOS sensor unit reads and extracts fingerprint data and sends it to a host PC for processing.
Fast, Accurate. SecuGen uses its own proprietary algorithms to perform a number of steps in the fingerprint matching process. These algorithms have been specially designed for speed and accuracy.
Integrates into Existing Systems. SecuGen's algorithms are incorporated into the software component of the solution to optimize the integration. This allows partners to develop solutions with SecuGen technology very rapidly.
Cost Effective. SecuGen technology can be installed on all desktops in an organization at an acceptable cost. A recent study by the Gartner Group on a medium-size corporation (500 desktops) where passwords are changed quarterly concluded that password maintenance cost the average corporation $340.00 (US) per user per year for password maintenance and administration.
Leading Edge Technology. SecuGen manufactures its fingerprint identification devices under strict factory conditions, and maintains its own research division to continuously evolve the product line.
For more information about SecuGen's security technology, visit the company's Web site at http://www.secugen.com.
How It Works
With SecuGen hardware and NMAS software, the fingerprint authentication process is simple. In order to log in, the user places the requested finger(s) on the reader, which performs a high-resolution scan of the fingerprint image. SecuGen devices use multiple LEDs to capture samples, which allows them to differentiate between actual fingers (three-dimensional objects) and fingerprints lifted from other sources (two-dimensional copies). The system will not allow copies of fingerprints to produce a match.
Once a valid fingerprint image is captured, the SecuGen device scans the image, looking for "minutiae" data (ridge ends, splits, dots, arches, bifurcations, and so on) that distinguish one fingerprint from another. This data is processed, enhanced, and sent to the host PC.When the host PC receives the data, it creates a template by hashing the output data. This template is then sent to the NMAS client. The NMAS client encrypts the template and sends it over the network to the server, where it is unencrypted and matched against the supplied credentials. The process returns a simple "yes" or "no" for access. Keep in mind that, as a user name is provided at login time, the NMAS client is able to search against the NDS templates because the process provides one-to-one matching. This also aids in speeding up the matching process.
Many people interested in fingerprint identification technology are under the initial impression that the fingerprint images themselves are stored on the server or encrypted and stored in NDS, similar to the way passwords are managed. Actually, the fingerprints are never stored anywhere. Rather, it is the hased digest of the extracted fingerprint data that is stored as a template (in this case, in NDS).
It is important to note that SecuGen does not extend the NDS schema during the installation of the NMAS method; NMAS extends the NDS schema to provide a place for vendor NMAS values to be written to. Vendor methods are written around a compliant structure so they add with compliance to Novell's structure. Thanks to Novell's industry-leading reputation with their products, purchasers of third-party add-on products can have much higher confidence in the stability of the add-ons. For an independent company to come up with a competing product, they would have to go through independent testing and validation to prove the product's stability. Even then, it is unlikely that a third-party, at the outset of their product introduction, would gain the same level of respect as Novell.
Hardware and Software Requirements
NMAS 2.0 requires Novell eDirectory 8.51, Certificate Server 2.02, and NICI 1.57. On the NetWare platform, version 5.1 or higher is required. The system can use domestic (128-bit) encryption or lower encyryption for international installations; you just need to ensure that the server, OS, and client components are all properly matched. On Windows NT, version 4 Service Pack 5 or higher is needed (SP6a is recommended). Memory requirements vary depending on the size of your NDS structure.
Any workstation that will be using biometric authentication must have a mouse (or equivalent device) and the proper drivers installed to ensure the capture of fingerprint data. Workstations require NetWare Client 32 version 4.7 or higher for Windows NT/2000, or version 3.21 or higher for Windows 95/98.
Note: Windows 95/98 is not a recommended platform in a truly secure environment, as local login can be permitted simply by escaping login screens rather than executing them. In cases where Windows 95/98 workstations are employed in a network, it is advisable to store all secure data on the network and guard against access using biometrics.
Implementation Overview
NMAS is installed by an Admin-equivalent user logged in to the target NetWare server using ConsoleOne. The installation is wizard- based and guides you through the process. It checks whether or not base requirements are met for OS software components (such as the version of NICI), and then asks which of the methods included in the NMAS 2.0 base package you want to install. You can choose any or all of the supplied methods, or come back and easily add or delete methods later. SecuGen's fully-supported method integrates with NDS in a trouble-free manner; like all installed methods, it can be managed from inside ConsoleOne as needed.
Adding an Authentication Method
To add a new authentication method in ConsoleOne, navigate to the Login Policy object in the NDS tree, as shown in Figure 1.
Locating the Login Policy via the NDS tree view in ConsoleOne.
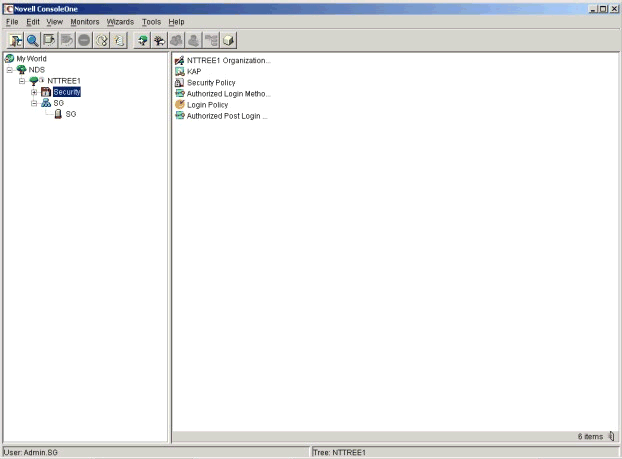
Right-click on the Login Policy, and then choose to add an authorized Login Method object. In the resulting dialog box, navigate to the method of choice and point to its CONFIG.TXT file. This file contains descriptions of all the parameters to be supplied to NMAS when the method is installed on the server. Once the method is added, it is available-but it needs to be enabled to be used by clients.
After the method is installed, it needs to be activated as a Login Policy. This is done by selecting the Security object in the NDS tree (located in the left pane as shown in Figure 1), and then right-clicking on the Login Policy object in the right pane and selecting Properties. (The resultant dialog box can be seen in Figure 2.) Adding or removing Authorized Login Methods is also done from the Security object. Instead of selecting Login Policy, you double-click on the Authorized Login Methods object (just above Login Policy) and, once inside this area, manipulate the objects as needed.
One caveat: If you try to remove an Authorized Login Method that is associated with a Login Policy, the system will tell you "Method in use-cannot be removed." You must unassociate the method from any active Login Policies before you can remove it, as the object is in use by NDS.
Enabling the Biometric Login Method
Once the new SGENBIOM method is active, it can be set as the primary method for login. Or it can be used with any other supported method to provide graded, multi-factor authentication. In the dialog box shown in Figure 2, you select the SGENBIOM method by clicking on the arrow to move it from the "Available Login Methods" list to the "Selected Login Methods" list. This will enable the login method for use on your network.
Login Sequences page demonstrating where graded authenitcation is set up.
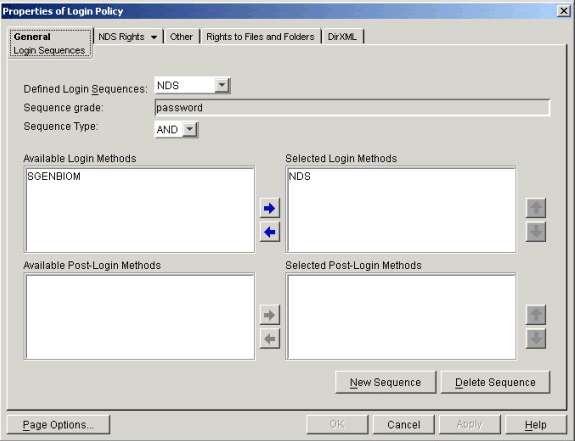
In order for users to use the biometric login functionality, the NMAS client must be installed at the users' desktops, with SGENBIOM being the chosen method.
Disallowing Password Authentication
For administrators who require it, login methods such as NDS passwords can be "locked off," disallowing users from authenticating via a password. In effect, this closes any password "back door" that an unauthorized user might try to exploit. As shown in Figure 3, this can be set on a user-by-user basis. Administrators can thereby employ a security architecture in which they can have extremely high confidence that any logged-in user viewed in a log file is in fact the authorized user.
ConsoleOne property page demonstrating where to disable use of a user's password for login purposes.
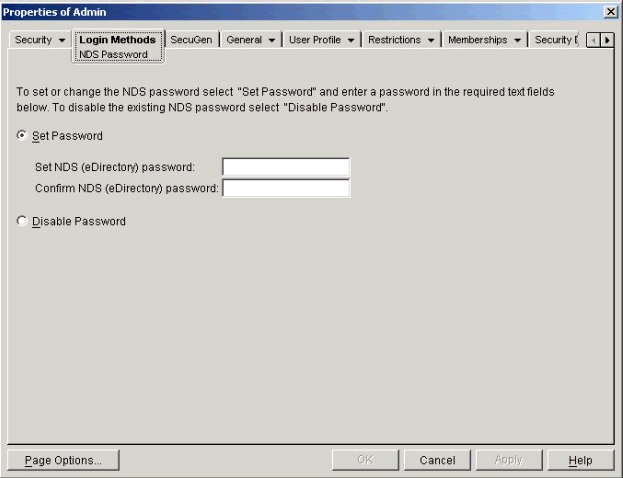
If you set the Disable Password option, the selected user will not be able to authenticate via a password under any circumstance for the account on which this setting has been activated.
Note: It is not recommended that top-level administrators of the tree use biometrics exclusively; if NDS becomes corrupted, a password will generally be needed to fix it.
Setting Authentication Sequences for Users
As shown in Figure 4, you can set the authentication sequences associated with the target user. For example, where the president of a company might access more sensitive data than a secretary, you would generally require different levels of proof for these two users. Users needing access to sensitive data can have stricter policies enforced, while less-sensitive users can have less strict policies.
ConsoleOne property page to set clearances (grades) of authentication by user.
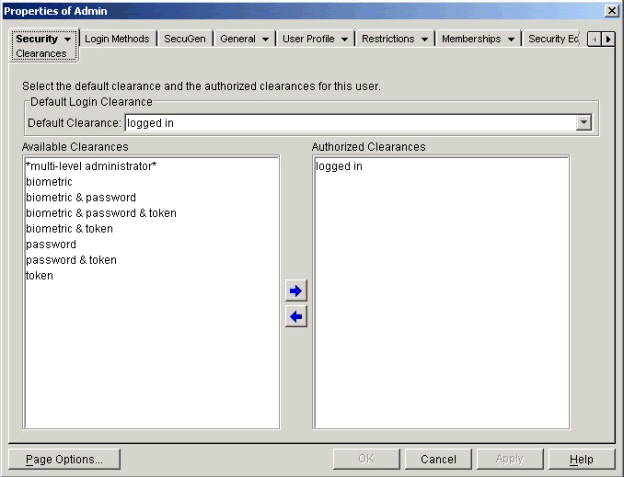
Updating and Exporting Methods
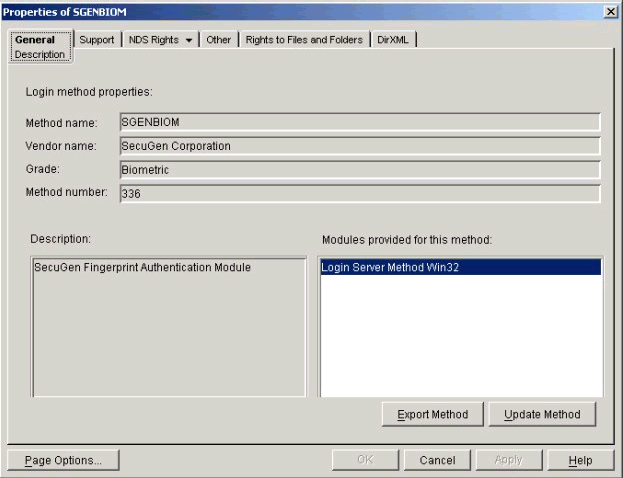
As shown in Figure 5, you can update an authentication method when a newer release becomes available (using the Update Method button). You can also export a method to another server if it is unavailable on that server and you need to get its source for another target system (using the Export Method button).
SGENBIOM method property page (General) from within ConsoleOne.
Enrolling a User's Fingerprint
To enroll a user's fingerprint, start ConsoleOne, go to the properties page for the user, and select the SecuGen tab (see Figure 6). Click on the Enroll Fingerprint button to invoke the SecuGen User Registration process.
SGENBIOM method property page (Enrollment) from within ConsoleOne.

Depending on how the administrator has configured the login policy, more than one digit may be asked for during registration.
Note: It is not recommended that the little finger ("baby" or "pinkie" finger) be used for registration. Extensive research has shown that this finger has minimal data and can prove to be inconclusive for matching purposes.
Figure 7 shows the User Registration dialog box after a fingerprint has been scanned.
SecuGen User Registration dialog box.
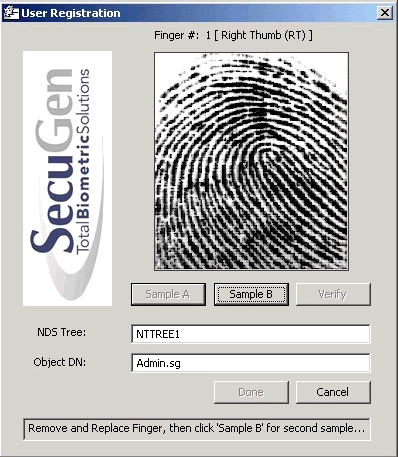
The user is registered with two samples, which are then verified against the finger, for a total of three samples for richer matching. Once all of the required digits are registered, click on the Done button (it is dimmed until all the registration is performed). The sample template data is then written to NDS.
On workstations with the client tool installed, users can enroll using this same interface from their workstations; using the same interface keeps the process consistent. Users will need to perform a sample capture for use as a base template. Therefore, they should understand the need for consistency and correct placement of the finger on the optic scanner for authentication at the user's workstation in the field. The best possible scan should be acquired to ensure the best possible results.
Be aware that the only way to enforce a true trust model is to supervise the user enrollment process. Allowing users to enroll themselves without supervision allows users other than the intended ones to register. This is why a remote registration module would be less useful-unless the process is rigorously supervised, you can never warranty the integrity of a user's credentials.
Conclusion
SecuGen and NMAS provide a highly secure and effective replacement for passwords in an organization. In addition to password replacement, this solution provides a high level of assurance users of a system are who they say they are.
NMAS can be implemented in an entire organization at the server level, and then deployed on a workstation-by-workstation model. Adopters can rest assured that this solution can be implemented as needed; there is no outside requirement to convert the entire organization once NMAS is installed.
NMAS can be used in conjunction with Novell Single Sign-On to provide a total solution for securing passwords at application levels. NMAS controls the login to NDS, while Single Sign-On allows a user to securely store passwords to applications and Web pages as needed. This combination allows for a rapidly-deloyable solution.
NetWare 6.0 has a native NMAS solution, providing two-factor authentication right out of the box. An upgrade to NMAS Enterprise Edition allows all the flexibility and tailoring an installation might desire.
Reviewing the costs of NMAS and SecuGen hardware, the cost savings on password maintenance alone can demonstrate a payback window of a single year. This doesn't even take into account increased productivity and decrease in fraud activity comensurate with this approach.
SecuGen's superior hardware solution with NMAS allows for a full featured, best-of-breed solution. The nature of SecuGen's technology makes it quick to integrate into existing applications, allowing rapid deployment of biomentrically-secure solutions as an extension of this solution.
For more information about SecuGen's line of biometric products, see http://www.secugen.com.
For more information about network security solutions, see http://www.novell.com/products/security.
* Originally published in Novell AppNotes
Disclaimer
The origin of this information may be internal or external to Novell. While Novell makes all reasonable efforts to verify this information, Novell does not make explicit or implied claims to its validity.