Setting Up a "Change Password Administrator" in NetWare 4
Articles and Tips: article
Software Engineer
Novell Developer Relations
01 Sep 1997
Resetting passwords for forgetful users is a common administrative chore. Now there's a way to let your support staff change passwords without giving them the keys to the entire NDS castle. This AppNote shows you how!
- Introduction
- How the Change Password Service Works
- Installing the Change Password Service
- Using the Change Password Service
- Change Password Service Availability
Introduction
A common question asked concerning access rights within Novell Directory Services is, "How can I set up a user to be able to just change passwords, without giving the user full administrative authority?" The answer is "This feature is currently not available." To allow a user to change passwords would normally involve giving the user write permission to All Properties on a container object and letting that permission flow down to the users with the container. Unfortunately, this gives the privileged user the power to add Access Control List (ACL) values to the contained users, or to any other object beneath the container. With the power to add ACL values to objects, the user could make himself or herself a supervisor of an object and hence have full administrative authority.
In the August 1996 issue of Novell Developer Notes, I outlined a system whereby the system administrator could delegate the authority to change passwords to pseudo-administrators. These pseudo-administrators would send requests to a NetWare Loadable Module (NLM); after verifying that the sender is authorised to make the request, the NLM then acts on the pseudo-administrator's behalf.
In addition to delegating authority to pseudo-administrators to change passwords, the administrator would want to be able to block pseudo-administrators from changing the password of key personnel, such as the administrator account. Any practical system should be able to incorporate exclusion lists to protect key accounts. The system should also be able to implement a hierarchy of pseudo-administrators, whereby senior accounts can only be modified by senior pseudo-administrators.
The Change Password Service (CPS) described in this AppNote is an implementation of the outline given in Developer Notes. It can be used to delegate authority to change passwords without giving any additional rights in the NDS tree. The system also incorporates the hierarchy described above and uses the NetWare Administrator tool for configuration and use. (Throughout this AppNote, "NWAdmin" will be used to refer to either of the 32-bit versions of the utility: NWADMN95 and NWADMNNT.)
How the Change Password Service Works
The Change Password Service is a collection of files that includes a custom-written NLM called CHPASSWD.NLM. Configuration and administration of the CPS system is performed through an extended NDS schema class called Change Password Administrator (CPA).
|
Note: This is the class name when viewed in the NWAdmin utility. The actual schemaclass name is OZDEVNET:PWAdminGroup. |
Objects of this class are used to record the following:
A list of pseudo-administrators
Excluded users and containers
The host server running CHPASSWD.NLM
Access rights to the NDS tree
The class schema also incorporates public/private key attributes and a password attribute. These attributes allow a CPA object to authenticate as an NDS object and modify the tree according to the ACL rights assigned to the object. The NDS schema for the class is shown in Figure 1, where names in italics are inherited from the base class.
Figure 1:NDS schema for the Change Password Administrator base class.
Name: OZDEVNET:PWAdminGroup Base class: Group Containment classes: Organization, Organization Unit Naming attributes: CN Mandatory attributes: CN, Object Class Optional attributes: Member, Lists pseudo-administrators Public Key, Private Key, Authentication keys Host Server, Distinguished name of host server OZDEVNET:PWExemptions, Lists protected accounts OZDEVNET:PWPassword Auto-authentication password
Change Password Administrator objects are created using the NetWare Administrator (NWAdmin) utility. Since the schema specification for the CPA class is based on the Group class, a CPA object can be created under Organization and Organizational Unit objects. When a CPA object is created, NWAdmin adds an ACL value to the container, giving the CPA object read/write access to All Properties. These rights are sufficient for CPA objects to modify the password of a user in the container or any sub-containers of the container.
The list of pseudo-administrators, excluded users and containers, and the CPA's password are set using NWAdmin. Since the CPA object has extensive rights to the container, it is suggested that a password be assigned to the object immediately. The password can be recorded in an encoded string within the CPA object to allow the CPS NLM to auto-authenticate as the CPA object on loading. (The process of NLM authentication is described in more detail later.)
To modify a user's password, a pseudo-administrator uses a new dialogue page added to the User Details dialogue box of NWAdmin. The dialogue page has a field to specify the CPA object to be used to "vouch" for the pseudo-administrator's authority to request the modification. The password request is sent to the host server of the CPA object. The CHPASSWD.NLM program running on the host server can then determine whether the CPA object does list the originator as a pseudo-administrator and that the user is not on the CPA object's exclusion list.
Communication between NWAdmin and CHPASSWD.NLM uses the NetWare Core Protocol (NCP) Extension interface. On loading, CHPASSWD.NLM registers an NCP extension which can then be used by the NWAdmin client to send NCP requests. The NLM can then interpret the request and send a reply to the client.
To avoid sending the password across the network inside an NCP Extension packet, CHPASSWD.NLM and the NWAdmin client use a common password. CHPASSWD.NLM sets the password to the common password, and the NWAdmin client changes the password to that specified by the user. This last step is possible since the client can supply the common password with the new password to server when requesting the change. Under this scheme, the password is transmitted from the client to the server within Novell's security system.
While NLMs have implicit supervisor access to the server file system, they do not have administrator rights to the NDS tree unless the NLM explicitly authenticates as an administrator object. For an NLM to be able to modify a user's password, the NLM must be authenticated as an NDS object with appropriate access rights. CHPASSWD.NLM authenticates as the CPA object it is hosting. Since the CPA object has read/write access to All Properties in the container, the NLM will have sufficient rights to reset passwords.
The CPA object's password can either be entered at the server console when CHPASSWD.NLM loads, or it can be encoded as a property of the CPA object. If the password is encoded, the NLM can auto-authenticate by reading the encrypted password, decoding the password, and then authenticating. By using auto-authentication it is possible to load CHPASSWD.NLM from within NCF files such as AUTOEXEC.NCF.
Installing the Change Password Service
The Change Password Service software consists of seven files, listed below:
CHPASSWD.DLL (NWAdmin snap-in library)
CHPASSWD.HLP (Help file for NWAdmin snap-in)
CHPASSWD.REG (Registry registration file)
CHPASSWD.NLM (Change Password Service NLM)
SNAPIN32.DLL (NWAdmin service library)
CW3230.DLL (Borland runtime library)
DESCHEMA.EXE (Removes CPS schema modifications)
To install CPS, do the following:
Copy the DLL and help files to a search directory in the pseudo-administrator's path.
Copy the CHPASSWD.NLM file to the SYS:SYSTEM directory of the servers that will be running the NLM.
Execute the REG file on the pseudo-administrator's workstation so that the DLL files are registered with NWAdmin. This file adds the following two Registry entries so that NWAdminwill load the snap-in DLL and add the new dialogue screens for the CPA class and User class:
HKEY_CURRENT_USER\ Software\NetWare\Parameters\NetWare Administrator\Snapin Object DLLs WIN95 "CHPASSWD"="CHPASSWD.DLL" Software\NetWare\Parameters\NetWare Administrator\Snapin Object DLLs WINNT "CHPASSWD"="CHPASSWD.DLL"To update the schema on the NDS tree, start NWAdmin. The snap-in DLL loaded by NWAdmin will check the schema on all NDS trees attached to the workstation. If a tree has not been updated to use CPS and the user has supervisor rights, the user will be asked whether the schema should be updated. (This step must be completed by an Admin-equivalent user, since the user must have supervisor rights to modify the schema.)
Uninstalling the CPS System
To uninstall the CPS system, do the following:
Delete all CPA objects in the NDS tree.
Remove the two Registry entries listed above.
Remove the schema extensions by running the DESCHEMA.EXE program included with the CPS software.
Using the Change Password Service
The remainder of this AppNote describes how to use the Change Password Service once it has been installed.
Creating Change Password Administrator Objects
Change Password Administrator objects are created using NWAdmin. This procedure must be carried out by an administrator who has sufficient rights to the container to grant the CPA object read/write rights to All Properties on the container. While a user might be able to create CPA objects in a container, unless the user can grant read/write rights the CPA object will effectively be powerless and will not be able to reset user passwords.
Once you have installed the CPS software as explained in the previous section, go to the Details page for the CPA class in NWAdmin (see Figure 2).
Figure 2: The Details page for the CPA class.
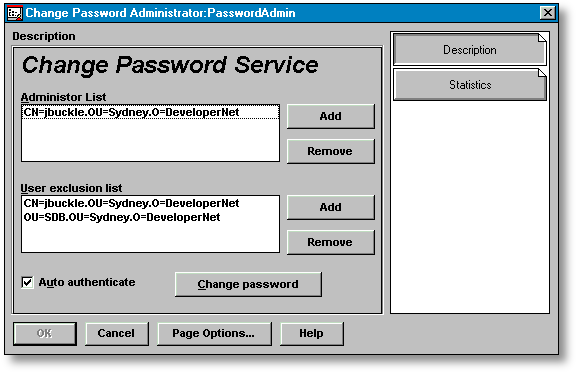
The Administrator List and the User Exclusion List are configured using the Add and Remove buttons adjacent to the list boxes. Clicking on the Add button will open an NWAdmin DS Browser window from which users (and containers, in the case of the Exclusion List) can be selected.
Multiple CPA objects can be created in the same container, or in both parent container and sub-containers, to establish a pseudo-administrator hierarchy. In this case, the system administrator may allow help desk staff to reset the passwords of most users, but only allow the help desk manager to reset management passwords. An example of this arrangement is given in Figure 3.
Figure 3: Sample tree showing multiple CPA objects.
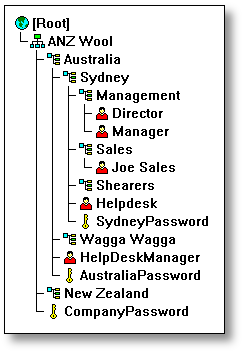
In this example tree, the SydneyPassword CPA object has user "Helpdesk" on its Administrator list and the "Management" container on its Exclusion list. AustraliaPassword has HelpdeskManager on its Administrator list and the director's account on the Exclusion list. The Helpdesk user can change the passwords of the sales team and the sheep shearers, but not of management. The managers would have to ask the HelpDeskManager to reset their passwords. (And, of course, managing directors never admit to forgetting their passwords.)
The default rights given to a CPA object on creation only cover the container holding the object. It is possible to assign a CPA object similar rights to other containers in the tree, thereby giving the CPA object the ability to modify objects outside of its container and sub-containers.
The password for the CPA object should be set immediately after the object has been created. Once the password has been entered, the "Auto Authenticate" check box is enabled. If this box is checked, the password just entered is encrypted and recorded in NDS. Checking the box allows CHPASSWD.NLM to auto-authenticate instead of prompting for a password on the server console.
|
Note: Auto-authentication is a convenient feature,but I cannot guarantee that it would take10,000 Cray years to crack the encryptionmethod, especially since the NLMcode canbe reversed engineered. Most hackers wouldfind it easier to walk up to a user's deskat lunch time rather than hack the auto-authenticationsystem. However, in an environment where highlevels of security are required,it is betterto leave auto-authentication deactivated. |
Loading the Change Password Service NLM
Once loaded, the Change Password Service NLM runs autonomously, requiring no supervisor intervention. The command line parameters for CHPASSWD.NLM are given below:
LOAD CHPASSWD DistinguishedNameOfCPAObject[/SUB]
The NLM will first attempt to authenticate as the CPA object specified on the command line. If the object has an auto-authentication attribute, the object's password will be decoded from the attribute; otherwise, the server will prompt for a password on the console. If authentication fails, the NLM will unload.
Once authentication is complete, the NLM will register the server as the host server in the CPA object. Any requests sent by NWAdmin using this CPA object will now be sent to this server.
Since only one copy of this NLM can be loaded on a server at the same time, the /SUB option is provided to allow this server to be the host server for all CPA objects in the container and sub-containers. On unloading, the NLM will deregister itself as the host server for all CPA objects in the container and sub-containers.
Example. Referring back to the sample tree in Figure 4, suppose you wanted the AustraliaPassword and SydneyPassword to be serviced by the same server. The load line would be as follows:
LOAD CHPASSWD AustraliaPassword.Australia.ANZ_WOOL/SUB
Operational Notes. Details on the request originator, CPA object, and user are displayed as requests are received on the NLM screen. If an error occurs, a NetWare error message is also displayed. The previous request details are cleared when a new request is received. Requests are logged in the SYS:ETC\CHPASSWD.LOG file. To stop logging, set this file to zero length and flag it as Read Only.
The server running CHPASSWD.NLM does not need to access any user or data files, nor does it require a read/write copy of any NDS replicas. Moreover, the server does not need a large license count since the connections required from clients are unlicensed. Hence this NLM can be loaded on a server running NetWare Runtime and be kept isolated from production servers.
Changing User Passwords
To change a user's password, the pseudo-administrator selects the user in NWAdmin and opens the User Details dialogue screen. This dialogue page for Change Password Service is given in Figure 4.
Figure 4: The Change Password Service page in NWAdmin.
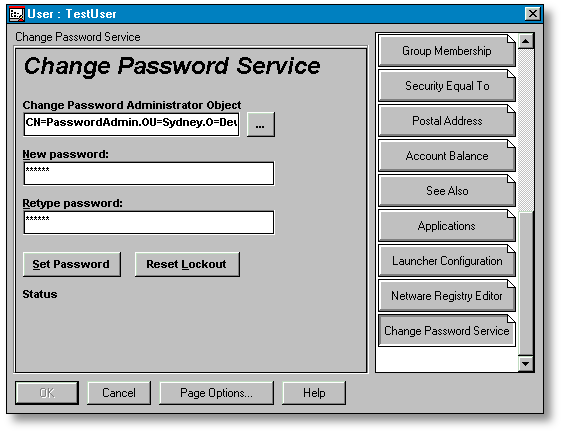
If there is a single CPA object in the user's container, it will be automatically selected. Otherwise use the ellipse (...) button to select a CPA object. To have any effect, the CPA object selected must meet the following criteria:
The Host Server attribute must be set with CHPASSWD.NLM running on that server.
The pseudo-administrator must be listed in the Administrator List.
The user and the user's container must not be listed in the Exclusion List.
The CPA object must have the appropriate rights to the user's container.
If the user has triggered the Intruder Lockout, the Intruder Lockout count can be reset by clicking the Reset Lockout button. The password can be set by entering the password in the Password and Retype fields and then clicking Set Password button. The Set Password button also resets the Intruder Lockout count and the grace login count.
The ongoing status of the operation is displayed at the bottom of the dialogue screen. The sequence of status messages is given below:
Sending request ...
Sending request ... reply received
- Lockout reset
- Password reset
Password changed
Setting the Host Server and Getting Usage Statistics
When the /SUB option is used, CHPASSWD.NLM automatically adds the server to the Host Server attribute of CPA objects in same container and sub-containers as the CPA object given on the load command line. The Statistics page of the CPA Details dialogue screen can be used to set the Host Server of a CPA object to a server that is already running the NLM (see Figure 5).
Figure 5: The Statistics page.
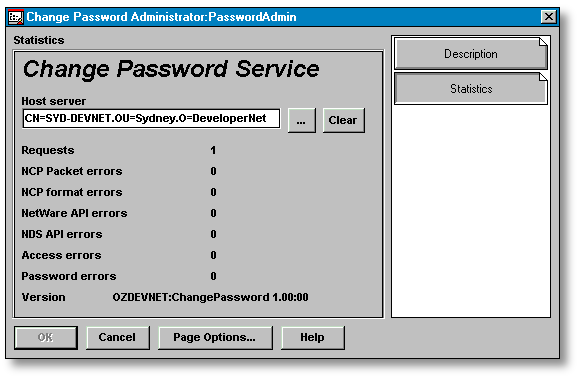
To change or set the host server, click the ellipse (...) button and select an NCP Server object. To stop a CPA object from sending requests, or if the host server is unavailable, click the Clear button.
|
Note: Setting the host server using theStatistics page is not normally necessary.An occasion when this feature is useful iswhen there are several CPA objects inparallelcontainers which should all be serviced byone server. Normally this arrangement shouldbe avoided by having a parent CPA object abovethe parallel CPA objects. |
A description and interpretation of the fields on the Statistics page is given in the table below. Note that these statistics refer to CHPASSWD.NLM acting as host for the CPA object, not the individual CPA object. Two CPA objects hosted by the same server will display the same statistics.
|
Statistic
|
Explanation
|
|
Requests |
Numberof requests sent to CPS NLM |
|
NCPPacket errors |
Errorsin the NetWare NCP handler |
|
NCPFormat errors |
Invalidor forged requests |
|
NetWareAPI errors |
Cannotdetermine user name of sender |
|
>NDSAPI errors |
Cannotread CPA object attributes |
|
Accesserrors |
Permissionto change password denied by CHPASSWD.NLM |
|
Passworderrors |
Permissionto change password denied by DS.NLM |
Change Password Service Availability
The Change Password Service software is currently in open beta. Copies are available by contacting the author via e-mail at JBUCKLE@NOVELL.COM with "Change Password Service" on the subject line.
Alternatively, you can download the CPS system with source code through Novell's DeveloperNet sample code web page at:
http://developer.novell.com/support/sample.htm
* Originally published in Novell AppNotes
Disclaimer
The origin of this information may be internal or external to Novell. While Novell makes all reasonable efforts to verify this information, Novell does not make explicit or implied claims to its validity.