Chapter Five:Using the AUDITCON Utility
Articles and Tips: article
01 Apr 1994
- Using the AUDITCON Utility
- Enabling Auditing
- Customizing the Auditing Environment
- How to Use the Auditing Information
- Maintaining Audit Files
- Summary
Using the AUDITCON Utility
As networks become more complex, the issue of system integrity increases in importance. The ability to audit the network to verify confidentiality, integrity, and availability is a cornerstone feature of NetWare 4.
This chapter provides information about the auditing capability of the NetWare 4 AUDITCON utility and describes the network administrator's part in setting up auditing. It also focuses on the procedures an auditor follows to audit NDS and the file system.
Specifically, this chapter explains how to do the following:
Set up auditing
Customize the auditing environment
Select auditing events
Create auditing reports
Maintain audit files
NetWare 4 Auditing
Auditing is the process of examining an organization's records and systems to assure information is properly protected, handled, and managed and meets the corporate policies for security. NetWare 4 auditing functionality is provided by the AUDITCON utility, which is protected by a confidential password. The auditing feature records specific NetWare Directory Services (NDS) and file system actions, called events, performed on the network.
Note: It is important to note that in NetWare 4.01 AUDITCON is a public utility, found in the SYS: PUBLIC directory of each NetWare server. It is a compressed file structure and must be protected accordingly. AUDITCON for NetWare 4.1 has been changed to be an encrypted file which is stored in a non-public directory.
Auditing tracks the following types of information:
User actions
Resource usage
File system security and access control.
NetWare 4 auditing adds credibility to complex network environments by serving as a checks and balances system. As a network grows and more users are added, many factors can cause security to deteriorate and allow unauthorized access to the network or to sensitive information such as:
Control becomes decentralized as core users are given specific security responsibilities.
Users create new files without setting the appropriate level of security.
New users are granted access to the system, increasing the complexity of the security structure.
File ownership is changed without corresponding changes being made to trustee rights.
The job responsibilities of a user change, requiring changes touser/group trustee rights.
Temporary access is granted, but not revoked, on a timely basis.
New software applications or releases are installed, requiring access restrictions.
Data collected during the auditing session can be used to:
Determine corporate security policy violations
Determine if computing and communications mistakes are occurring
Determine if procedures are being followed.
Determine who is performing tasks at the NetWare server level
Troubleshoot problems on the network
In addition to providing information necessary to reducing security risks, auditing also provides valuable information relating to network resources and troubleshooting. For example, the network administrator can use the auditing information to reconstruct events leading up to a crash or disaster.
Reasons to Audit the Network
Auditing minimizes security risks, provides valuable information about resource usage, and serves as a troubleshooting aid. Network auditing provides invaluable information about the system to the auditor and network administrator(s) who need data to validate the integrity of the information and its processing in the client/server networks, just as financial auditing statements can give a company's annual report credibility.
The importance of network auditing is exemplified in the following circumstances:
Government contracts where security at a company must be certified
Financial institutions regulated by the SEC
Confidential departments such as Human Resources and Accounting
The Auditing Process
The first step in the auditing process is to select the individuals that will be assigned the status of auditor. The number of people needed depends on the size of the organization and the network that services it. Ordinarily an auditor is assigned to an individual volume. However, in large centralized installations an individual - such as a security administrator - can audit several volumes from a single location.
Security administrators and auditors should be individuals who do not have a privileged status or a vested interest in the operation of the system. They should be independent and able to function in such a manner that they verify the integrity of the network without bias. They should not be responsible for the network or for the area to be reviewed.
Figure 1: The auditing process.
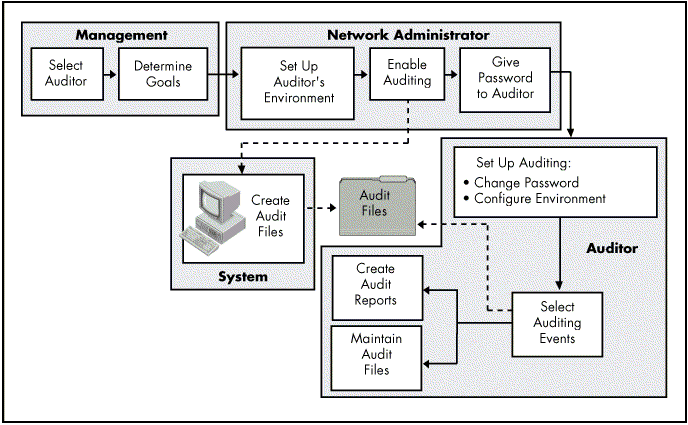
The auditor should be more experienced than the average network user and should be knowledgeable about the network topology, network structure, NDS, and file system services that are being audited.
The auditor should have information about the structure of the company's organization, data flow, file system, and NDS tree. The auditor can then use generally accepted auditing principles to help management clarify the audit goal and design an audit plan to accomplish the goals.
Note: Auditing is a privileged function and should be controlled by management. It is also important that management support this function and that it be aware of the results on an ongoing basis.
After the auditor is selected and the goals of the audit are determined, the network administrator:
Sets up the auditor's environment
Enables auditing for the appropriate container or volume, and assigns an auditing password
Gives the auditing password to the designated auditor
Note: Forgetting the audit passwords can cause a serious problem. Without a password for a volume or a container, one is unable to access the audit files and backup/recovery requires one to delete the volume or container and restore it from a backup. This is a very costly process.
When given the auditing password, the auditor assumes full responsibility for auditing the specified container or volume. The auditor performs the following auditing tasks:
Sets up auditing by changing the password and configuring the auditing environment.
Selects events to audit.
Creates reports.
Maintains the audit files.
The auditing process includes the creation of audit files by the system. When the network administrator enables auditing, AUDITCON automatically creates files to record the audited events and the auditor's actions.
AUDITCON creates separate files for each container and volume in which auditing is enabled. At the NDS level, the data is stored in the Audit Data files. At the volume level, the data is stored in the Audit Data records of the Audit History file.
The auditor maintains the audit files and uses the data collected in the files to create reports.
The Network Administrator's Role
The network administrator prepares the network environment for auditing. Network administrators should be limited to doing audits only for troubleshooting purposes - the primary auditing responsibility should be given to the auditor.
Before passing the audit responsibility to the auditor, you must set up the auditor on the network, enable auditing, and give the auditing password to the auditor.
To set up the auditor on a NetWare 4.01 network, one needs to:
Create a User object for the auditor and assign the appropriate rights.
Create a home directory for the audit or to store report files in.
Map a drive to the directory that contains the auditing executable program files (SYS:PUBLIC).
Make sure the Browse right has been assigned in each container that needs to be audited.
Provide the auditor with the one time use password.
Enabling Auditing
You can enable auditing to track events in NDS and in the file system.
Note: When auditing is enabled for the NDS container it is enabled for that container only - it is not enabled for subordinate containers. Likewise, when auditing is enabled for a volume, it is enabled for that volume only. This reduces overhead on other volumes.
At the NDS container level, events relate to the use of NDS. For example, the NDS container level is the appropriate choice when the goal is to monitor the creation of User objects.
At the volume level, events relate to the use of files and directories, queues, or NetWare servers. For example, the volume level is the appropriate choice when the goal is to track the number of times a certain user opens a specific file.
Enabling Auditing for an NDS Container
To enable auditing for an NDS container, do the following:
At the DOS prompt, type the following:
AUDITCON <Enter<
The "Available Audit Options" menu appears. The current NetWare server and volume appear at the top of the screen.
Select "Audit Directory Services".
The "Audit Directory Services" menu appears.The session context appears at the top of the screen.
(Optional) Change the context by doing the following:
a. Select "Change Session Context".
b. At the prompt, type the context of the container for which auditing is being enabled and press <Enter<.
The "Audit Directory Services" menu appears.
Select "Audit NDS tree".
A list of containers appears.
Highlight the container to be audited and press <F10<. The "Available Audit Options" menu appears.
Select "Enable Container Auditing".
At the prompt, type a password for the container and press <Enter<.
At the prompt, retype the password and press <Enter<.
Notify the auditor of the password.
Enabling Auditing for a Volume
The procedure for enabling auditing at the volume level is similar to enabling auditing at the NDS container level. The difference is that menu selections pertain to the volume being audited.
To enable auditing at a volume level, do the following:
At the DOS prompt, type the following:
AUDITCON <Enter<
The "Available Audit Options" menu appears.
The current NetWare server and volume appear at the top of the screen.
Select "Enable Volume Auditing".
A list of volumes appears.
Highlight the volume to be audited and press <F10<.
The "Available Audit Options" menu appears.
Select "Auditor Volume Login".
At the prompt, type a password for the volume and press <Enter<.
At the prompt, retype the password and press <Enter<.
Notify the auditor of the password.
Customizing the Auditing Environment
The auditing environment is the auditor's work space. In the same way that you configure the network to help accomplish administrative tasks, the auditor configures the auditing environment to optimize his ability to accomplish auditing tasks. To set up the Auditing environment the auditor does the following:
Accesses auditing functionality by running AUDITCON and logging in to the appropriate NDS container or volume
Changes the auditing password
Customizes the auditing environment
Accesses auditing functionality
In addition to the standard network login, the auditor must use the AUDITCON login procedure to access the auditing capabilities at either the NDS container or the volume.
A password is needed for each container or volume the auditor wants to audit. The next step the auditor takes to establish independence is to change the auditing "password" for the NDS container and volume to be audited. This provides security for the auditing data and adds credibility to the network.
Note: Take precautions against forgetting or losing the auditing password as stipulated above.
Changing the Audit Password for an NDS Container
To change the auditing password for an NDS container, do the following:
At the DOS prompt, type:
AUDITCON <Enter<
The "Available Audit Options" menu appears.
The current NetWare server and volume appear at the top of the screen.
Select "Audit Directory Services".
The "Audit Directory Services" menu appears. The session context appears at the top of the screen.
(Optional) Change the context by doing the following:
a. Select "Change Session Context".
b. At the prompt, type the context for the container to be audited and press <Enter<.
The "Audit Directory Services" menu appears.
Select "Audit NDS tree".
A list of containers appears.
Highlight the container to be audited and press <F10<.
The "Available Audit Options" menu appears.
Select "Auditor Container Login".
At the prompt, type the current auditing password and press <Enter<.
The "Available Audit Options" menu appears.
Select "Auditing Configuration".
The "Auditing Configuration" menu appears.
Select "Change Audit Password".
At the prompt, type the current password and press <Enter<.
At the prompt, type the new password and press <Enter<.
At the prompt, retype the new password and press <Enter<.
Changing the Auditing Password for a Volume
To change the auditing password for a volume, do the following:
At the DOS prompt, type the following:
AUDITCON <Enter<
The "Available Audit Options" menu appears.
The current NetWare server and volume appear at the top of the screen.
Select "Auditor Volume Login".
At the prompt, type the current auditing password and press <Enter<.
The "Available Audit Options" menu appears.
Select "Auditing Configuration".
The "Auditing Configuration" menu appears.
Select "Change Audit Password".
At the prompt, type the current password and press <Enter<.
At the prompt, type the new password and press <Enter<.
At the prompt, retype the new password and press <Enter<.
Customizing the Auditing Parameters
After changing the password, the auditor has complete control of the auditing environment and the files that contain the auditing records.
Figure 2: Customizing the auditing environment.
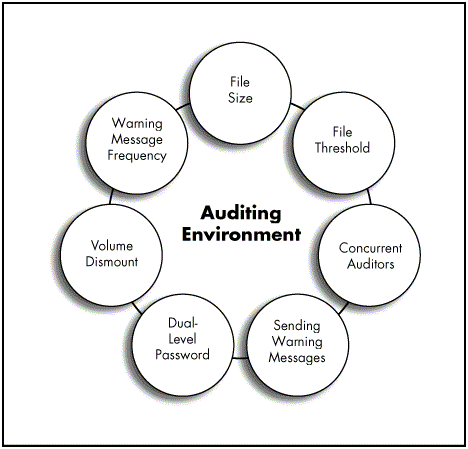
The auditor can set numerous parameters which map the corporate security policies and generally accepted security practices to determine how auditing works in the volume or container being audited. These parameters include options to:
Set the size limit of the Audit Data file.
Set a file size threshold beyond which AUDITCON sends warning messages to the NetWare server console and the system log file.
Allow more than one auditor to log in to the volume or container at the same time. (NetWare 4.01 requires an auditor to login into each volume or container separately. NetWare 4.1 will allow single log in functionality.)
Send broadcast warning messages to all users or to the console.
Require a dual-level password to change Auditing settings.
Set a volume to dismount or disable event recording when the Audit Data file reaches its size limit or an unrecoverable write error occurs.
Set the frequency for warning messages to be sent to the NetWare sever console when the audit file is full.
Note: AUDITCON is being revised to move it from the SYS:PUBLIC directory. Encryption of the data with bit sensitivity, as well as the ability to archive the AUDITCON files automatically is being added to NetWare 4.1. This will allow auditing to continue and the file to be archived when predetermined limits are reached instead of turning the auditing function or the system off.
Customizing Auditing at the NDS Container Level. To customize the auditing environment at the container level, do the following:
At the DOS prompt, type the following:
AUDITCON <Enter<
The "Available Audit Options" menu appears, as shown in Figure 3. The current NetWare server and volume appear at the top of the screen.
Figure 3: Available Audit Options menu.
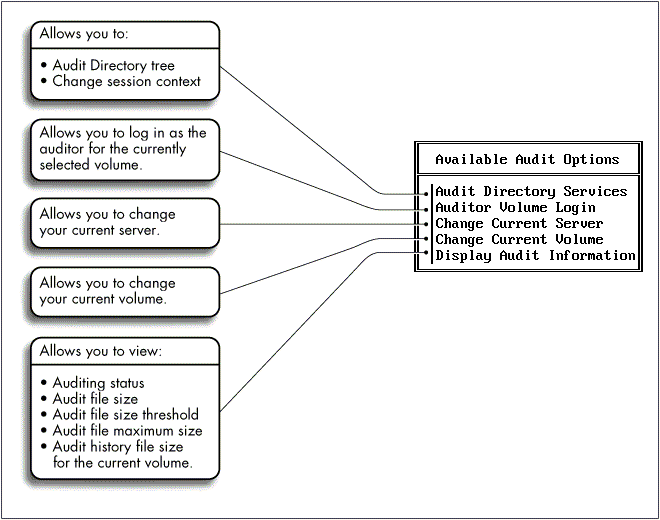
Select "Audit Directory Services".
The "Audit Directory Services" menu appears. The session context appears at the top of the screen.
(Optional) Change the context by doing the following:
a. Select "Change Session Context".
b. At the prompt, type the context for the container to be configured; then press <Enter<.
The "Audit Directory Services" menu appears.
Select "Audit NDS Tree".
A list of containers appears.
Highlight the container to be audited and press <F10<.
The "Available Audit Options" menu appears.
Select "Auditor Container Login".
At the prompt, type the auditing password and press <Enter<.
The "Available Audit Options" menu appears.
Select "Auditing Configuration".
The "Auditing Configuration" menu appears.
Select "Audit Options Configuration".
The "Audit Configuration" form appears.
Enter the setting for the option you want tochange and press <Enter<.
Repeat step 10 for each option you want to change.
When you have completed the changes, press <Esc<.
Select "Yes" to save the settings.
Customizing Auditing at the Volume Level. To customize the auditing environment at the volume level, do the following:
At the DOS prompt, type the following:
AUDITCON <Enter<
The "Available Audit Options" menu appears.
The current NetWare server and volume appear at the top of the screen.
Select "Auditor Volume Login".
At the prompt, type the auditing password and press <Enter<.
The "Available Audit Options" menu appears.
Select "Auditing Configuration".
The "Auditing Configuration" menu appears.
Select "Audit Options Configuration".
The "Audit Configuration" form appears.
Type the setting for the option you want to change and press <Enter<.
Repeat step 6 for each option you want to change.
When you have completed the changes, press <Esc<.
Select "Yes" to save the settings.
Selecting the Events to Audit
After configuring the environment and returning to the Auditing Configuration menu, the auditor can log in to different NDS containers and volumes to select the events to be audited. These selections should be based on auditing goals and focus.
At the NDS container level, the auditor can choose to audit by an NDS event or by user. At the volume level, the auditor can choose to audit by event, by files or by user.
In addition, the auditing function includes options for managing the auditing environment at both the container and volume level.
Figure 4: Selecting the events to audit.
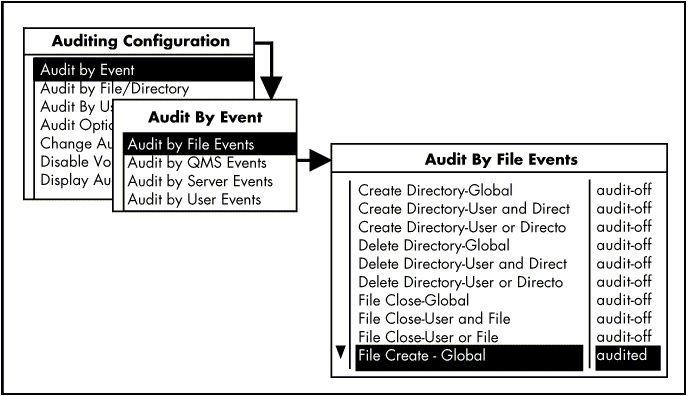
Examples of events an auditor might be interested in recording:
"Reads" of a database to see if invalid users attempt to read a file(s)
"Change password" to check if passwords were changed after hours when a security breach may be suspected
"Login/Logout" to track trends of login/out during odd hours
Global. This selects all events, regardless of which user performs the event or in which file or directory the event occurs throughout the volume.
User and File/Directory. To create an audit record a flagged event must be performed by the flagged user.
Example: File Close-User and File causes the auditing system to record an event when a flagged user closes a flagged file.
User or File/Directory. Only one of two conditions has to be met to create an audit record: either the flagged event occurs, or the flagged user performs the event.
Example: Delete Directory- User or Directory causes the auditing system to record every time a flagged user deletes any directory, and every time a flagged directory is deleted by any user.
Auditing Options for NDS
The following table lists auditing options that are available at the NDS container level.
Figure 5: Auditing options for NDS.
|
Option
|
Explanation
|
|
Audit by DS Events |
Gives the auditora list of NDS events. The auditor can selectthe events to be audited. When auditing isturned on for an event, all occurrences ofthe event within the container are recorded. |
|
Audit by User |
Gives a listof NDS objects. The auditor can select theusers to audit from the list by selectingthe user's name and pressing <F10<.If auditing is turned on for a user, a recordis entered in the Audit Data file each timethe user performs an audited even. |
To select events to audit for a container, do the following:
Log in to the container to be audited.
The "Available Audit Options" menu appears.
Select "Auditing Configuration".
The "Auditing Configuration" menu appears.
(Optional) Select "Audit By DS Events".
A list of available NDS events appears.
a. Highlight the event to be audited and press <F10<.
The tag for that event changes from "audit off" to "AUDITED".
b. When you have completed your selection, press <Esc<.
A confirmation box appears.
c. Select "Yes" to save the changes.
Note: At the NDS container level, events are audited within the audited container only - auditing does not record actions that occur at higher levels of the NDS tree. Auditing records events for leaf objects within a container, not for Organizational Units within the container.
(Optional) Select "Audit By User".
A list of available NDS users appears.
a. Highlight the user to be audited and press <F10<.
The tag for that user changes from "audit off" to "AUDITED."
b. When you have completed your selections, press <Esc<.
A confirmation box appears.
c. Select "Yes" to save the changes.
Use the "Audit by User" option in volume auditing to track events initiated by users (including SUPERVISOR) within the bindery context.
The "Audit by User" option will not flag NDS users.
Auditing Options For a Volume
The following table lists auditing options that are available at the volume level.
Figure 6: Auditing options for a volume.
|
Option
|
Explanation
|
|
|
Audit by Event |
File/Directory Events |
Create or delete a directory Open, close, read, and write files Includes file or directory activity such as directory createor delete, and file open, close, read, andwrite requests. Events can be audited globally(all files and directories are audited forthe event regardless of user), by user orfile (the event is recorded only when itapplies to an audited user or file), or user and file (the event is recorded whenit applies to and audited user in an auditedfile or directory). |
|
QMS Events |
Tracks activitiesaffecting print queues, such as requeststo create or destroy a queue. |
|
|
Server Events |
Audits requests,such as mounting a volume or bringing downa NetWare server, that affect a specificserver. Server events are audited globally(all instances of the audited event are recorded). |
|
|
User Events |
Includes activitiessuch as logging in, logging out, and logoutschanging, trustee assignments and creatingor deleting users. |
|
|
Audit by File/Directory |
Givesa list of all files and directories. Theauditor can select the files and directoriesto be audited. When a file or directory isaudited, a record is added to the Audit Datafile each time an audited event occurs forthat file or directory. If a parent directoryis set to "Audited," it has the sameeffect as browsing up one level in the NDStree and setting the actual directory nameas audited. |
|
|
Audit by User |
Givesthe auditor a list of users in the binderycontext. When auditing is activated for abindery user, a record is entered in theAudit Data file each time the user performsan event that is audited. This only appliesto file system events. |
Auditing tracks volume activities by the following:
Events -File system (file and directory) events -NDS events -Server events -User events
Files and directories
Users. (This option is for tracking the system events for bindery users who attach to a NetWare 4 server and use file services.)
Selecting Events to Audit for a Volume
To select events to audit for a volume, do the following:
Log in to the volume to be audited.
The "Available Audit Options" menu appears.
Select "Auditing Configuration".
The "Auditing Configuration" menu appears.
(Optional) Select "Audit By Event".
The "Audit By Event" menu appears.
a. Select a type of event from the following options:
Audit By File Events
AuditBy NDS Events
Audit By Server Events
Audit By User Events
A list of available event options for the type of event you selected appears.
b. Highlight the event to be audited and press <F10<.
The tag for that event changes from "auditoff" to "AUDITED."
c. Repeat step" b" for each item to be audited.
d. When you have completed your selections, press <Esc<.
A confirmation box appears.
e. Select "Yes" to save the changes.
Press <Esc<.
(Optional) Select additional events by choosing from the following event options:
a. Select "Audit by File/Directory" to audit by files or directories
or
b. Select "Audit By User" to audit by users.
A list of available files and directories or of available users appears.
c. Highlight the item to be audited and press <F10<.
The tag for that item changes from "audit off" to "AUDITED".
d. Repeat step "c" for each item to be audited.
e. When you have completed the selections, press <Esc<.
A confirmation box appears.
f. Select "Yes" to save the changes.
Auditing Event Guidelines
The following table lists auditing goals and the selections the auditor makes to achieve each goal. All of these events affect the file system, except where noted below.
Figure 7: Auditing event guidelines.
|
Goal
|
What to Audit
|
|
Justify resources |
Writes to an application file |
|
Use of print queues |
|
|
Diagnose performance problems |
File opens to an application that is slow |
|
Determine holes in security |
Changes to ACL (NDS) |
|
File opens of sensitive files |
|
|
Determine if a user has accessed unauthorized areas |
File opens in the audited areas |
|
File writes in the audited area |
|
|
File opens by an audited user |
|
|
DetermineNetWare server security |
Login security(NDS) |
|
Volume mounts and dismounts |
|
|
NetWare server events |
|
|
Audit file security |
File reads and writes |
|
File creations and deletions |
How to Use the Auditing Information
The following cases illustrate situations where auditing is helpful. These cases also illustrate how to:
Justify the purchase of another word processor license.
Locate a potential security breach.
Locate and correct a trustee rights problem.
Monitor volumes being dismounted or mounted.
Determine if a workgroup manager is abusing his or her rights.
Monitor changes in partitions and replicas.
Case 1: The network administrator is told to justify the purchase of another word processor license.
The auditor flags the word processor file for OPEN by all users and counts the number of accesses to that file. The resulting information gives the network administrator an idea of how many people use the word processor program and how often. The persons responsible for purchasing can then decide whether the need is great enough to buy another license based on number and frequency of accesses.
Case 2: The auditor helps the network administrator find a potential security breach.
The network administrator finds that some of the console parameters have changed in the past few days. The auditor may be asked to check the server events and RCONSOLE accesses within the past week to determine who has gained access to the server console.
Case 3: The auditor helps the network administrator find and correct a trustee rights problem.
A user says that he cannot access a database program that he used to have rights to. The auditor searches the auditing records, determines that the rights to the database directory have been changed, and tells the network administrator that the rights were changed on a certain date and by whom.
Case 4: The network administrator wants reports on volume mounts and dismounts.
The administrator has the auditor flag the Volume Mount and Volume Dismount under Audit by Event server events. Each time the volumes are mounted or dismounted for that server, auditing records the event.
Case 5: The network administrator suspects a workgroup manager of abusing power and changing users' rights.
The administrator has the auditor flag the User object in the container with the Change in ACL flag under the Audit by NDS Events menu. When the user makes any change to trustee assignments or ACLs, the auditing file reflects the change.
Case 6: The network administrator wants to monitor changes in NDS partitions and replicas.
The auditor goes to the Audit by DS Events menu and flags the following:
Add Partition
Change Replica Type
Join Partitions
Remove Partitions
Remove Replicas
Split Partitions
These events must be flagged on the parent container for each partition that the network administrator wants to monitor.
Creating Auditing Reports
The auditor is responsible for managing the data collected in the audit files and communicating the results to management.
With AUDITCON, the auditor can create reports to be printed or to be viewed online. To get the pertinent information from the audit files, the auditor does the following:
Creates, edits, and applies filters
Sends data to a DOS text file to be printed
Views audit data online
No data appears in the report until events are selected and actions have occurred on audited events.
The Audit Data file can include an enormous amount of information. Providing management with all the information, however, could obscure the important findings in the data. To avoid this, the auditor can create a report filter to make the presentation and interpretation of audit data more meaningful.
The auditor uses report filters to extract specific information from the Audit Data file, based on the requirements of the report. Once a filter is created, it can be saved in the Edit Filter list and used again.
Figure 8: Creating auditing reports.
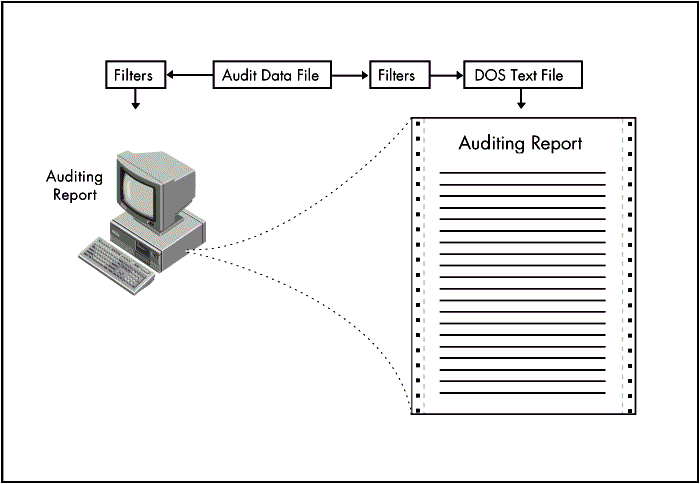
When creating reports, the auditor has the option of using an existing filter, modifying an existing filter, or creating a completely new filter. The auditor can create a filter to satisfy the information needs of each situation. With this list of filters to select from, the report task becomes streamlined.
Figure 9: Report filter options.
|
Option
|
Explanation
|
|
|
Report byDate/Time |
Allowsthe auditor to enter a period in which thesystem should create a report. All recordedevents that fall within the dates and timesentered appear in the report. |
|
|
Report byEvent |
Allowsthe auditor to select the type of auditedevents to be included in the report. If thisoption is selected, AUDITCON prompts forselection from the types explained below.Events are dependent on the files and directories,and users included in or excluded from thereport. |
|
|
FileEvents |
Files eventsto be included in the report are selectablein the report column where the events aremarked "Audited". |
|
|
QMSEvents |
Queue eventsto be included in the report are selectablein the report column where the events aremarked "Audited". |
|
|
ServerEvents |
Server eventsto be included in the report are selectablein the report column where the events aremarked "Audited". |
|
|
UserEvents |
User eventsto be included in the report are selectablein the report column where the events aremarked "Audited". |
|
|
ReportExcludePaths/Files |
Allowsthe auditor to specify files or directoriesto exclude from the report. Press <Ins<and type the name of a file or a directoryto be excluded. All other audited files anddirectories are included. |
|
|
ReportExcludeUsers |
Allowsthe auditor to specify the name of an auditeduser to exclude from the report. Pres <Ins<and type the name of a user to be excluded.All other audited users are included. |
|
|
ReportIncludePaths/Files |
Allowsthe auditor to specify files or directoriesto include in the report. Press <Ins<and type the name of a file or a directoryto be included. All other audited files anddirectories are excluded. |
|
|
ReportInclude Users |
Allowsthe auditor to specify the name of an auditeduser to include in the report. Press <Ins<and type the name of a user to be included.All other audited users are excluded. |
Creating a Report Filter To create a report filter, do the following:
Log in to the NDS container or volume.
The "Available Audit Options" menu appears.
Select "Auditing Reports".
The "Auditing Reports" menu appears.
Select "Edit Report Filters".
The "Edit Filter" list of previously created filters appears.
Press <Insert<.
The "Edit Report Writer" menu appears.
Select the audited events or period of time to include in, or exclude from the report.
Complete the selections and press <Esc<.
The "Edit Report Filter" menu appears.
Press <Esc<.
A confirmation box appears.
Select "Yes" to save the filter.
Delete the default name and type a name for the filter; then press <Enter<.
The new filter is now included in the Edit Filter list.
The filter option creates a file called FILTER.ARF at the root of SYS.
Editing a Report Filter. Changes to existing filters can be made through the Edit Report filters option. To edit a report filter, do the following:
Log in to the NDS container or volume.
The "Available Audit Options" menu appears.
Select "Auditing Reports".
The "Auditing Reports" menu appears.
Select "Edit Report Filters".
The "Edit Filter" list of previously created filters appears.
Select a filter to be edited.
The "Edit Report Filter" menu appears.
Select the audited events or time periods to includein or exclude from the report.
Complete the selections and press <Esc<.
The "Edit Report Filter" menu appears.
Press <Esc<.
A confirmation box appears.
Select "Yes" to save the changes.
At the Save filter changes prompt, press <Enter<.
Sending Audit Data to Files. To print the audit report, the auditor must first send the data to a DOS text file.
For the security of the auditing data, the audit files are always open and the data collected in the audit files is unreadable by standard text editors. They are compressed under 4.01 and will be encrypted in 4.1. When the auditor selects the option to create a report, the system converts the unreadable data into a DOS text file. The auditor can then print the file and use a DOS text editor to edit it.
Note: You need to consider the security of the audit data when sending the data to a DOS text file. If the auditor does not specify a destination directory for the file, the system copies it to the auditor's home directory; the file can then be accessed by any user with the Supervisory right to that directory. To ensure the integrity of the audit data, the files should be copied to a local directory or floppy disk drive.
When sending the audit data to a DOS text file, the auditor can choose to use a filter or to send the data without a filter. The auditor can also create new filters or edit existing filters at this time, rather than going to the Edit Report Filter option to make the changes.
Sending Audit Data to a File. To send audit data to a DOS text file, do the following:
Log in to the NDS container or volume.
The "Available Audit Options" menu appears.
Select "Auditing Reports".
The "Auditing Reports" menu appears.
Select "Report Audit File".
Specify the destination for the file:
At the prompt, type a destination path and the filename for the audit file and press <Enter<.
or
Press <Enter< to copy the report to a default file in the auditor's home directory.
A list of filters appears.
(Optional) Create a new filter by doing the following:
a. Press <Insert<.
b. Select the audited events or period of time toinclude in or exclude from this report and press <Esc<.
The "Save Filter" menu appears.
c. Select one of the following options:
Discard Filter Changes
Savefilter changes
Use filter withoutsaving changes
d. (Optional) At the prompt, type a name for the new filter to be saved and press <Enter<.
A list of filters appears. If a new filter was saved, that filter is included on the list.
(Optional) Edit a filter:
a. Highlight the filter to be edited and press <F10<.
b. For the procedure to edit a filter, see "Editing a Report Filter" in this section.
Select a filter.
The audit event data is sent to the DOS text file.
Viewing a Report. The auditor can also apply a filter when viewing a report online. This is another opportunity to tailor the report depending on the needs of the audience.
To view a report online, do the following:
Log in to the NDS container or volume.
The "Available Audit Options" menu appears.
Select "Auditing Reports".
The "Auditing Reports" menu appears.
Select "View Audit File".
A list of filters appears.
(Optional) Create a new filter by doing the following:
a. Press <Insert<.
b. Select the audited events or period of time to include in or exclude from this report and press <Esc<.
The "Save Filter" menu appears.
c. Select one of the following options:
Discard Filter Changes
Savefilter changes
Use filter withoutsaving changes
(Optional) Edit a filter by doing the following:
a. Highlight the filter to be edited and press <F10<.
b. For the procedure to edit a filter, see "Editing a Report Filter in this section.
Select a filter.
The audited events appear at the bottom of the screen.
Press the arrow keys to scroll through the report.
Press <Esc< to exit the report.
Example of Creating Auditing Reports
NetWare 4 provides the auditor with auditing and reporting functionality which was not integral to NetWare 3. The following section describes a typical scenario that an auditor might find experience.
Scenario. The general manager has just called you to discuss the results of the audit sessions, specifically security issues. The auditor needs to view the ACL and Security Equivalence information online to discuss it with the general manager.
Procedure. To ensure that your auditing report includes auditing events, complete the following in NDS as network administrator:
Make changes to any user's ACL.
Change any user's security equivalence.
Rename any object.
Complete the following to view the auditing report online and to get the information the general manager has requested.
Log in to the Directory Services container.
Select "Auditing Reports".
Select "View Audit File".
Create the appropriate filter.
View the report online.
Maintaining Audit Files
AUDITCON creates the following audit files when auditing is enabled at the volume or NDS container level:
Audit Data file (NET$AUD.DAT)
Audit History file (AUD$HIST.DAT)
Audit Configuration file (NET$AUD.CFG)
Figure 10: Maintaining audit files.
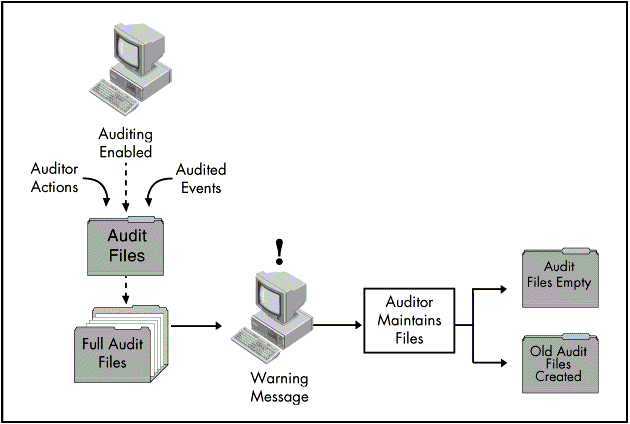
The Audit Data file keeps records of all audited transactions at both the NDS and Volume level. the auditing configuration that is set (recorded in the NET$AUD.CFG file) determines the type of records entered into the Audit Data file.
The Audit Data file operates like a system log and error file records are automatically entered into the file whenever an audited event occurs.
At the NDS container level, the Audit Data file also includes the records of the auditor's activities, such as auditor logins and logouts, and auditing configuration changes.This information is hidden in the root of the volume audited. This information is stored in the NDS database files, which are replicated throughout the network.
The Audit Data file and Audit History file store auditing data for the volume, whereas the NDS audit data is stored in the NDS database files. The NDS auditing data is replicated everywhere the partition is replicated.
The auditor is responsible for maintaining the audit files. As auditing continues, the audit files include more and more records of audited events. Like the log files on the NetWare server, these files do not circle back on top of themselves.
Note: When audit files get full, two different events can occur under NetWare 4.01: the system stops processing, or the audit process is stopped. The auditor should select the latter and stop the auditing function. It is also recommended that the auditor set a warning when the audit file threshold is reached. This allows one to stop the auditing at a predetermined size less than the maximum audit file size and perform appropriate archiving of the file. NetWare 4.1 will have automatic archiving.
The space required to record the auditing events is as follows:
12 bytes per volume- audited event
28 bytes per NDS- audited event
Be sure to set the maximum file sizes in AUDITCON to prevent the audit files from unnecessarily filling volume space.
Audit Flags
Auditing attaches flags or attributes to each file, directory, and NDS object that is flagged for auditing. The following are important characteristics of the auditing flags:
The attributes are invisible to all users and applications except AUDITCON.
Since the attributes are invisible, they are not backed up.
The attributes can only be changed through specific, encrypted NCP calls.
The only way to disable volume auditing (or recover from a lost password) is to do the following:
Back up the file system.
Delete the volume with INSTALL.
Create the volume.
Restore the files from the backup copy.
This procedure will remove all auditing data and flags from the volume.
Note: NDS must also be recreated to remove the auditing information.
Audit Files Maintenance Options
Auditing provides several options the auditor can use to maintain the audit files at the NDS container and volume level. For example, when files reach their size limits (established by the auditor when setting up the auditing environment), the auditor should archive the files at the appropriate record retention period.
From the Audit Files Maintenance Options menu, the auditor can maintain the files by selecting from the following options:
Select "Close Old Audit File" to close old data files and allow others access to them.
Select "Copy Old Audit File" to copy an old audit file to a file or directory as a compressed, non- readable file.
Select "Delete Old Audit File" to delete the old audit file.
Select "Display Audit Status" to display basic informationabout the audit files.
Select "Reset Audit Data File" to reset the Audit Data file and move the existing data to the old Audit Data file. This data overwrites the data in the old file. The original Audit Data file records the same events as before.
Select "Reset Auditing History File" to move the existing data in the Audit History file to the old Audit History file.This data overwrites the data in the old Audit History file.
Resetting the Audit Data File
To reset an Audit Data or Audit History file, do the following:
Log in to the NDS container or volume.
The "Available Audit Options" menu appears.
Select "Audit Files Maintenance".
The "Audit Files Maintenance" menu appears.
Select "Reset Audit Data File" or "Reset Auditing History File".
Select "Yes" to reset the file.
The current contents of the file move to the old audit file and previous records in the old audit file are deleted. The original audit file size and audit record count are reset to zero.
Summary
The auditing function of NetWare 4 helps increase the integrity of network data by tracking network events. Auditing data can be used to determine if procedures are being followed and who is performing tasks at the NetWare server level.
AUDITCON allows auditors to specify the parts of the system to be monitored and provides functions for outputting auditing data for management review. AUDITCON also monitors the activities concerned with identification, access, and modification of network resources.
The network administrator role is to set up the auditor's environment or, the network and enable auditing for the appropriate NDS container or volume. Once this has been completed, the network administrator gives the auditing password to the auditor, who assumes responsibility for auditing.
The auditor changes the auditing password to ensure that the auditing data is secure. The auditor configures the auditing environment, sets the events to be audited. and manages the auditing data.
The auditing capability of AUDITCON provides reassurance to management and other parties interested in the security and integrity of the network. Each company should know that a user's access to and use of network resources is appropriate and authorized and that the system is operating appropriately.
* Originally published in Novell AppNotes
Disclaimer
The origin of this information may be internal or external to Novell. While Novell makes all reasonable efforts to verify this information, Novell does not make explicit or implied claims to its validity.