The New Face of Networking
Articles and Tips: article
Chairman and CEO
Novell, Inc.
01 Jan 1998
Novell's new CEO outlines the future of networking and Novell's long-term strategy for delivering the kinds of technologies that people need to run their networks.
- Introduction
- The New Face of the Network
- The Digital Persona
- Solutions for Network Simplification
- Open Solutions Architecture
- Conclusion
Introduction
Editor's Note: This AppNote is adapted from a keynote speech given at the Fall COMDEX trade show in November, 1997. Novell's substantial presence at this show included booths representing all of our key products, programs and services, two full-time Novell Product Solutions Theaters, and the 30 booths of the Novell Partners Solutions Pavilion. In partnership with Compaq and Bay Networks, Novell also debuted Novell Connecting Points, a show-floor intranet that provided e-mail and Internet access to thousands of attendees, powered by an integrated set of top-flight technologies, including Novell's Web-Enabled GroupWise running on the IntranetWare platform, Novell Directory Services (NDS) for security and administration, and Novell's BorderManager managing Internet access. Compaq servers and workstations and Bay Networks hubs and switches ensured reliable connections 24 hours a day. By the end of the show, Novell Connecting Points had carried 5.6 million total messages and processed an average of 1.5 million http server requests and transmitted approximately six gigabytes of data per day--all without any system downtime. The city-sized network was physically assembled within the space of four days, yet was thoroughly reliable and very noticeably fast. Dr. Schmidt began his remarks with an allusion to this network.
When the folks from Softbank asked how long it would take to put together a network of 250,000 users, we replied, "A few days, maybe a week." And we did it, with the help of Compaq. I'm very, very proud of that. The network was able to handle1.85 million messages a day because of what you guys are doing, which I think is incredible.
What I want to do in this hour is take you through all the things that you can do with networking, the promise of networking, and some of the exciting things that are going on in the industry.
Today, Novell has a much more sharpened focus. We're trying to balance new technologies with our existing customer commitments. We're managing the complexity of applications--all the kinds of problems that everybody here deals with, and we're planning with our customers their long-term information technology strategy. We have a renewed focus at Novell to deliver the kind of technologies that people need to run their networks. That's what we're all about.
The New Face of the Network
My talk is about the new face of the network. This new face is not an interface nor is it even a single face. The new face of networking has a human face; it has as many faces as there are users on the network today.
The Speed of Mind
In everything we've done over the last 15 years, we've been governed by Moore's Law. While it's been a good law for all of us, we're now moving to a situation where we're governing much more by the speed of light. But I think the ultimate constraint is the speed of people's minds. It's the ability of organizations to deal with the complexity and creativity that networks bring to them. Solving that problem turns out to be the most important thing we can do, and we need adaptive systems that can work with this set of problems.
The industry we're in is young and it moves fast. We deal with time compression and globalization, and we're very proud of what we have accomplished. But we're seeing a declining significance of Moore's Law, and an increasing significance of the problems that I'm going to highlight. They ultimately become the barrier to progress. In other words, the scarcity here is of time: time of the person, time of the customer, time to change these new models.
How big is this? There's a lot of interesting statistics. For instance, the size of the web: there are roughly 71.3 million web users right now, according to IDC [International Data Corporation], and 130 million are expected by the year 2000. The compound growth rate of these things yields tremendous numbers. We've often said that at the current growth rate, every human on the planet would have their own web site by the year 2004. If you look at the number of trade shows we have to go to, every human will have their own trade show by the year 2004. It just goes on and on.
Shift from Static to Dynamic
There's an underlying transition here from static to dynamic, and that shift is something that underpins almost everything we do. It's not obvious until you begin to think about its implications, because the Internet and networking technology are bringing forth a whole new set of mediums.
There are several examples of what computers can do that really couldn't be done before. One is creative pattern matching. They can watch what you do, figure out what you want, and suggest the next thing. For instance:
Amazon.com, one of the services that I use on the 'Net, now remembers what books you have bought and then makes a suggestion, based on a perception algorithm, for books that you might want to buy. When was the last time your bookstore did that for you?
American Airlines has a program that, for a certain category of customers who buy through electronic means, can give you instantaneous price updates so that you can absolutely know the marginal price of that middle seat that you didn't want anyway.
We see computers being used not just as substitutes for the physical world we're used to, but in a very different way. This whole thing is governed by a set of laws around network effects. If you look back, we can see network effects that were a surprise to us 20 years ago. Most of us spend much of our time traveling around and dealing with the United States airline industry and their hub cities. When the airline industry was deregulated, what was the competitiveness equation? Of course, it was the domination of hubs. That's the network effect. The more people you can get into one hub, the more you can make sure they stay in your network.
Increasing Returns
The same principle applies to what we do. Technology adoption is driven by laws of increasing returns. When the first fax machine came out, it wasn't very useful. But when lots of people had them, all of a sudden everyone else had to have them. When the first cellular phone came out, the same pattern unfolded.
These mass waves, driven by brands and people, are often confused by how absolutely crazy these markets are. One year you're a failure, the next year you're a billionaire. It happens all the time. You announce a new product, and in a week you have a million customers, and then you go public. You have to get the revenue later; ubiquity first, revenue later. That's what URL stands for.
My essential thesis here is that there are two intertwining issues:
The human face of networking is interactive and changing--the network is intelligent, and it knows you.
The adoption of technology is driven by increasing returns.
These two issues together make our world extraordinarily dynamic and fascinating, as well as very competitive.
The World of Me
If you follow the new face of networking idea, every face is different, and everyone's needs for networks are different. Every person on the network has a different perspective. The world of needs is really about millions of new faces coming onto the Internet.
Networks are empowering. When people think about computers, they really think about themselves and what they can achieve. This technology and the industry that it is making is an incredibly personal one. Ultimately it's driven by the desire for intrinsic recognition that we all have. We're busy building this world that consists of cyberspace replicas of our physical space. It shouldn't surprise you that there are both saints and criminals on the net. You have to have churches where you can pray for support on the 'Net. There are even banks to put your money in. It makes sense that we're building all these new models.
The CIO Challenge. In the middle of this, we have the chief information officer (CIO), who has enormous challenges. In my new role as CEO of Novell, I've spent a lot of time talking to these people. The problem they have is that they more or less had it wired 10 years ago when they understood what everybody was doing. But things are different now.
For example, consider a software distribution company. Before, product went first to a distributor, then to a CIO, and finally to the user. What happens now is the user goes directly to the software manufacturer, using the Internet. You say, "No big deal; I do that all the time." The problem is serious, at least from a corporate perspective, because of the support, asset management, legal use, and most importantly, security issues. You need a solution that works politically within the organization. The end-user has to feel empowered, but the CIO has to be able to set up a framework.
Now, the CIO says, "What I really want is a network where I have a command central, a place where I have asset management, software distribution, bandwidth managing, web access, security policies, and so on" (see Figure 1).
Figure 1: The CIO view of the network.
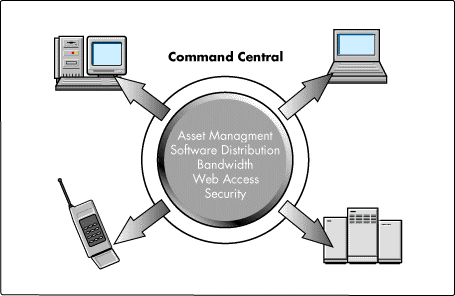
The end users, however, have a very different view. They want it all now, they want to make it happen; it's the world of me.
The correct way to think about this is that the services will evolve so the end user will have permission granted through a set of directory-enabled solutions that allow her to get access to the things she cares about. The CIO won't stand in the way; he'll make that happen. The CIO must embrace a view of the network which enables that. The key strategies are to use directory-enabled services to make the solutions available, and then give the CIOs and the end users the power to make the choice.
The Data Explosion
At the same time, there's an enormous data explosion going on. The World Wide Web, HTTP, Java, and other technologies have made it easy to publish any kind of data and deliver it to the world. Web traffic is increasing by roughly 30 percent every three months. Currently, that traffic is approximately 31 terabytes per month, with the expectation that it will grow by at least a factor of 100. I looked that up: it's 3 teta bytes (which is a really big number) per month.
Because of the latency inside of organizations, you should expect to see really innovative things first on the web; then, because of end-user demand, they will move into corporations, and so forth. The web is a tremendous cauldron of innovation which has awakened us from the networking conundrum we've all been in for so long.
With the interaction in the world of needs, there's an issue around being close to things. When you build these data networks, the most important issue is to have perceived proximity. You absolutely must have the data close to you. The technical solution for that is called replication. By replicating caches and making all that stuff work, the network recognizes a person's identity and knows who you are.
The architecture that underlies these networks is built on a set of caches ("cache" in the sense of a place where you keep a local copy) and complex algorithms to keep the caches up to date. We all know that the computer performance and the demand from end users is outstripping the ability for enterprises to deploy the bandwidth they need. Combining the two makes a great deal of sense.
As an aside, we have a Border Manager product which handles approximately 50,000 concurrent connections and 5,000 pages per second, to do caching and proxy analysis. The equivalent NT and Unix versions are 1/10th of those. That's an example of a sweet spot that you can find when you look around on these networks at all of these different devices.
Network Evolution
We find ourselves living in a world that's very different from what we thought. I first thought we would have a series of tiers: first tier, second tier, and so on. In fact, the ISPs [Internet Service Providers] that we so much depend on are interconnecting, which is great. By doing so, they're building a whole new network (see Figure 2).
Figure 2: Moving from a multi-tiered to a one-hop world.
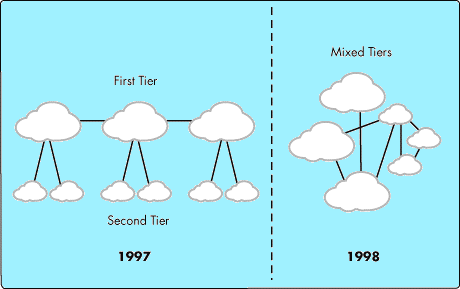
The TCP/IP technology, which is suited for voice, is becoming the basis for the world's data networks. Although today the percentage of voice and data are roughly equal, some analysts expect that in the next seven years the percentage of data versus voice will shift to about 99 percent data and 1 percent voice. That gives you an idea of how significant this change is.
This matters to us because we live in a deregulated world. It's an example of an inversion. Just when you thought you understood exactly how everything would be priced, all of a sudden we have an opportunity to change it again. I don't know how that will change it, but I know it will affect a $650 billion industry.
Reed Hundt, a friend of mine and former FCC Chairman, said, "What we need is a high-speech, congestion-free, always reliable, friction-free, packet-switched, big bandwidth, data friendly network that is universally available, competitively priced, and capable of driving our economy to new heights." Put another way, what we need is a data network that can easily carry voice instead of what we have today, which is a voice network struggling to carry data. That makes sense to me. And, by the way, we're building it together.
Yesterday, AT&T announced WorldNet, a virtual private network service, with a business-quality IP offering and end-to-end service guarantee. It enables remote access to LANs, extranets, and intranets. It brings down a huge complexity barrier for all of us as customers, and it uses a protocol called RADIUS to authenticate into a directory, which happens to be Novell Directory Services (NDS).
The IP Tornado
There is a tornado happening, which is this change resulting from the adoption of IP (see Figure 3). I've talked about this before, calling it an intelligent network. This is a replacement-- the subnet that you've built for so many years in that model will be replaced by interconnected TCP/IP networks.
Figure 3: The widespread adoption of TCP/IP is bringing sweeping changes.

For us at Novell, the next version of NetWare [code-named Moab] is the key part of our strategy, because that version uses IP completely natively. All of the best-of-class services you know and love will be available on these open, interconnected networks, with extraordinary performance--much higher performance than any of the other competitors in those spaces. That's the commitment Novell has made, and Moab is available in beta today.
Just saying TCP/IP, which appears to be a mantra in our industry, is not sufficient. In a situation of open interoperability where everybody has the same stuff, how do you differentiate? What's important is that you have the base of TCP/IP and then all of these services, which run on top. The enabled services turn out to be the real differentiator. In our case, it would be to make this tornado be worth something to your business. Don't be afraid of the destruction that the tornado means. Ultimately, it's a much better model.
Shades of Gray
The other issue that people are struggling with is a set of border or firewall issues. As people are building these networks, there are huge issues around security and access and those kinds of things. The original model that we pushed three or four years ago was that there was the intranet, where the good guys are; and the Internet, where the bad guys are; and between them is the firewall, which is like "Dr. No" saying no to everything.
The problem with that is it was an extraordinarily inflexible architecture; it was not the correct technical approach. What you really need instead of just "no" is about 45 shades of gray. Our customers are trying very hard to interconnect your customers and your suppliers with different levels of service. You're going to deal differently with your customers and your partners than with your competitors, but you may even collaborate some with your competitors. You need this different approach. The point here is that security should be a business decision for you.
After we announced BorderManager, IDG said, "With initiatives like BorderManager, Novell is, for the first time, truly repositioning its core competencies strongly within the Internet space." We have an opportunity here to drive a very different and powerful IP model. The Internet service providers have all the border, caching, security and naming issues that I'm describing. A combination of solving the ISP, caching, access and security problems turns out to be a huge "sweet spot" for all of us to drive right through. I'm mixing metaphors, but you get the idea.
Thin Is In
We've heard a lot about thin clients, and they're a lot of fun. There's this thin client and that thin client, and there's not-so-thin clients. And then there's the fat client. I bet you didn't know you had a lot of fat clients when you bought them.
If you take a look, thin clients are actually happening. Over the next few years, people expect to build a lot of non-PC devices (see Figure 4).
Figure 4: A wide array of thin clients.
It's very clear to me that one size no longer fits all. But I don't think it's going to be either/or; it's clearly going to be a mix. You want the promise of a network computer, for a lot of the reasons that we've talked about, but you also want to use your existing investments.
NC Your PC. Perhaps a better approach is to "NC your PC." In order to do that, there's a set of services you need; in particular, you need a directory service that can keep information and hold the statistics somewhere else than in your fat client. By moving the complexity from the PC client onto the network, you can pull that off. From our perspective, NetWare is the perfect model to do this. It has the dedicated performance and the scalability to handle many different devices and the right platform for directory-level kinds of things.
What's happening in this whole initiative is that people are beginning to develop applications. To me, this is incredibly important. The whole Java phenomenon (I'll talk about that in a few minutes) is creating a new sort of network architecture. These are applications which are a little different from what we use today: distributed by design, multi-user by need, geographically dispersed by necessity. They derive value from using a thin client, and they often include workflow.
Look at the players in the industry pushing this initiative. Oracle has something called NCA, which is really data in the network. Sun calls it Java Computing. Netscape calls it Netscape ONE, really web computing. IBM calls it the "Open Blueprints," also network computing. Novell calls it an Open Solutions Architecture. Microsoft has named Oracle, Sun, Netscape, IBM, and Novell the Gang of Five, and feels it's a conspiracy. I'd prefer to think of it as being right.
Total Cost of PC Ownership. This initiative around building these new categories of applications is one that all of us can participate in. It does match the model that our customers--and everyone's customers--are really striving for, this year-2000 kind of model.
For example, you've heard cost of ownership arguments for years, and they never seem to get solved. We've been analyzing PC ownership, and it turns out that the majority of the cost of PC ownership is in managing them (see Figure 5).
Figure 5: Total cost of PC ownership.
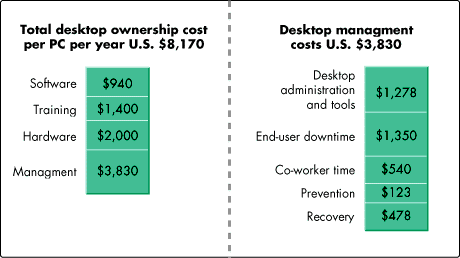
You might say, "Well, just don't manage them." That may be an option for folks in this room who are very sophisticated, but it isn't a rational option for most corporations. A better solution is to leverage the power of the network and the digital persona.
The Digital Persona
What makes up your identity is your relationship to things. You have a place in the hierarchy. You're identified by your company, your geography, your department, and yourself as an individual. You can interact with things in the network world differently, depending on which department you are in. I know this is obvious to us as humans, but it is not to our computers. Our computers are authenticated to the machine, not to the person. The solutions that we are building are based on this notion of the digital persona.
As part of this digital persona, you have certain "inalienable rights" when you are set up on the network. From the technology perspective, you get access to services, you get through routers, you have modem banks, these kinds of things. The important point is that, using the technologies I'm describing, you can authenticate to the person. And you can end up in a situation where the network knows you.
Demo: A Day in the Life . . .
Start thinking about what happens when a new person joins your organization. What is their life like? Typically, the person needs the following:
Desktop applications
E-mail
File server access
Ability to print
Network applications (Oracle, IIS, and so on)
Ability to be mobile (dial-in, web access of e-mail, workstation independence, and so on)
Document management
Corporate information directory access
I want to demonstrate how this scenario might work when the network knows you. I'd like to ask three people who work at Novell--Kent Prows, J.D. Marymee, and Gary Hein--to join me on stage.
Kent: The demonstration we've put together is deceptively simple and yet extremely powerful. We're going to take two perspectives of this technology: one from the administrator, played by J.D.; the second from the user, played by Gary. The idea we want to portray is of a digital persona, and that with a single user we can expose this digital persona. We decided to create a new CEO inside of Novell.
In this world, you've got all of these different technologies: You've got e-mail, you've got database actions, you've got file imprints, you've got groupware, you've got application management, you've got software distribution, you've got all of these things. J.D., from the administrator's perspective, what's it like to manage all this stuff?
J.D.: As an administrator, I'm responsible for thousands of workstations in hundreds of different sites, and I'm constantly trying to integrate new technologies into our existing systems with our existing infrastructure. Making all these systems work together as a solution is usually very difficult. Adding a new user to our company used to require coordination between half a dozen network administrators, each of whom was responsible for a piece of the complete enterprise solution.
Now I've got all these issues distilled down to a single user create. We're going to create the new CEO now, or expose his digital persona. I have one template that's going to create everything, including the ability to access e-mail over the web. I'm going to put a password in for that, so it's at least somewhat secure over the Internet.
Eric: You're setting up this digital persona in the entire enterprise network?
J.D.: Yes, I am. I've actually got him set up with access to his workstation, access to e-mail, access to the Internet (or limited access to the Internet, depending on how I want to govern that), access to the Netscape enterprise web server, even access to file and print services, both on NT and on NetWare.
Kent: Let's come over to our new CEO, played by Gary. Gary, how does this affect you?
Gary: I'm a CEO, not really a computer geek--well, maybe I am a little bit. But I really don't care about operating systems and protocols. I just need to have applications on a desktop to do my job. I want to come to Novell my first day at work, log in one time, and have access to all the resources I need to do my job, regardless of what platforms those happen to be hosted on.
Kent: J.D. created your account over there. You've got an NT workstation that's got the network client loaded. Why don't you log in and let's see what happens?
Gary: It looks like I got into my NT workstation, got to the desktop, and it's starting to pull down some information. What's happening here?
Kent: J.D., from your perspective, what did you do to the CEO?
J.D.: NT Workstation is a secure desktop, which means the user has got to have a password before accessing the workstation. I've provided a single sign-on to the NT workstation by creating a user in NDS and granting the user rights to his desktop. This saved me, the administrator, the work of manually creating the workstation account on that particular machine. The benefit to the user is that he didn't need a second password to get into that system.
Before the user can start to do his job, though, he needs applications on his desktop. The Directory knows who the user is, and we're using this information to install and configure the software he needs to do his job.
Kent: Wow, it looks like everything came down, even the new corporate bitmap. I know you're the CEO, but I doubt even you can change this bitmap.
Gary: Oh yeah, I know NT; it's easy for me to change this. I just click on properties, and I can change . . . hmmm, nothing, really.
Kent: I guess we know who really controls all this stuff!
Gary: What happened? I don't understand.
J.D.: Because you're known in the directory, we can actually configure applications on your desktop and everything with information from your digital persona that is stored in the directory.
Kent: It looks like your Netscape Communicator was downloaded there. Start that up and let's see what kind of work you can do.
Gary: Before I do that, I really need some more applications down on my desktop. We just purchased a lot of licenses for some productivity applications, so I'm going to ask my administrator, J.D., to set up some more applications on my desktop for me.
J.D.: We're going to add a couple of applications here for this user. Anybody who happens to be in that part of the tree will also get access to these applications. With just a couple of clicks, I can deliver availability for Access, Powerpoint, Word, and other applications down to the user's platform.
Gary: Before I can do any work, I need to customize my computer and my applications so they understand my identity or persona. What I'd like to do is configure my preferences in Netscape Communicator with my information. Hey, it looks like it's already there: my name and e-mail address are in there. How did that happen? This application isn't necessarily NDS-aware.
J.D.: Remember that as we bring this information down, we go and read your digital persona. We can customize any application as it's distributed to the desktop to match your exact needs.
Gary: Great! Now, I hear we have a little issue with employees spending a lot of time out on the web. I've asked my administrator to make sure that this doesn't happen any longer. So I'm going to see if he's actually doing his job. I'll just browse over to Playboy, you know, just for the articles. Hey, wait a minute, it looks like I couldn't get in for some reason. I used to be able to get in . . . I mean, users used to be able to get in here.
Kent: J.D., please explain to the new CEO how this happened.
J.D.: BorderManager makes it simple to do that kind of Internet access management. I just created a couple of rules that control access to content on the web, such as non-productive sites like the one that Gary just tried. Once again, the Directory manages who these rules affect.
Now, Gary, instead of you sitting around browsing the web, let me give you a URL for the new online real-time sales database. Since you're now a user in the e-mail system as well, I can e-mail this to you. We'll just say "new URL: sales.novell.com."
Gary: I spend a lot of time on the road, and I'd like to access my e-mail anywhere. I don't always have a connection to the phone system, believe it or not, but I will always have a connection to the Internet. I'm going to log in and access my e-mail right from my web browser.
J.D.: The URL that I sent Gary points to an application running on a Netscape Enterprise Server running on Novell's NetWare, produced by Novonyx. This application is running server-side Java script that natively connects to our Oracle sales database.
Gary: As I go to the URL, it looks like the front-end to our new Oracle database. I'd like to check sales for a couple of the different regions. It looks like North America is a little bit behind their quota. So I want to check on which of our sales reps is in the North America region, and how close they are to their quota.
What's basically happened at this point is I've used a standard web browser, talked to my Netscape Suite Spot server that's running a Java server-side scripting that talks natively to the Oracle database, posted on the IntraNetWare server. I can go through and browse the sales figures from any web browser anywhere in the world.
This is wonderful . . . everything I need to do my job happened the very first day.
Kent: J.D., I noticed that one of the requirements we've put up there was access to Windows NT. I was just wondering, how did you achieve that access?
J.D.: When I created the user account in NDS, I gave Gary access to an NT domain. I can manage the domain information now using NDS for NT. For example, let's add access in another domain. To add Gary into another domain, it's just a matter of choosing the domain I'm interested in. In this case, we'll go into the Seattle domain. That's how simple it is to manage user access to NT domains now using NDS for NT.
Kent: To summarize, the challenges we face with daily are from both the users' and the administrators' perspectives. Users need access to applications. They need database access, and also file and print services, to do their jobs. Users also have groupware and e-mail needs, as well as access to the Internet. Administrators need to be able to manage the desktop and control access to the Internet. We've demonstrated that when a user is created, this digital persona is also created. Based on the information you put into the Directory, the Directory manages that relationship and provides you with the ability to get access to the information you need.
This may be quite a departure from what many of you think Novell is doing. The important message about that demo is that these products are all shipping, except for the Netscape web server from our subsidiary called Novonyx. That product ships in beta in November and is downloadable from the Internet at www.novonyx.com.
Solutions for Network Simplification
There's a much broader story about what we can do. The current sorry state of our networks could be represented by a human face wrapped up in wires (see Figure 6). It's enormously complicated. The average number of directories that a person in a Fortune 500 company is in is about 120.
Figure 6: The current sorry state of networks.
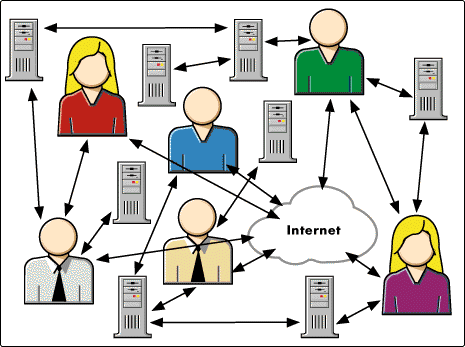
At Novell we have a solution for all of this. We have distributed network services in the mid-tier--that's what the Moab and NetWare stuff is all about; a platform for management of these services--that's NDS, our ManageWise product, etc.; and a new and renewed attractiveness to the developer community. People are doing user account management, desktop and network management, collaboration, and application management--all of which are made possible through this model.
The Directory simplifies networking because of one of the most fundamental principles in computer science. That is, every problem can be solved by one level of indirection (see Figure 7).
Figure 7: One level of indirection.
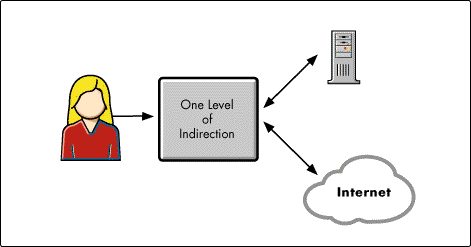
We've essentially taken all of the complexity you all deal with every day and put it in a place, which is the network. It's intelligent, it's replicated, it's cached, and it's an area where we have a significant competitive lead. The Aberdeen Group wrote that "NDS for NT, the same product running on NT, even obviates the need for Microsoft's Active Directory." That is good, because Active Directory doesn't exist yet.
Management and Cost Control
What you saw in the demo is the principle we call application redirection. The old-timers here know that Novell made a name for itself because of DOS file redirection--a unique skill within the company. Now, by bringing out a set of libraries and services that are protocol-compatible with everybody else, we can take all the applications you use and have all this happen without user or systems administrator intervention. That second phase is a huge change in the way we all use networks (see Figure 8).
Figure 8: Application reduction evolution.
By delivering this common access management security framework, you don't have to rewrite your applications. You get all sorts of other benefits, too: shared data, less hardware, everything's more secure. The total cost of ownership solutions are incredible. I think it's intuitively obvious how strong that stuff really is. By the way, we're going to do it for NetWare, for NT, and also for UNIX. We've got white paper after white paper from the marketing folks giving you all the information about it. [Visit www.novell.com for more information about Novell's products and technologies.]
Java on the Server
Java is also part of our strategy, for obvious reasons. Java today is a huge success. There have been more than 1.1 million downloads of the JDK 1.1. IDC says there are now 450,000 Java programmers, with 700,000 projected for 1998. There are 800 books, showing where the real revenue is. There are 400,000 web sites using Java, and more than 1,000 Java applications shipping. The Java-One conference in March had approximately 10,000 attendees. For a language that is only two years old, this represents is a very significant phenomenon.
To date, 87 percent of the Java application development has been on the client. That's where all the lawsuits and battles are really being fought over who controls what and who has which library. But people are missing the real story behind this. The real opportunity for Java will be when it's implemented on the server. Remember, there's that middle tier that, by its very nature, is not dominated by any single monopoly. There are lots of different choices, and they're not going to go away. The middle tier is where server-side Java will take off. We call this the intelligence in the middle. It's very powerful. Server-side Java plays to one of Java's strongest suits, which is platform independence, as well as faster performance and portability of applications. It has the right architecture to build these new network-aware applications. That's why server-side Java is a core part of our strategy (see Figure 9).
Figure 9: Mission-critical Java.
Java on the server will be platform-independent, whereas the client depends a lot on things like how the litigation plays. The technical issues will be fixed independently of the battles between Sun and Microsoft. It's incredibly important that the APIs in the industry not get split. If you read sections 2.6 and 2.8 of the Java contract, you can form your own opinion about what 117 licensees have all agreed to do.
Java is more than a dancing bear on your web site. It's really the language of electronic commerce. The Java language will eventually replace C and C++, and the 100 million JVMs [Java Virtual Machines] that are out there really are an enormous asset for universities, new language development, and things like that. Key computer and software companies--companies like Novell--are going to build new dedicated platforms that use Java to provide new value. Those dedicated platforms will eventually become major platform players in our industry. It will take a while because of applications and robustness and things like that. But a key part of this value proposition is Java breaking into the mainstream with the server components and an incredibly scalable JVM on the server--in our case, one that is probably going to be higher in performance than its competitors.
Open Solutions Architecture
To put all this into perspective, we've got an architecture that solves the final piece of the problem. If you take a look at the architectures that I mentioned earlier, they tend to be specific to clients or applications categories (see Figure 10).
Figure 10: Other vendors' architectures.
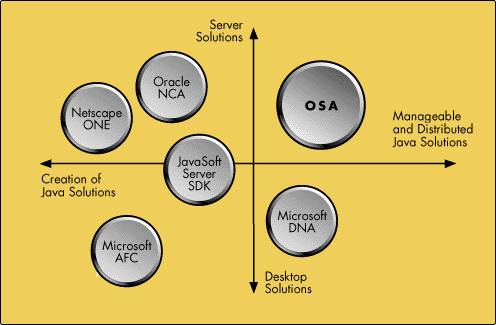
These are all important, but they're missing the component that provides them the manageability and the distributed Java solutions. By bringing out something we call the Open Solutions Architecture (OSA), Novell can deliver, better than anyone else, the back end of the services that make this whole value proposition happen. The key is to build an infrastructure that is targeting networks, developers, and ISPs. Then we can provide the complete management infrastructure on top of them and make the rest of this stuff work (see Figure 11).
Figure 11: Novell's proposed infrastructure.
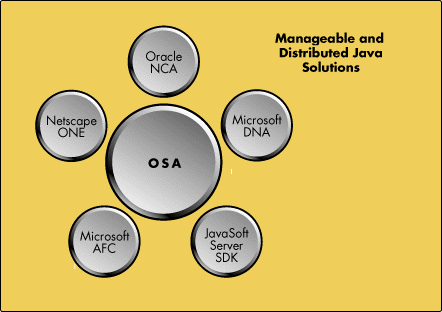
We are building all of the pieces. Figure 12 is a diagram showing each of the different layers in the OSA.
Figure 12: The Open Solutions Architecture.
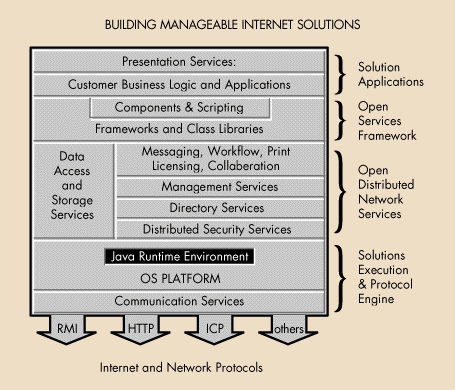
I know that's a busy slide. The important thing is that this architecture is based on the principles of the Internet. Each of the sets of interfaces is open; anybody can adopt them. In most cases, they're already industry standard, and, in those others, we will work with the appropriate partners. By doing so, we have a strong commitment to open interfaces on the server side--which, again, is where the action is going to be--to build these business-critical applications across the 'Net.
Waypoints to the Networked Age
How do you know how you're doing against this broad panoply of choices and direction that I've laid out? Here is a list of the waypoints or progress points to the network age:
Everyone on e-mail and document management systems
Many internal web-enabled processes
Security policy in place
Bandwidth managed in chaotic user base
A Directory you can use
All applications leverage the Directory
Desktop asset and software management centralized
Public network used for private business
Most customers struggle with getting all this deployed. This is ground zero in the networking industry today. These are the things that are on everyone's short-term time horizon. Getting these things implemented is the next stage.
Novell's Strategy
Novell has solutions in each of these cases (see Figure 13).
Figure 13: Novell strategy.
I am fortunate to be involved with a company where most people in the industry are already customers. We begin by saying, "You're probably already a network customer, and NetWare is going to be completely TCP/IP capable in the next six to nine months." And everybody says, "That's a good idea."
Along the way, we're deploying this Directory called NDS. Many customers are aware that there's a Directory, but they don't understand what it's good for. They use it for, say, sign-on. But once you have this Directory, you're enabled in all sorts of the ways that I described. By having the Directory-enabled applications that I described and others that we will be announcing on a monthly basis over the next six months, we can deliver network-centric applications. The progress for our ManageWise business and our GroupWise business is all part of that. The BorderManager products are all integrated with that.
Because we do dedicated kernels and because we do networking software that does networking and nothing else, our products are more scalable, more reliable, and more available. All of those abilities make sense if you have a best-of-breed approach.
That story is sufficient to grow Novell's business, to restore its leadership position in key parts of the networking industry. But there's a twist, and the twist is Java. By adding the ability to run these Java applications that I highlighted briefly for you, we can actually become a significant need to your server vendor as well.
Taking the Lead
In taking the lead, we as a company are going through several phases (see Figure 14).
Figure 14: Stabilize, drive, and thrive.
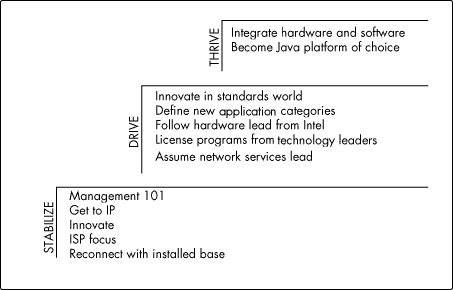
The first phase--think of it as a stabilize phase--is a learn-how-to phase; things like Management 101, deliver products on time, solve your customers problems of one kind or another. That phase probably goes on for another six to nine months until this next generation of products is shipping and customers are excited about them.
Then comes an opportunity to drive. This part is focusing on innovation in the standards world, driving new applications categories along the lines that I described, and really driving the network services-ISP integration. There's enormous growth in those markets.
Once we deliver on that, it's possible to get to this interesting ultimate destination, with the opportunity to thrive. This destination is very much Java-based, and I think it will take a couple of years for it all to happen. To the degree that leadership is inventing the future, Novell will lead and others will follow in this new world.
Conclusion
In conclusion, I want to go back to my earlier theme, which is that the new face of networking has a human face. It has your face and my face on it. I've taken you through a clear understanding of where networking and Novell are going and what our product portfolio looks like. We will win because we have a product strategy in place that will reconcile the drive towards this new face of networking with the reality that many of you deal with. We are one of the companies on the verge of one of the most exciting new areas of network computing. Network computing is the interesting thing to be doing. I'm glad to be part of it, and I want to thank you all for being part of it too.
* Originally published in Novell AppNotes
Disclaimer
The origin of this information may be internal or external to Novell. While Novell makes all reasonable efforts to verify this information, Novell does not make explicit or implied claims to its validity.