Speedy Delivery
Articles and Tips: article
01 Apr 2005
When employees are hired, whether on a regular, temporary or contract basis, how much time do they spend counting paper clips before they have everything they need to do their jobs? And I mean everything, from network resources like directories, databases, e-mail and other applications, to physical assets like an office, a phone, a desktop or laptop, credit cards, smart cards-even paper clips.
Now consider existing employees: how much time lapses between the moment they are promoted or transferred and the moment they finally gain due rights to new IT resources? Arguably more important, when employees leave, for how many hours after the fact can they access resources to which they should no longer be entitled?
Admittedly, answers to questions about the efficiency with which you grant or restrict access to resources and assets vary, assuming that you are still manually managing these processes. That said, if you are hoping to be coaxed to respond with the old no-answer-is-a-wrong-answer ruse, forget it. In this context, lots of answers are wrong.
For example, Meta Group research reveals that when internal users move, manually granting rights to resources takes an average of 14 hours from request to resolution. That is a lot of wasted time; 14 hours is the wrong answer. This research also shows that on average, manually restricting access to resources takes 10 hours. Again, wrong answer-in fact, in this case, any time is too much time. Ideally, former employees should be denied access to corporate information (which they could steal or corrupt) before they start packing up their office. (For more information, see The Value of Identity Management, META Group, August 2002.)
So what are the right answers? The right answers are small numbers that are better couched in terms of minutes than hours. How do you reduce the time it takes to grant or restrict users' access to resources and assets from hours to minutes? You already know the answer to this question: through automation. Automating provisioning processes saves you time and your company money and better protects your information and assets. (For information about the inherent benefits of automation, see Why Identity Management Makes Cents.)
Chances are that you already have automated several of your provisioning processes. However, most likely, you have not automated every step required to provision access to all of your systems and assets. The problem is that not all systems are created equal: some systems are special and, as such, require approval from one or more gatekeepers. Likewise, users typically need approval to acquire physical tools, such as pagers and laptops. So how can you automate these approval processes?
Novell answers this question with the Enhanced Provisioning Module, a consultant's toolkit that augments the award-winning Novell Nsure Identity Manager 2.0. (For a quick look at the benefits of using this module, see What a Case!)
A Word (or 353) About the Parent Product
Nsure Identity Manager is an identity management solution that bi-directionally synchronizes identity information across diverse systems on your own or your partner's network. (For information about accolades for Nsure Identity Manager, see the web site.)
Describing in detail what this means and how it works goes beyond the scope of this article. (But if you're interested in the details, see Locking down Identity and Password Management with the New DirXML: Nsure Identity Manager 2.0 in the November/December 2003 issue.)
For now, you need only understand this much: change an account, a password or profile data in one system, and Nsure Identity Manager automatically synchronizes this change across other connected systems.
A connected system in the context of Nsure Identity Manager is any system for which you have a special connector, called a "driver." Novell provides drivers for many popular applications, databases, directories, e-mail programs, operating systems, mainframes and midrange systems, including the following:
PeopleSoft
SAP
Oracle
Novell GroupWise
Microsoft Active Directory
SUSE LINUX
Red Hat Linux
OS/400
If you find a system or two for which Novell does not offer a driver, no worries: you (or a developer) can build a custom driver. (For a complete list of available drivers, see it online. For information about writing custom drivers, see the web site.)
Of course, Nsure Identity Manager does not randomly synchronize changes across every system; instead, it synchronizes changes according to rules that you create to control how connected systems exchange information. Through these rules, you can automate many identity management tasks, including provisioning tasks.
For example, you can create rules that dictate that when someone in Human Resources (HR) creates a new account in PeopleSoft, this event triggers the creation of a new User object in Novell eDirectory. In turn, this eDirectory event might trigger the simultaneous creation of accounts on SUSE LINUX, Novell GroupWise and MS Active Directory. Likewise, you can create a rule that ensures that Nsure Identity Manager automatically deletes a user's accounts on all connected systems the moment someone in HR disables this user's account in PeopleSoft.
What the Module Adds
In other words, with Nsure Identity Manager, you take a giant step toward automating many of your provisioning processes. However, Nsure Identity Manager alone cannot automate the steps users must take to get the approval they need for accessing some of your systems or acquiring certain assets. To that end, you need help, which is available in the form of the Enhanced Provisioning Module.
The Enhanced Provisioning Module adds handy identity features and a powerful provisioning tool to the Nsure Identity Manager foundation. For example, the Enhanced Provisioning Module offers advanced search capabilities and organizational charts. (For more information, see Super Search and The Power of Organization.)
While these features are useful, the really big deal is this: the Enhanced Provisioning Module enables you to create approval flows that automate your company's approval processes, the completion of which can trigger provisioning events in Nsure Identity Manager. The end result is that you can automate all of your provisioning processes-including the ones that involve approvals. In doing so, you significantly cut the time it takes to get users the resources and assets they need to do their jobs.
Cut Time by Cutting Red Tape-Automatically
You work with consultants to develop and edit approval flows (which represent your company's actual approval processes) using a visual, drag-and-drop designer. (See Figure 1.) Approval flows are portlets that encapsulate the business logic that coordinates and automates the flow of approvals required to initiate particular provisioning requests.
Figure 1
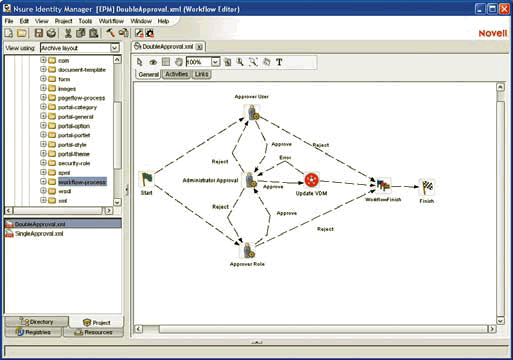
Depending upon how you configure your approval flows, the Enhanced Provisioning Module executes them when one of the following occurs:
A user submits a provisioning request. (See Figure 2).
Figure 2
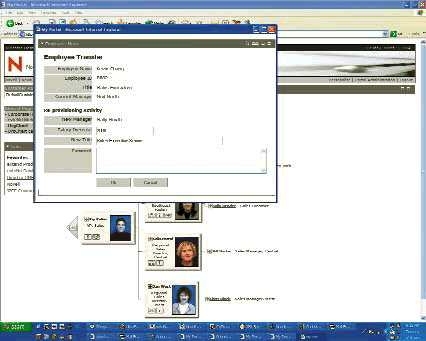
A particular event occurs in one of your connected systems.
Users submit approval requests using the Service Provisioning portlet, which displays all of the provisioning requests to which this user has rights. Users access this portlet by way of an out-of-the-box provisioning portal that you can configure and customize to suit your business needs. (For more information about this portal and components of the Enhanced Provisioning Module architecture, see About the Architecture.)
When a user submits a provisioning request, the Enhanced Provisioning Module executes the approval flow associated with this request. The result depends upon how you have configured your approval flow. For example, you might have configured your flow so that the module routes e-mail messages to the individual or individuals whose approval is required to fulfill this user's request. The Enhanced Provisioning Module enables you to route e-mail messages to several individuals. In these cases, you have the option to route messages to one individual at a time in an established order or to send the message simultaneously to all individuals who must approve the request.
In any case, these e-mail messages include a link to the provisioning portal. An individual who receives an approval request clicks this link, which opens a page displaying a list of approval requests that are pending this individual's approval. After clicking to open an approval request, the individual clicks the appropriate action: Approve, Forward or Reject. The individual clicks Forward when he wishes to delegate this task to someone else with appropriate rights to grant or deny approval.
When a provisioning request has been approved by everyone identified in your approval flow, the completed process can trigger a provisioning action in Nsure Identity Manager.
Approval Flow from the Top
An approval flow in action might look something like this: suppose your company hires an accounting clerk, let's call her Karen. Accordingly, an HR worker enters Karen's information in your HR system, in this case, SAP. Further suppose that you have configured Nsure Identity Manager such that this new hire event in SAP triggers the automatic creation of accounts for Karen on several systems, including eDirectory, SUSE LINUX, GroupWise, MS Active Directory and OS/400.
So far, so good, right? Yes, but Karen is an accounting clerk and as such requires access to your payroll system. Access to this system requires approval from the accounting department's manager, Becky. Nsure Identity Manager alone cannot help you here, but Nsure Identity Manager with the Enhanced Provisioning Module can.
In this case, suppose that you have created an approval flow that is triggered automatically when a new User object is created in the eDirectory Accounting container. Governed by this approval flow, the Enhanced Provisioning Module sends a provisioning request to Becky, who later opens the request and clicks Approve. Based on rules you configure for the Approval Workflow Driver, the completion of this approval flow prompts Nsure Identity Manager to provision Karen's access to the payroll system. (The Approval Workflow Driver is the interface between the Enhanced Provisioning Module and Nsure Identity Manager. For more information, see About the Architecture.)
Karen also requires access to your Oracle financial system, which requires a more complex, multi-step approval process. Both the comptroller and chief financial officer (CFO) must approve access to Oracle. As with the last approval flow, this flow executes automatically when a new User object is created in the eDirectory Accounting container. Based on the order of things prescribed in this flow, the Enhanced Provisioning Module sends an Oracle provisioning request first to the comptroller. When the comptroller approves this request, the Enhanced Provisioning Module automatically routes it to the CFO. Again based on rules you have configured for your Approval Workflow Driver, the completion of this approval flow triggers Nsure Identity Manager to provision Karen's access to the Oracle financial system.
Within minutes of HR entering Karen's information into SAP, she has access to all of the network resources she needs to do her job. You can extend this example further and suppose that at the time the HR person entered Karen's information, she submitted provisioning requests for a laptop and cell phone. Perhaps later, after several productive days, Karen submits a request of her own-for paper clips.
Super Search
While the ability to automate approval flows steals the limelight when discussing the Enhanced Provisioning Module, the module does have additional, attractive features.
For example, the Enhanced Provisioning Module includes the Search List portlet that enables you and users to search the mass of corporate identity information with pin-point accuracy. Using this portlet, users can search one or more eDirectory data stores for any objects and attributes that you expose. (You expose these objects and attributes through the data abstraction layer. For more information about that, see About the Architecture.)
Depending upon how this portlet's preferences have been configured, users can start their search by choosing from a pulldown list the objects for which they want to search. For example, they might choose to search for users, groups or devices. The search criteria from which they can choose depends upon the object type they select. For example, you might configure this portlet to display options such as "First name starts with" or "Last name includes" when the search focus is users.
Finally, users choose the type of information they want displayed, and this is where the potential for the Search List portlet gets interesting. Users can choose from one of several display types, namely White Pages, Yellow Pages, Green Pages or Organization Pages. (See Figure 3A and Figure 3B.) These pages generally display the following type of information, but can include more or less, depending upon how you have configured them:
White Pages display contact information, such as telephone number, e-mail address and GroupWise or Yahoo instant messaging (IM) name. You can enable users to send e-mail or launch IM directly from the results.
Yellow Pages display location information, such as users' assigned geographic region.
Green Pages display skill sets, such as users' education, certifications, technical skills (such as COBOL, XML or Java) and technology skills (such as names of actual products).
Organization Pages display information regarding users' positions in the corporate hierarchy, such as users' managers or department location.
Figure 3A
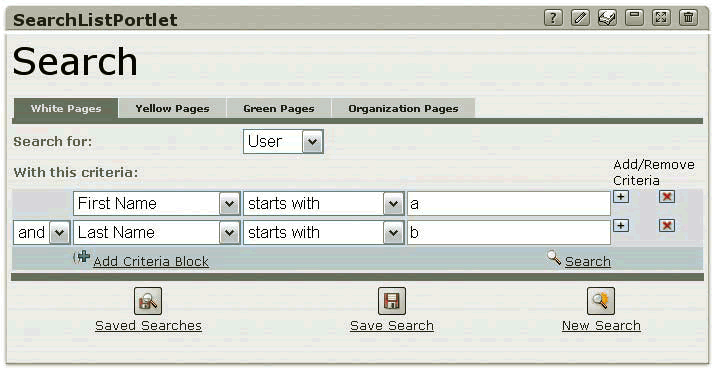
Figure 3B
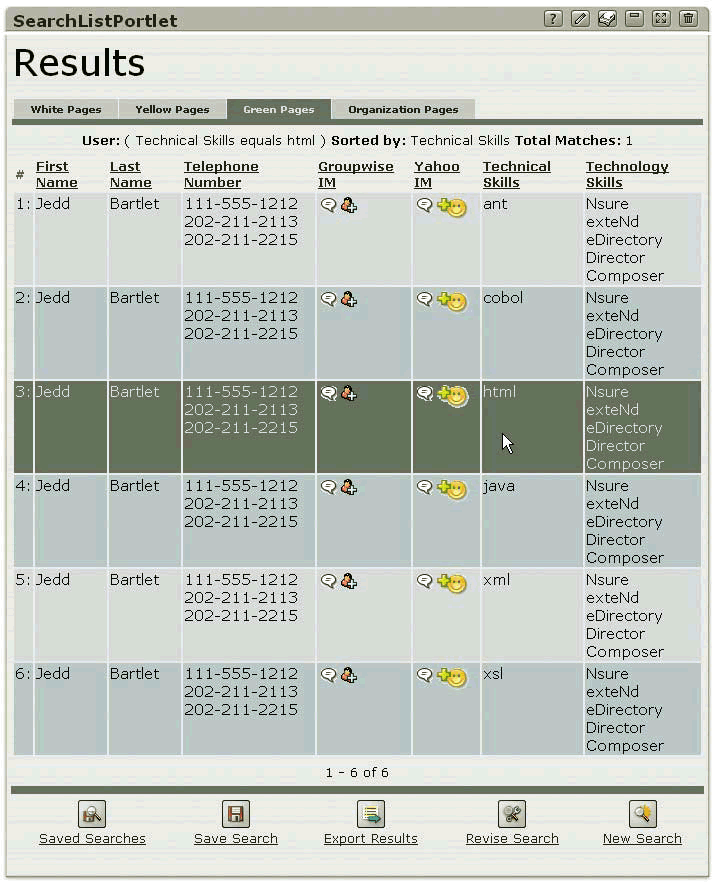
Users also can save their search results and later retrieve them.
The Power of Organization
The Enhanced Provisioning Module also enables you to define advanced organizational charts and to offload some identity management tasks.
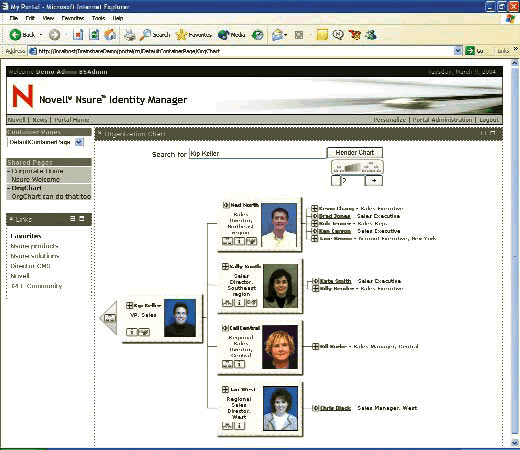
The Enhanced Provisioning Module includes an Org Chart portlet that enables end users to view (and only view) and browse relationships between eDirectory objects that you define in the Relationship Designer portlet. (See Figure 4.) The results, which are more interesting than this brief description might lead you to believe, can reveal information such as the following:
The hierarchy of your organization, such as employees and their managers
A group membership list
The devices (such as cell phones and laptops) assigned to a user
Figure 4
Another portlet (called the Entity Create portlet) enables end users with the necessary rights to create eDirectory objects or to launch workflows that create the objects. This can be particularly useful for temporary or contract workers, partners, customers and even permanent employees (who may not be entered into the HR system immediately). Assuming that new accounts in your HR system serve as triggers for automated provisioning processes, then you might have to manually provision resources for users who fit these descriptions.
The Entity Create portlet saves you the hassle. By enabling department managers and other users to create eDirectory User objects, you empower them to better manage their own areas within your company. Furthermore, once they create the object, the provisioning processes you already have in place can execute automatically, thereby sparing you the time you would otherwise spend manually creating accounts for these users.
About the Architecture
At this point, you may have a fairly good understanding of what the Enhanced Provisioning Module enables, but little to no understanding of how it works. A brief look at the architecture helps to clear the fog on this front. (See Figure 5.)
As you can see in Figure 5, the Enhanced Provisioning Module interacts with several Novell products:
exteNd
Novell Modular Authentication Services (NMAS)
eDirectory
Nsure Identity Manager
Novell Nsure Audit
Figure 5
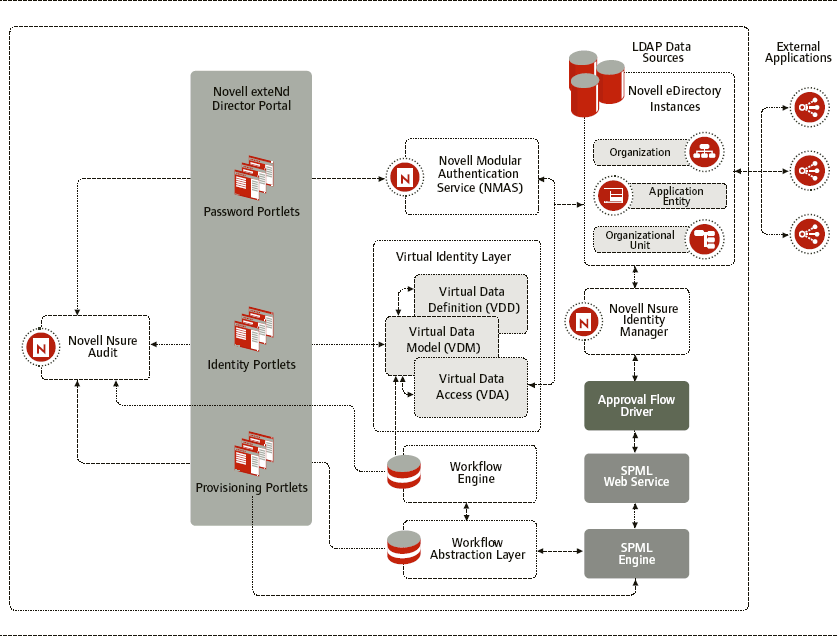
As this figure also shows, these products interact with the Enhanced Provisioning Module architectural components:
Portlets
Virtual Identity Layer
Service Provisioning Markup Language (SPML) Engine and SPML Web Service
Workflow Components
Workflow Abstraction Layer
Approval Flow Driver
What is the purpose of each of these components and how do they interact?
Novell exteNd
To begin with, a user logs into the Enhanced Provisioning Module out-of-the-box portal that you configure and customize using Novell exteNd.
As you may know, exteNd is a suite of tools for rapidly developing and deploying service-oriented Web applications, such as portals. (For more information, see Novell exteNd 5.2 and the Pursuit of SOA-Called Happiness, in the November/December 2004 issue.) Working with consultants, you use exteNd to build a provisioning portal, which opens the door for you and network users to many of the features that the Enhanced Provisioning Module provides.
Novell Modular Authentication Services
The user is authenticated to this portal by way of Novell Modular Authentication Services. With Novell Modular Authentication Services, you can authenticate users to your network resources by deploying login methods based on any type of login factor or combination of factors. For example, using modules provided by Novell or a thirdparty developer, you can authenticate users based on tokens, smart cards, fingerprints, voices or even faces. (For more information, see NMAS: It's What Spy Movies are Made Of in the February 2000 issue.)
Portlets
Once logged in, the user launches one of the portlets included with the Enhanced Provisioning Module. These portlets provide several different services and fall into three categories:
Identity portlets, which allow end users to interact with the identity-based data in your eDirectory stores.
Password portlets, which enable users to change their own passwords.
Provisioning portlets, which provide the interfaces through which users interact with approval flows.
Virtual Identity Layer
If the user launches one of the identity or password portlets to search, add to or modify information in eDirectory, the portal routes the user's requests to eDirectory by way of the Virtual Identity Layer. This layer provides applicationspecific authorization and virtual aggregation of identity data in one or more eDirectory instances. The Virtual Identity Layer consists of three components:
Virtual Data Definition, a set of XML files in which you define the eDirectory objects and attributes that users will be able to access via the Enhanced Provisioning Module.
Virtual Data Access, an interface that portlets call (by way of the Virtual Data Model and using a Java API) to gain read-write access to your eDirectory data store(s).
Virtual Data Model, an interface that exposes the Virtual Data Definition and Virtual Data Access to the portlets that run in your provisioning portal.
The Virtual Identity Layer also is responsible for delivering the identity information that the user requests (via the identity portlet) in the requested presentation format (for example, as one of the Search List pages).
When users launch one of the Identity or Password portlets to submit changes to the eDirectory data store, for example, by creating an object or changing their password, the changes they make are synchronized according to Nsure Identity Manager rules that govern connected systems.
SPML and Workflow Components
Approval flows interact with the Service Provisioning Markup Language (SPML) Engine provided by the Enhanced Provisioning Module. The SPML Engine supports SPML 1.0, an OASIS standard that defines an XML-based framework for exchanging provisioning information. (For more information, see www.oasis-open.org.)
The SPML Engine processes provisioning requests from provisioning portlets and interacts with the Workflow Abstraction Layer to initiate the processes required to fulfill these requests. The Workflow Abstraction Layer interacts with the exteNd Director Workflow Engine to execute and manage the processes associated with approval flows that are triggered by provisioning requests.
The SPML Engine also interacts with the Approval Flow Driver. The Approval Flow Driver provides an interface between Novell Nsure Identity Manager and the Enhanced Provisioning Module (via the SPML Engine). This driver gives the module the ability to initiate approval flows automatically in response to events in connected systems in your Nsure Identity Manager environment.
Novell Nsure Audit
You can configure Novell Nsure Audit to log events generated by the Enhanced Provisioning Module, such as approval flows, eDirectory searches and password self-service. Nsure Audit is a centralized, cross-platform auditing service that collects event data from multiple applications running on diverse platforms. Nsure Audit logs the data it collects in a single, non-repudiable data store. If you log events to Nsure Audit, you can later run reports on the logged data. The Enhanced Provisioning Module comes with two predefined log reports that you can run with Nsure Audit Report to query data from an Nsure Audit log database.
The Right Answer
At this time, you purchase, install and configure the Enhanced Provisioning Module with help from either Novell Consulting or a Novell channel partner. (To request a demo, see it online.) In the next release of Nsure Identity Manager (scheduled for third quarter 2005), the Enhanced Provisioning Module will be included as a core component. When released as part of Nsure Identity Manager, the Enhanced Provisioning Module will require only minimal configuration.
In any case, with the Enhanced Provisioning Module up and running, your answers to questions about the efficiency of your provisioning practices might change-significantly. How much time do employees waste before they have the resources and assets they need to get to work? How much time does it take for employees who are promoted or transferred to gain rights to newly needed IT resources? How many hours can disgruntled employees write to (and potentially corrupt) the systems they should no longer even see?
Why Identity Management Makes Cents
At the core of every provisioning solution is a solid identity management foundation, but implementing such a solution requires an investment of time and money that does not go unnoticed. If you have a chief financial officer who is still blanching at the initial cost of identity management, I have good news-or rather, PricewaterhouseCoopers has good news.
According to PricewaterhouseCoopers, companies can expect a return on investment (ROI) in an identity management solution in "usually 8 to 12 months." (For more information, see the report online.)
Even the cheapest of cheap financial officers has to admit that's not bad-and entirely convincing in light of statistics from Meta Group Consulting. Meta Group Consulting surveyed 420 companies with annual revenues of US $500M. From this survey, the group determined that deploying an identity management solution could potentially save such companies an average of US $4,395,081.60 in one year alone. (For more information, see the report online.)
The relatively short ROI and relatively large savings are not the only points that help build a convincing business case for identity management. Results from the 2004 Information Security Breach Survey bring this already-clear case into even sharper focus. For this survey, the Department of Trade and Industry (DTI) for the United Kingdom interviewed representatives from 1,000 businesses of all sizes throughout the UK. Among pages worth of findings, DTI noted that last year, one in five large businesses experienced a security breach resulting from weaknesses in their identity management practices. These security breaches included unauthorized access, financial fraud, and breaches in confidentiality, 15 percent of which cost companies more than £100,000 to resolve. (You can download this survey from www.security-survey.gov.uk.)
What a Case!
Using the Enhanced Provisioning Module, you can work with consultants to configure and customize a provisioning portal that helps answer some of the questions that might plague you:
How can I automate complex approval flows?
With the Enhanced Provisioning Module, you can create approval flows that automatically route provisioning requests to one or more individuals either sequentially or in parallel. Users can initiate these approval flows by submitting provisioning requests. The types and number of provisioning requests you make available to your users are limited only by your imagination. Potentially, you can give users the power to initiate requests for literally anything-digital or physical-they might need to do their job.
That said, users are not the only ones who can get an approval flow flowing. Approval flows can be launched automatically in response to events in any of the systems you have connected via Novell Nsure Identity Manager. For example, a new account in PeopleSoft might initiate an approval flow that gains the permission necessary to provision access to the Prototype directory on a Linux server.
How can I automatically provision resources and assets for temporary and contract employees or for business partners and customers?
The Enhanced Provisioning Module provides a set of portlets and architectural components for managing identity information in one or more identity data stores. For example, one portlet enables users (to whom you grant the necessary rights) to create new objects in eDirectory. By creating User objects for users whose information is not entered in the HR database, you can tap into automated provisioning processes you already have in place.
How do I provide user self-service and delegated administration?
The Enhanced Provisioning Module enables you to empower users with the ability to create objects in your identity data stores. The result is that you offload some of your identity management burden. The Enhanced Provisioning Module also provides self-service features, such as password management features, that lift still more identity management weight off your shoulders. In fact, 30 percent of all help desk calls are password related. Thus, by empowering users with the ability to solve their own password problems, you significantly decrease your workload.
How do I find users, devices and resources within my organization?
The Enhanced Provisioning Module provides several configurable search portlets out of the box. Depending upon how you configure these portlets, users can search your identity data store(s) for various objects and request a wide range of information about these objects. For example, a search for users can return information about users' geographic location and their technical skills.
* Originally published in Novell Connection Magazine
Disclaimer
The origin of this information may be internal or external to Novell. While Novell makes all reasonable efforts to verify this information, Novell does not make explicit or implied claims to its validity.