An Introduction to BorderManager Enterprise Edition 3.0
Articles and Tips: article
01 Feb 1999
Adapted from the BorderManager 3.0 Reviewer's Guide.
The recent release of this latest version of BorderManager is gaining a lot of attention. Find out how you can get higher performance, more security, and lower cost of ownership as you connect your local network to the Internet.
- Introduction
- The Need for Integrated Security Services
- The BorderManager Enterprise Edition Solution
- Typical BorderManager Deployment Scenarios
- Conclusion
Introduction
BorderManager Enterprise Edition 3.0 is a complete Internet security management suite for networks that use Novell Directory Services (NDS). It leverages NDS to deliver secure single sign-on to network services, as well as directory-based policy management. The integration of security services such as firewall services, virtual private networking, caching, and authentication provide a direct benefit to network designers in making intranet and Internet access easy to secure and easy to manage. BorderManager also delivers high performance and low total cost of network ownership through centralized administration and control.
This AppNote summarizes the need for an integrated security services solution and describes how BorderManager Enterprise Edition meets the need. It covers each component of the BorderManager suite, including:
Firewall services
Virtual Private Network (VPN) services
Proxy caching services
Policy-based administration
Authentication services
Logging, alerting, and reporting
For more information about BorderManager Enterprise Edition, visit the BorderManager Web site at:
http://www.novell.com/products/bordermanager/
The Need for Integrated Security Services
Many companies are taking advantage of the Internet as a low-cost wide area network link and interconnecting their local area networks through virtual private networks (VPNs). The advantages are many, including closer interaction with employees through internal Web servers, closer interaction with customers through the Internet, and closer interaction with business partners through extranets. However, companies must address a major issue when connecting to the Internet and deploying intranets and extranets—that issue is security.
The Internet is notoriously unsecure. As a result, integrating a corporate network with the Internet exposes it to intrusion from the outside. To provide protection, a number of vendors provide firewalls, which form a protective barrier between the Internet and the corporate network. There is a more severe and more subtle security problem, however, one that is more difficult to deal with than Internet hackers. Deploying Internet technologies, such as internal Web servers, on a corporate network exposes the information stored on them to intruders from within the company. In this case, an Internet firewall provides no protection.
Software vendors as a group have addressed several aspects of the security and performance issues associated with deploying Internet technologies. They offer a variety of products, including Internet firewalls, performance accelerators, VPNs, and Internet Web destination content filters. The problem is, a network owner has to cobble together these products from multiple vendors to provide a solution.
Managing a conglomeration of separate products is complicated, inefficient, and error prone. In fact, the ICSA reports that up to 90 percent of all firewall break-ins are due to configuration errors. Administrators have to deal with multiple directories for each user, and users have to deal with multiple user IDs and passwords. To make matters worse, as difficult and costly as the resulting solution is to manage and use, it still does not provide strong protection against internal break-ins.
What is required is a set of services that provides protection from outside break-in, protection from inside break-in, performance acceleration, a secure VPN capability, and full control over outgoing Internet access—all in a single, integrated, and manageable package.
The BorderManager Enterprise Edition Solution
Novell's BorderManager Enterprise Edition 3.0 provides an integrated security services solution. This security management solution uses the power of Novell Directory Services (NDS). With BorderManager, a company can:
Take full advantage of the Internet and its technologies while protecting company information from internal and external intruders.
Deliver high performance to users—without trading off strong security.
Lower the total cost of network ownership through centralized administration and control.
Because BorderManager is integrated with NDS, network administrators can control security and access globally from a single, centralized point. Security management through NDS scales easily and allows administrators to delegate certain access management responsibilities in a controlled and secure manner. Tight integration with NDS makes BorderManager a natural extension for current NDS users.
Because all authentication is performed through NDS, administrators do not have to maintain a multitude of access control and security information spread across multiple products and directories. As a result, BorderManager reduces the risk of error, which ensures a high level of security. In addition, with a single sign-on through NDS users can access all network resources to which they are authorized, regardless of their network entry point or the location of the resources. They can sign-on from a directly-connected LAN workstation, from a dial-up LAN workstation, or from a remote VPN client over the Internet.
NDS-based authorization is far more secure than conventional TCP/IP security mechanisms. TCP/IP security is based on IP addresses or segments rather than on users. The resulting security is weak. For example, an employee whose workstation does not have access to a particular network resource can simply move to another employee's workstation that does have the desired access. Dynamic Host Control Protocol (DHCP) worsens the problem because each user's machine address changes, making identity-based management difficult. BorderManager with NDS, provides security that is user centric rather than machine or IP-segment centric. This allows administrators to establish security based on both resource identity and user identity. When a user logs in, access to a network resource is granted or denied based on the user's identity and access permissions rather than on the identity of the workstation from which the user logs in.
BorderManager Enterprise Edition 3.0 includes the following services:
Firewall Services
Virtual Private Network Services
Proxy Caching Services
Policy-Based Administration
Authentication Services
Logging, Alerting, and Reporting
Firewall Services
BorderManager provides a firewall strong barrier between the corporate intranet and the Internet to protect against outside intruders. BorderManager firewalls can be used to partition the corporate intranet into secure segments to protect sensitive information from internal break-in. BorderManager firewall services allow a company to control incoming access from the Internet as well as outgoing access to the Internet.
BorderManager implements access control components at all layers of the Open Standards Interconnection (OSI) model to provide solid protection. Each higher-level component provides additional security over the lower-level components. The components are integrated and work together to provide a secure environment. The components listed from the highest level to the lowest level are:
Application Proxy. BorderManager includes a number of application proxies, such as HTTP, FTP, Gopher, Mail, News, Real Audio/Video, and DNS. BorderManager also includes a generic TCP proxy and a generic UDP proxy to allow administrators to configure additional application proxies such as LDAP. The application proxies relay all data between user applications and Internet/intranet resources. The proxy examines information at OSI layer 7, the application layer. It looks not only at the address of a packet, but also at the entire context of the session in which the packet is being sent and applies content-based semantic access controls prior to relaying the data.
Application proxies provide the highest level of protection, enhancing the protection provided by circuit gateways and packet filters. For example, once a circuit exam gateway creates a virtual pipe between a client and remote host, any application can run over that connection. The application proxy, however, can restrict sessions over the pipe based on application and even types of commands within an application.
The HTTP application proxy supports Secure Sockets Layer (SSL) tunneling, allowing an encrypted path between the client and server to protect information from eavesdroppers and vandals.
Circuit Gateway. BorderManager provides two circuit gateways: a SOCKS gateway and the Novell IP Gateway. The SOCKS gateway includes SOCKS client and server v4 and v5 protocols. SOCKS support enables the BorderManager firewall to be configured as a component of a firewall solution, working in conjunction with firewalls from other vendors. BorderManager can be used in front of, within, or behind existing firewalls. SOCKS server support allows the BorderManager server to operate with universal SOCKS clients, providing strong cross-platform client support. SOCKS with SSL provides a VPN capability for NT, UNIX and NetWare clients.
The Novell IP Gateway includes both an IPX /IP gateway and an IP/IP gateway which provides transparent authentication to BorderManager. The Novell IP Gateway allows both IPX and IP clients to access TCP/IP services. When an IPX or IP client requests a TCP/IP service (such as HTTP, FTP, Telnet, or Gopher) from a host inside or outside the firewall, the associated circuit gateway intercepts the request. It then consults NDS to verify that the user has the authorization to initiate the session. Access controls can restrict sessions based on protocol and by host address/domain name. The circuit gateway, which examines packet information at layer 5 of the OSI information model, provides a higher level of protection than just a packet filtering solution alone. The Novell IP Gateway uses native MS Winsock 2.0.
Network Address Translation. BorderManager provides both dynamic and static IP and IPX network address translation (NAT) tables. The administrator configures the tables with public sets of IP addresses. BorderManager uses the tables to remap automatically the source address of the packet headed for a destination outside of the firewall. This address translation, which takes place at OSI level 3, hides the addresses of the internal network from the outside world for strong security. In addition, address translation relieves the administrator from the time-consuming and error-prone task of managing IP addresses by dynamically and automatically mapping unregistered internal addresses to registered IP addresses. It can map up to 5,000 unregistered addresses concurrently per interface.
Packet Filter. The BorderManager packet filter, which operates at OSI layer 3, checks each packet against access controls. The filter checks source and destination host IP address to restrict access to and from certain IP hosts; source and destination IPX addresses to restrict access to and from certain IPX hosts; IP protocol/port to restrict access to certain Internet protocols and ports, such as HTTP, FTP, Telnet, and Gopher; and IPX Protocol to restrict access to certain types of NetWare Core Protocol (NCP) requests.
BorderManager provides a stateful packet filter engine that looks not only at the address of a packet, but also at the entire context of the session in which the packet is being sent. This makes it far more effective in identifying suspicious packets. For example, a hacker could easily get through an address filter using address spoofing. But a hacker could not use address spoofing alone to get through the BorderManager packet filter. The hacker would also have to determine the entire context of the session in which the packet is being sent.
For even more protection, the BorderManager firewall provides a set of application programming interfaces (APIs) that enable additional filters developed by third-parties to be integrated with the firewall. Novell partners will offer a variety of third-party filters, including anti-virus, Java, ActiveX, reporting, and MIMEtag. For an up-to-date list of available filters, visit www.novell.com/products/bordermanager.
In addition, BorderManager includes a trial version of the CyberPatrol destination content filter that can deny outgoing Internet access to certain Web sites based on content, such as denying access to sites with sexually-oriented content.
One of the major problems with traditional firewalls, especially packet filters, is that although they can provide tight security, setting them up is complex and difficult. Administrators often make errors in setting up the firewall, which could cause security loopholes.
BorderManager simplifies firewall setup and administration setup with a simple sequence:
The BorderManager firewall automatically initializes to allow no traffic to pass through in either direction.
The administrator next configures the circuit gateways and application proxies to be used through the BorderManager Setup window.
The administrator then moves to the BorderManager Rules window and establishes high-level access rules for the circuit gateways and application proxies selected. BorderManager then uses the rules information to make the correct settings in the packet filter-automatically.
Virtual Private Network Services
BorderManager enables a company to use the Internet as a link to connect sites, allow remote clients to access the corporate intranet, and implement extranets that connect business partners with the corporate intranet. The information transmitted over the Internet is secured through encryption to prevent unauthorized access by eavesdroppers. In addition, the information is checked for accuracy to detect tampering by vandals.
BorderManager provides VPN services that allow organizations to run private networks securely and economically over the Internet. BorderManager VPN allows a company to implement three types of virtual private networks:
Site to Site. A company can interconnect servers at two or more sites using the Internet as a link. In this way, independent LAN segments can be connected into a single cohesive WAN.
Client/Server. A company can allow LAN users, dial-up users, and even cable modem users running either IP or IPX protocol to access VPN resources through a secure connection over the Internet. In this way, a company can give users secure access to the network resources they need, regardless of their location or the location of resources. With BorderManager VPN, users can access all resources from anywhere with a single sign-on.
Extranet. A company can connect its corporate network with its business partners' networks into a single cohesive extranet using the Internet to link sites.
When implementing a VPN, it is essential to ensure that only authorized members of the VPN community are allowed to use it. It is necessary to ensure that all information transmitted over the VPN is safe from eavesdroppers and vandals. BorderManager authenticates all users through NDS to ensure that only authorized VPN community members are permitted to use the VPN. BorderManager VPN services employ security mechanisms based on open standards and established cryptographic techniques, such as IP SEC, RC2, RC5, DES, 3DES, and SKIP to ensure the privacy and integrity of information transmitted.
BorderManager VPN supports symmetric multiprocessing (SMP), allowing it to take advantage of multiprocessing hardware to increase speed. To optimize performance further, BorderManager performs selective encryption which encrypts only the information sent to and from protected networks, as specified by the administrator. BorderManager employs maintenance traffic reduction techniques, such as header compression and efficient WAN routing updates, to deliver high bandwidth over the VPN. BorderManager can support up to 256 sites per tunnel and can service up to 1,000 dial-in users per server.
BorderManager supports a variety of standard tunneling, encryption, and key exchange mechanisms to provide a strong, flexible security framework. It supports tunneling based on the field-proven IP relay mechanism using the IP SEC standard (RFC # 1825-1828). It supports the RC2, RC5, DES, and 3DES encryption algorithms. And it supports the SKIP (simple key exchange Internet protocol) standard to allow secure distribution of authentication keys. BorderManager VPN services are also managed through NDS. This allows the administrator to manage the VPN, even multiple VPNs, from a single, centralized point.
Proxy Caching Services
BorderManager provides performance-enhancing Web and FTP proxy caching services that provide a high level of performance without jeopardizing security. A company can use BorderManager caching services to reduce the number of Web servers it needs, lowering both equipment and management costs.
One of the major problems companies face in consolidating their many scattered internal LANs and integrating the resulting global network with the Internet is performance degradation. One of the major sources of this degradation is the low bandwidth of the WAN links used to interconnect LAN segments. Another source of performance degradation is the need to pass all information through one or more security firewalls, which can slow information transfer. BorderManager cache services enable companies to create high-performance global enterprise networks without sacrificing security. Because BorderManager Caching Services support open Internet standards, they can be used with Novell's intranet and Internet products as well as with any browsers and web servers in heterogeneous, multivendor environments.
BorderManager Cache Services are based on Internet Cache Protocol (ICP), a next-generation Harvest/Squid proxy cache research, which is fully compatible with first-generation CERN proxy caching. This advanced technology delivers superior performance in an open standards environment that supports HTTP, FTP, SSL, and Gopher protocols. Novell has optimized this technology for the NetWare platform. And NetWare is optimized for the network environment. As a result, its performance surpasses that of application servers, general-purpose operating systems, such as NT and Unix, and other systems. BorderManager Cache Services can handle over 100,000 concurrent connections and over 6,000 connections per second. Using SPECWEB 96, BorderManager cache was rated at over 2,200 operations per second, the fastest, most scalable caching solution available.
With the advanced proxy caching technology employed in BorderManager Cache Services, organizations can achieve up to ten times improvement in performance. By caching data on a LAN-based proxy server, BorderManager Cache Services reduce traffic across the WAN-typically by more than 60 percent. That means organizations can realize 2 1/2 times as much throughput over the same physical WAN connection. As a result, they don't have to purchase expensive, higher bandwidth WAN connections.
Proxy caching is completely transparent to the client. That means users do not have to point their browsers at the BorderManager server to take advantage of caching services. Their request is directed automatically to the proper server. BorderManager also caches information actively, that is, it anticipates the user's movement through Web pages, caching new information before the user actually requests it. Additional caching features further improve performance. For example, a batch download capability allows administrators to schedule downloading of information to nearby caches, such as during off-hours, to minimize network loading.
BorderManager Cache Services support the following three fundamental cache configurations.
Client Acceleration (Standard Proxy Caching). The cache is interposed between clients and the Internet. It intercepts requests from clients for Web pages and supplies the requested pages to the client, if cached, at LAN speed. This eliminates the delay incurred in going to the origin Web site and minimizes the traffic between the corporate network and the Internet. The proxy server makes requests of Web servers on behalf of intranet clients using appropriate protocols such as HTTP, FTP, and Gopher. It caches all Internet objects, including URLs, HTML pages, GIF files, and FTP files, to accelerate subsequent requests to the same object.
Web/FTP Server Acceleration (Reverse Proxy Caching). The BorderManager server front-ends one or more Web or FTP servers and caches all static information belonging to the servers. When a client requests information from a Web or FTP server, the request is diverted to the BorderManager proxy server. The proxy server supplies the cached pages to the client at high speed. Operating in this way, the proxy server greatly accelerates access. It also takes the request load off the Web and FTP servers, enabling the network to service more users with fewer servers. BorderManager Cache Services can provide acceleration for all vendors' Web and FTP servers, in any combination.
Network Acceleration (ICP Hierarchical Caching). In this configuration multiple BorderManager servers are configured in a hierarchical (mesh) topology. When a miss occurs, the proxy cache contacts the other servers in the mesh to determine if any have the requested information cached. If so, the nearest proxy cache with the requested information forwards it to the requesting proxy cache which in turn forwards it to the requesting client. ICP hierarchical caching reduces the WAN traffic load significantly freeing up valuable bandwidth. Because the requested information is sent from the nearest BorderManager server, network delays are minimized.
Policy-Based Administration
Administrators manage all BorderManager services through NDS. They control access through the use of access control list (ACL) rules stored in NDS. The policy rules can be applied to network resources, such as machines, and to users and groups. Control is flexible and includes restriction by protocol, site (URL), category (such as sex and violence), and time of day. Management is easy because administrators work with easy-to-follow, high-level rules and not by individual services.
Access control rules are distributed in NDS and are associated with individual users or groups rather then with machines. As a result, employees "take their access control with them" as they move about the network, always operating from the same access control rules, regardless of where they enter the network. Access control rules are also automatically replicated in NDS throughout the network to provide a high degree of fault tolerance.
The administrator can establish rules for individual NDS objects as well as for NDS containers. Rules are inherited through NDS containment, so the effective rule set is a composite that is built up from rules established for various NDS objects. The rule's position in the list determines its priority of application relative to the other rules in the list. If a lower-priority rule (lower on the list) contradicts a higher-priority rule (higher on the list), the higher-priority rule supersedes the lower-priority one.
The top of the list contains rules defined on the BorderManager server through which the access request is coming. The next level contains the rules set for the BorderManager server's container. From there, the priority works down to the root of the NDS tree. At the bottom of every list is a single default rule that cannot be deleted or modified. This default rule denies access to anything. The administrator can add, delete, cut, copy, and paste rules. In addition, the administrator can change a rule's position in the list to increase or decrease its priority.
Authentication Services
BorderManager Authentication Services (BMAS) combines the remote access security allowed by the Remote Authentication Dial-In User Service (RADIUS) protocol with the ease and convenience of NDS. BMAS enables remote users to log into the network over the Internet using only a single password, and have access to all their network resources, including applications, files, printers, services and other network resources.
Users may authenticate to BorderManager using any of four methods:
Novell IP Gateway. Users can sign-on to the network using the Novell IP Gateway client to provide background authentication to NDS.
Web browser. Users can sign-on to the network from any Web browser. In this case, BorderManager will spawn an HTML or Java sign-on screen when the user attempts to access a protected resource. (The login is performed over an SSL-secured link.)
VPN client. Users can sign-on to the network from a BorderManager VPN client.
BorderManager Authentication Services. Users can sign-on from any dial-in client and enter the network through the RADIUS protocols supported by BorderManager authentication services.
BorderManager authenticates all users through NDS. Users can access all network resources that they are authorized to access regardless of the user's location or the location of the resources, and all with a single sign-on. This means users have to remember only a single user ID and password.
Because BorderManager authenticates all users through NDS, administrators can manage all access from a single, centralized point. This approach simplifies not only the addition of users, but also the deletion of users. For example, an administrator can immediately remove a terminated employee from the network by simply removing that employee's user object from NDS. This eliminates the need for the administrator to remove the user separately from each server or domain, which takes time and is error-prone. This could result in the employee retaining access rights to sensitive information long after he or she is terminated.
Logging, Alerting, and Reporting
BorderManager generates a variety of alerts that can notify the administrator of out-of-tolerance conditions in security, such as loading or unloading of security-sensitive NLMs, Ping flooding, SYN packet flooding, or CPU hogging. It also provides alerts on out-of-tolerance conditions in BorderManager components such as disk space shortage, memory shortage, ECB shortage, license errors, down ICP parent, and down SOCK server. By responding proactively to these alerts, administrators can head off problems before they result in network down time.
BorderManager also logs a wide variety of events, including security events such as attempted unauthorized access to protected network resources. The events to be logged are specified by the administrator. Logging uses standard log and text formats.
By examining the information contained in these logs, either directly or through selective reports, administrators can quickly detect suspicious situations, and react before they result in problems such as the compromise of sensitive information.
Typical BorderManager Deployment Scenarios
BorderManager can provide a wide range of solutions that enable companies to leverage Internet technologies, such as Web and FTP, in their enterprise networks. This section presents typical scenarios that illustrate the power and flexibility of BorderManager. Each scenario below describes:
A particular problem
The deployment of the BorderManager server to provide a solution
The resulting advantages
Scenario 1: Connecting to the Internet
A company needs to connect its corporate network to the Internet to give its employees access to Internet resources such as the Web. It wants to ensure that the connection is secure from Internet hackers (see Figure 1).
Figure 1: BorderManager deployment to provide a solution between the Internet and a corporate intranet.
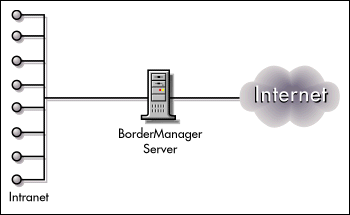
BorderManager Advantages
Strong firewall security. BorderManager packet filter, network address translation, circuit gateways, and application proxies protect the internal network from break-in through the Internet.
High performance. BorderManager forward proxy caching speeds Internet access for internal users.
Control of outgoing Internet access. The BorderManager firewall and the CyberPatrol destination content filter allow the administrator to control outgoing Internet access by employees, restricting access based on a number of factors including site content, user profile, and time of day.
Control of inbound access from the Internet. BorderManager's identity-based authentication allows the administrator to control inbound access to the intranet by users on the Internet.
Complete software solution. BorderManager includes everything you need to connect to the Internet in a single package: a runtime version of the NetWare 5 operating system, routing capability, and remote access.
Scenario 2: Adding Identity-based Control Behind an Existing Firewall
A company already has another vendor's firewall installed but now wants to enhance protection of its intranet. Figure 2 shows the BorderManager server deployment to address this requirement.
Figure 2: Deploying BorderManager to enhance protection of the intranet.
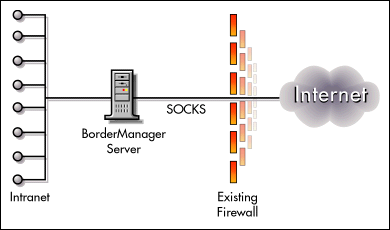
BorderManager Advantages
Identity-based control. Because it performs authentication through NDS, BorderManager permits the administrator to establish identity-based access control to the intranet rather than the address-based control provided by the existing firewall.
High performance. BorderManager forward proxy caching speeds Internet access for internal users and eases the bottleneck at the existing firewall.
Control of outgoing Internet access. The BorderManager firewall and the CyberPatrol destination content filter allow the administrator to control outgoing Internet access by employees on a per user basis.
Scenario 3: Creating Protected Intranet Segments
A company needs to create a protected network segment that will secure certain intranet Web and FTP servers that contain sensitive information such as financial and engineering information. The information on the servers is dynamic and requires frequent update. The servers belong to multiple departments, such as human resources and engineering. The information must be protected from unauthorized access by internal employees as well as from Internet hackers.
The existing firewall protects the servers from Internet hackers. However, it does not protect them from unauthorized access by users who are inside the firewall. In an attempt to protect the servers, the company has placed them in a secure room and uses the security mechanisms provided with the Web and FTP server software. This presents two problems. First, the Web and FTP server security mechanisms do not provide a high level of security. In addition, to update the contents, department personnel must submit the updates to the IT personnel who control the servers and all information posted on them. The procedure complicates the update process considerably and introduces delays. The departments would prefer to have the servers located in their area to facilitate content update.
To solve the problem, the company deploys the BorderManager server between the Internet firewall and the servers to be protected (see Figure 3).
Figure 3: This solution creates a secure network intranet segment.
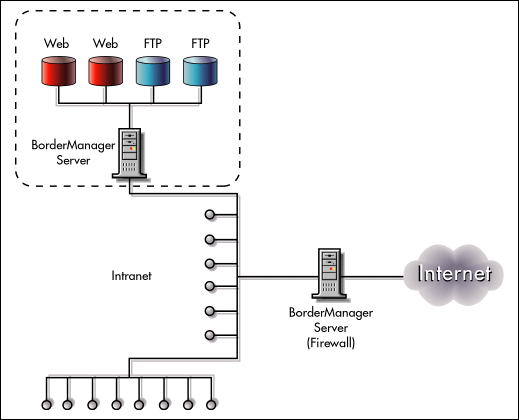
BorderManager Advantages
Strong protection from internal break-in. The BorderManager server protects the network segment from unauthorized access by intruders who are inside the firewall and increases protection from Internet hackers. It accomplishes this through the user identity-based control provided by NDS.
High performance. The BorderManager server's forward proxy cache speeds access to Web pages and FTP files. In addition, the BorderManager server can be configured to provide reverse proxy caching to the Web and FTP servers it front-ends.
Easier management. With BorderManager, the servers can be placed in the responsible departments' areas, enabling department personnel to update the servers directly without IT involvement.
Single sign-on. Authenticating through NDS enables users to use a single sign-on to access all network resources for which they have authorization, including those on secure intranet segments.
Scenario 4: Implementing a Virtual Private Network
A company needs to connect three branch offices located at three separate sites into a single enterprise network using the Internet to provide the inter-site links. (A similar scenario would be that a company wants to implement an extranet that connects its headquarters site with the sites of two business partners.) This scenario is illustrated in Figure 4.
Figure 4: BorderManager VPN clients can be deployed as needed for remote users who need to access critical information over the internet in a secure manner.
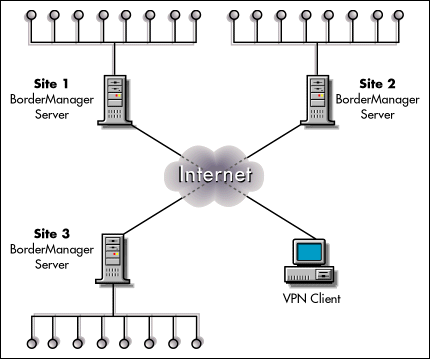
BorderManager Advantages
Strong security. The BorderManager VPN service provides encryption tunneling and authentication to control access and protect the privacy of information transmitted over the Internet.
High performance. BorderManager has a number of features, such as selective encryption, that enhance performance.
Centralized management. The entire VPN network is managed centrally and from the same point as the other BorderManager services.
High level of scalability. BorderManager VPN services can support even the largest corporations with up to 256 sites per tunnel and up to 1,000 dial-in users per server.
Scenario 5: Increasing Web and FTP Server Performance
A company is generating rapidly increasing traffic on its Web and FTP sites. To keep up with the demand, the company needs either to add additional Web and FTP servers or to accelerate its existing servers in some way. Acceleration is the more economical solution because it allows the same number of Web and FTP servers to handle more users, as shown in Figure 5.
Figure 5: A BorderManager server deployed in a reverse proxy caching configuration.
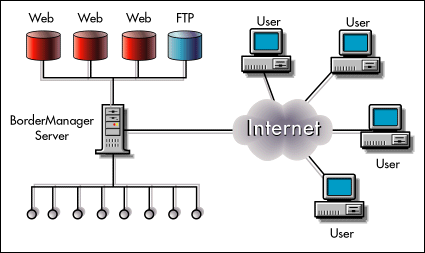
BorderManager Advantages
Increased performance. BorderManager reverse proxy caching can improve Web and FTP server performance up to tenfold.
Lower cost. The BorderManager reverse proxy server takes the request load off the Web and FTP servers, enabling the network to service more users with fewer Web and FTP servers.
Increased security. The BorderManager server isolates the Web and FTP servers from the network, increasing their resistance to unauthorized access, even from inside the firewall.
Simplified management. The administrator can manage security for all Web and FTP servers in a consistent fashion from a single point, regardless of the Web and FTP server platforms used.
Single sign-on. Because BorderManager authenticates through NDS, users can access all front-ended Web and FTP servers with a single sign-on.
Scenario 6: Increasing Intranet Web Server Performance Over Wide Area Networks
A large company has facilities scattered all over the world. The sites have LANs that are all connected through 56 kilobyte per second WAN links. Users in the international offices often access Web servers at the U.S. headquarters to keep updated on company information. Due to the low bandwidth of the WAN links and the large number of links between the user and the Web server, information access can be extremely slow. The solution is shown in Figure 6.
Figure 6: BorderManager servers deployed in the hierarchical proxy caching configurations to increase Web server performance over a WAN.
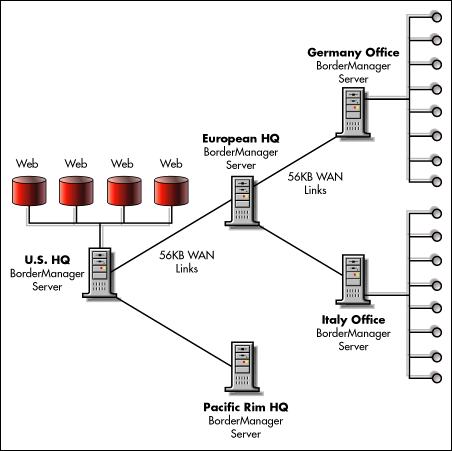
BorderManager Advantages
Increased performance. BorderManager hierarchical proxy caching allows first-time access and cache-miss data to be fetched from the optimal nearby proxy server, without going to the origin Web server. That reduces the number of WAN links between the user and the target Web server, increasing performance.
Lower cost. Because the BorderManager reverse proxy servers takes the request load off the Web servers, a given number of web servers can handle many more users. Because it makes more efficient use of available bandwidth, it reduces the need to add links to handle an increasing user load.
Easier management. All BorderManager servers can be managed from a single, central point simplifying management.
Scenario 7: Providing Universal, Secure Dial-up Access to Remote Users
A company has employees scattered around the world. Many of them are mobile computer users who dial into the Internet through an Internet service provider. They need access through the Internet to network resources that are also scattered around the world. The company wants to ensure that employees can access all the resources they are authorized to use quickly and simply, with a single sign-on (see Figure 7).
Figure 7: BorderManager servers deployed for single sign-on, universal access for remote users.
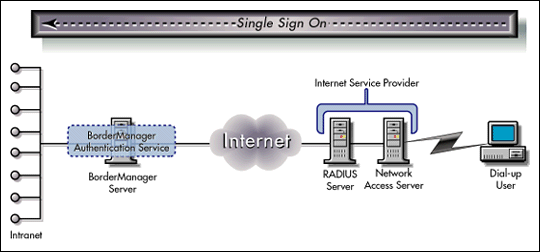
BorderManager Advantages
Single sign-on. BorderManager allows remote, dial-in users to access any resource they are authorized to use with a single sign-on.
Easier management. With BorderManager and NDS, the administrator can manage all remote, dial-in users through a single point of administration. Without it the administrator would have to configure and manage multiple access servers and their associated user databases.
Conclusion
This AppNote has outlined the need for an integrated security services solution such as BorderManager Enterprise Edition 3.0. It has provided an overview of the various components of this product and given several sample implementation scenarios. Future AppNotes on BorderManager will describe these components and installation scenarios in more detail.
* Originally published in Novell AppNotes
Disclaimer
The origin of this information may be internal or external to Novell. While Novell makes all reasonable efforts to verify this information, Novell does not make explicit or implied claims to its validity.